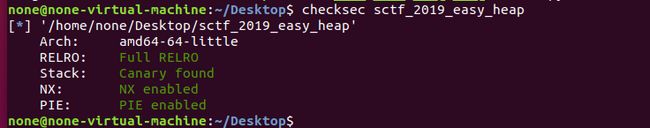
- Canary
Sean_summer
安全web安全
定义:Canary是一种用以防护栈溢出的保护机制。原理:是在一个函数的入口处,先从fs/gs寄存器中取出一个4字节(eax,四字节通常是32位的文件)或者8字节(rax,通常是64位的文件)的值存到栈上,当函数结束是会检查这个栈上的值是否和存进去的值相同。通常在pwn题写exp是用的字符a,这样存储进缓冲区,将会覆盖原始的canary的值当canary被覆盖后,也就是原应为canary的位置被字符
- ctfshow-stack36
dd-pwn
pwn
每天下午抖音(47253061271)直播pwn题,小白一只,欢迎各位师傅讨论可以发现全文只有一个ctfshow的自定义函数Gets函数,发现有溢出漏洞,可以利用该漏洞进行构建exp,发现有get_flag供我们使用,可以直接打开根目录的flag,因此只需要构造溢出,溢出返回地址覆盖成get_flag就行Exp:
- Pwn,我的栈溢出笔记就该这么写(上)
「已注销」
栈
一周的刨坟结束了,忙着搭建维护k8s,该整个小小的笔记了原理篇什么是栈溢出?栈溢出指的是程序向栈中某个变量中写入的字节数超过了这个变量本身所申请的字节数,因而导致与其相邻的栈中的变量的值被改变。栈溢出会导致什么结果?栈溢出漏洞轻则可以使程序崩溃,重则可以使攻击者控制程序执行流程。如何防范栈溢出?(1).金丝雀(canary)1、在所有函数调用发生时,向栈帧内压入一个额外的随机DWORD(数),这个
- ctfshow做题笔记—前置基础—pwn13~pwn19
Yilanchia
笔记学习
文章目录前言一、pwn13二、pwn14三、pwn15(编译汇编代码到可执行文件,即可拿到flag)四、pwn16(使用gcc将其编译为可执行文件)五、pwn17六、pwn18七、pwn19(关闭了输出流,一定是最安全的吗?)前言记录一下pwn13~pwn19,巩固一下学到的知识。一、pwn13知识点:如何使用GCCgccmain.c-oprogram·gcc是调用GCC编译器的命令。·-opro
- Django下防御Race Condition漏洞
落沐萧萧
djangopython后端
今天下午在v2ex上看到一个帖子,讲述自己因为忘记加分布式锁导致了公司的损失:我曾在《从Pwnhub诞生聊Django安全编码》一文中描述过关于商城逻辑所涉及的安全问题,其中就包含并发漏洞(RaceCondition)的防御,但当时说的比较简洁,也没有演示实际的攻击过程与危害。今天就以v2ex上这个帖子的场景来讲讲,常见的存在漏洞的Django代码,与我们如何正确防御竞争漏洞的方法。0x01Pla
- 【wp】hgame2023 week3 Re&&Pwn
woodwhale
ctf与君共勉pwnctfpwnrehgame
【wp】hgame2023week3Re&&PwnRecpp那个chacha20加密不会。kunmusic用dnspy逆dll,在Program的Main方法中找到了初始化的数据下断点执行,拷贝出data写一份脚本进行data与104的异或defstep_one():withopen("./data",encoding="u8")asf:lines=f.readlines()data=[]forl
- Pwntools 的详细介绍、安装指南、配置说明
程序员的世界你不懂
效率工具提升百度新浪微博
Pwntools:Python开源安全工具箱一、Pwntools简介Pwntools是一个由Securityresearcher开发的高效Python工具库,专为密码学研究、漏洞利用、协议分析和逆向工程设计。它集成了数百个底层工具的功能,提供统一的PythonAPI接口,广泛用于CTF竞赛、渗透测试和安全开发。其核心优势包括:模块化设计:支持密码学、网络协议、shellcode生成等全栈操作跨平台
- vulnhub(8):pWnOS(还没信息收集就已经成功打点)
anddddoooo
vulnhuboscp-like靶场linux运维网络安全安全服务器
端口nmap主机发现nmap-sn192.168.89.0/24Nmapscanreportfor192.168.89.116Hostisup(0.00020slatency).116是新出现的机器,他就是靶机nmap端口扫描nmap-Pn192.168.89.116-p---min-rate10000-oAnmap/scan扫描开放端口保存到nmap/scan下PORT STATESER
- ffmpeg合成视频
一个高效工作的家伙
大模型ffmpeg
记录下ffmpeg如何安装配置,以及如何合成视频。一、安装ffmpeg1、下载ffmpeg安装包打开DpwnloadFFmpeg官网,选择安装包Windowsbuildsfromgyan.dev2、下滑找到releasebulids部分,选择ffmpeg-7.0.2-essentials_build.zip3、下载完成后,解压缩得到FFmpeg文件夹。解压文件并检查目录结构解压后的文件夹中应包含以
- python软件安装教程-Python-中文版软件安装包以及安装教程
weixin_37988176
Python-3.5.2(32/64位)软件下载地址链接:https://pan.baidu.com/s/1O1GIOCudBqPWNP6voPMpEA密码:zp58安装步骤:1.鼠标右击软件压缩包,选择“解压到python-3.5.2”2.打开“python-3.5.2”文件夹,鼠标右击“python-3.5.2-amd64.exe”(32位电脑操作系统鼠标右击“python-3.5.2.exe
- PWN基础15:GOT表 和 PLT表
prettyX
PWN
在学习总结GOT、PLT表的相关知识,下面是我参考的文章和视频,每条资源都互有补充感谢各位作者的分享精神https://zhuanlan.zhihu.com/p/130271689https://blog.csdn.net/qq_18661257/article/details/54694748https://blog.csdn.net/linuxheik/article/details/8850
- pwn7(利用格式化字符串泄露libc)
再劝
网络安全算法linux服务器数据库
题目[HNCTF2022WEEK4]ezcanaryint__fastcallmain(intargc,constchar**argv,constchar**envp){chars[96];//[rsp+0h][rbp-170h]BYREFcharbuf[264];//[rsp+60h][rbp-110h]BYREFunsigned__int64v6;//[rsp+168h][rbp-8h]v6=
- hackcon ctf 2018 | pwn wp
fantasy_learner
BOF漏洞点:栈溢出利用过程栈溢出跳转callMeMaybe函数获得flagexpSheSellsSeaShells90流程分析:给出了输入的栈地址有一个栈溢出点没有nx利用过程:根据以上三点,得出可以使用ret2shellcode使用shellcraft生成shellcode利用栈溢出,输入并跳转到shellcodeexpSimpleYetElegent150这道题目做了最久,卡在了能否根据_d
- BUUCTF 2021-10-4 Pwn
Ch1lkat
BUUCTFPwnlinuxpwn
文章目录保持手感echo分析EXPPwnme1分析EXPwdb_2018_1st_babyheap分析EXPFSOPhouseoforange_hitcon_2016分析前置知识House_of_orangeFSOPEXPzctf_2016_note3分析EXPgyctf_2020_document分析EXP动态调试复现护网杯_gettingstart分析EXPpicoctf_2018_buffe
- pwn学习笔记(8)--初识Pwn沙箱
晓幂
Pwn学习笔记
初识Pwn沙箱沙箱机制,英文sandbox,是计算机领域的虚拟技术,常见于安全方向。一般说来,我们会将不受信任的软件放在沙箱中运行,一旦该软件有恶意行为,则禁止该程序的进一步运行,不会对真实系统造成任何危害。安全计算模式seccomp(SecureComputingMode)在Linux2.6.10之后引入到kernel的特性,可用其实现一个沙箱环境。使用seccomp模式可以定义系统调用白名单和
- pwn学习笔记(9)-中级ROP--ret2csu
晓幂
Pwn学习笔记
pwn学习笔记(9)-中级ROP–ret2csu前置知识首先是64位文件的传参方式:前六个参数是从左到右放入寄存器:rdi、rsi、rdx、rcx、r8、r9,之后的通过栈传参。比如:传参函数大于7个:H(a,b,c,d,e,f,g,h)a->%rdi、b->%rsi、c->%rdx、d->%rcx、e->%r8、f->%r9h->(%esp)g->(%esp)callH先看看如下代码:#incl
- OVS主线流程之ovs-vswitchd主体结构分析
大空新一
网络OVS
OVS是openvirtualswitch的简称,是现在广泛使用的软件实现的虚拟网络交换机。各大云厂商普遍使用OVS来实现自身的虚拟网络,各厂商会根据自身需要加以修改使之符合自身需求,DPU中也使用OVS来实现流表的offload。OVS中的流表基于多级结构,与用户强相关的是opwnflow,下发的流表称为emcflow。OVS一般存在两种运行模式,内核模式和DPDK模式。内核模式下存在一个dat
- 重头开始嵌入式第二十一天(Linux系统编程 文件相关函数)
FLPGYH
vimlinuxc语言
目录1.getpwuid2.getpwnam3.getgrgid4.symlink在Linux和类Unix系统中,创建软链接(符号链接)的常用指令是ln-s。5.remove6.rename7.link8.truncate9.perror10.strerror11.error1.makefile2.gdbstrtok1.getpwuidgetpwuid函数是C语言标准库中的一个函数,用于通过用户I
- 2022羊城杯pwn wp
Loτυs
wppwn
YCBSQL远程是上传一个sql文件,题目提示用nc带出flag。优先考虑sqlite自带的.system函数(抱着试一试的想法),然后找web手要了个vps监听,莫名其妙就出了。sql文件内容:.systemnc1.117.171.2489997b->c->dunlink之后成为a->c->db->c->d不过此时b->c->d的nodenum为1,因此不好操作,唯一好利用的点就是通过delet
- 安恒杯2018-pwn-over
Sadmess
framefaking正如这个技巧名字所说的那样,这个技巧就是构造一个虚假的栈帧来控制程序的执行流。原理概括地讲,我们在之前讲的栈溢出不外乎两种方式控制程序EIP控制程序EBP其最终都是控制程序的执行流。在framefaking中,我们所利用的技巧便是同时控制EBP与EIP,这样我们在控制程序执行流的同时,也改变程序栈帧的位置。一般来说其payload如下bufferpadding|fakeebp
- pwn学习笔记(4)ret2libc
晓幂
学习笔记
pwn学习笔记(4)静态链接:静态链接是由链接器在链接时将库的内容加入到可执行程序中的做法。链接器是一个独立程序,将一个或多个库或目标文件(先前由编译器或汇编器生成)链接到一块生成可执行程序。这里的库指的是静态链接库,Windows下以.lib为后缀,Linux下以.a为后缀。也就是说将静态链接库中的所有的函数都写入这个ELF文件中,所以会造成该二进制文件极为庞大,因此也会存在很多的可供利用来re
- HGAME 2024 WEEK1 WP
是Mumuzi
ctf信息安全
文章目录WEBezHTTPBypassitSelectCourses2048*16jhatREezASMezPYCezUPXezIDAPWNEzSignInCRYPTO奇怪的图片ezRSAezMathezPRNGMISCSignIn来自星尘的问候simple_attack希儿希儿希尔签到放假比较闲,打打比赛WEBezHTTP来自vidar.club、UA要求阿巴阿巴阿巴、来自本地(提示不是XFF,
- pwnable.kr解题write up —— Toddler's Bottle(一)
captain_hwz
securityCTFsecurity
1.fd#include#includecharbuf[32];intmain(intargc,char*argv[],char*envp[]){if(argcunsignedlonghashcode=0x21DD09EC;unsignedlongcheck_password(constchar*p){int*ip=(int*)p;inti;intres=0;for(i=0;i#includevo
- pwnable.kr解题write up —— Toddler's Bottle(二)
captain_hwz
securityCTFsecurity
9.mistake#include#include#definePW_LEN10#defineXORKEY1voidxor(char*s,intlen){inti;for(i=0;i0)){printf("readerror\n");close(fd);return0;}charpw_buf2[PW_LEN+1];printf("inputpassword:");scanf("%10s",pw_b
- pwn旅行之[WUSTCTF 2020]getshell2(一些小知识)
晓幂
安全
题目分析1首先打开这个题目的链接的时候,看到了ret2syscall,以为是一个纯正的syscall的题,结果,做的时候发现这个题的危险函数限制的字符串个数不足以写入syscall需要的所有地址,所以,这里参考dalao们的方法,/做出了这道题,这里记录一下。首先,checksec看一下这个题目的保护以及架构:是一个32位小端序程序,开了栈不可执行的保护,所以初步判断,stack的ret2shel
- pwn学习笔记(2)ret_2_text_or_shellcode
晓幂
学习笔记
pwn学习笔记(2)1.三种常见的寄存器:ax寄存器:通用寄存器,可用于存放多种数据bp寄存器:存放的是栈帧的栈底地址sp寄存器:存放的是栈顶的地址2.栈帧与栈工作的简介:栈帧是存储函数的一些信息的地方,栈帧存储有函数的局部变量,传递给子函数的实际参数,父函数的地址以及上一个栈帧栈底的地址,大致情况如下:在函数调用的过程中,首先会讲bp寄存器的值进行压栈,以方便在恢复的时候恢复栈底寄存器的值,再之
- pwn学习笔记(3)ret2syscall
晓幂
学习笔记
pwn学习笔记(3)ROP原理:ROP(ReturnOrientedProgramming)返回导向编程,主要思想是通过在程序中已有的小片段(gadgets)来改变某些寄存器或者变量的值,从而控制程序的执行流程。栈溢出–ret2syscall:1.系统调用:对于一个已经存在于标准库中的函数,例如printf(),我们编写某个程序的时候,这个函数仅仅只用了printf(参数);这么一行,但是,其工作
- 从零开始学howtoheap:解题西湖论剑Storm_note
网络安全我来了
逆向二进制Re网络安全系统安全安全安全架构
how2heap是由shellphish团队制作的堆利用教程,介绍了多种堆利用技术,后续系列实验我们就通过这个教程来学习。环境可参见从零开始配置pwn环境:从零开始配置pwn环境:从零开始配置pwn环境:优化pwn虚拟机配置支持libc等指令-CSDN博客1.题目信息https://github.com/ble55ing/ctfpwn/blob/master/pwnable/ctf/x64/Sto
- 从零开始学howtoheap:理解fastbins的unsorted bin攻击
网络安全我来了
网络安全安全系统安全安全架构
how2heap是由shellphish团队制作的堆利用教程,介绍了多种堆利用技术,后续系列实验我们就通过这个教程来学习。环境可参见从零开始配置pwn环境:从零开始配置pwn环境:从零开始配置pwn环境:优化pwn虚拟机配置支持libc等指令-CSDN博客1.fastbins的unsorted_bin攻击unsortedbin攻击通常是为更进一步的攻击做准备的,我们知道unsortedbin是一个
- 从零开始学howtoheap:理解fastbins的large_bin攻击
网络安全我来了
网络安全系统安全安全安全架构
how2heap是由shellphish团队制作的堆利用教程,介绍了多种堆利用技术,后续系列实验我们就通过这个教程来学习。环境可参见从零开始配置pwn环境:从零开始配置pwn环境:从零开始配置pwn环境:优化pwn虚拟机配置支持libc等指令-CSDN博客1.fastbins的large_bin攻击根据原文描述跟unsortedbinattack实现的功能差不多https://blog.csdn.
- PHP,安卓,UI,java,linux视频教程合集
cocos2d-x小菜
javaUIlinuxPHPandroid
╔-----------------------------------╗┆
- zookeeper admin 笔记
braveCS
zookeeper
Required Software
1) JDK>=1.6
2)推荐使用ensemble的ZooKeeper(至少3台),并run on separate machines
3)在Yahoo!,zk配置在特定的RHEL boxes里,2个cpu,2G内存,80G硬盘
数据和日志目录
1)数据目录里的文件是zk节点的持久化备份,包括快照和事务日
- Spring配置多个连接池
easterfly
spring
项目中需要同时连接多个数据库的时候,如何才能在需要用到哪个数据库就连接哪个数据库呢?
Spring中有关于dataSource的配置:
<bean id="dataSource" class="com.mchange.v2.c3p0.ComboPooledDataSource"
&nb
- Mysql
171815164
mysql
例如,你想myuser使用mypassword从任何主机连接到mysql服务器的话。
GRANT ALL PRIVILEGES ON *.* TO 'myuser'@'%'IDENTIFIED BY 'mypassword' WI
TH GRANT OPTION;
如果你想允许用户myuser从ip为192.168.1.6的主机连接到mysql服务器,并使用mypassword作
- CommonDAO(公共/基础DAO)
g21121
DAO
好久没有更新博客了,最近一段时间工作比较忙,所以请见谅,无论你是爱看呢还是爱看呢还是爱看呢,总之或许对你有些帮助。
DAO(Data Access Object)是一个数据访问(顾名思义就是与数据库打交道)接口,DAO一般在业
- 直言有讳
永夜-极光
感悟随笔
1.转载地址:http://blog.csdn.net/jasonblog/article/details/10813313
精华:
“直言有讳”是阿里巴巴提倡的一种观念,而我在此之前并没有很深刻的认识。为什么呢?就好比是读书时候做阅读理解,我喜欢我自己的解读,并不喜欢老师给的意思。在这里也是。我自己坚持的原则是互相尊重,我觉得阿里巴巴很多价值观其实是基本的做人
- 安装CentOS 7 和Win 7后,Win7 引导丢失
随便小屋
centos
一般安装双系统的顺序是先装Win7,然后在安装CentOS,这样CentOS可以引导WIN 7启动。但安装CentOS7后,却找不到Win7 的引导,稍微修改一点东西即可。
一、首先具有root 的权限。
即进入Terminal后输入命令su,然后输入密码即可
二、利用vim编辑器打开/boot/grub2/grub.cfg文件进行修改
v
- Oracle备份与恢复案例
aijuans
oracle
Oracle备份与恢复案例
一. 理解什么是数据库恢复当我们使用一个数据库时,总希望数据库的内容是可靠的、正确的,但由于计算机系统的故障(硬件故障、软件故障、网络故障、进程故障和系统故障)影响数据库系统的操作,影响数据库中数据的正确性,甚至破坏数据库,使数据库中全部或部分数据丢失。因此当发生上述故障后,希望能重构这个完整的数据库,该处理称为数据库恢复。恢复过程大致可以分为复原(Restore)与
- JavaEE开源快速开发平台G4Studio v5.0发布
無為子
我非常高兴地宣布,今天我们最新的JavaEE开源快速开发平台G4Studio_V5.0版本已经正式发布。
访问G4Studio网站
http://www.g4it.org
2013-04-06 发布G4Studio_V5.0版本
功能新增
(1). 新增了调用Oracle存储过程返回游标,并将游标映射为Java List集合对象的标
- Oracle显示根据高考分数模拟录取
百合不是茶
PL/SQL编程oracle例子模拟高考录取学习交流
题目要求:
1,创建student表和result表
2,pl/sql对学生的成绩数据进行处理
3,处理的逻辑是根据每门专业课的最低分线和总分的最低分数线自动的将录取和落选
1,创建student表,和result表
学生信息表;
create table student(
student_id number primary key,--学生id
- 优秀的领导与差劲的领导
bijian1013
领导管理团队
责任
优秀的领导:优秀的领导总是对他所负责的项目担负起责任。如果项目不幸失败了,那么他知道该受责备的人是他自己,并且敢于承认错误。
差劲的领导:差劲的领导觉得这不是他的问题,因此他会想方设法证明是他的团队不行,或是将责任归咎于团队中他不喜欢的那几个成员身上。
努力工作
优秀的领导:团队领导应该是团队成员的榜样。至少,他应该与团队中的其他成员一样努力工作。这仅仅因为他
- js函数在浏览器下的兼容
Bill_chen
jquery浏览器IEDWRext
做前端开发的工程师,少不了要用FF进行测试,纯js函数在不同浏览器下,名称也可能不同。对于IE6和FF,取得下一结点的函数就不尽相同:
IE6:node.nextSibling,对于FF是不能识别的;
FF:node.nextElementSibling,对于IE是不能识别的;
兼容解决方式:var Div = node.nextSibl
- 【JVM四】老年代垃圾回收:吞吐量垃圾收集器(Throughput GC)
bit1129
垃圾回收
吞吐量与用户线程暂停时间
衡量垃圾回收算法优劣的指标有两个:
吞吐量越高,则算法越好
暂停时间越短,则算法越好
首先说明吞吐量和暂停时间的含义。
垃圾回收时,JVM会启动几个特定的GC线程来完成垃圾回收的任务,这些GC线程与应用的用户线程产生竞争关系,共同竞争处理器资源以及CPU的执行时间。GC线程不会对用户带来的任何价值,因此,好的GC应该占
- J2EE监听器和过滤器基础
白糖_
J2EE
Servlet程序由Servlet,Filter和Listener组成,其中监听器用来监听Servlet容器上下文。
监听器通常分三类:基于Servlet上下文的ServletContex监听,基于会话的HttpSession监听和基于请求的ServletRequest监听。
ServletContex监听器
ServletContex又叫application
- 博弈AngularJS讲义(16) - 提供者
boyitech
jsAngularJSapiAngularProvider
Angular框架提供了强大的依赖注入机制,这一切都是有注入器(injector)完成. 注入器会自动实例化服务组件和符合Angular API规则的特殊对象,例如控制器,指令,过滤器动画等。
那注入器怎么知道如何去创建这些特殊的对象呢? Angular提供了5种方式让注入器创建对象,其中最基础的方式就是提供者(provider), 其余四种方式(Value, Fac
- java-写一函数f(a,b),它带有两个字符串参数并返回一串字符,该字符串只包含在两个串中都有的并按照在a中的顺序。
bylijinnan
java
public class CommonSubSequence {
/**
* 题目:写一函数f(a,b),它带有两个字符串参数并返回一串字符,该字符串只包含在两个串中都有的并按照在a中的顺序。
* 写一个版本算法复杂度O(N^2)和一个O(N) 。
*
* O(N^2):对于a中的每个字符,遍历b中的每个字符,如果相同,则拷贝到新字符串中。
* O(
- sqlserver 2000 无法验证产品密钥
Chen.H
sqlwindowsSQL ServerMicrosoft
在 Service Pack 4 (SP 4), 是运行 Microsoft Windows Server 2003、 Microsoft Windows Storage Server 2003 或 Microsoft Windows 2000 服务器上您尝试安装 Microsoft SQL Server 2000 通过卷许可协议 (VLA) 媒体。 这样做, 收到以下错误信息CD KEY的 SQ
- [新概念武器]气象战争
comsci
气象战争的发动者必须是拥有发射深空航天器能力的国家或者组织....
原因如下:
地球上的气候变化和大气层中的云层涡旋场有密切的关系,而维持一个在大气层某个层次
- oracle 中 rollup、cube、grouping 使用详解
daizj
oraclegroupingrollupcube
oracle 中 rollup、cube、grouping 使用详解 -- 使用oracle 样例表演示 转自namesliu
-- 使用oracle 的样列库,演示 rollup, cube, grouping 的用法与使用场景
--- ROLLUP , 为了理解分组的成员数量,我增加了 分组的计数 COUNT(SAL)
- 技术资料汇总分享
Dead_knight
技术资料汇总 分享
本人汇总的技术资料,分享出来,希望对大家有用。
http://pan.baidu.com/s/1jGr56uE
资料主要包含:
Workflow->工作流相关理论、框架(OSWorkflow、JBPM、Activiti、fireflow...)
Security->java安全相关资料(SSL、SSO、SpringSecurity、Shiro、JAAS...)
Ser
- 初一下学期难记忆单词背诵第一课
dcj3sjt126com
englishword
could 能够
minute 分钟
Tuesday 星期二
February 二月
eighteenth 第十八
listen 听
careful 小心的,仔细的
short 短的
heavy 重的
empty 空的
certainly 当然
carry 携带;搬运
tape 磁带
basket 蓝子
bottle 瓶
juice 汁,果汁
head 头;头部
- 截取视图的图片, 然后分享出去
dcj3sjt126com
OSObjective-C
OS 7 has a new method that allows you to draw a view hierarchy into the current graphics context. This can be used to get an UIImage very fast.
I implemented a category method on UIView to get the vi
- MySql重置密码
fanxiaolong
MySql重置密码
方法一:
在my.ini的[mysqld]字段加入:
skip-grant-tables
重启mysql服务,这时的mysql不需要密码即可登录数据库
然后进入mysql
mysql>use mysql;
mysql>更新 user set password=password('新密码') WHERE User='root';
mysq
- Ehcache(03)——Ehcache中储存缓存的方式
234390216
ehcacheMemoryStoreDiskStore存储驱除策略
Ehcache中储存缓存的方式
目录
1 堆内存(MemoryStore)
1.1 指定可用内存
1.2 驱除策略
1.3 元素过期
2 &nbs
- spring mvc中的@propertysource
jackyrong
spring mvc
在spring mvc中,在配置文件中的东西,可以在java代码中通过注解进行读取了:
@PropertySource 在spring 3.1中开始引入
比如有配置文件
config.properties
mongodb.url=1.2.3.4
mongodb.db=hello
则代码中
@PropertySource(&
- 重学单例模式
lanqiu17
单例Singleton模式
最近在重新学习设计模式,感觉对模式理解更加深刻。觉得有必要记下来。
第一个学的就是单例模式,单例模式估计是最好理解的模式了。它的作用就是防止外部创建实例,保证只有一个实例。
单例模式的常用实现方式有两种,就人们熟知的饱汉式与饥汉式,具体就不多说了。这里说下其他的实现方式
静态内部类方式:
package test.pattern.singleton.statics;
publ
- .NET开源核心运行时,且行且珍惜
netcome
java.net开源
背景
2014年11月12日,ASP.NET之父、微软云计算与企业级产品工程部执行副总裁Scott Guthrie,在Connect全球开发者在线会议上宣布,微软将开源全部.NET核心运行时,并将.NET 扩展为可在 Linux 和 Mac OS 平台上运行。.NET核心运行时将基于MIT开源许可协议发布,其中将包括执行.NET代码所需的一切项目——CLR、JIT编译器、垃圾收集器(GC)和核心
- 使用oscahe缓存技术减少与数据库的频繁交互
Everyday都不同
Web高并发oscahe缓存
此前一直不知道缓存的具体实现,只知道是把数据存储在内存中,以便下次直接从内存中读取。对于缓存的使用也没有概念,觉得缓存技术是一个比较”神秘陌生“的领域。但最近要用到缓存技术,发现还是很有必要一探究竟的。
缓存技术使用背景:一般来说,对于web项目,如果我们要什么数据直接jdbc查库好了,但是在遇到高并发的情形下,不可能每一次都是去查数据库,因为这样在高并发的情形下显得不太合理——
- Spring+Mybatis 手动控制事务
toknowme
mybatis
@Override
public boolean testDelete(String jobCode) throws Exception {
boolean flag = false;
&nbs
- 菜鸟级的android程序员面试时候需要掌握的知识点
xp9802
android
熟悉Android开发架构和API调用
掌握APP适应不同型号手机屏幕开发技巧
熟悉Android下的数据存储
熟练Android Debug Bridge Tool
熟练Eclipse/ADT及相关工具
熟悉Android框架原理及Activity生命周期
熟练进行Android UI布局
熟练使用SQLite数据库;
熟悉Android下网络通信机制,S