Two answers to questions about MISC
ONE glance-50
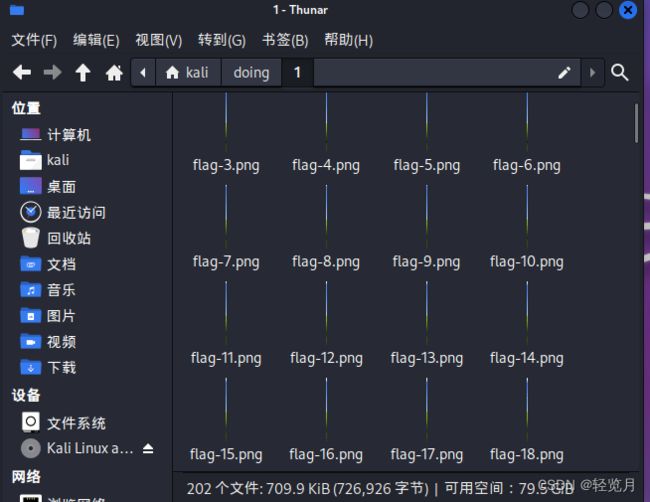
All I get here is a very long gif.
Go to kali and run the following command to update and install.
apt-get update
apt-get install imagemagickBreak the gif down into images.
convert /home/kali/doing/9266eadf353d4ada94ededaeb96d0c50.gif /home/kali/doing/1/flag.pngThe following procedure is performed.
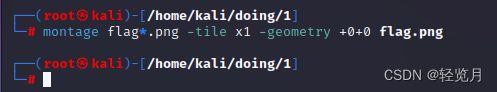
Then I switch to the picture directory here and run the following command to stitch all the pictures together.
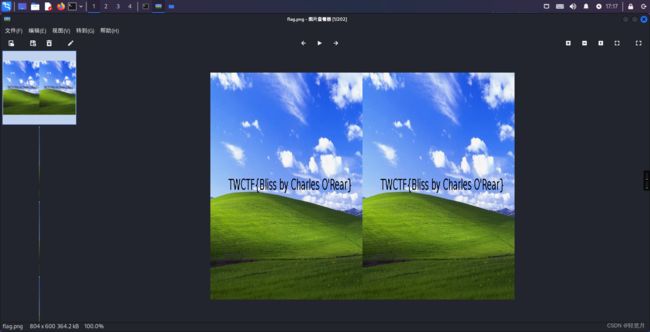
cd /home/kali/doing/1/montage flag*.png -tile x1 -geometry +0+0 flag.pngFinally I got the result.
TWO IgniteMe
攻防世界 (xctf.org.cn)![]() https://adworld.xctf.org.cn/challenges/problem-set-index?id=1
https://adworld.xctf.org.cn/challenges/problem-set-index?id=1
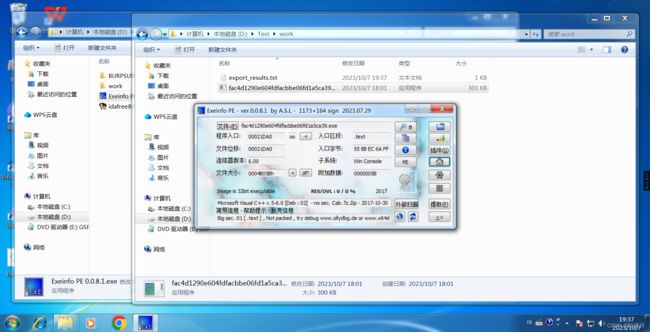
All I got here was an exe program.
Exeinfo PE
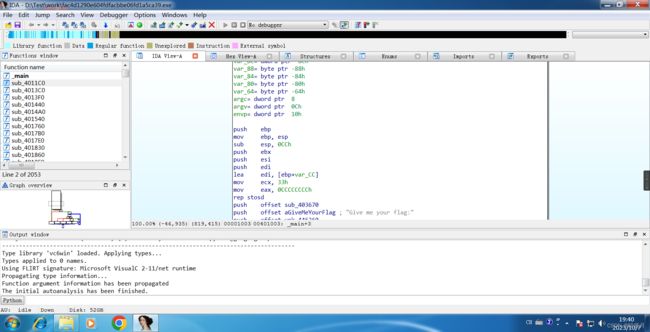
IDA
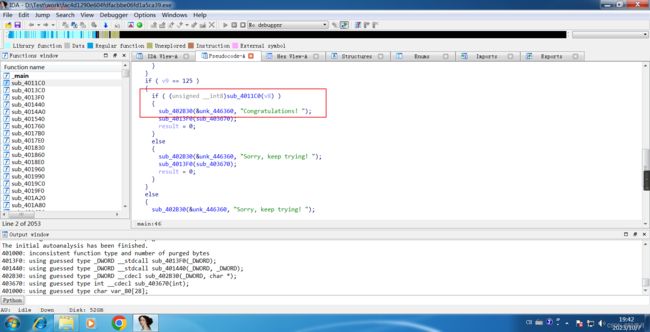
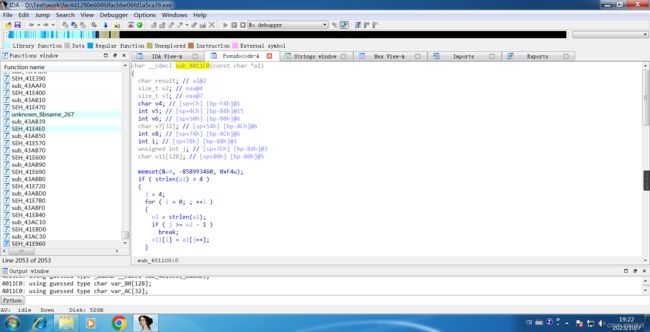
Open the F5 decompile main program using IDA-32.
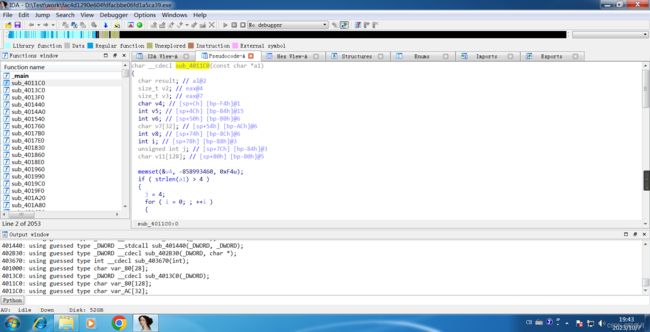
Click sub_4011C0() for a deeper look.
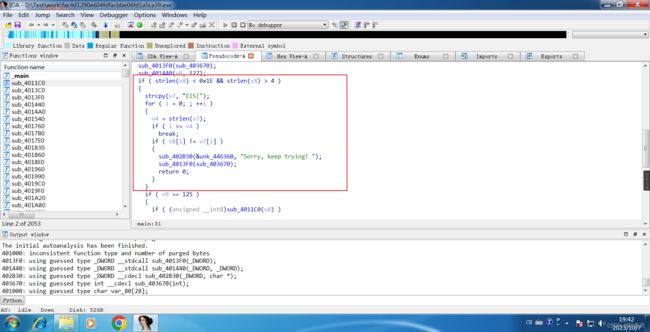
char __cdecl sub_4011C0(const char *a1)
{
char result; // al@2
size_t v2; // eax@4
size_t v3; // eax@7
char v4; // [sp+Ch] [bp-F4h]@1
int v5; // [sp+4Ch] [bp-B4h]@15
int v6; // [sp+50h] [bp-B0h]@6
char v7[32]; // [sp+54h] [bp-ACh]@6
int v8; // [sp+74h] [bp-8Ch]@6
int i; // [sp+78h] [bp-88h]@3
unsigned int j; // [sp+7Ch] [bp-84h]@3
char v11[128]; // [sp+80h] [bp-80h]@5
memset(&v4, -858993460, 0xF4u);
if ( strlen(a1) > 4 )
{
j = 4;
for ( i = 0; ; ++i )
{
v2 = strlen(a1);
if ( j >= v2 - 1 )
break;
v11[i] = a1[j++];
}
v11[i] = 0;
v8 = 0;
v6 = 0;
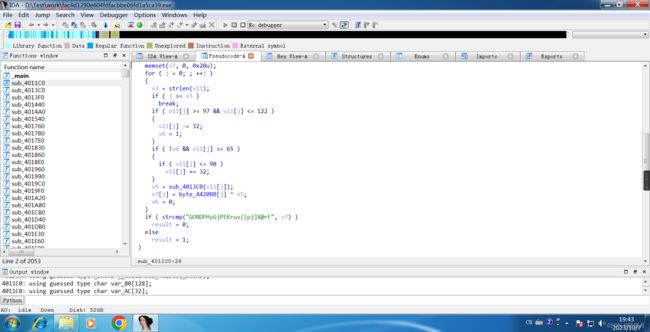
memset(v7, 0, 0x20u);
for ( j = 0; ; ++j )
{
v3 = strlen(v11);
if ( j >= v3 )
break;
if ( v11[j] >= 97 && v11[j] <= 122 )
{
v11[j] -= 32;
v6 = 1;
}
if ( !v6 && v11[j] >= 65 )
{
if ( v11[j] <= 90 )
v11[j] += 32;
}
v5 = sub_4013C0(v11[j]);
v7[j] = byte_4420B0[j] ^ v5;
v6 = 0;
}
if ( strcmp("GONDPHyGjPEKruv{{pj]X@rF", v7) )
result = 0;
else
result = 1;
}
else
{
result = 0;
}
return result;
}------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Just a little test before.
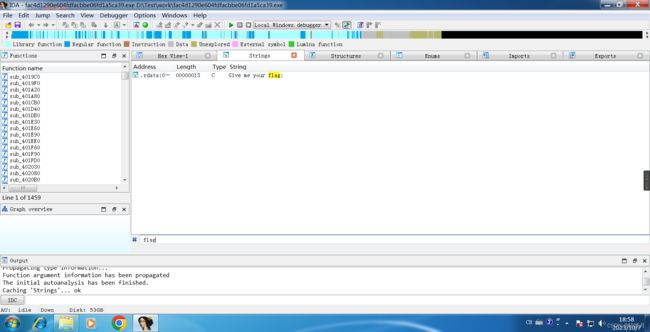
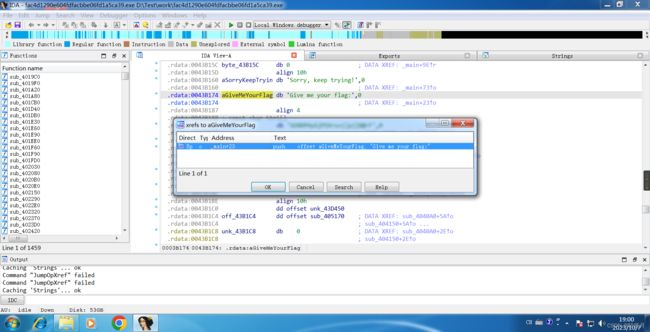
Shift + F2 , Ctrl + F , input ' flag '
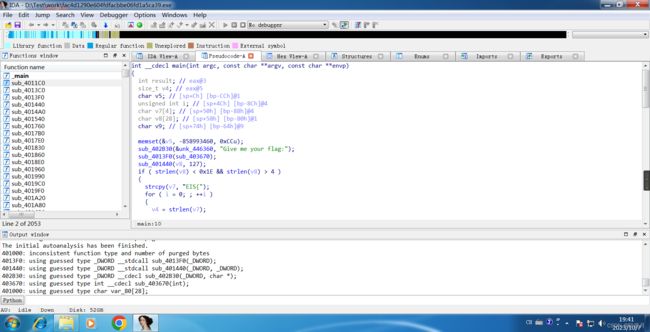
Press x cross-reference to jump to the main code.
Then press Tab decompile to get pseudo c code.
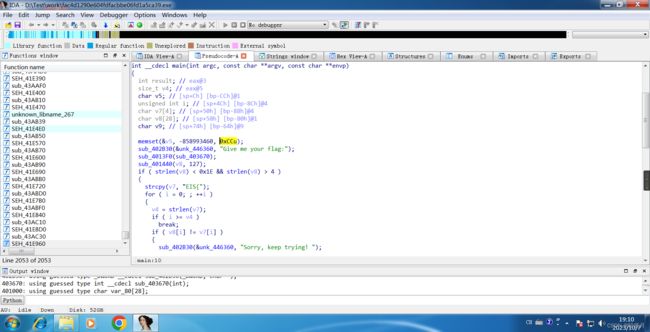
Enter the sub_4011C0(v6) function.
---------------------------------------------------------------------------------------------------------------------------------
---------------------------------------------------------------------------------------------------------------------------------
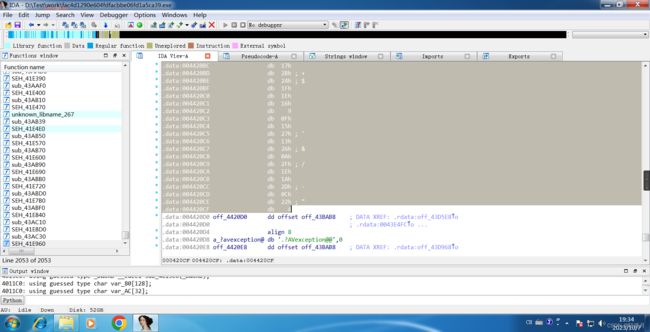
Click byte_4420B0 to extract the data, select the data.
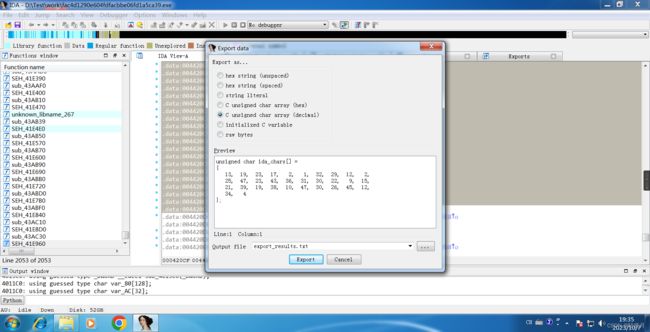
Press Shift + E to extract data, which is extracted in decimal.
Write a program:
#include
int main() {
const char* str = "GONDPHyGjPEKruv{{pj]X@rF";
unsigned char byte_4420B0[] = {
13, 19, 23, 17, 2, 1, 32, 29, 12, 2,
25, 47, 23, 43, 36, 31, 30, 22, 9, 15,
21, 39, 19, 38, 10, 47, 30, 26, 45, 12,
34, 4};
char flag[31] = "EIS{";
int index = 4;
for (size_t i = 0; i < 24; i++) {
flag[index] = ((str[i] ^ byte_4420B0[i]) - 72) ^ 0x55;
if (flag[index] >= 97 && flag[index] <= 122) {
flag[index] -= 32;
} else if (flag[index] >= 65 && flag[index] <= 90) {
flag[index] += 32;
}
index++;
}
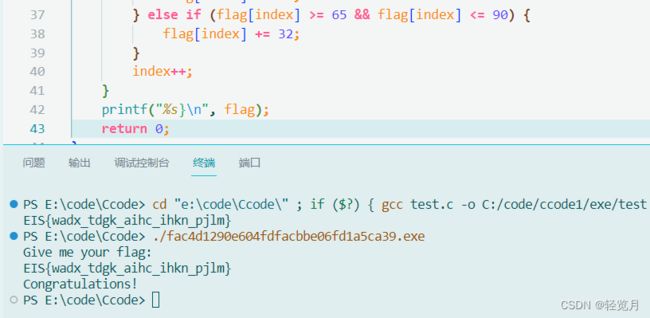
printf("%s}\n", flag);
return 0;
}
Get the flag:
Attached: Some tools used: