笔记Kubernetes核心技术-之Controller
2、Controller
2.1、概述
在集群上管理和运行容器的对象,控制器(也称为:工作负载),Controller实际存在的,Pod是抽象的;
2.2、Pod和Controller关系
2.3、常用控制器(deployment)
2.3.1、应用场景
- 部署无状态应用(例如:nginx);
- 管理Pod和ReplicaSet;
- 部署,滚动升级等功能;
- 应用场景:web服务,微服务;
2.3.2、通过yaml文件部署应用
- 使用yaml文件部署应用
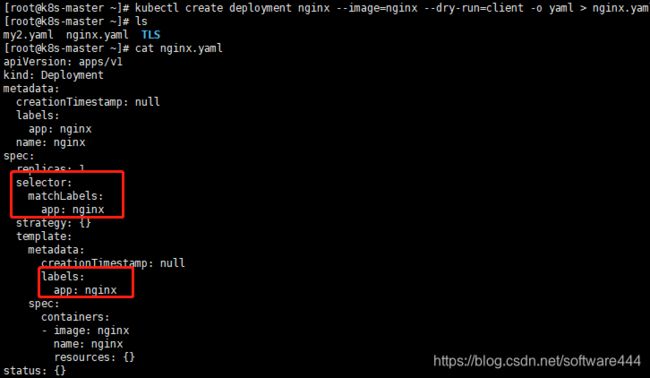
#创建并导出yaml文件
kubectl create deployment nginx --image=nginx --dry-run=client -o yaml > nginx.yaml
#通过yaml文件部署应用
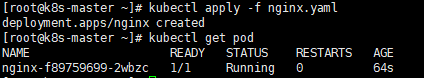
kubectl apply -f nginx.yaml
#查看状态
kubectl get pod
- 对外发布(暴露端口号)
#暴露端口号(target-port=80)
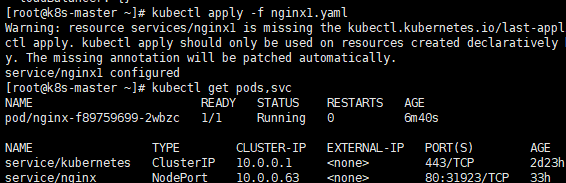
kubectl expose deployment nginx --port=80 --type=NodePort --target-port=80 --name nginx -o yaml > nginx1.yaml
#通过yaml文件暴露端口
kubectl apply -f nginx1.yaml
2.4、应用升级回滚和弹性伸缩
2.4.1、应用升级
升级过程中保证服务不中断,会一个Pod一个Pod逐步替换,升级实质image版本升级;
(1)先指定应用版本部署,这里指定nginx版本为1.14

#创建指定版本应用
kubectl apply -f nginx1.yaml

在Node节点查看镜像,会看到下载的1.14版本;

(2)应用升级,此处nginx版本为1.15
#nginx:第一个表示名称,nginx第二个表示镜像
kubectl set image deployment nginx nginx=nginx:1.15

在Node节点查看镜像,会看到下载的1.15版本;

(3)查看升级状态
kubectl rollout status deployment nginx
2.4.2、应用版本回滚
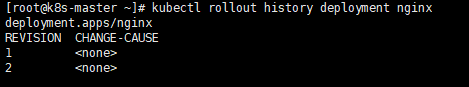
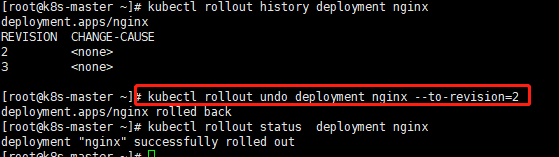
(1)查看历史版本
kubectl rollout history deployment nginx
- 回滚到上一个版本
#回滚到上一个版本
kubectl rollout undo deployment nginx
#查看回滚后状态
kubectl rollout status deployment nginx
- 回滚到指定版本
#回滚到指定版本
kubectl rollout undo deployment nginx --to-revision=2
2.4.3、应用弹性伸缩
#弹性伸缩命令
kubectl scale deployment nginx --replicas=5
2.5、部署有状态应用(StatefulSet)
2.5.1、无状态和有状态
(1)无状态
- 认为Pod都是一样;
- 无顺序要求;
- 不用考虑在任意node运行;
- 可随意伸缩和控制;
(2)有状态 - 上面的因素都需要考虑到;
- 每个Pod都是独立的,保持Pod启动顺序和唯一性;
- 唯一的网络标识符,持久存储;
- 有序,比如:mysql主从;
2.5.2、部署有状态应用
(1)SatefulSet部署有状态应用
无头service,指ClusterIP:none。
- 无头的service
cat < sts.yaml << EOF
apiVersion: v1
kind: Service
metadata:
creationTimestamp: null
labels:
app: nginx
name: nginx
spec:
ports:
- port: 80
name: web
selector:
app: nginx
clusterIP: None
---
apiVersion: apps/v1
kind: StatefulSet
metadata:
name: nginx-statefulset
namespace: default
spec:
serviceName: nginx
replicas: 3
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- image: nginx:latest
name: nginx
ports:
- containerPort: 80
EOF
#查看服务
kubectl get svc
#删除statefulset
kubectl delete statefulset --all
(2)deployment和statefulset区别:
- statefulset特点
有唯一标识:根据主机名 + 按照一定规则生成域名;
每个pod有唯一主机名,唯一域名,格式:主机名称.service名称.名称空间.svc.cluster.local
nginx-statefulset-0.nginx.default.svc.cluster.local
2.6、部署守护进程(DaemonSet)
让每个node上运行同一个pod,新加入的node也同样运行在一个pod里面;
例如:在每个node节点安装数据采集工具(适用场景:每台虚拟机(Node) 进行日志采集);
- 创建daemonset文件
cat < daemon.yaml << EOF
apiVersion: apps/v1
kind: DaemonSet
metadata:
name: ds-test
labels:
app: filebeat
namespace: default
spec:
selector:
matchLabels:
app: filebeat
template:
metadata:
labels:
app: filebeat
spec:
containers:
- name: logs
image: nginx
ports:
- containerPort: 80
volumeMounts:
- name: varlog
mountPath: /tmp/log
volumes:
- name: varlog
hostPath:
path: /var/log
EOF
- 创建守护进程pod
#执行daemon.yaml文件
kubectl apply -f deamon.yaml
kubectl get pods
- 进入容器查看日志
kubectl get pods
#进入容器
kubectl exec -it ds-test-bg657 bash
#查看日志
ls /tmp/log
#退出
exit
2.6、一次性任务和定时任务
2.6.1、Job(一次性任务)
- 创建job.yaml文件
#创建job文件,计算PI的值
cat < job.yaml <<EOF
apiVersion: batch/v1
kind: Job
metadata:
name: pi-calculate
namespace: default
spec:
template:
spec:
containers:
- name: pi
image: perl
command: ["perl", "-Mbignum=bpi", "-wle", "print bpi(2000)"]
restartPolicy: Never
backoffLimit: 4
EOF
- 创建job
#创建job,应用yaml文件
$kubectl apply -f job.yaml
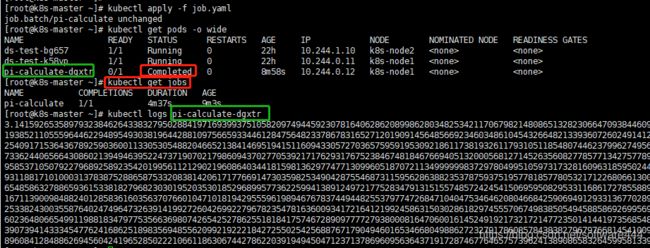
#Node: 【Completed】表示一次性任务完成
$kubectl get pods -o wide
#查看一次性job
$kubectl get jobs
#查看日志: 格式: kubectl logs pod名称
$kubectl logs pi-calculate-dgxtr
#删除job
$kubectl delete -f job.yaml
2.6.2、CornJob(定时任务)
- 创建cronjob.yaml文件
cat < cronjob.yaml << EOF
apiVersion: batch/v1beta1
kind: CronJob
metadata:
name: hello-world
namespace: default
spec:
schedule: "*/1 * * * *"
jobTemplate:
spec:
template:
spec:
containers:
- name: hello-world
image: busybox
args:
- /bin/sh
- -c
- date; echo Hello from the kubernetes
restartPolicy: OnFailure
EOF
- 创建cronjob
#创建cronjob,应用yaml文件
$kubectl apply -f cronjob.yaml
#Node: 【Completed】表示一次性任务完成,此处会定时输出
$kubectl get pods -o wide
#查看一次性job
$kubectl get cronjobs
#查看日志: 格式: kubectl logs pod名称
$kubectl logs hello-world-1624xxx
#删除job
$kubectl delete -f cronjob.yaml
4、配置管理
4.1、Secret
作用:存储加密数据到etcd,让Pod容器以变量或者挂载Volume方式进行访问数据,适用场景:凭证(认证)。
(1)创建secret加密数据
- base64 编码用户名或密码
#编码base64
echo -n 'admin' | base64
- 创建加密数据文件
cat < secret.yaml << EOF
apiVersion: v1
kind: Secret
metadata:
name: mysecret
type: Opaque
data:
username: YWRtaW4=
password: MWYyZDF1MmU2N2Rm
EOF
- 生成加密数据
$kubectl create -f secret.yaml
#获取加密数据,注此处加密名称为:mysecret
$kubectl get secret
#辅助命令:kubectl delete secret --all (删除secret)
- 创建带有加密的pod yaml文件
环境变量名称分别为:SECRET_USERNAME,SECRET_PASSWORD
加密名称(name):mysecret,和(1)中mysecret要相同;
cat < secret-val.yaml << EOF
apiVersion: v1
kind: Pod
metadata:
name: mypod
spec:
containers:
- name: nginx
image: nginx
env:
- name: SECRET_USERNAME
valueFrom:
secretKeyRef:
name: mysecret
key: username
- name: SECRET_PASSWORD
valueFrom:
secretKeyRef:
name: mysecret
key: password
EOF
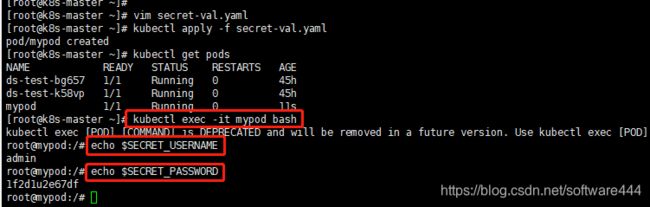
- 创建pod并访问加密数据
$kubectl apply -f secret-val.yaml
$kubectl get pods
#进入pod
$kubectl exec -it mypod bash
#查看环境变量
echo $SECRET_USERNAME
echo $SECRET_PASSWORD
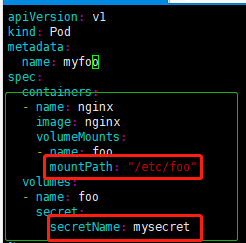
- 创建带有加密的pod yaml文件
加密名称(secretName):mysecret,和(1)中mysecret要相同;
挂载目录(mountPath):容器/etc/foo目录;
cat < secret-vol.yaml << EOF
apiVersion: v1
kind: Pod
metadata:
name: myfoo
spec:
containers:
- name: nginx
image: nginx
volumeMounts:
- name: foo
mountPath: "/etc/foo"
volumes:
- name: foo
secret:
secretName: mysecret
EOF
- 创建pod并访问加密数据
$kubectl apply -f secret-vol.yaml
$kubectl get pods
#进入pod
$kubectl exec -it myfoo bash
#进入目录
ls /etc/foo
cd /etc/foo
#查看文件
cat password
cat username
4.2、ConfigMap
作用:存储不加密数据到etcd,让Pod容器以变量或者挂载Volume方式进行访问数据,适用场景:配置文件(IP、端口号、不加密的用户名和密码)。
4.2.1、挂载Volume方式访问
(1)创建配置文件
cat < redis.properties << EOF
redis.host=127.0.0.1
redis.port=6379
redis.password=123456
EOF
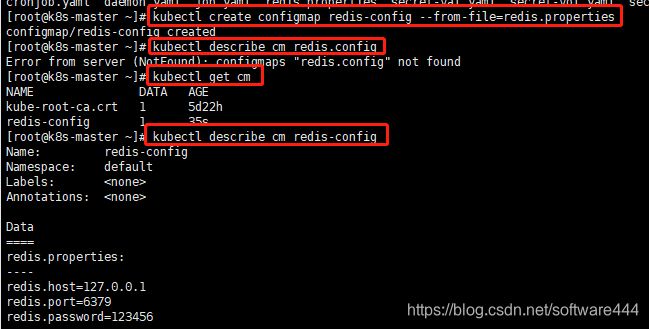
(2)创建configmap(名称:redis-config)
#从配置文件创建configmap
$kubectl create configmap redis-config --from-file=redis.properties
#获取cm(configmap)
$kubectl get cm
#查看cm(configmap)
$kubectl describe cm redis-config
#辅助命令:kubectl delete cm --all 删除所有cm
- 创建cmpod yaml文件
mountPath:将上面redis.properties文件挂载到/etc/config目录;
command:输入redis.properties信息;
name:名称redis-config;
cat < cm.yaml << EOF
apiVersion: v1
kind: Pod
metadata:
name: cmpod
spec:
containers:
- name: busybox
image: busybox
command: ["/bin/sh", "-c", "cat /etc/config/redis.properties"]
volumeMounts:
- name: config-volume
mountPath: "/etc/config"
volumes:
- name: config-volume
configMap:
name: redis-config
restartPolicy: Never
EOF
- 创建pod以volume挂载并输出配置
$kubectl apply -f cm.yaml
$kubectl get pods
#查看日志,Completed状态,只能以查看日志方式,不能进入容器
$kubectl logs cmpod
4.2.2、变量方式访问
(1)以变量方式挂载到Pod容器
- 创建cm yaml文件
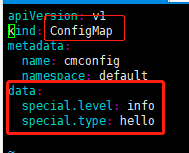
变量名称为:special.level,special.type
kind:类型为ConfigMap
name:名称为cmconfig
cat < cmconfig.yaml << EOF
apiVersion: v1
kind: ConfigMap
metadata:
name: cmconfig
namespace: default
data:
special.level: info
special.type: hello
EOF
cat < cmconfig-var.yaml << EOF
apiVersion: v1
kind: Pod
metadata:
name: cmvarpod
spec:
containers:
- name: busybox
image: busybox
command: ["/bin/sh", "-c", "echo $(LEVEL) $(TYPE)"]
env:
- name: LEVEL
valueFrom:
configMapKeyRef:
name: cmconfig
key: special.level
- name: TYPE
valueFrom:
configMapKeyRef:
name: cmconfig
key: special.type
restartPolicy: Never
EOF

输出变量special.level和special.type值

5、集群安全机制
5.1、概述
(1)访问K8s集群资源的时候,需要经过三个步骤完成具体操作;
- 认证
传输安全:对外不暴露8080端口,只能内部访问,对外使用端口6443;
认证方式(客户端身份认证常用方式):https证书认证,基于ca证书;
http token认证,通过token识别用户;
http基本认证,用户名+密码认证,使用较少; - 鉴权(授权)
基于RBAC进行鉴权操作(基于角色访问控制); - 准入控制
就是准入控制器的列表,如果列表中找到请求内容则通过,没有拒绝;

(2)访问集群时候,都需要经过apiserver,apiserver做统一协调,类似门卫职责,在访问过程中需要证书、token、或者用户名+密码,进行相关操作和授权,如果访问Pod还需要serviceAccount。
5.2、RBAC
基于角色的访问控制;
(1)角色
- role:针对特定的命名空间访问权限
- ClusterRole:针对所有命名空间访问权限
(2)角色绑定
- roleBinding:角色绑定到主体;
- ClusterRoleBinding:集群角色绑定到主体;
(3)主体
5.3、RBAC实现鉴权
5.3.1、创建命名空间
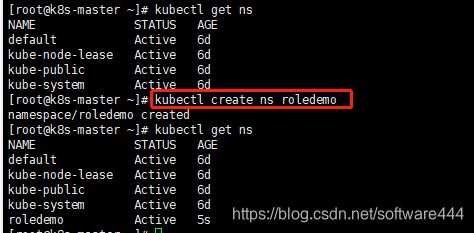
#查看命名空间
$kubectl get ns
#创建命名空间,名称为roledemo
$kubectl create ns roledemo
#在namespace(roledemo)下创建pod
$kubectl run nginx --image=nginx -n roledemo
#查看指定命名空间下pod
$kubectl get pods -n roledemo
cat < rbac-role.yaml << EOF
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: pod-reader
namespace: roledemo
rules:
- apiGroups: [""] # "" indicates the core API group
resources: ["pods"]
verbs: ["get", "watch", "list"]
EOF
#在命名空间中创建角色
$kubectl apply -f rbac-role.yaml
#查看命名空间下角色
$kubectl get role -n roledemo
#辅助命令:kubectl get role 查看所有命名空间角色
cat < rbac-rolebinding.yaml << EOF
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: read-pods
namespace: roledemo
subjects:
- kind: User
name: ["pods"]
verbs: ["get", "watch", "list"]
EOF