kubernetes Helm-dashboard搭建
kubernetes dashboard
-
- Helm 安装部署 dashboard
-
-
- 一、下载 dashborad - helm 到本地
- 二、node节点下载 阿里云的 dashboard 镜像
-
- 三、自定义 dashboard.yaml 文件替代 values.yaml
- 四、执行 dashboard - Helm
- 五、访问 web-UI
-
- dashboard 权限不够
-
- 一、创建 ServiceAccount(SA)
- 二、将 SA(dashboard-admin)绑定给 dashboard-cluster-admin用户,并授于clusterrole权限,访问管理整个集群
- 三、获取serviceaccount的secret信息,可得到token(令牌)的信息
- 四、kubeconfig配置文件登录
Helm 安装部署 dashboard
一、下载 dashborad - helm 到本地
mkdir -p /kubernetes/helm/dashboard;cd /kubernetes/helm/dashboard
helm repo update
helm fetch aliyuncs/kubernetes-dashboard
tar -zxvf kubernetes-dashboard-1.10.1.tgz 二、node节点下载 阿里云的 dashboard 镜像
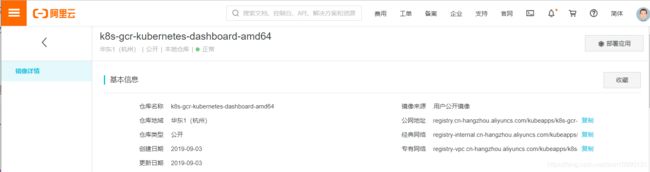
阿里云 K8S 镜像 dashboard地址: https://cr.console.aliyun.com/images/cn-hangzhou/kubeapps/k8s-gcr-kubernetes-dashboard-amd64/detail
registry.cn-hangzhou.aliyuncs.com/kubeapps/k8s-gcr-kubernetes-dashboard-amd64:v1.8.3
docker pull registry.cn-hangzhou.aliyuncs.com/kubeapps/k8s-gcr-kubernetes-dashboard-amd64:v1.8.3
三、自定义 dashboard.yaml 文件替代 values.yaml
image:
repository: registry.cn-hangzhou.aliyuncs.com/kubeapps/k8s-gcr-kubernetes-dashboard-amd64
tag: v1.8.3
ingress:
enabled: true
hosts:
- k8s.frognew.com
annotations:
nginx.ingress.kubernetes.io/ssl-redirect: "true"
nginx.ingress.kubernetes.io/backend-protocol: "HTTPS"
tls:
- secretName: frognew-com-tls-secret
hosts:
- k8s.frognew.com
rbac:
clusterAdminRole: true
四、执行 dashboard - Helm
helm install dashboard .
–namespace kube-system
-f kubernetes-dashboard.yaml
NAME: dashboard
LAST DEPLOYED: Fri Jun 26 18:22:14 2020
NAMESPACE: kube-system
STATUS: deployed
REVISION: 1
TEST SUITE: None
NOTES:
*********************************************************************************
*** PLEASE BE PATIENT: kubernetes-dashboard may take a few minutes to install ***
*********************************************************************************
From outside the cluster, the server URL(s) are:
https://k8s.frognew.com
Pod 验证: kubectl get pod -n kube-system
查看 Pod 详细信息:kubectl get pod -n kube-system dashboard-kubernetes-dashboard-746c5869f9-bj9hx -o wide
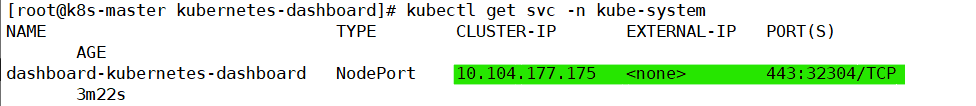
SVC 验证: kubectl get svc -n kube-system
暴露外网,修改其 type 类型
kubectl edit svc -n kube-system dashboard-kubernetes-dashboard
type: NodePort五、访问 web-UI
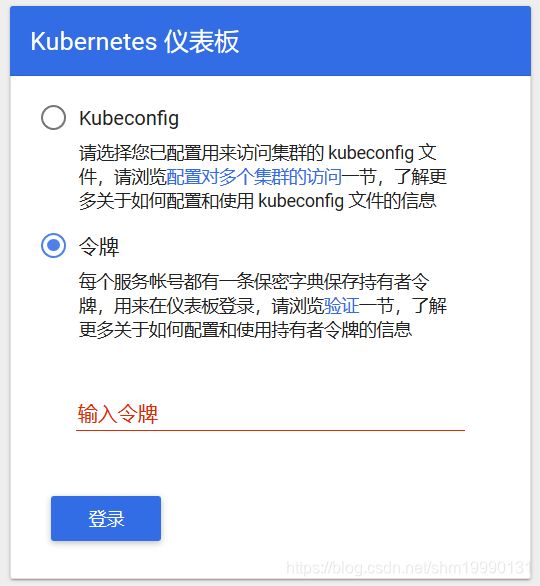
火狐浏览器访问:https://192.168.168.11:32304 选择采用 令牌 (token) 的方式来进行登录
获取 dashboard 的 token码名(key) :
kubectl -n kube-system get secret | grep dashboard
根据 token名(key) 查看具体的 token值(value)
kubectl describe secret -n kube-system dashboard-kubernetes-dashboard-token-2mkj8
dashboard 权限不够
有时候会出现因为权限不够,通过 token 值登录后查看集群,但是并没有查看集群信息权限。
需要做的是创建一个可以访问集群全部权限的 token,或者是某个超级管理员使用这个用户的 token。
一、创建 ServiceAccount(SA)
[root@k8s-master kubernetes-dashboard]# kubectl create serviceaccount dashboard-admin -n kube-system
serviceaccount/dashboard-admin created
[root@k8s-master kubernetes-dashboard]# kubectl get sa -n kube-system | grep dashboard-admin
dashboard-admin 1 23s二、将 SA(dashboard-admin)绑定给 dashboard-cluster-admin用户,并授于clusterrole权限,访问管理整个集群
[root@kubernetes01 pki]# kubectl create clusterrolebinding dashboard-cluster-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin
clusterrolebinding.rbac.authorization.k8s.io/dashboard-cluster-admin created三、获取serviceaccount的secret信息,可得到token(令牌)的信息
[root@k8s-master kubernetes-dashboard]# kubectl get secret -n kube-system |grep dash
dashboard-admin-token-2fb94 kubernetes.io/service-account-token 3
dashboard-kubernetes-dashboard-token-n2sxp kubernetes.io/service-account-token 3 [root@k8s-master kubernetes-dashboard]# kubectl describe secrets -n kube-system dashboard-admin-token-2fb94
Name: dashboard-admin-token-2fb94
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: dashboard-admin
kubernetes.io/service-account.uid: c44a068c-9620-4fc0-a293-393b2b96b3eb
Type: kubernetes.io/service-account-token
Data
====
token: eyJhbGciOiJSUzI1NiIsImtpZCI6Im1YdzVaVTlhNV80dUFjMXNmTmsxNmtQVmpPeGpUaDRMbjM0VFhxdHlnQjQifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tMmZiOTQiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiYzQ0YTA2OGMtOTYyMC00ZmMwLWEyOTMtMzkzYjJiOTZiM2ViIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.KrUc1jvzxQUzCiDlwpFpY8OwHNCe81L_yyMeKahqr8UMOSyz1aRK7QPG7QxlhWjSLIMBOWi-dvir4u7Loxr3jDACLVyOZptq0tUZpBHuSDqsa4hIc18Hq7dHnGw94BGJKn5s8_lmHGTHKM4gYlmdFeg2vOQbFKDcQIwlEa0C8u_WLn4NRoL_tu_Zhfy7KJEvRAm-H0RnlwYfxPjcNiZB3Q2MsQbWApaU3gVkUAKe-ymrfGTirbQgcBCjD6h6t-KFwstnSyz9EBrHVPKZ5kAeO4gyXNTghHA9iv1myqJAoBeX15JUv78W4GLwCk7GbYa_-1tCwanyKlqk7sH9WwlRAA
ca.crt: 1025 bytes
namespace: 11 bytes
四、kubeconfig配置文件登录
创建一个只能对default名称空间有权限的serviceaccount
[root@kubernetes01 pki]# kubectl create serviceaccount def-ns-admin -n defaultserviceaccount/def-ns-admin created
[root@kubernetes01 pki]# kubectl create rolebinding def-ns-admin --clusterrole=admin --serviceaccount=default:def-ns-admin
rolebinding.rbac.authorization.k8s.io/def-ns-admin
[root@kubernetes01 pki]# kubectl get secretNAME
TYPE DATA AGEadmin-token-bwrbg kubernetes.io/service-account-token 3 5d1hdef-ns-admin-token-xdvx5 kubernetes.io/service-account-token 3 2m9sdefault-token-87nlt kubernetes.io/service-account-token 3 49dtomcat-ingress-secret kubernetes.io/tls 2 21d
[root@master1 pki]# kubectl describe secret def-ns-admin-token-xdvx5
Name: def-ns-admin-token-xdvx5
Namespace: default
Labels: <none>
Annotations: kubernetes.io/service-account.name: def-ns-admin kubernetes.io/service-account.uid: 928bbca1-245c-11e9-81cc-000c291e37c2
Type: kubernetes.io/service-account-token
Data====
ca.crt: 1025 bytes
namespace: 7 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi14ZHZ4NSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI5MjhiYmNhMS0yNDVjLTExZTktODFjYy0wMDBjMjkxZTM3YzIiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.EzUF13MElI8b-kuQNh_u1hGQpxgoffm4LdTVoeORKUBTADwqHEtW2arj76oZuI-wQyy5P0v5VvOoefr6h3NpIgbAze8Lqyrpg9wO0Crfi30IE1kZ2wUPYU9P_5inMxmCPLttppyPyc8mQKDkOOB1xFUmEebC63my-dG4CZljsd8zwNU6eXnhaThSUUn12UTvRsbSBLD-dvau1OY6YgDL6mgFl3cVqzCPd7ELpEyNYWCh3x5rcRfCcjcHGfUOrWY2NvdW50Iiwia3ViZXJpby9-CI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2这种情况下的权限较小,用token登陆后只能对default名称空间有权限
[root@kubernetes01 pki]# kubectl config set-cluster kubernetes --certificate-authority=./ca.crt --server="https://10.0.0.100:6443" --embed-certs=true --kubeconfig=/root/def-ns-admin.conf
Cluster "kubernetes" set.
[root@kubernetes01 pki]# kubectl config view --kubeconfig=/root/def-ns-admin.conf
apiVersion: v1
clusters:-
cluster:
certificate-authority-data: DATA+OMITTED
server: https://10.0.0.100:6443
name: kubernetes
contexts: []
current-context: ""
kind: Config
preferences: {}
users: []
[root@kubernetes01 pki]# kubectl get secret
NAME TYPE DATA AGE
def-ns-admin-token-xdvx5 kubernetes.io/service-account-token 3 5d
[root@kubernetes01 pki]# kubectl describe secret def-ns-admin-token-xdvx5
Name: def-ns-admin-token-xdvx5
Namespace: default
Labels: <none>
Annotations: kubernetes.io/service-account.name: def-ns-admin kubernetes.io/service-account.uid: 928bbca1-245c-11e9-81cc-000c291e37c2
Type: kubernetes.io/service-account-token
Data====
ca.crt: 1025 bytes
namespace: 7 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi14ZHZ4NSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI5MjhiYmNhMS0yNDVjLTExZTktODFjYy0wMDBjMjkxZTM3YzIiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.EzUF13MElI8b-kuQNh_u1hGQpxgoffm4LdTVoeORKUBTADwqHEtW2arj76oZuI-wQyy5P0v5VvOoefr6h3NpIgbAze8Lqyrpg9wO0Crfi30IE1kZ2wUPYU9P_5inMxmCPLttppyPyc8mQKDkOOB1xFUmEebC63my-dG4CZljsd8zwNU6eXnhaThSUUn12UTvRsbSBLD-dvau1OY6YgDL6mgFl3cVqzCPd7ELpEyNYWCh3x5rcRfCcjcHGfUOrWY2NvdW50Iiwia3ViZXJpby9-CI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2
[root@master1 pki]# kubectl config set-credentials def-ns-admin --token=eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi14ZHZ4NSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI5MjhiYmNhMS0yNDVjLTExZTktODFjYy0wMDBjMjkxZTM3YzIiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.EzUF13MElI8b-kuQNh_u1hGQpxgoffm4LdTVoeORKUBTADwqHEtW2arj76oZuI-wQyy5P0v5VvOoefr6h3NpIgbAze8Lqyrpg9wO0Crfi30IE1kZ2wUPYU9P_5inMxmCPLttppyPyc8mQKDkOOB1xFUmEebC63my-dG4CZljsd8zwNU6eXnhaThSUUn12UTvRsbSBLD-dvau1OY6YgDL6mgFl3cVqzCPd7ELpEyNYWCh3x5rcRfCcjcHGfUOrWY2NvdW50Iiwia3ViZXJpby9-CI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2 --kubeconfig=/root/def-ns-admin.conf
User "def-ns-admin" set.
设置context
[root@kubernetes01 pki]# kubectl config set-context def-ns-admin@kubernetes --cluster=kubernetes --user=def-ns-admin --kubeconfig=/root/def-ns-admin.conf
Context "def-ns-admin@kubernetes" created.
use-context
[root@kubernetes01 pki]# kubectl config use-context def-ns-admin@kubernetes --kubeconfig=/root/def-ns-admin.conf
Switched to context "def-ns-admin@kubernetes".
查看conf文件,此时已经完整了
[root@kubernetes01 pki]# kubectl config view --kubeconfig=/root/def-ns-admin.conf