阿里云服务器的 webRTC 系统搭建与验证
本篇内容是对本次实验过程记录,即可以备忘、也能给有需求朋友提供一些参考。
环境说明:
服务器环境:
阿里云ecs的 cetos7 系统.
虚拟机ip:inet 172.26.43.146 netmask 255.255.240.0 broadcast 172.26.47.255
公网IP:39.99.xx.xx
房间与信令服务: SkyRTC,连接地址,https://github.com/dtltljb/webrtc_server_node.git
客户端环境
测试手机: 2部华为手机
安卓测试代码: https://github.com/dtltljb/webrtc_android.git
备注:
此服务端 nodejs 代码和安卓客户端代码是在 ddssingsong 大神 github 上 fork 过来,在此贴上
他的github地址, https://github.com/ddssingsong/ ,再次感谢。
一、安装环境依赖
1.1). 下载nodejs:
https://nodejs.org/en/download/
测试使用的版本:v16.13.2
//> 解压
tar -xvf node-v16.13.2-linux-x64.tar.xz
//> 改名
mv node-v16.13.2-linux-x64 nodejs
//> 进入目录
cd nodejs/
//> 确认一下nodejs下bin目录是否有node和npm文件,如果有就可以执行软连接
sudo ln -s /root/webRTC/nodejs/bin/npm /usr/local/bin/
sudo ln -s /root/webRTC/nodejs/bin/node /usr/local/bin/
//> 版本信息
[root@iZ8vbdsaostzzry9mmk5lrZ webRTC]# ls /usr/local/bin/npm -la
lrwxrwxrwx 1 root root 27 Jan 13 10:11 /usr/local/bin/npm -> /root/webRTC/nodejs/bin/npm
[root@iZ8vbdsaostzzry9mmk5lrZ webRTC]# npm -v
8.3.0
[root@iZ8vbdsaostzzry9mmk5lrZ webRTC]# ls /usr/local/bin/node -la
lrwxrwxrwx 1 root root 28 Jan 13 10:11 /usr/local/bin/node -> /root/webRTC/nodejs/bin/node
[root@iZ8vbdsaostzzry9mmk5lrZ webRTC]# node -v
v16.13.2
1.2) 安装相关依赖包
$ sudo yum install openssl-devel
$ sudo yum install sqlite3
$ sudo yum install sqlite-devel
$ sudo yum install libevent
$ sudo yum install libevent-devel
$ sudo yum install coturn
二、 房间与信令服务
本次实验只测试 安卓客户端与客户端直连功能,不测试pc端web服务,所以不用修改服务端代码,
直接运行server.js 服务即可。
2.1 下载服务端源码、安装 SkyRTC 依赖包
$ git clone https://github.com/dtltljb/webrtc_server_node.git
$ cd webrtc_server_node
$ npm install //> 安装依赖模块
2.1 运行服务及日志
[root@iZ8vbdsaostzzry9mmk5lrZ webrtc_server_node]# node server.js
Server running at http://0.0.0.0:3000/
创建新连接
{"data":{"room":"232343"},"eventName":"__join"}
房间里有1人
新用户5001bf26-3bec-4556-b6b8-b926487e5594加入房间232343
创建新连接
{"data":{"room":"232343"},"eventName":"__join"}
房间里有2人
新用户ec9337c5-9364-4417-ad39-00d8a8aabefd加入房间232343
{"data":{"sdp":{"sdp":"v=0\r\no=-label:ARDAMSv0\r\n","type":"offer"},"socketId":"5001bf26-3bec-4556-b6b8-b926487e5594"},"eventName":"__offer"}
......
接收到来自ec9337c5-9364-4417-ad39-00d8a8aabefd的ICE Candidate
{"data":{"candidate":"candidate:1510613869 1 udp 2122063615 127.0.0.1 46037 typ host generation 0 ufrag 7h+X network-id 1","id":"video","label":1,"socketId":"5001bf26-3bec-4556-b6b8-b926487e5594"},"eventName":"__ice_candidate"}
接收到来自ec9337c5-9364-4417-ad39-00d8a8aabefd的ICE Candidate
{"data":{"candidate":"candidate:842163049 1 udp 1685987071 36.112.201.199 39490 typ srflx raddr 10.25.193.90 rport 38269 generation 0 ufrag 7h+X network-id 3 network-cost 900","id":"video","label":1,"socketId":"5001bf26-3bec-4556-b6b8-b926487e5594"},"eventName":"__ice_candidate"}
接收到来自ec9337c5-9364-4417-ad39-00d8a8aabefd的ICE Candidate
{"data":{"candidate":"candidate:842163049 1 udp 1685987071 36.112.201.199 39491 typ srflx raddr 10.25.193.90 rport 42357 generation 0 ufrag 7h+X network-id 3 network-cost 900","id":"audio","label":0,"socketId":"5001bf26-3bec-4556-b6b8-b926487e5594"},"eventName":"__ice_candidate"}
.......
接收到来自ec9337c5-9364-4417-ad39-00d8a8aabefd的ICE Candidate
{"data":{"sdp":{"sdp":"v=0\r\no=- label:ARDAMSv0\r\n","type":"answer"},"socketId":"ec9337c5-9364-4417-ad39-00d8a8aabefd"},"eventName":"__answer"}
接收到来自5001bf26-3bec-4556-b6b8-b926487e5594的Answer
{"data":{"candidate":"candidate:161754461 1 udp 2122260223 172.16.20.209 59089 typ host generation 0 ufrag u1pU network-id 3 network-cost 10","id":"audio","label":0,"socketId":"ec9337c5-9364-4417-ad39-00d8a8aabefd"},"eventName":"__ice_candidate"}
......
接收到来自5001bf26-3bec-4556-b6b8-b926487e5594的ICE Candidate
{"data":{"candidate":"candidate:1876313031 1 tcp 1518222591 ::1 46443 typ host tcptype passive generation 0 ufrag u1pU network-id 2","id":"audio","label":0,"socketId":"ec9337c5-9364-4417-ad39-00d8a8aabefd"},"eventName":"__ice_candidate"}
接收到来自5001bf26-3bec-4556-b6b8-b926487e5594的ICE Candidate
{"data":{"candidate":"candidate:344579997 1 tcp 1518149375 127.0.0.1 42070 typ host tcptype passive generation 0 ufrag u1pU network-id 1","id":"audio","label":0,"socketId":"ec9337c5-9364-4417-ad39-00d8a8aabefd"},"eventName":"__ice_candidate"}
接收到来自5001bf26-3bec-4556-b6b8-b926487e5594的ICE Candidate
三、 ICE(STUN、TURN)服务
3.1 安装
安装 coturn 服务有两种方法,直接安装和下载源码安装。
//> centos 7 直接安装
$ sudo yum install coturn
下载源码安装:
git clone https://github.com/coturn/coturn
cd coturn
./configure
make
sudo make install
此两种安装方式缺省配置文件路径有些差异,需注意一下。
验证验证。
router@ubuntu:~/webRTC/webrtc_server_node$ which turnserver
/usr/local/bin/turnserver
3.2 创建数据库
coturn的“瞬时认证”需要依赖数据库,如果我们的用户量较大可以考虑采用其他数据库;
采用源码安装coturn时,源码文件夹下/turndb/schema.sql 是 sqlite3 数据库初始化内容.
//> 配置数据库
router@ubuntu:~/webRTC$ rm -f /usr/local/var/db/turndb
router@ubuntu:~/webRTC$ cat coturn/turndb/schema.sql |sqlite3 /usr/local/var/db/turndb
//> 查看数据表
router@ubuntu:~/webRTC$ sqlite3 /usr/local/var/db/turndb
SQLite version 3.31.1 2020-01-27 19:55:54
Enter ".help" for usage hints.
sqlite> .tables
admin_user oauth_key turn_secret
allowed_peer_ip turn_origin_to_realm turnusers_lt
denied_peer_ip turn_realm_option
//> 数据库表list
router@ubuntu:~/webRTC$ cat coturn/turndb/schema.sql
CREATE TABLE turnusers_lt (
realm varchar(127) default '',
name varchar(512),
hmackey char(128),
PRIMARY KEY (realm,name)
);
CREATE TABLE turn_secret (
realm varchar(127) default '',
value varchar(256),
primary key (realm,value)
);
CREATE TABLE allowed_peer_ip (
realm varchar(127) default '',
ip_range varchar(256),
primary key (realm,ip_range)
);
CREATE TABLE denied_peer_ip (
realm varchar(127) default '',
ip_range varchar(256),
primary key (realm,ip_range)
);
CREATE TABLE turn_origin_to_realm (
origin varchar(127),
realm varchar(127),
primary key (origin)
);
CREATE TABLE turn_realm_option (
realm varchar(127) default '',
opt varchar(32),
value varchar(128),
primary key (realm,opt)
);
CREATE TABLE oauth_key (
kid varchar(128),
ikm_key varchar(256),
timestamp bigint default 0,
lifetime integer default 0,
as_rs_alg varchar(64) default '',
realm varchar(127),
primary key (kid)
);
CREATE TABLE admin_user (
name varchar(32),
realm varchar(127),
password varchar(127),
primary key (name)
);
本次实验测试实验采用静态用户名方式,不安装数据库应该也可以使用的,我没有测试过。
3.3 turnserver.conf配置文件
本次实验配置文件内容和路径。
[root@iZ8vbdsaostzzry9mmk5lrZ webRTC]# cat /etc/coturn/turnserver.conf
# RFC5766-TURN-SERVER configuration file
# RFC5766-TURN-SERVER配置文件
# TURN为UDP和TCP的侦听器端口(默认: 3478)。
# 注:实际上,TLS和DTLS会话可以连接到"清晰的"TCP和UDP端口,——如果允许配置。
#
#listening-port=3478
listening-port=3478
# TURN为TLS的侦听器端口(默认: 5349)。
# 注意:事实上,"清晰的"TCP和UDP会话可以连接到TLS和DTLS端口,如果允许配置。
# TURN服务器"自动"识别传输类型。实际上,两个监听终端点("清晰的"端和"TLS"端)是
# 对等的功能;但我们保持两个端点来满足RFC 5766规范。
# 对于安全的TCP连接,我们目前支持SSL的3个版本,是TLS 1.0版本,1.1版本和1.2版本。
# SSL2还支持"encapculation模式"。对于安全的UDP连接,我们支持DTLS版本1。
#
tls-listening-port=5349
# 侦听器中继服务器的IP地址。可以指定多个侦听器。
# 如果没有在配置文件或者命令选项中指定监听的IP,
# 那么所有的IPv4和IPv6所有的IP将被监听
#
listening-ip=172.26.43.146
#listening-ip=2607:f0d0:1002:51::4
# 中继地址(本地IP地址将用于传递数据包的给每个端)
# 可以使用多个中继地址。
# 相同的IP可以用作监听IP和继电器IP。
# 如果没有指定中继IP,那么turnserver将应用默认策略:它将自行决定使用那个中继
# 地址,并且它总是会使用客户端套接字的IP地址作为中继的IP地址在TURN会话中(如果
# 请求的中继地址族解决同族的客户端套接字)。
#
relay-ip=172.26.43.146
#relay-ip=2607:f0d0:1002:51::5
# By default, this value is empty, and no address mapping is used.
#
external-ip=39.99.xx.xx
#OR:
#external-ip=60.70.80.91/172.17.19.101
# Number of relay threads to handle the established connections
# (in addition to authentication thread and the listener thread).
# If set to 0 then application runs relay process in a single thread,
# in the same thread with the listener process (the authentication thread will
# still be a separate thread).
# In the older systems (Linux kernel before 3.9),
# the number of UDP threads is always one thread per network listening endpoint -
# including the auxiliary endpoints - unless 0 (zero) or 1 (one) value is set.
relay-threads=5
# UDP中继端点的上下边界:
# (默认是49152至65535)
#
min-port=59000
max-port=65500
# 取消TURN服务器运行'normal' 'moderate'详细模式。
# 默认情况下,详细模式是关闭的。
#
verbose
# 取消在TURN消息中使用指纹。
# 默认情况下,指纹是关闭的。
#
fingerprint
# 取消使用长期证书机制。
# 默认情况下不使用凭证机制(允许任何用户)。
# 这个选项可能使用用户数据文件或PostgreSQL或MySQL或Redis来存储用户密钥。
#
lt-cred-mech
# 'Static'用户长期占凭证机制。
# 这个选项不能用于TURN REST API或短期凭证机制。
# 'Static'用户帐户不是turnserver程序动态检查,所以他们不能改变在turnserver运行时。
# Or, equivalently, with open clear password (less secure):
#或者是这样,明文密码(不安全的):
#
user=ddssingsong:123456
# 'Dynamic'用户帐户数据库文件名。
# 只有用户长期机制可以存储在一个文件,短期机制不会处理选项,短期机制需要PostgreSQL或MySQL或
# Redis数据库。
# 'Dynamic'的长期用户帐户在turnserver程序中动态检查的,这样他们可以改变的在turnserver运行时。
# 默认文件名是turnuserdb.conf.
userdb=/etc/coturn/turndb
# TURN REST API的长期凭证机制范围。
#
realm=metis.org
# 如果没有TLS客户端监听器需要取消。
# 默认情况下TLS客户端监听器总是启动。
#
no-tls
# 如果不允许TCP中继端点需要取消。
# 默认情况下启用TCP继电器端点(如在RFC 5766)。
#
no-tcp-relay
# 取消如果需要额外的安全,现时已有有限的生命周期(600秒)。
# 默认情况下,一个会话的唯一临界值,但它一般拥有无限的生命周期。这个选项,临界值
# 仅限于600秒,之后,客户端将得到438错误,将不得不重新认证。
#
stale-nonce
# 证书文件。
# 使用绝对路径或路径相对于配置文件。
#
cert=/etc/turn_server_cert.pem
# 私钥文件。
# 使用绝对路径或路径相对于配置文件。使用PEM文件格式。
#
pkey=/etc/turn_server_pkey.pem
# 设置日志文件
# 默认情况下,turnserver尝试一个日志文件在/var/log,/var/tmp,/tmp和
# 当前目录(那个文件先打开成功,文件将被使用)。
# 采用这一选项可以设置明确的日志文件名。
# 特殊的名字是"stdout"和"-"——他们将强制所有的输出。同时,"syslog"名称将强制所有的系统日志(syslog)。
# 在运行时,日志文件可以重置通过SIGHUP信号在turnserver程序中。
#
log-file=/var/tmp/turn.log
# 标记用于不接受的端在环回地址(127.x.x.x 和 ::1)。
# 这是一个额外的安全措施。
no-loopback-peers
# 标记用于不接受的端在广播地址(224.0.0.0和以上的,和FFXX:*)。
# 这是一个额外的安全措施。
no-multicast-peers
# 存储进程pid的文件名。
# 默认是/var/run/turnserver.pid(超级用户使用)或者是/var/tmp/turnserver.pid
#
#pidfile="/var/run/turnserver.pid"
pidfile="/var/tmp/turnserver.pid"
# Mobility with ICE (MICE) specs support.
#
# 移动的ICE(MICE)的规范支持。
#
mobility
#
# 关掉CLI的支持。
# 默认情况下它总是ON。
# 参阅选项cli-ip和cli-port。
no-cli
四、 安卓客户端
4.1 下载源码切换分支
git clone https://github.com/dtltljb/webrtc_android.git
cd webrtc_android
git branch -a
git checkout branch_nodejs
切换分支后,我的android studio是3.5 版本,打开直接编译通过,感谢 ddssingsong 大神的分享。
4.2 修改源码
//> 第一处修改: 登录界面 ip 地址和http协议,app/src/main/java/com/dds/nodejs/NodejsActivity.java
public class NodejsActivity extends AppCompatActivity {
private EditText et_signal;
private EditText et_room;
@Override
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
setContentView(R.layout.activity_nodejs);
Toolbar toolbar = findViewById(R.id.toolbar);
setSupportActionBar(toolbar);
initView();
initVar();
}
//> 修改部分
private void initVar() {
et_signal.setText("http://39.99.xx.xx:3000/wss");
et_room.setText("232343");
}
}
//> 第二处修改: /app/src/main/java/com/dds/nodejs/WebrtcUtil.java
public class WebrtcUtil {
//public static final String HOST = "47.93.186.97";
public static final String HOST = "39.99.xx.xx";
// turn and stun
private static MyIceServer[] iceServers = {
new MyIceServer("stun:stun.l.google.com:19302"),
// 测试地址1
new MyIceServer("stun:" + HOST + ":3478?transport=udp"),
new MyIceServer("turn:" + HOST + ":3478?transport=udp",
"ddssingsong",
"123456"),
new MyIceServer("turn:" + HOST + ":3478?transport=tcp",
"ddssingsong",
"123456"),
};
......
}
本次实验未采用 nginx 代理 ws 服务,所以代码修改为http协议。本次实验以简单粗暴方式,搭建处系统运行基本环境为主旨。
本次在网上也看了很多相关内容,本次实验环境非常简洁方式。
五、网络环境处理
由于本次实验是在阿里云ecs上,需要进入阿里 ECS 控制台开启输入规则并关闭 Centos 7 系统的防火墙。
阿里云网络与安全
进入控制台后、选择 ECS 实例、左侧有"网络与安全"选项,在"入方向"栏中,手动增加"3478、5349、3000" TCP和UDP端口放行规则。
关闭 Centos 防火墙
systemctl stop firewalld.service.
systemctl disable firewalld.service.
此命令是临时性的关闭。
六、实验验证结果记录及图片
至此webRTC系统运行环境就搭建完成,直接启动 turnserver 服务就可以,输出日志内容如下。
turnserver 运行日志
0: : IPv4. TCP listener opened on : 172.26.43.146:3478
0: : IO method (general relay thread): epoll (with changelist)
0: : turn server id=4 created
0: : IPv4. TCP listener opened on : 172.26.43.146:3478
0: : IO method (general relay thread): epoll (with changelist)
0: : turn server id=0 created
0: : IPv4. TCP listener opened on : 172.26.43.146:3478
0: : IPv4. DTLS/UDP listener opened on: 172.26.43.146:3478
0: : IPv4. DTLS/UDP listener opened on: 172.26.43.146:5349
0: : Total General servers: 5
0: : SQLite DB connection success: /var/lib/coturn/turndb //> 连接数据库成功,sqlite3
0: : IO method (auth thread): epoll (with changelist)
0: : IO method (auth thread): epoll (with changelist)
0: : IO method (admin thread): epoll (with changelist)
144: : session 004000000000000001: realm <metis.org> user <>: incoming packet BINDING processed, success
144: : session 001000000000000001: realm <metis.org> user <>: incoming packet BINDING processed, success
144: : session 004000000000000001: realm <metis.org> user <>: incoming packet message processed, error 401: Unauthorized
144: : session 001000000000000001: realm <metis.org> user <>: incoming packet message processed, error 401: Unauthorized
144: : IPv4. tcp or tls connected to: 36.112.201.199:39661
144: : IPv4. tcp or tls connected to: 36.112.201.199:39663
144: : session 001000000000000002: realm <metis.org> user <>: incoming packet message processed, error 401: Unauthorized
144: : IPv4. Local relay addr: 172.26.43.146:60979
144: : session 004000000000000001: new, realm=<metis.org>, username=<ddssingsong>, lifetime=600
144: : session 004000000000000001: realm <metis.org> user <ddssingsong>: incoming packet ALLOCATE processed, success
144: : session 004000000000000002: realm <metis.org> user <>: incoming packet message processed, error 401: Unauthorized
144: : IPv4. Local relay addr: 172.26.43.146:61337
144: : session 001000000000000001: new, realm=<metis.org>, username=<ddssingsong>, lifetime=600
144: : session 001000000000000001: realm <metis.org> user <ddssingsong>: incoming packet ALLOCATE processed, success
144: : IPv4. Local relay addr: 172.26.43.146:60173
144: : session 001000000000000002: new, realm=<metis.org>, username=<ddssingsong>, lifetime=600
144: : session 001000000000000002: realm <metis.org> user <ddssingsong>: incoming packet ALLOCATE processed, success
144: : IPv4. Local relay addr: 172.26.43.146:60186
144: : session 004000000000000002: new, realm=<metis.org>, username=<ddssingsong>, lifetime=600
144: : session 004000000000000002: realm <metis.org> user <ddssingsong>: incoming packet ALLOCATE processed, success
144: : session 003000000000000001: realm <metis.org> user <>: incoming packet BINDING processed, success
144: : session 003000000000000001: realm <metis.org> user <>: incoming packet message processed, error 401: Unauthorized
144: : IPv4. Local relay addr: 172.26.43.146:62015
144: : session 003000000000000001: new, realm=<metis.org>, username=<ddssingsong>, lifetime=600
144: : session 003000000000000001: realm <metis.org> user <ddssingsong>: incoming packet ALLOCATE processed, success
144: : IPv4. tcp or tls connected to: 124.202.194.238:58740
144: : session 001000000000000003: realm <metis.org> user <>: incoming packet message processed, error 401: Unauthorized
144: : session 003000000000000001: peer 10.25.193.90 lifetime updated: 300
144: : session 003000000000000001: realm <metis.org> user <ddssingsong>: incoming packet CREATE_PERMISSION processed, success
144: : session 003000000000000001: realm <metis.org> user <ddssingsong>: incoming packet CREATE_PERMISSION processed, error 403: Forbidden IP
144: : session 003000000000000001: realm <metis.org> user <ddssingsong>: incoming packet message processed, error 403: Forbidden IP
144: : session 003000000000000001: peer 36.112.201.199 lifetime updated: 300
144: : session 003000000000000001: realm <metis.org> user <ddssingsong>: incoming packet CREATE_PERMISSION processed, success
144: : session 003000000000000001: peer 172.26.43.146 lifetime updated: 300
144: : session 003000000000000001: realm <metis.org> user <ddssingsong>: incoming packet CREATE_PERMISSION processed, success
144: : session 003000000000000001: peer 172.26.43.146 lifetime updated: 300
144: : session 003000000000000001: realm <metis.org> user <ddssingsong>: incoming packet CREATE_PERMISSION processed, success
144: : IPv4. Local relay addr: 172.26.43.146:65200
144: : session 001000000000000003: new, realm=<metis.org>, username=<ddssingsong>, lifetime=600
144: : session 001000000000000003: realm <metis.org> user <ddssingsong>: incoming packet ALLOCATE processed, success
144: : session 001000000000000003: peer 10.25.193.90 lifetime updated: 300
144: : session 001000000000000003: realm <metis.org> user <ddssingsong>: incoming packet CREATE_PERMISSION processed, success
144: : session 001000000000000003: realm <metis.org> user <ddssingsong>: incoming packet CREATE_PERMISSION processed, error 403: Forbidden IP
144: : session 001000000000000003: realm <metis.org> user <ddssingsong>: incoming packet message processed, error 403: Forbidden IP
144: : session 001000000000000003: peer 36.112.201.199 lifetime updated: 300
144: : session 001000000000000003: realm <metis.org> user <ddssingsong>: incoming packet CREATE_PERMISSION processed, success
144: : session 001000000000000003: peer 172.26.43.146 lifetime updated: 300
144: : session 001000000000000003: realm <metis.org> user <ddssingsong>: incoming packet CREATE_PERMISSION processed, success
144: : session 001000000000000003: peer 172.26.43.146 lifetime updated: 300
144: : session 001000000000000003: realm <metis.org> user <ddssingsong>: incoming packet CREATE_PERMISSION processed, success
144: : session 004000000000000002: refreshed, realm=<metis.org>, username=<ddssingsong>, lifetime=0
144: : session 004000000000000002: realm <metis.org> user <ddssingsong>: incoming packet REFRESH processed, success
144: : session 004000000000000002: TCP socket closed remotely 36.112.201.199:39663
144: : session 004000000000000002: usage: realm=<metis.org>, username=<ddssingsong>, rp=3, rb=236, sp=3, sb=312
144: : session 004000000000000002: peer usage: realm=<metis.org>, username=<ddssingsong>, rp=0, rb=0, sp=0, sb=0
144: : session 004000000000000002: closed (2nd stage), user <ddssingsong> realm <metis.org> origin <>, local 172.26.43.146:3478, remote 36.112.201.199:39663, reason: TCP connection closed by client (callback)
144: : session 004000000000000002: delete: realm=<metis.org>, username=<ddssingsong>
144: : session 001000000000000001: refreshed, realm=<metis.org>, username=<ddssingsong>, lifetime=0
144: : session 001000000000000001: realm <metis.org> user <ddssingsong>: incoming packet REFRESH processed, success
144: : session 001000000000000003: peer 36.112.201.199 lifetime updated: 300
......
145: : session 004000000000000001: realm <metis.org> user <ddssingsong>: incoming packet CHANNEL_BIND processed, success
145: : session 001000000000000001: usage: realm=<metis.org>, username=<ddssingsong>, rp=4, rb=256, sp=4, sb=404
145: : session 001000000000000001: peer usage: realm=<metis.org>, username=<ddssingsong>, rp=0, rb=0, sp=0, sb=0
145: : session 001000000000000001: closed (2nd stage), user <ddssingsong> realm <metis.org> origin <>, local 172.26.43.146:3478, remote 36.112.201.199:39660, reason: allocation timeout
145: : session 001000000000000001: delete: realm=<metis.org>, username=<ddssingsong>
153: : session 004000000000000001: usage: realm=<metis.org>, username=<ddssingsong>, rp=903, rb=334991, sp=1155, sb=623631
153: : session 004000000000000001: peer usage: realm=<metis.org>, username=<ddssingsong>, rp=1145, rb=617405, sp=893, sb=330054
......
317: : session 004000000000000001: usage: realm=<metis.org>, username=<ddssingsong>, rp=1036, rb=128147, sp=1012, sb=101684
317: : session 004000000000000001: peer usage: realm=<metis.org>, username=<ddssingsong>, rp=1012, rb=97636, sp=1036, sb=124003
324: : session 003000000000000001: realm <metis.org> user <ddssingsong>: incoming packet BINDING processed, success
329: : session 004000000000000001: usage: realm=<metis.org>, username=<ddssingsong>, rp=1026, rb=126147, sp=1022, sb=93671
329: : session 004000000000000001: peer usage: realm=<metis.org>, username=<ddssingsong>, rp=1022, rb=89583, sp=1026, sb=122043
334: : session 003000000000000001: realm <metis.org> user <ddssingsong>: incoming packet BINDING processed, success
341: : session 004000000000000001: usage: realm=<metis.org>, username=<ddssingsong>, rp=1026, rb=142446, sp=1022, sb=91173
341: : session 004000000000000001: peer usage: realm=<metis.org>, username=<ddssingsong>, rp=1022, rb=87085, sp=1026, sb=138342
344: : session 003000000000000001: realm <metis.org> user <ddssingsong>: incoming packet BINDING processed, success
354: : session 004000000000000001: usage: realm=<metis.org>, username=<ddssingsong>, rp=942, rb=116998, sp=1106, sb=89184
354: : session 004000000000000001: peer usage: realm=<metis.org>, username=<ddssingsong>, rp=1106, rb=84760, sp=942, sb=113230
354: : session 003000000000000001: realm <metis.org> user <ddssingsong>: incoming packet BINDING processed, success
364: : session 003000000000000001: realm <metis.org> user <ddssingsong>: incoming packet BINDING processed, success
366: : session 004000000000000001: usage: realm=<metis.org>, username=<ddssingsong>, rp=992, rb=119141, sp=1056, sb=80693
366: : session 004000000000000001: peer usage: realm=<metis.org>, username=<ddssingsong>, rp=1056, rb=76469, sp=992, sb=115173
374: : session 003000000000000001: realm <metis.org> user <ddssingsong>: incoming packet BINDING processed, success
378: : session 004000000000000001: usage: realm=<metis.org>, username=<ddssingsong>, rp=1012, rb=115590, sp=1036, sb=75468
378: : session 004000000000000001: peer usage: realm=<metis.org>, username=<ddssingsong>, rp=1036, rb=71324, sp=1012, sb=111542
384: : session 003000000000000001: peer 10.25.193.90 lifetime updated: 300
384: : session 003000000000000001: realm <metis.org> user <ddssingsong>: incoming packet CREATE_PERMISSION processed, success
384: : session 003000000000000001: peer 36.112.201.199 lifetime updated: 300
......
385: : session 003000000000000001: peer 172.26.43.146 lifetime updated: 600
385: : session 003000000000000001: realm <metis.org> user <ddssingsong>: incoming packet CHANNEL_BIND processed, success
385: : session 004000000000000001: peer 124.202.194.238 lifetime updated: 600
385: : session 004000000000000001: realm <metis.org> user <ddssingsong>: incoming packet CHANNEL_BIND processed, success
390: : session 004000000000000001: usage: realm=<metis.org>, username=<ddssingsong>, rp=1002, rb=121010, sp=1052, sb=78191
390: : session 004000000000000001: peer usage: realm=<metis.org>, username=<ddssingsong>, rp=1046, rb=73527, sp=996, sb=116370
394: : session 003000000000000001: realm <metis.org> user <ddssingsong>: incoming packet BINDING processed, success
401: : session 004000000000000001: usage: realm=<metis.org>, username=<ddssingsong>, rp=1041, rb=84575, sp=1007, sb=76642
401: : session 004000000000000001: peer usage: realm=<metis.org>, username=<ddssingsong>, rp=1007, rb=72614, sp=1041, sb=80411
6.2 安卓客户端运行效果
本次客户端实验网络 4G 与 WIFI 之间通讯,局域网内测试。
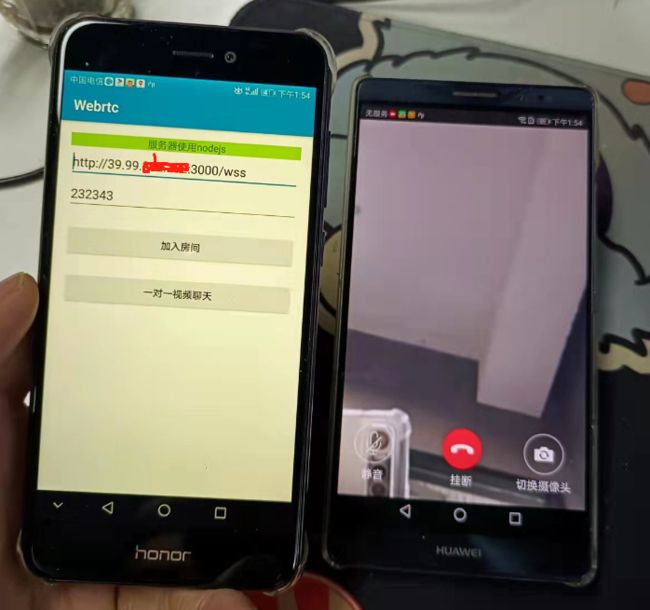
一对一视频聊天登录后效果如下:

参考链接:
https://blog.csdn.net/u011077027/article/details/86225524