中小型企业网网络搭建ensp模拟
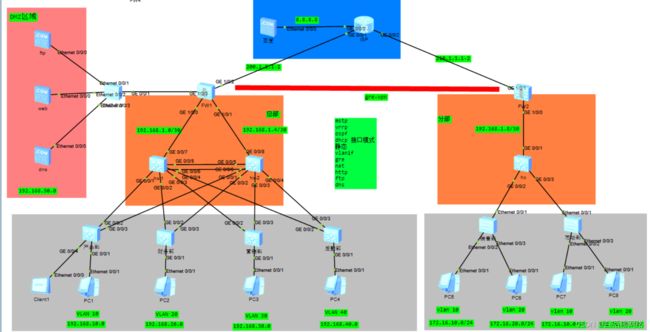
本期模拟中小型企业的万能组网,该场景为总部与分部之间的跨运营商互访,如果拆开来,就是小型企业的内网环境,技术可以任意搭配
场景1:总部部署STP\RSTP\VRRP\OSPF\静态,基于防火墙的GRE VPN\IPSEC VPN、NAT
场景2:总部部署STP\MSTP\VRRP负载\OSPF\静态,基于防火墙的GRE VPN\IPSEC VPN、NAT
场景3:只有总部,没有分部,部署STP\MSTP\VRRP负载\OSPF\静态,基于防火墙的NAT
本期模拟的是场景2,选配GRE隧道方式实现总部与分部之间访问,灰色区域为接入层设备,橘色为核心层设备,直接上配置
总部接入层配置
sysname sw1
#
vlan batch 10
#
stp region-configuration
region-name huawei
instance 1 vlan 10 20
instance 2 vlan 30 40
active region-configuration
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 10
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 10
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 10
#
interface GigabitEthernet0/0/4
port link-type access
port default vlan 10
总部核心交换机1
#
sysname HX-1
#
vlan batch 10 20 30 40 100
#
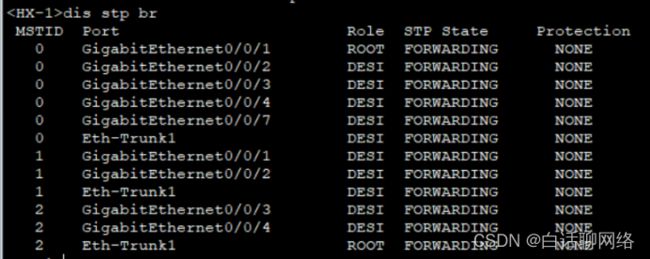
stp instance 1 root primary
stp instance 2 root secondary
#
dhcp enable
#
stp region-configuration
region-name huawei
instance 1 vlan 10 20
instance 2 vlan 30 40
active region-configuration
#
interface Vlanif10
ip address 192.168.10.252 255.255.255.0
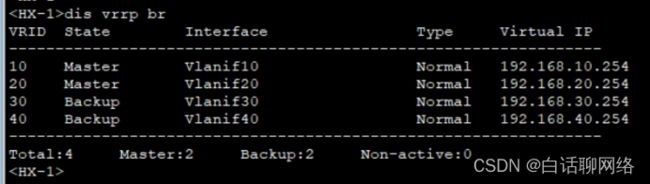
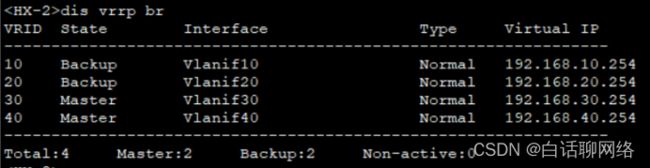
vrrp vrid 10 virtual-ip 192.168.10.254
vrrp vrid 10 priority 120
vrrp vrid 10 track interface GigabitEthernet0/0/7 reduced 30
dhcp select interface
#
interface Vlanif20
ip address 192.168.20.252 255.255.255.0
vrrp vrid 20 virtual-ip 192.168.20.254
vrrp vrid 20 priority 120
vrrp vrid 20 track interface GigabitEthernet0/0/7 reduced 30
dhcp select interface
#
interface Vlanif30
ip address 192.168.30.252 255.255.255.0
vrrp vrid 30 virtual-ip 192.168.30.254
dhcp select interface
#
interface Vlanif40
ip address 192.168.40.252 255.255.255.0
vrrp vrid 40 virtual-ip 192.168.40.254
dhcp select interface
#
interface Vlanif100
ip address 192.168.1.1 255.255.255.252
#
interface Eth-Trunk1
port link-type trunk
port trunk allow-pass vlan 10 20 30 40
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 10
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 20
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 30
#
interface GigabitEthernet0/0/4
port link-type trunk
port trunk allow-pass vlan 40
#
interface GigabitEthernet0/0/5
eth-trunk 1
#
interface GigabitEthernet0/0/6
eth-trunk 1
#
interface GigabitEthernet0/0/7
port link-type access
port default vlan 100
#
ospf 1
area 0.0.0.0
network 192.168.1.1 0.0.0.0
area 0.0.0.1
network 192.168.10.0 0.0.0.255
network 192.168.20.0 0.0.0.255
network 192.168.30.0 0.0.0.255
network 192.168.40.0 0.0.0.255
总部核心交换机2
sysname HX-2
#
vlan batch 10 20 30 40 100
#
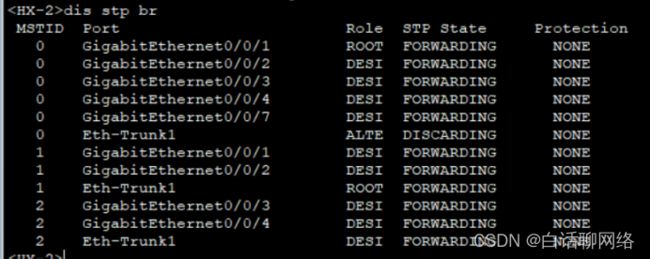
stp instance 1 root secondary
stp instance 2 root primary
#
dhcp enable
#
stp region-configuration
region-name huawei
instance 1 vlan 10 20
instance 2 vlan 30 40
active region-configuration
#
interface Vlanif10
ip address 192.168.10.253 255.255.255.0
vrrp vrid 10 virtual-ip 192.168.10.254
dhcp select interface
#
interface Vlanif20
ip address 192.168.20.253 255.255.255.0
vrrp vrid 20 virtual-ip 192.168.20.254
dhcp select interface
#
interface Vlanif30
ip address 192.168.30.253 255.255.255.0
vrrp vrid 30 virtual-ip 192.168.30.254
vrrp vrid 30 priority 120
vrrp vrid 30 track interface GigabitEthernet0/0/7 reduced 30
dhcp select interface
#
interface Vlanif40
ip address 192.168.40.253 255.255.255.0
vrrp vrid 40 virtual-ip 192.168.40.254
vrrp vrid 40 priority 120
vrrp vrid 40 track interface GigabitEthernet0/0/7 reduced 30
dhcp select interface
#
interface Vlanif100
ip address 192.168.1.5 255.255.255.252
#
interface Eth-Trunk1
port link-type trunk
port trunk allow-pass vlan 10 20 30 40
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 10
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 20
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 30
#
interface GigabitEthernet0/0/4
port link-type trunk
port trunk allow-pass vlan 40
#
interface GigabitEthernet0/0/5
eth-trunk 1
#
interface GigabitEthernet0/0/6
eth-trunk 1
#
interface GigabitEthernet0/0/7
port link-type access
port default vlan 100
#
ospf 1
area 0.0.0.0
network 192.168.1.5 0.0.0.0
area 0.0.0.1
network 192.168.10.0 0.0.0.255
network 192.168.20.0 0.0.0.255
network 192.168.30.0 0.0.0.255
network 192.168.40.0 0.0.0.255
出口防火墙
sysname FW1
interface GigabitEthernet1/0/0
undo shutdown
ip address 192.168.1.2 255.255.255.252
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 192.168.1.6 255.255.255.252
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 200.1.1.1 255.255.255.252
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 192.168.50.254 255.255.255.0
#
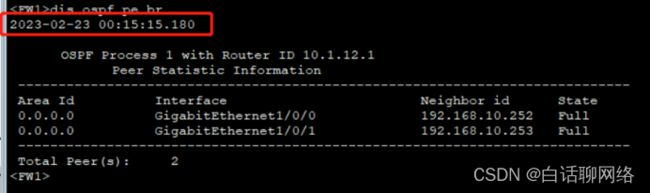
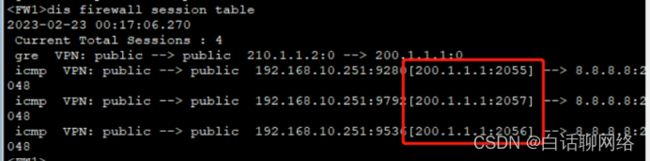
interface Tunnel0
ip address 10.1.12.1 255.255.255.0
tunnel-protocol gre
source 200.1.1.1
destination 210.1.1.2
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/1
add interface Tunnel0
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/2
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/3
#
ospf 1
default-route-advertise
area 0.0.0.0
network 192.168.1.0 0.0.0.3
network 192.168.1.4 0.0.0.3
network 192.168.50.0 0.0.0.255
#
ip route-static 0.0.0.0 0.0.0.0 200.1.1.2
ip route-static 172.16.10.0 255.255.255.0 Tunnel0
ip route-static 172.16.20.0 255.255.255.0 Tunnel0
#
security-policy
rule name t-u
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
source-address 192.168.30.0 mask 255.255.255.0
source-address 192.168.50.0 mask 255.255.255.0
action permit
rule name t-dmz
source-zone trust
destination-zone dmz
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
source-address 192.168.30.0 mask 255.255.255.0
destination-address 192.168.50.0 mask 255.255.255.0
action permit
rule name u-dmz
source-zone untrust
destination-zone dmz
source-address 172.16.10.0 mask 255.255.255.0
source-address 172.16.20.0 mask 255.255.255.0
destination-address 192.168.50.0 mask 255.255.255.0
action permit
rule name l-u
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
action permit
rule name gre
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
source-address 192.168.30.0 mask 255.255.255.0
source-address 192.168.50.0 mask 255.255.255.0
destination-address 172.16.10.0 mask 255.255.255.0
destination-address 172.16.20.0 mask 255.255.255.0
action permit
rule name gre-
source-zone untrust
destination-zone trust
source-address 172.16.10.0 mask 255.255.255.0
source-address 172.16.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.30.0 mask 255.255.255.0
destination-address 192.168.50.0 mask 255.255.255.0
action permit
#
nat-policy
rule name gre
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
source-address 192.168.30.0 mask 255.255.255.0
source-address 192.168.50.0 mask 255.255.255.0
destination-address 172.16.10.0 mask 255.255.255.0
destination-address 172.16.20.0 mask 255.255.255.0
action no-nat
rule name t-u
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
source-address 192.168.30.0 mask 255.255.255.0
action source-nat easy-ip
分部接入交换机
sysname xiaoshoubu
#
vlan batch 10 20
#
interface Ethernet0/0/1
port link-type trunk
port trunk allow-pass vlan 10 20
#
interface Ethernet0/0/2
port link-type access
port default vlan 10
#
interface Ethernet0/0/3
port link-type access
port default vlan 20
分部核心交换机
sysname hx
#
vlan batch 10 20 100
#
stp instance 0 root primary
#
interface Vlanif10
ip address 172.16.10.254 255.255.255.0
#
interface Vlanif20
ip address 172.16.20.254 255.255.255.0
#
interface Vlanif100
ip address 192.168.1.9 255.255.255.252
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 100
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 10 20
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 10 20
#
ospf 1
area 0.0.0.0
network 192.168.1.8 0.0.0.3
network 172.16.10.0 0.0.0.255
network 172.16.20.0 0.0.0.255
分部出口防火墙
sysname FW2
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 192.168.1.10 255.255.255.252
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 210.1.1.2 255.255.255.252
#
interface Tunnel0
ip address 10.1.12.2 255.255.255.0
tunnel-protocol gre
source 210.1.1.2
destination 200.1.1.1
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
add interface Tunnel0
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
firewall zone dmz
set priority 50
#
ospf 1
default-route-advertise
area 0.0.0.0
network 192.168.1.8 0.0.0.3
#
ip route-static 0.0.0.0 0.0.0.0 210.1.1.1
ip route-static 192.168.10.0 255.255.255.0 Tunnel0
ip route-static 192.168.20.0 255.255.255.0 Tunnel0
ip route-static 192.168.30.0 255.255.255.0 Tunnel0
ip route-static 192.168.50.0 255.255.255.0 Tunnel0
#
security-policy
rule name t-u
source-zone trust
destination-zone untrust
source-address 172.16.10.0 mask 255.255.255.0
source-address 172.16.20.0 mask 255.255.255.0
action permit
rule name l-u
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
action permit
rule name gre
source-zone untrust
destination-zone trust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
source-address 192.168.30.0 mask 255.255.255.0
source-address 192.168.50.0 mask 255.255.255.0
destination-address 172.16.10.0 mask 255.255.255.0
destination-address 172.16.20.0 mask 255.255.255.0
action permit
rule name gre-
source-zone trust
destination-zone untrust
source-address 172.16.10.0 mask 255.255.255.0
source-address 172.16.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.30.0 mask 255.255.255.0
destination-address 192.168.50.0 mask 255.255.255.0
action permit
#
nat-policy
rule name gre
source-zone trust
destination-zone untrust
source-address 172.16.10.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.30.0 mask 255.255.255.0
destination-address 192.168.50.0 mask 255.255.255.0
action no-nat
rule name isp
source-zone trust
destination-zone untrust
source-address 172.16.10.0 mask 255.255.255.0
source-address 172.16.20.0 mask 255.255.255.0
action source-nat easy-ip
实验测试验证
MSTP验证
Vrrp验证
Dhcp验证
Ospf验证
Nat验证
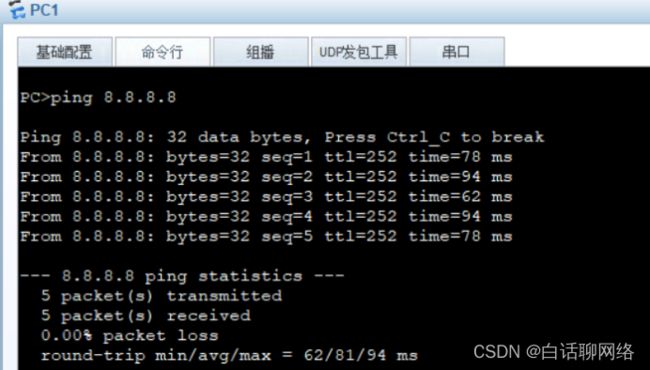
连通性测试
注意:进入隧道的流量,一定要在防火的的nat策略中或路由的高级acl中禁掉,再放行各自的源ip到外网的策略