1.storageclass(存储类)概念
storageclass是一个存储类,k8s集群管理员通过创建storageclass可以动态生成一个存储卷供k8s用户使用。
2.storageclass资源定义
每个StorageClass都包含字段provisioner,parameters和reclaimPolicy,当需要动态配置属于该类的PersistentVolume时使用这些字段。
StorageClass对象的名称很重要,是用户可以请求特定类的方式。管理员在首次创建StorageClass对象时设置类的名称和其他参数,并且在创建对象后无法更新这些对象。
管理员可以为不请求任何特定类绑定的PVC指定默认的StorageClass
(1)yaml文件示例说明:
apiVersion: storage.k8s.io/v1
kind: StorageClass
metadata:
name: standard
provisioner: kubernetes.io/aws-ebs
parameters:
type: gp2
reclaimPolicy: Retain
mountOptions:
- debug
volumeBindingMode: Immediate
(2)Provisioner
storageclass需要有一个供应者,用来确定我们使用什么样的存储来创建pv
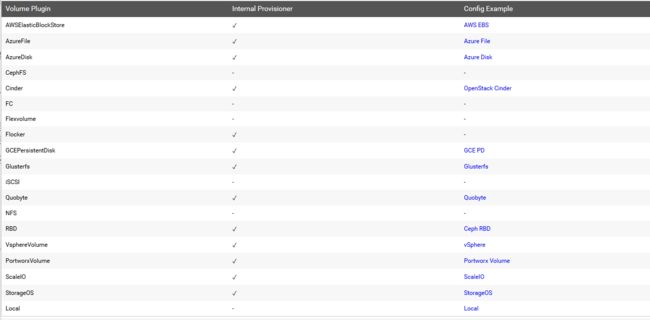
常见的provisioner供应者如下:
provisioner既可以是内部供应程序,也可以由外部供应商提供,如果是外部供应商可以参考https://github.com/kubernetes-incubator/external-storage/下提供的方法创建storageclass的provisioner,例如,NFS不提供内部配置程序,但可以使用外部配置程序。一些外部供应商列在存储库https://github.com/kubernetes-incubator/external-storage下。
nfs的provisioner:
https://github.com/kubernetes-incubator/external-storage/tree/master/nfs/deploy/kubernetes
Reclaim Policy
由存储类动态创建持久化存储卷(pv)时可以指定reclaimPolicy字段,这个字段中指定的回收策略可以是Delete或Retain。如果在创建StorageClass对象时未指定reclaimPolicy,则默认为Delete。
Mount Options(挂载选项)
如果Volume Plugin不支持这个挂载选项,但是指定了,就会使provisioner创建失败
Volume Binding Mode
这个字段用来说明什么时候进行卷绑定和动态配置;
默认情况下,立即模式表示一旦创建了PersistentVolumeClaim,就会发生卷绑定和动态配置。对于受拓扑约束且无法从群集中的所有节点全局访问的存储后端,将在不知道Pod的调度要求的情况下绑定或配置PersistentVolumes。这可能导致不可调度的Pod。
集群管理员可以通过指定WaitForFirstConsumer模式来解决此问题,该模式将延迟绑定和配置PersistentVolume,直到创建使用PersistentVolumeClaim的Pod。将根据Pod的调度约束指定的拓扑选择或配置PersistentVolumes。这些包括但不限于资源需求,节点选择器,pod亲和力和反亲和力,以及污点和容忍度。
通过nfs实现存储类的动态供给
1.安装nfs服务
选择自己的任意一台机器,我选择k8s的master1节点,对应的机器ip是192.168.0.6,在192.168.0.6上执行如下步骤,大家在自己环境找一台k8s节点的机器安装就可以了~
(1)yum安装nfs
yum install nfs-utils -y
systemctl start nfs
chkconfig nfs on
(2)在master1上创建一个nfs共享目录
mkdir /data/nfs_pro -p
#修改/etc/exports文件,把刚才生成的共享目录添加到这个文件里
cat /etc/exports
/data/nfs_pro 192.168.0.0/24(rw,no_root_squash)
让刚才配置文件生效
exportfs -arv
systemctl restart nfs
(3)k8s的各个node节点也需要安装nfs
yum install nfs-utils -y
systemctl start nfs
chkconfig nfs on
2.创建运行nfs-provisioner的sa账号
cat serviceaccount.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: nfs-provisioner
通过kubectl更新yaml文件
kubectl apply -f serviceaccount.yaml
3.对sa账号做rbac授权
cat service-rbac.yaml
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: nfs-provisioner-runner
rules:
- apiGroups: [""]
resources: ["persistentvolumes"]
verbs: ["get", "list", "watch", "create", "delete"]
- apiGroups: [""]
resources: ["persistentvolumeclaims"]
verbs: ["get", "list", "watch", "update"]
- apiGroups: ["storage.k8s.io"]
resources: ["storageclasses"]
verbs: ["get", "list", "watch"]
- apiGroups: [""]
resources: ["events"]
verbs: ["create", "update", "patch"]
- apiGroups: [""]
resources: ["services", "endpoints"]
verbs: ["get"]
- apiGroups: ["extensions"]
resources: ["podsecuritypolicies"]
resourceNames: ["nfs-provisioner"]
verbs: ["use"]
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: run-nfs-provisioner
subjects:
- kind: ServiceAccount
name: nfs-provisioner
namespace: default
roleRef:
kind: ClusterRole
name: nfs-provisioner-runner
apiGroup: rbac.authorization.k8s.io
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: leader-locking-nfs-provisioner
rules:
- apiGroups: [""]
resources: ["endpoints"]
verbs: ["get", "list", "watch", "create", "update", "patch"]
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: leader-locking-nfs-provisioner
subjects:
- kind: ServiceAccount
name: nfs-provisioner
namespace: default
roleRef:
kind: Role
name: leader-locking-nfs-provisioner
apiGroup: rbac.authorization.k8s.io
通过kubectl更新yaml文件
kubectl apply -f service-rbac.yaml
4.通过deployment创建pod用来运行nfs-provisioner
cat deployment.yaml
kind: Deployment
apiVersion: apps/v1
metadata:
name: nfs-provisioner
spec:
selector:
matchLabels:
app: nfs-provisioner
replicas: 1
strategy:
type: Recreate
template:
metadata:
labels:
app: nfs-provisioner
spec:
serviceAccount: nfs-provisioner
containers:
- name: nfs-provisioner
image: registry.cn-hangzhou.aliyuncs.com/open-ali/nfs-client-provisioner:latest
volumeMounts:
- name: nfs-client-root
mountPath: /persistentvolumes
env:
- name: PROVISIONER_NAME
value: example.com/nfs
- name: NFS_SERVER
value: 192.168.0.6
- name: NFS_PATH
value: /data/storage
volumes:
- name: nfs-client-root
nfs:
server: 192.168.0.6
path: /data/storage
通过kubectl更新yaml文件
kubectl apply -f deployment.yaml
查看nfs provisioner的pod是否创建成功
kubectl get pods
显示如下,说明创建成功
NAME READY STATUS RESTARTS AGE
nfs-provisioner-7d6859cc59-pzr7n 1/1 Running 0 72s
创建storageclass
cat class.yaml
kind: StorageClass
apiVersion: storage.k8s.io/v1
metadata:
name: nfs-storage
provisioner: example.com/nfs
通过kubectl更新yaml文件
kubectl apply -f class.yaml
查看storageclass是否创建成功
kubectl get storageclass
显示如下,说明创建成功
NAME PROVISIONER RECLAIMPOLICY VOLUMEBINDINGMODE ALLOWVOLUMEEXPANSION AGE
nfs-storage example.com/nfs Delete Immediate false 11h
通过helm部署gitlab
1、解压gitlab-ce.tar.gz
tar zxvf gitlab-ce.tar.gz
2、进入到解压路径,通过helm安装gitlab、postgresql、redis
cd gitlab-ce
通过helm安装部署helm install .
查看是否部署成功
kubectl get pods
显示如下,看到STATUS都是running状态,说明部署成功
NAME READY STATUS RESTARTS AGE
alliterating-quail-gitlab-ce-756ddcb6d5-rwnzj 1/1 Running 0 3m56s
alliterating-quail-postgresql-68bc89cd7f-slt6g 1/1 Running 0 3m56s
alliterating-quail-redis-7954fbbfbc-5jqfx 1/1 Running 0 3m56s
查看gitlab在宿主机暴露的端口
kubectl get svc | grep gitlab
alliterating-quail-gitlab-ce NodePort 10.105.171.114 22:32503/TCP,80:31572/TCP,443:32
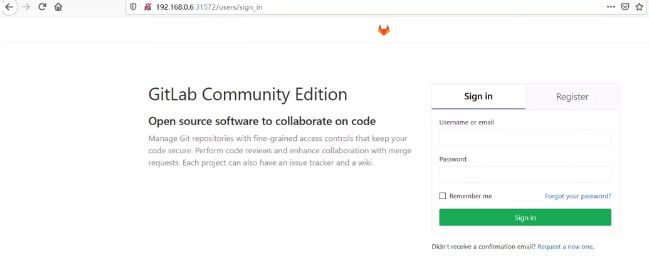
通过上面可以看到容器里的80端口在宿主机映射的端口是31572,所以浏览器访问k8s的master1节点ip:31572即可,我在浏览器访问如下地址:
192.168.0.6:31572
默认的用户名和密码分别是:
root
gitlab0920
输入用户名和密码之后即可登陆到gitlab的web界面
gitlab-ce.tar.gz里涉及的Chart文件说明讲解
1.上面的压缩包解压之后,在gitlab-ce目录下,有个values.yaml文件,内容及解释如下
## GitLab CE image
## ref: https://hub.docker.com/r/gitlab/gitlab-ce/tags/
##
image: gitlab/gitlab-ce:10.6.2-ce.0
#gitlab使用的镜像,我们安装的是10版本
## Specify a imagePullPolicy
## 'Always' if imageTag is 'latest', else set to 'IfNotPresent'
## ref: http://kubernetes.io/docs/user-guide/images/#pre-pulling-images
##
# imagePullPolicy:
imagePullPolicy: IfNotPresent
#镜像拉取策略,IfNotPresent表示本地不存在,就从官方拉取
## The URL (with protocol) that your users will use to reach the install.
## ref: https://docs.gitlab.com/omnibus/settings/configuration.html#configuring-the-external-url-for-gitlab
##
externalUrl: http://gitlab.lucky.com/
#可访问的域名,这里我随便写了有一个,暂时用不到
## Change the initial default admin password if set. If not set, you'll be
## able to set it when you first visit your install.
##
gitlabRootPassword: "gitlab0920"
#登陆gitlab web界面的密码,可以随便写,符合密码复杂度即可
#登陆gitlab web界面的默认用户是root
## For minikube, set this to NodePort, elsewhere use LoadBalancer
## ref: http://kubernetes.io/docs/user-guide/services/#publishing-services---service-types
##
serviceType: NodePort
#service的类型,NodePort表示暴露出来的服务可以在k8s集群外部访问
## Ingress configuration options
##
ingress:
annotations:
# kubernetes.io/ingress.class: nginx
# kubernetes.io/tls-acme: "true"
enabled: false
tls:
# - secretName: gitlab.cluster.local
# hosts:
# - gitlab.cluster.local
url: gitlab.cluster.local
#上面是ingress相关的,暂时我们用不到
## Configure external service ports
## ref: http://kubernetes.io/docs/user-guide/services/
sshPort: 22
#容器里暴露的22端口
httpPort: 80
#容器里暴露的80端口
httpsPort: 443
#容器里暴露的443端口
## livenessPort Port of liveness probe endpoint
livenessPort: http
## readinessPort Port of readiness probe endpoint
readinessPort: http
## Configure resource requests and limits
## ref: http://kubernetes.io/docs/user-guide/compute-resources/
##
resources:
## GitLab requires a good deal of resources. We have split out Postgres and
## redis, which helps some. Refer to the guidelines for larger installs.
## ref: https://docs.gitlab.com/ce/install/requirements.html#hardware-requirements
requests:
memory: 1Gi
cpu: 500m
limits:
memory: 2Gi
cpu: 1
## Enable persistence using Persistent Volume Claims
## ref: http://kubernetes.io/docs/user-guide/persistent-volumes/
## ref: https://docs.gitlab.com/ce/install/requirements.html#storage
##
persistence:
#下面配置的是跟持久化存储相关的内容
## This volume persists generated configuration files, keys, and certs.
##
gitlabEtc:
enabled: true
size: 1Gi
## If defined, volume.beta.kubernetes.io/storage-class:
## Default: volume.alpha.kubernetes.io/storage-class: default
##
storageClass: "nfs-storage"
#开启了storageclass,这里的storageclass是nfs-storage,
#就是我们上面创建的那个nfs-storage
accessMode: ReadWriteOnce
#访问模式,单路独写
## This volume is used to store git data and other project files.
## ref: https://docs.gitlab.com/omnibus/settings/configuration.html#storing-git-data-in-an-alternative-directory
##
gitlabData:
enabled: true
size: 10Gi
## If defined, volume.beta.kubernetes.io/storage-class:
## Default: volume.alpha.kubernetes.io/storage-class: default
##
storageClass: "nfs-storage"
#开启了storageclass,这里的storageclass是nfs-storage,
#就是我们上面创建的那个nfs-storage
accessMode: ReadWriteOnce
#访问模式,单路独写
## Configuration values for the postgresql dependency.
## ref: https://github.com/kubernetes/charts/blob/master/stable/postgresql/README.md
##
postgresql:
# 9.6 is the newest supported version for the GitLab container
imageTag: "9.6.5"
cpu: 1000m
memory: 1Gi
postgresUser: gitlab
postgresPassword: gitlab
postgresDatabase: gitlab
persistence:
size: 10Gi
storageClass: "nfs-storage"
## Configuration values for the redis dependency.
## ref: https://github.com/kubernetes/charts/blob/master/stable/redis/README.md
##
redis:
redisPassword: "gitlab"
resources:
requests:
memory: 1Gi
persistence:
size: 10Gi
storageClass: "nfs-storage"
#开启了storageclass,这里的storageclass是nfs-storage,
#就是我们上面创建的那个nfs-storage
原文:https://mp.weixin.qq.com/s/vOI1o7iH6gz4-aqwzZQyGQ