【ELK】系列入门教程一,边学边记之Elasticsearch入门与使用教程
【ELK】系列入门教程一,边学遍记之Elasticsearch入门与使用教程
- 一、Elasticsearch介绍
- 二、安装并运行
-
- 1、Windows安装
- 2、Docker安装
- 三、确认安装成功
- 四、使用Elasticsearch
-
- 1、数据结构
- 2、索引Index
- 2、类型Type
- 3、文档内容Document
- 五、安全认证
- 六、更多姿势请自行学习
一、Elasticsearch介绍
- 本人学习过程中使用了多个版本,高版本与低版本之间区别还是有的,像高版本默认开启https,安全认证等等。
来看教程又不是读小说的,略略略
有兴趣自己去看官网
Elasticsearch中文文档
Elastic官网
Elastic文档
可以的话,中文文档先大致浏览一遍
二、安装并运行
1、Windows安装
中文文档中使用Dos命令,说白了就是解压即安装成功。
进入安装目录,双击elasticsearch.bat批处理文件即可
不知道是不是因为路径不能有中文问题,我Windows启动不起来,同事的电脑可以,不去深究。
2、Docker安装
Docker基础知识请浏览我之前的文章。
//docker run -id --name=elasticsearch -e "ELASTIC_PASSWORD=123456" -e "discovery.type=single-node" -e "ES_JAVA_OPTS=-Xms256m -Xmx256m" -p 9200:9200 -p 9300:9300 -v /etc/elasticsearch/elasticsearch.yml:/usr/share/elasticsearch/config/elasticsearch.yml elasticsearch:8.7.1
docker run -id --name=elasticsearch -e "ES_JAVA_OPTS=-Xms256m -Xmx256m" -p 9200:9200 -p 9300:9300 elasticsearch
//参数说明
9300 端口为Elasticsearch 系统端口,
9200 端口为Elasticsearch REST APIs 端口。
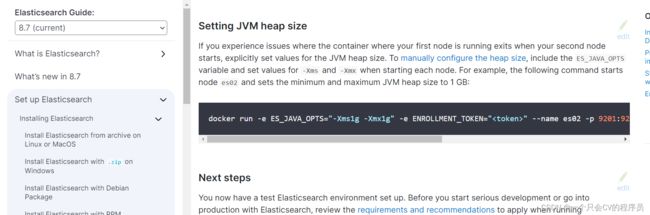
-e "ES_JAVA_OPTS=-Xms256m -Xmx256m" 参数表示设置最小/大堆栈,对应jvm.options文件配置
-e "discovery.type=single-node" 类型为单点,高版本才有
-e "ELASTIC_PASSWORD=123456" 给elastic用户设置密码123456
此段为可跳过部分
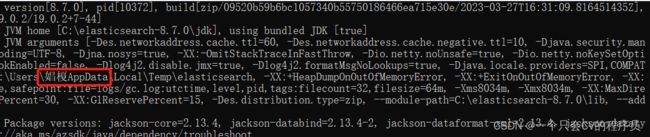
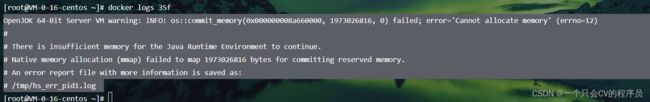
我第一次没加ES_JAVA_OPTS参数,就遇到问题,容器自动停止,查看日志
由于进不去容器,无法查看jvm.options配置,再次去读官网说明,运行容器添加参数
–e “ES_JAVA_OPTS=-Xms256m -Xmx256m”
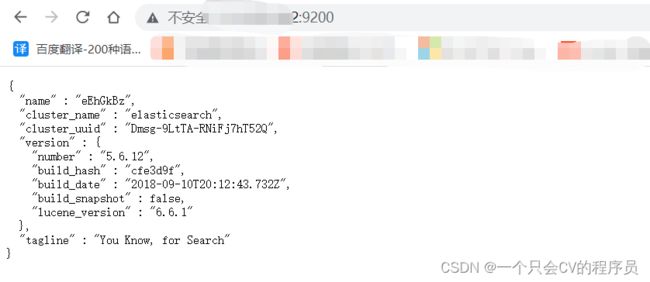
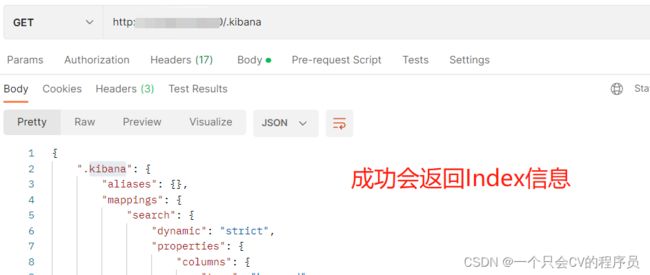
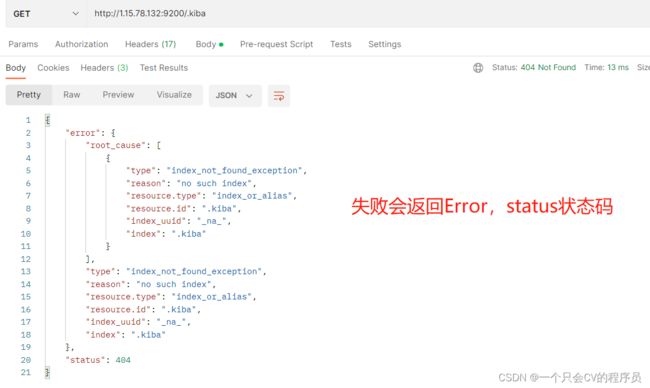
三、确认安装成功
四、使用Elasticsearch
运行为容器时,参数说明9200端口为restfull api地址,那么就可以进行get,post等等请求
更多用法请参考: REST APIs说明
1、数据结构
使用前需要先了解数据结构:
Elasticsearch:本身可以认为是一台webApi、sql服务器。可以单点集群部署,Cluster:集群
Index:索引,可以认为是api的控制器、数据库的db库注意全小写
Type:类型,可以认为是api控制器内的function、数据库中的表
Document:文档、内容,可以认为是api的出/入参、数据库中的数据行
Field:字段、属性,这个没什么可比喻的
请求示例:
http://服务器IP:9200/{Index}/{Type}/{id}
{整个Json=Document}
{
“Field”:“value”
}
相信悟性高的同学已经发出“噢,原来如此了。”
是不是很熟悉?我们拿api路由与其对比:
api_Route:api/{controller}/{action}/{id}
ES_Route:ES/{Index}/{Type}/{id}
当然也不能这么绝对,只用来理解,因为还有很多保留命令会使路由变化,先给自己挖个坑,下面填坑。
2、索引Index
Elasticsearch本身服务器已经装好,直接开始使用
对于索引操作相当于Restfull控制器,HTTP请求:ES/[Index]
用法多种多样,下面只记录简单的curd
a、查看索引Index
//GET请求,索引名称支持模糊查询,相当于sql like,[%]换成[*]
http://服务器IP:9200/<*IndexName*>
b、创建索引Index
//PUT
http://服务器IP:9200/
c、删除索引Index
//DELETE
http://服务器IP:9200/
d、打开关闭索引Index
//POST
http://服务器IP:9200//_open
http://服务器IP:9200//_close
填坑,_开头为保留命令/保留关键字
2、类型Type
Elasticsearch并没有提供直接对type的操作,或者我没找到,略略略~
3、文档内容Document
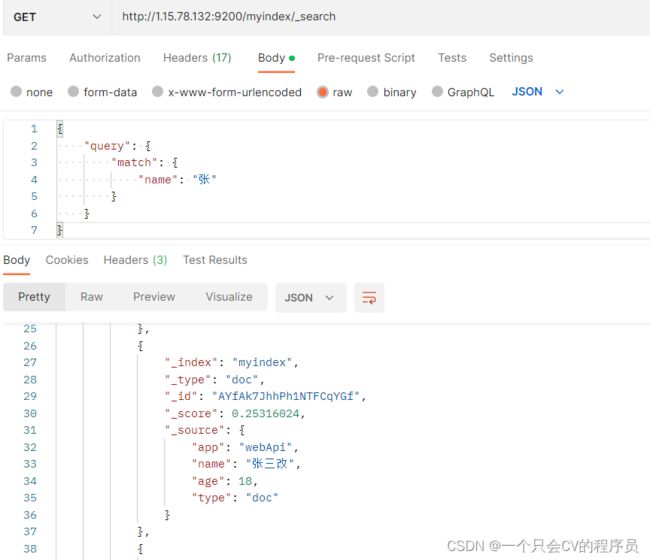
a、查询所有文档
//GET 查询索引下的所有
http://服务器IP:9200/myindex/_search
//BODY为Json格式的条件、排序、分页等等
{
"query": { "match_all": {} },
"sort": [
{ "account_number": "asc" }
]
}
文档中的示例
填坑,_开头为保留命令/保留关键字
b、查询具体文档
//GET
http://服务器IP:9200/myindex//
c、新增修改文档
//PUT
http://服务器IP:9200/myindex//
//POST
http://服务器IP:9200/myindex//[id]
//文档内容
{
"app":"webApi",
"name":"张三",
"age":18,
"type":"doc"
}
PUT请求id为必填,如果id不存在新增,否则修改。表现为返回示例中result=updated,created=false
POST请求id为可选项,如果不传只会新增,返回示例中_id=AYfA*****, result只会=created。 如果传则修改或者新增,规则同PUT请求。
//返回示例
{
"_index": "myindex",
"_type": "doc",
"_id": "2",
"_version": 1,
"result": "created",
"_shards": {
"total": 2,
"successful": 1,
"failed": 0
},
"created": true
}
d、删除文档
//DELETE
http://服务器IP:9200/myindex//
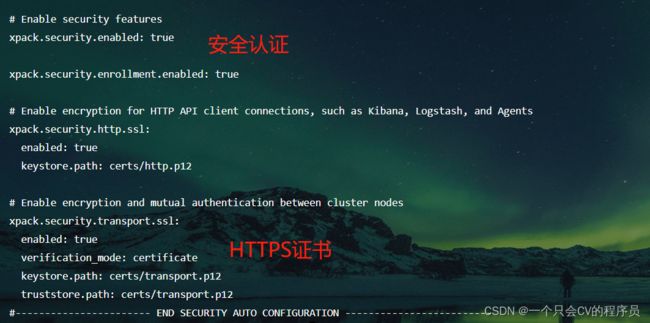
五、安全认证
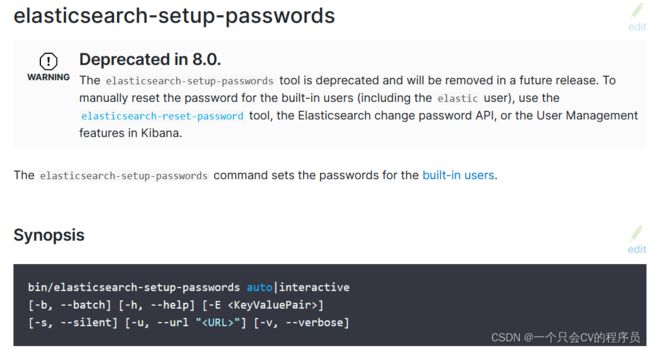
//auto 为所有内置账户生产安全性较高的密码
//interactive 交互形式设置,用户输入密码,再次输入密码。
bin/elasticsearch-setup-passwords auto|interactive
遇到了大坑,执行elasticsearch-setup-passwords auto|interactive 没有反应。
08:18:41.526 [main] WARN org.elasticsearch.common.ssl.DiagnosticTrustManager - failed to establish trust with server at [172.18.0.5]; the server provided a certificate with subject name [CN=99e2090e500c], fingerprint [f99ab02c579805573f6b1e4c8813c1681047d8f4], no keyUsage and extendedKeyUsage [serverAuth]; the certificate is valid between [2023-05-12T07:13:35Z] and [2025-05-11T07:13:35Z] (current time is [2023-05-12T08:18:41.523023369Z], certificate dates are valid); the session uses cipher suite [TLS_AES_256_GCM_SHA384] and protocol [TLSv1.3]; the certificate has subject alternative names [DNS:localhost,IP:172.18.0.2,IP:0:0:0:0:0:0:0:1,IP:127.0.0.1,IP:fe80:0:0:0:42:acff:fe12:2,DNS:99e2090e500c]; the certificate is issued by [CN=Elasticsearch security auto-configuration HTTP CA]; the certificate is signed by (subject [CN=Elasticsearch security auto-configuration HTTP CA] fingerprint [041b5bd45226075c2eb4374ef085be3ae9b14c4e] {trusted issuer}) which is self-issued; the [CN=Elasticsearch security auto-configuration HTTP CA] certificate is trusted in this ssl context ([xpack.security.http.ssl (with trust configuration: Composite-Trust{JDK-trusted-certs,StoreTrustConfig{path=certs/http.p12, password=<non-empty>, type=PKCS12, algorithm=PKIX}})])
java.security.cert.CertificateException: No subject alternative names matching IP address 172.18.0.5 found
at sun.security.util.HostnameChecker.matchIP(HostnameChecker.java:160) ~[?:?]
at sun.security.util.HostnameChecker.match(HostnameChecker.java:101) ~[?:?]
at sun.security.ssl.X509TrustManagerImpl.checkIdentity(X509TrustManagerImpl.java:457) ~[?:?]
at sun.security.ssl.X509TrustManagerImpl.checkIdentity(X509TrustManagerImpl.java:431) ~[?:?]
at sun.security.ssl.X509TrustManagerImpl.checkTrusted(X509TrustManagerImpl.java:237) ~[?:?]
at sun.security.ssl.X509TrustManagerImpl.checkServerTrusted(X509TrustManagerImpl.java:132) ~[?:?]
at org.elasticsearch.common.ssl.DiagnosticTrustManager.checkServerTrusted(DiagnosticTrustManager.java:80) ~[?:?]
at sun.security.ssl.CertificateMessage$T13CertificateConsumer.checkServerCerts(CertificateMessage.java:1302) ~[?:?]
at sun.security.ssl.CertificateMessage$T13CertificateConsumer.onConsumeCertificate(CertificateMessage.java:1195) ~[?:?]
at sun.security.ssl.CertificateMessage$T13CertificateConsumer.consume(CertificateMessage.java:1138) ~[?:?]
at sun.security.ssl.SSLHandshake.consume(SSLHandshake.java:393) ~[?:?]
at sun.security.ssl.HandshakeContext.dispatch(HandshakeContext.java:469) ~[?:?]
at sun.security.ssl.HandshakeContext.dispatch(HandshakeContext.java:447) ~[?:?]
at sun.security.ssl.TransportContext.dispatch(TransportContext.java:201) ~[?:?]
at sun.security.ssl.SSLTransport.decode(SSLTransport.java:172) ~[?:?]
at sun.security.ssl.SSLSocketImpl.decode(SSLSocketImpl.java:1506) ~[?:?]
at sun.security.ssl.SSLSocketImpl.readHandshakeRecord(SSLSocketImpl.java:1421) ~[?:?]
at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:455) ~[?:?]
at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:426) ~[?:?]
at sun.net.www.protocol.https.HttpsClient.afterConnect(HttpsClient.java:587) ~[?:?]
at sun.net.www.protocol.https.AbstractDelegateHttpsURLConnection.connect(AbstractDelegateHttpsURLConnection.java:187) ~[?:?]
at sun.net.www.protocol.https.HttpsURLConnectionImpl.connect(HttpsURLConnectionImpl.java:142) ~[?:?]
at org.elasticsearch.xpack.core.common.socket.SocketAccess.lambda$doPrivileged$0(SocketAccess.java:42) ~[?:?]
at java.security.AccessController.doPrivileged(AccessController.java:571) ~[?:?]
at org.elasticsearch.xpack.core.common.socket.SocketAccess.doPrivileged(SocketAccess.java:41) ~[?:?]
at org.elasticsearch.xpack.core.security.CommandLineHttpClient.execute(CommandLineHttpClient.java:178) ~[?:?]
at org.elasticsearch.xpack.core.security.CommandLineHttpClient.execute(CommandLineHttpClient.java:112) ~[?:?]
at org.elasticsearch.xpack.security.tool.BaseRunAsSuperuserCommand.checkClusterHealthWithRetries(BaseRunAsSuperuserCommand.java:214) ~[?:?]
at org.elasticsearch.xpack.security.tool.BaseRunAsSuperuserCommand.execute(BaseRunAsSuperuserCommand.java:127) ~[?:?]
at org.elasticsearch.common.cli.EnvironmentAwareCommand.execute(EnvironmentAwareCommand.java:54) ~[elasticsearch-8.7.1.jar:8.7.1]
at org.elasticsearch.cli.Command.mainWithoutErrorHandling(Command.java:85) ~[elasticsearch-cli-8.7.1.jar:8.7.1]
at org.elasticsearch.cli.Command.main(Command.java:50) ~[elasticsearch-cli-8.7.1.jar:8.7.1]
at org.elasticsearch.launcher.CliToolLauncher.main(CliToolLauncher.java:64) ~[cli-launcher-8.7.1.jar:8.7.1]
ERROR: Failed to determine the health of the cluster.
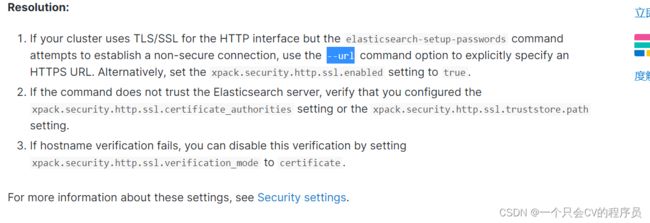
- 官方解释说开启了HTTPS要显式请求
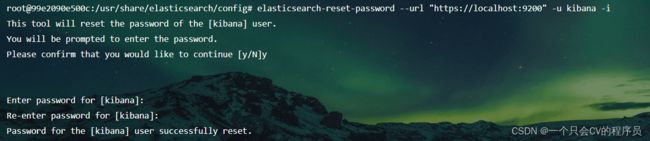
//修改密码 -i 交互设置
elasticsearch-reset-password -u elastic -i --url https://localhost:9200
elasticsearch-reset-password -u kibana -i --url https://localhost:9200
六、更多姿势请自行学习
【ELK】系列入门教程一,边学边记之Elasticsearch入门与使用教程
【ELK】系列入门教程二,边学边记之Kibana入门与使用教程
【ELK】系列入门教程三,边学边记之自定义logger写入Es