Kubernetes-Ingress服务、ingress部署、域名访问、加密认证、重定向
目录:
- 一.Ingress服务简介
- 二.ingress部署
- 三.域名访问+ingress-nginx
-
- 1.编辑ingress.yaml
- 2.编辑svc.yaml
- 3.添加本地解析
- 4.测试
- 5.添加第二个域名
- 6.编辑deployment.yaml
- 7.测试:
- 四.Ingress 加密
-
- 1.配置密钥
- 2.测试:
- 五.Ingress 认证
-
- 1.生成证书
- 2.访问测试:
- 六. 重定向
-
- 1.重定向到 /hostname.html
- 2.根目录重定向到westos
- 3.测试
一.Ingress服务简介
一种全局的、为了代理不同后端 Service 而设置的负载均衡服务,就是 Kubernetes 里的Ingress 服务。
Ingress由两部分组成:Ingress controller和Ingress服务。
Ingress Controller 会根据你定义的 Ingress 对象,提供对应的代理能力。业界常用的各种反向代理项目,比如 Nginx、HAProxy、Envoy、Traefik 等,都已经为Kubernetes 专门维护了对应的 Ingress Controller。
ingress服务的使用必须在策略网络中才能实现,如calico网络
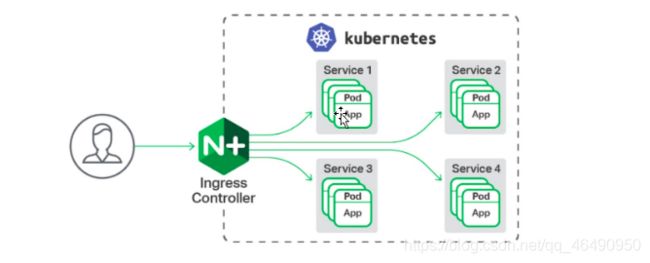
ingress相当于一个7层的负载均衡器,是k8s对反向代理的一个抽象。大概的工作原理也确实类似于Nginx,可以理解成在 Ingress 里建立一个个映射规则 , ingress Controller 通过监听 Ingress这个api对象里的配置规则并转化成 Nginx 的配置(kubernetes声明式API和控制循环) , 然后对外部提供服务。ingress包括:ingress controller和ingress resources
ingress controller:核心是一个deployment,实现方式有很多,比如nginx, Contour, Haproxy, trafik, Istio,需要编写的yaml有:Deployment, Service, ConfigMap, ServiceAccount(Auth),其中service的类型可以是NodePort或者LoadBalancer。
ingress resources:这个就是一个类型为Ingress的k8s api对象了,这部分则是面向开发人员。
二.ingress部署
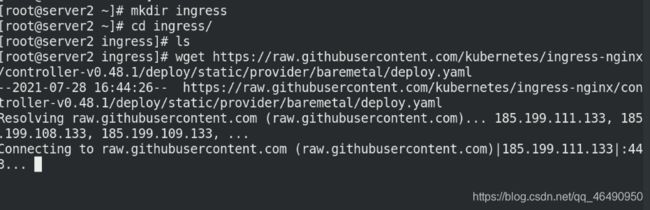
mkdir ingress
cd ingress/
下载所需要的deploy.yaml
vim deploy.yaml
image: ingress-nginx/controller:v0.48.1
image: ingress-nginx/kube-webhook-certgen:v1.5.1
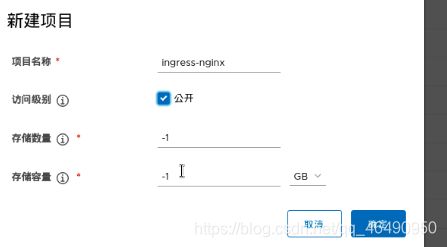
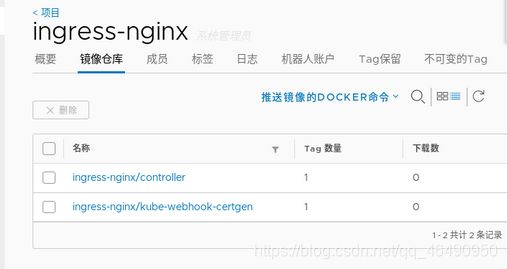
首先在自己的仓库中添加项目ingress-nginx专门存放相关的镜像!
docker pull willdockerhub/ingress-nginx/controller:v0.48.1
docker pull jettech/kube-webhook-certgen:v1.5.1
docker tag reg.westos.org/ingress-nginx/controller:v0.48.1 reg.westos.org/ingress-nginx/controller:v0.48.1
docker tag reg.westos.org/ingress-nginx/kube-webhook-certgen:v1.5.1 reg.westos.org/ingress-nginx/kube-webhook-certgen:v1.5.1
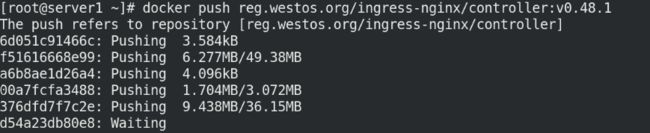
docker push reg.westos.org/ingress-nginx/controller:v0.48.1
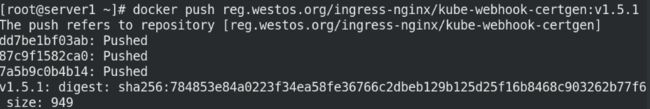
docker push reg.westos.org/ingress-nginx/kube-webhook-certgen:v1.5.1
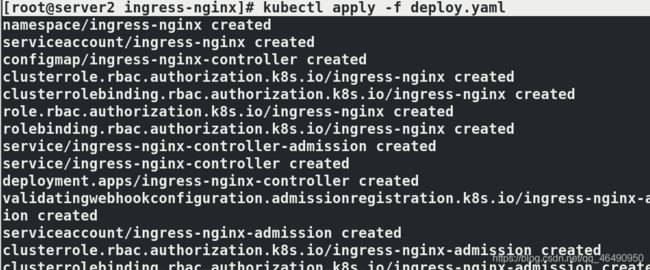
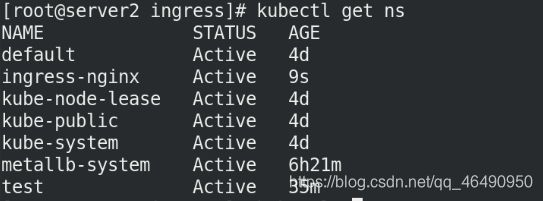
执行deploy.yaml清单,查看ns状态:
kubectl apply -f deploy.yaml
kubectl get ns
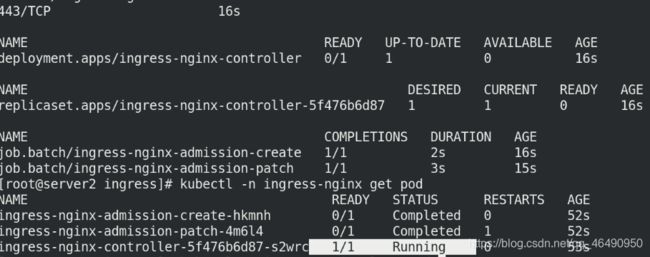
查看ingress-nginx的所有信息,可以看到ingress-nginx-controller已经running
kubectl -n ingress-nginx get all
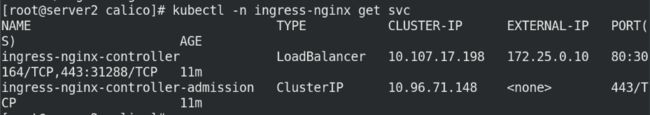
查看svc暴露端口
kubectl -n ingress-nginx get svc
三.域名访问+ingress-nginx
1.编辑ingress.yaml
现在的名字起为ingress-demo
name: ingress-demo
待会增加两个域名的时候需要改编为ingress-nginx,往下看会说到!!
vim ingress.yaml
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-demo
spec:
rules:
- host: www1.westos.org
http:
paths:
- path: /
backend:
serviceName: nginx-svc
servicePort: 80
将之前实验的svc删除,重新执行一个svc节点:
kubectl get svc
kubectl delete svc lb-svc
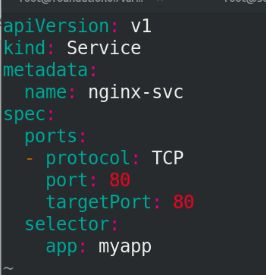
2.编辑svc.yaml
cd
cd pod/
vim svc.yaml
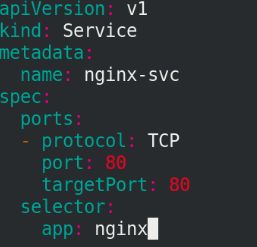
apiVersion: v1
kind: Service
metadata:
name: nginx-svc
spec:
ports:
- protocol: TCP
port: 80
targetPort: 80
selector:
app: myapp
运行svc节点,并查看:
kubectl appy -f svc.yaml
kubectl get svc
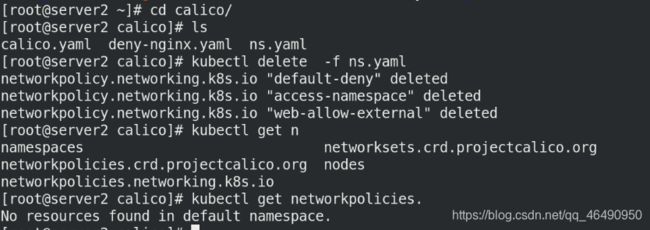
将之前实验网络策略都删掉:
cd
cd calico/
kubectl delete -f ns.yaml
kubectl get networkpolicies.
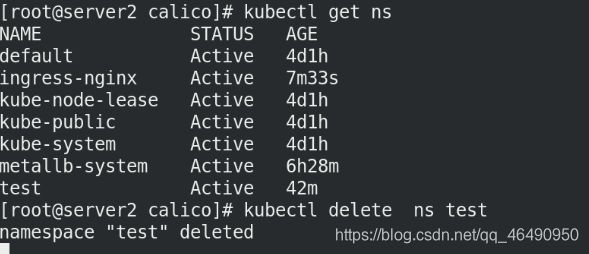
删掉test
kubectl get ns
kubectl delete ns test
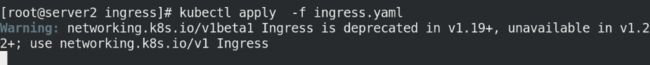
删掉之后。准备执行ingress.yaml清单
cd
cd ingress
kubectl apply -f ingress.yaml
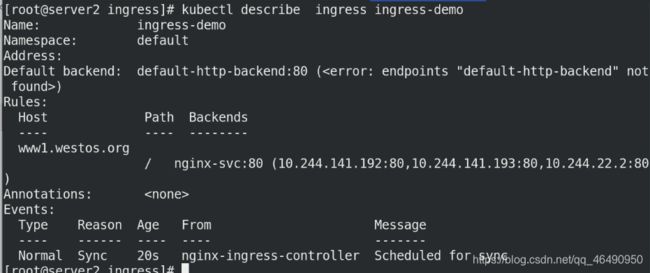
kubectl get ingress
kubectl describe ingress ingress-demo
修改svc配置文件为负载均衡
kubectl -n ingress-nginx edit svc ingress-nginx-controller
type: LoadBalabcer
kubectl -n ingress-nginx get svc
3.添加本地解析
完成之后,我们需要在真机上加上本地解析:
vim /etc/hosts
172.25.0.10 www1.westos.org
4.测试
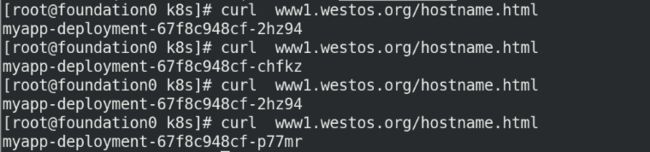
访问域名,观察能否实现负载均衡!
ping www1.westos.org
curl www1.westos.org/hostname.html
5.添加第二个域名
此时需要将前面的name改变
name: ingress-demo 改为:ingress.nginx
vim ingress.yaml
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-nginx
spec:
rules:
- host: www1.westos.org
http:
paths:
- path: /
backend:
serviceName: nginx-svc
servicePort: 80
---
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
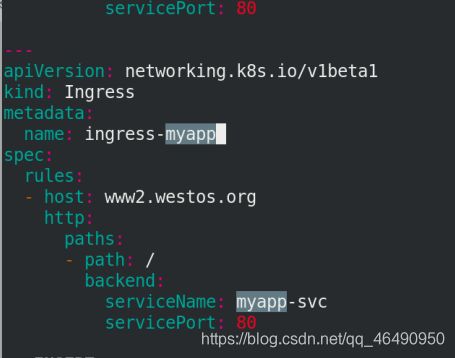
name: ingress-myapp
spec:
rules:
- host: www2.westos.org
http:
paths:
- path: /
backend:
serviceName: myapp-svc
servicePort: 80
6.编辑deployment.yaml
更改deployment.yaml文件的镜像!如下图所示:
cd
cd pod/
vim deployment.yaml
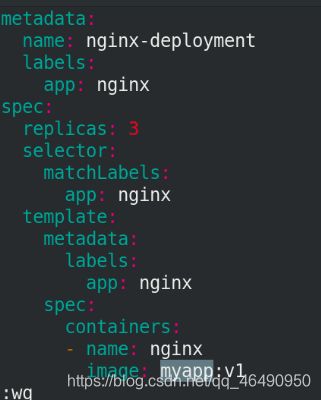
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
labels:
app: nginx
spec:
replicas: 3
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: myapp:v1
执行deployment.yaml清单
Kubectl apply -f deployment.yaml
将刚才实验的svc节点删除,更改内容重新执行!
kubectl delete svc nginx-svc
vim svc.yaml #添加了一个svc节点信息
kubectl apply -svc.yaml
cat svc.yaml
apiVersion: v1
kind: Service
metadata:
name: nginx-svc
spec:
ports:
- protocol: TCP
port: 80
targetPort: 80
selector:
app: nginx
---
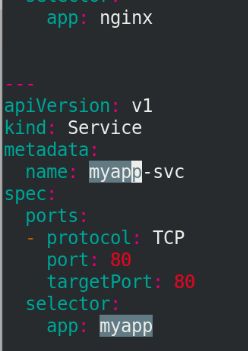
apiVersion: v1
kind: Service
metadata:
name: myapp-svc
spec:
ports:
- protocol: TCP
port: 80
targetPort: 80
selector:
app: myapp
查看svc节点成功:
kubectl get svc
重新执行ingress.yaml清单,查看ingress信息可以看到两个域名都出现了!
kubectl apply -f ingress.yaml
kubectl get ingress
7.测试:
将www2.westos.org也添加到本地解析中:
vim /etc/hosts
172.25.0.10 www2.westos,org

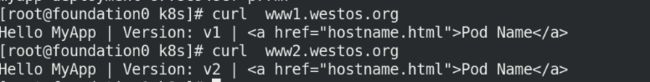
在真机上访问两个域名都成功!
curl www1.westos.org
curl www2.westos.org
四.Ingress 加密
1.配置密钥
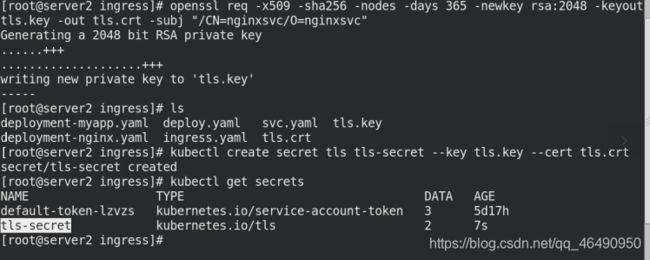
生成密钥,创建secrets对应密钥,并查看密钥!
生成密钥
openssl req -x509 -sha256 -nodes -days 365 -newkey rsa:2048 -keyout tls.key -out tls.crt -subj "/CN=nginxsvc/O=nginxsvc"
ls
创建secrets对应密钥
kubectl create secret tls tls-secret --key tls.key --cert tls.crt
kubectl get secrets
编辑ingress文件
将前面的www2.westos.org部分注释掉!
修改 www1.westos.org部分!
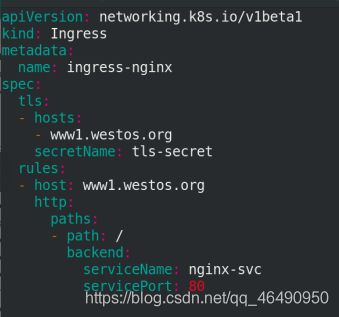
vim ingress.yaml
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-nginx
spec:
tls:
- hosts:
- www1.westos.org
secretName: tls-secret
rules:
- host: www1.westos.org
http:
paths:
- path: /
backend:
serviceName: nginx-svc
servicePort: 80
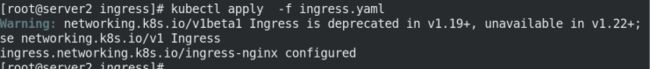
执行ingress.yaml文件,并查看信息:
kubectl apply -f ingress.yaml
kubectl describe ingress
2.测试:
在真机上访问curl www1.westos.org
发现是308:表示重定向!
curl www1.westos.org -I 查看重定向地址
查看到表示已经重定向到了httpds://www1.westos.org

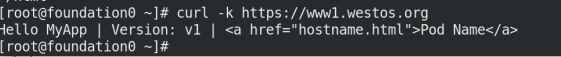
-k 访问加密域名
访问httpds://www1.westos.org
curl -k https://www1.westos.org
五.Ingress 认证
因为认证需要系统自带的认证功能!
所以需要安装生成认证整数的插件
yum install -y httpd-tools
1.生成证书
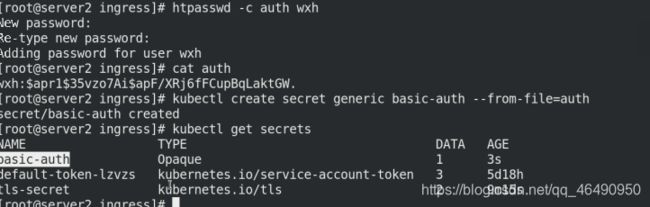
生成证书,输入认证密码
创建证书到k8s secret
htpasswd -c auth wxh #生成证书,输入认证密码
cat auth
kubectl create secret generic basic-auth --from-file=auth
# 创建证书到k8s secret
kubectl get secrets
编辑文件ingress.yaml导入证书:
vim ingress.yaml
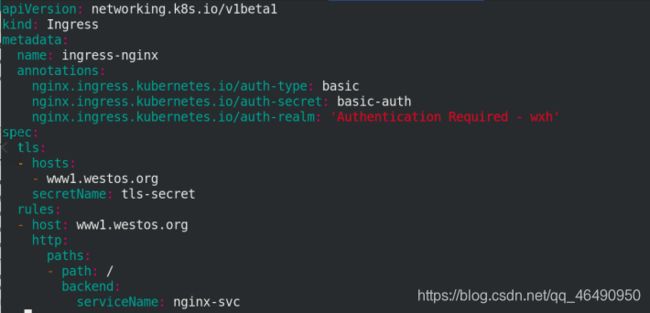
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-nginx
annotations:
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - wxh'
spec:
tls:
- hosts:
- www1.westos.org
secretName: tls-secret
rules:
- host: www1.westos.org
http:
paths:
- path: /
backend:
serviceName: nginx-svc
servicePort: 80
kubectl apply -f ingress.yaml
2.访问测试:
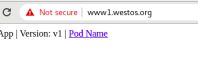
浏览器访问:www1.westos.org
发现需要认证和密码才可以登陆:
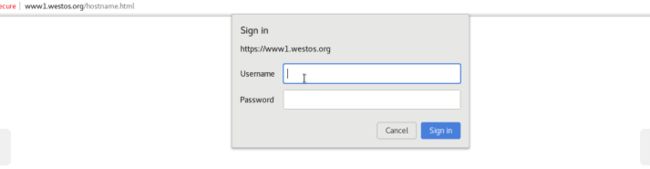
输入前面创建的证书名字,输入认证密码之后就可以成功登陆了!
六. 重定向
1.重定向到 /hostname.html
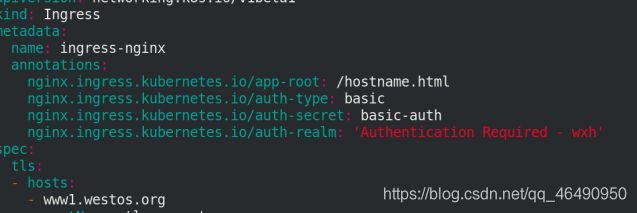
修改文件ingress.yaml
annotations:
nginx.ingress.kubernetes.io/app-root: /hostname.html
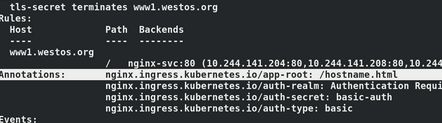
再次执行文件ingress.yaml,查看信息:
kubectl apply -f ingress.yaml
kubectl describe ingress
访问www1.westos.org发现自动重定向到了www1.westos.org/hostname.html
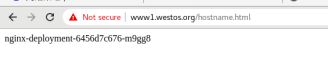
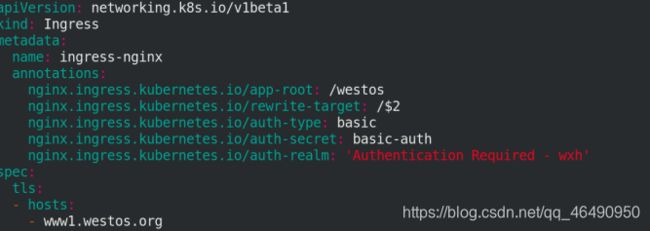
2.根目录重定向到westos
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-nginx
annotations:
nginx.ingress.kubernetes.io/app-root: /westos
nginx.ingress.kubernetes.io/rewrite-target: /$2
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - wxh
spec:
tls:
- hosts:
- www1.westos.org
secretName: tls-secret
rules:
- host: www1.westos.org
http:
paths:
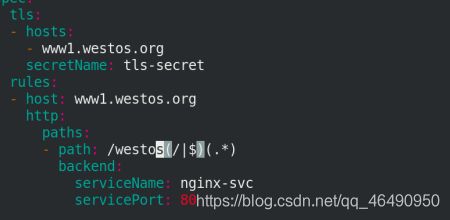
- path: /westos(/|$)(.*)
backend:
serviceName: nginx-svc
servicePort: 80
3.测试
域名代理到/westos
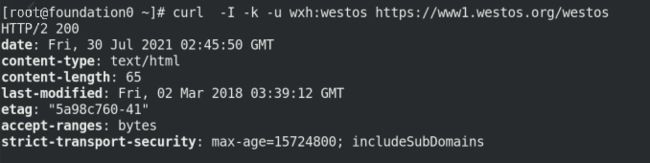
curl -I www1.westos.org
curl -I www1.westos.org/westos
-k访问443加密端口,显示需要认证;-u 后跟认证用户和密码即可查看
curl -I -k -u wxh:westos https://www1.westos.org/westos
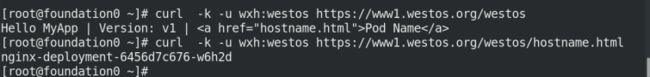
curl -k -u wxh:westos https://www1.westos.org/westos
curl -k -u wxh:westos https://www1.westos.org/westos/hostname.html