攻防世界 Crypto cr4-poor-rsa
题目来源:alexctf-2017
0x00 下载附件
1、补全后缀名
2、解压文件
解压缩,得到base64编码的flag文件flag.b64和RSA的公钥key.pub

flag.b64:
Ni45iH4UnXSttNuf0Oy80+G5J7tm8sBJuDNN7qfTIdEKJow4siF2cpSbP/qIWDjSi+w=
key.pub:
-----BEGIN PUBLIC KEY-----
ME0wDQYJKoZIhvcNAQEBBQADPAAwOQIyUqmeJJ7nzzwMv5Y6AJZhdyvJzfbh4/v8
bkSgel4PiURXqfgcOuEyrFaD01soulwyQkMCAwEAAQ==
-----END PUBLIC KEY-----
0x01 读取RSA参数信息
1、首先获取n和e的值
python脚本:
from Crypto.PublicKey import RSA
with open("./key.pub", "rb") as file:
key = file.read()
print(key)
pub = RSA.importKey(key)
n = pub.n
e = pub.e
print("n = ", n)
print("e = ", e)
运行结果:
n = 833810193564967701912362955539789451139872863794534923259743419423089229206473091408403560311191545764221310666338878019
e = 65537
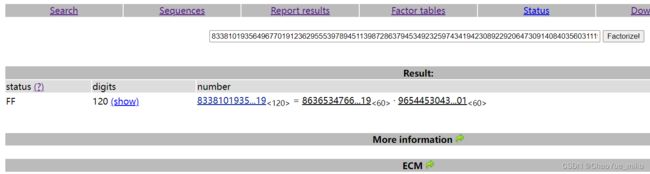
2、使用factordb.com对n进行分解
p = 863653476616376575308866344984576466644942572246900013156919
q = 965445304326998194798282228842484732438457170595999523426901
3、计算d的值
p = 863653476616376575308866344984576466644942572246900013156919
q = 965445304326998194798282228842484732438457170595999523426901
phi_n = (p - 1) * (q - 1)
d = gmpy2.invert(e, phi_n)
print("d = ", d)
d = 521250646663056391768764366517618655312275374668692430321064634566533568373969990465313092928455546989832961905578375473
0x02 解密密文
1、生成私钥
priv = rsa.PrivateKey(n, e, d, p, q)
2、对密文进行解密
首先是base64解码,然后是rsa解密
with open("./flag.b64", "rb") as file:
cipher = file.read()
cipher = base64.b64decode(cipher)
flag = rsa.decrypt(cipher, priv).decode()
print(flag)