CentOS7 配置OpenLDAP(一) 配置OpenLDAP服务单节点模式并实现服务器登录管理常见场景
参考索引
第1篇:配置OpenLDAP服务单节点模式
第2篇:配置OpenLDAP主从架构(Replication模式)
第3篇:配置OpenLDAP多主模式(镜像模式)
单节点配置OpenLDAP服务并实现服务器登录管理常见场景
1. 环境信息介绍
1.1 实现场景
- 客户端服务器可以通过openldap账户实现登录
- 客户端服务器可以通过openldap账户实现秘钥登录
- 可以通过openldap控制指定账户允许登录的主机列表
- 客户端服务可以通过openldap管理账户的sudo权限
- OpenLDAP启用MemberOf属性[默认未启用]
- 基于浏览器的openldap管理工具phpldapadmin配置
- windows下的局域网内管理openldap的工具ldapadmin
1.2 环境信息
| 主机名称 | 地址 | 版本 | 角色 | 备注 |
|---|---|---|---|---|
| sysldap-shylf-1 | 10.116.72.11 | CentOS7.6 min | openLdap, httpd, phpldapadmin | |
| sysldap-shylf-2 | 10.116.72.12 | CentOS7.6 min | openLdap, httpd, phpldapadmin | 本文没有用到 |
| systerm-shylf-1 | 10.116.72.15 | CentOS7.6 min | openLdap client |
前提条件,为了方便配置防火墙以及禁用selinux
配置示例:dc=example,dc=com
2. OpenLDAP服务端配置
创建一个配置目录,将相关配置文件放在这个目录下面
openldap
├── base.ldif
├── config.ldif
├── demo.ldif
├── loglevel.ldif
├── schema
│ ├── sudo.ldif
│ └── sudo.schema
├── sudo_ops_role.ldif
└── SUODers.ldif
cd openldap
2.1 安装LDAP组件并启动服务
yum -y install openldap openldap-clients openldap-servers
# 3. 建立Ldap数据库
cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
chown ldap:ldap /var/lib/ldap/*
systemctl start slapd.service
systemctl enable slapd.service
netstat -antup | grep -i 389
tcp 0 0 0.0.0.0:389 0.0.0.0:* LISTEN 16349/slapd
tcp6 0 0 :::389 :::* LISTEN 16349/slapd
2.2 配置OpenLDAP服务
# 1. 生成Ldap root密码
~]# slappasswd
New password: openldap
Re-enter new password: openldap
{SSHA}npo7WhvpY+s4+p584zAnoduStQzeTxHE
#-------------------------------------------
# 2. 添加需要的schemas [可以根据需要添加更多]
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
#-------------------------------------------
# 3. 配置openLDAP服务
vi config.ldif
dn: olcDatabase={1}monitor,cn=config
changetype: modify
replace: olcAccess
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external, cn=auth" read by dn.base="cn=Manager,dc=example,dc=com" read by * none
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcSuffix
olcSuffix: dc=example,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootDN
olcRootDN: cn=Manager,dc=example,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootPW
olcRootPW: {SSHA}npo7WhvpY+s4+p584zAnoduStQzeTxHE
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcAccess
olcAccess: {0}to attrs=userPassword,shadowLastChange by dn="cn=Manager,dc=example,dc=com" write by anonymous auth by self write by * none
olcAccess: {1}to dn.base="" by * read
olcAccess: {2}to * by dn="cn=Manager,dc=example,dc=com" write by * read
# 发送配置到LDAP服务
ldapmodify -Y EXTERNAL -H ldapi:/// -f config.ldif
#-------------------------------------------
# 4. 域example.com配置
vi base.ldif
dn: dc=example,dc=com
o: example com
dc: example
objectClass: top
objectClass: dcObject
objectClass: organization
dn: cn=Manager,dc=example,dc=com
objectClass: organizationalRole
cn: Manager
description: LDAP Manager
dn: ou=People,dc=example,dc=com
objectClass: organizationalUnit
ou: People
dn: ou=Group,dc=example,dc=com
objectClass: organizationalUnit
ou: Group
# 发送配置到LDAP服务
ldapadd -x -W -D "cn=Manager,dc=example,dc=com" -f base.ldif
# 5. 配置ldap log
vi loglevel.ldif
dn: cn=config
changetype: modify
replace: olcLogLevel
olcLogLevel: stats
# 发送配置到LDAP服务
ldapmodify -Y EXTERNAL -H ldapi:/// -f loglevel.ldif
vi /etc/rsyslog.conf
...
local4.* /var/log/openldap.log
vi /etc/logrotate.d/slapd
/var/log/openldap.log {
rotate 14
size 10M
missingok
compress
copytruncate
}
systemctl restart rsyslog
# 如果有需要还可以配置日志轮转
# 6. 创建一个测试用户
# 可以先生成一个加密的密码,或者单独修改密码
slappasswd -h {SHA} -s 'passwd@123'
{SHA}+M6FvbHGI6Jmf/8gMv6RbIvC4C4=
vi demo.ldif
dn: uid=800001,ou=People,dc=example,dc=com
objectClass: top
objectClass: account
objectClass: posixAccount
objectClass: shadowAccount
cn: demo
uid: 800001
uidNumber: 3000
gidNumber: 100
homeDirectory: /home/ldapusers
loginShell: /bin/bash
gecos: Demo [Demo user (at) example]
userPassword: {crypt}x # 后面单独修改密码
# userPassword: {SHA}+M6FvbHGI6Jmf/8gMv6RbIvC4C4= #也可以使用预先生成的加密密码
shadowLastChange: 17058
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
dn: cn=ops,ou=Group,dc=example,dc=com
objectClass: posixGroup
objectClass: top
cn: ops
gidNumber: 80001
memberUid: 800001
ldapadd -x -W -D "cn=Manager,dc=example,dc=com" -f demo.ldif
ldappasswd -s 'passwd@123' -W -D "cn=Manager,dc=example,dc=com" -x "uid=800001,ou=People,dc=example,dc=com"
ldapsearch -x uid=800001 -b dc=example,dc=com
//删除使用如下命令
ldapdelete -W -D "cn=Manager,dc=example,dc=com" -x "uid=800001,ou=People,dc=example,dc=com"
3. ldap客户端配置
# 1. 安装组件
yum install -y openldap-clients nss-pam-ldapd
# 2. 添加client服务器到LDAP服务
authconfig --enableldap --enableldapauth --ldapserver="10.116.72.11" --ldapbasedn="dc=example,dc=com" --update
# 这个指令修改了/etc/nsswitch.conf 以及/etc/openldap/ldap.conf文件
# 3. 启动ldap客户端服务
systemctl restart nslcd
# 4. 验证
getent passwd 800001
800001:3000:100:Demo [Demo user (at) example]:/home/demo:/bin/bash
# 5. 远程ssh登录验证
ssh [email protected]
[email protected]'s password: demopassword
-bash-4.2$ id 800001
uid=3000(800001) gid=100(users) groups=100(users),80001(ops)
-bash-4.2$
# 这里可以看到没有配置自动生成账户的家目录,在实际的运维过程中,也不会去生成家目录(不然一堆的账户加目录),而是让运维账户统一一个家目录,并且设置为只读。
# 不过如果有需要配置配置家目录自动生成,需要修改pam模块
4. 配置LDAP使用公钥(publicKey)远程ssh登录客户主机
4.1 openldap服务端配置
# 1. 安装openssh-ldap
yum install openssh-ldap
rpm -aql |grep openssh-ldap
/usr/share/doc/openssh-ldap-7.4p1
/usr/share/doc/openssh-ldap-7.4p1/HOWTO.ldap-keys
/usr/share/doc/openssh-ldap-7.4p1/ldap.conf
/usr/share/doc/openssh-ldap-7.4p1/openssh-lpk-openldap.ldif
/usr/share/doc/openssh-ldap-7.4p1/openssh-lpk-openldap.schema
/usr/share/doc/openssh-ldap-7.4p1/openssh-lpk-sun.ldif
/usr/share/doc/openssh-ldap-7.4p1/openssh-lpk-sun.schema
# 2. 配置添加相关schema
cp /usr/share/doc/openssh-ldap-7.4p1/openssh-lpk-openldap.ldif /etc/openldap/schema/
cp /usr/share/doc/openssh-ldap-7.4p1/openssh-lpk-openldap.schema /etc/openldap/schema/
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/openssh-lpk-openldap.ldif
# 3. 账户添加objectClass: ldapPublicKey 并添加属性sshPublicKey
# 具体修改流程,可以使用下面安装的ldapadmin或者phpldapadmin进行配置
objectClass: ldapPublicKey
sshPublicKey: 值是具体的publickey
4.2 客户主机配置
yum install openssh-ldap
cp /usr/share/doc/openssh-ldap-7.4p1/ldap.conf /etc/ssh/
# 如果使用TLS 配置TLS,这里不使用
vi /etc/ssh/ldap.conf
ssl no
uri ldap://10.116.72.11/
vi /etc/ssh/sshd_config
# 脚本将从LDAP获取密钥并将其提供给SSH服务器
AuthorizedKeysCommand /usr/libexec/openssh/ssh-ldap-wrapper
AuthorizedKeysCommandUser nobody
PubkeyAuthentication yes
4.3 登录验证
ssh -i ~/.ssh/id_rsa [email protected]
Last login: Thu Jul 4 16:15:30 2019 from 10.116.71.200
Could not chdir to home directory /home/demo: No such file or directory
-bash-4.2$
5. 配置LDAP账户可以登录的主机列表
测试使用的远程ssh服务器是10.116.72.15,我们验证如下
- 添加账户主机列表(host属性)不包含116.116.72.15 测试是否可以正常登录
- 添加账户主机列表(host属性)包含116.116.72.15 测试是否可以正常登录
5.1 需要通过Ldap远程登录的客户机配置
vi /etc/nsswitch.conf
# 添加如下过滤配置,包含本机主机名称。表示过滤匹配包括本机IP或者允许任意IP地址的账户授权信息
filter passwd (|(host=10.116.72.15)(host=\*))(host=ALL)
备注:如果远程主机是centos6,配置稍有不同
vi /etc/pam_ldap.conf
pam_filter |(host=10.116.72.16)(host=\*)(host=ALL)
5.2 LDAP账户配置
ldap命令或者ldapadmin管理工具为账户添加属性host,这个属性可以添加多次。
- 第一次配置不包含测试主机10.116.72.15
ldapsearch -x uid=800001 -b 'ou=People,dc=example,dc=com'
dn: uid=800001,ou=People,dc=example,dc=com
objectClass: top
objectClass: account
objectClass: posixAccount
objectClass: shadowAccount
cn: demo
uid: 800001
uidNumber: 3000
gidNumber: 100
homeDirectory: /home/demo
loginShell: /bin/bash
gecos: Demo [Admin (at) eju]
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
host: 10.116.72.12
host: 10.116.72.16
测试登录
# ssh [email protected]
[email protected]'s password:
Permission denied, please try again.
- 第二次配置包含测试主机10.116.72.15
ldapsearch -x uid=800001 -b 'ou=People,dc=example,dc=com'
dn: uid=800001,ou=People,dc=example,dc=com
objectClass: top
objectClass: account
objectClass: posixAccount
objectClass: shadowAccount
cn: demo
uid: 800001
uidNumber: 3000
gidNumber: 100
homeDirectory: /home/demo
loginShell: /bin/bash
gecos: Demo [Admin (at) eju]
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
host: 10.116.72.12
host: 10.116.72.15
host: 10.116.72.16
测试登录
# ssh [email protected]
[email protected]'s password:
Last login: Thu Jul 4 16:15:30 2019 from 10.116.71.200
Could not chdir to home directory /home/demo: No such file or directory
-bash-4.2$
以上,测试通过。
6. OpenLDAP启用MemberOf属性[默认未启用]
默认情况下OpenLDAP的用户组属性是Posixgroup,Posixgroup用户组和用户没有实际的对应关系。如果需要把Posixgroup和user关联起来则需要将用户添加到对应的组中。
很多场景下,我们需要快速的查询指定一个用户是属于哪一个或多个组(memberof),例如gitlab,jenkins,harbor集成openLDAP的时候。memberOf 属性提供了这样的功能:如果指定groupOfUniqueNames用户组中通过 uniquemember 属性新增了一个用户,OpenLDAP 便会自动在该用户上创建一个 memberOf 属性,其值为该组的 dn。
6.1 注册memberof模块
- 不同发行版memberof模块的路径不同,centos7 rpm包安装(Yum),模块路径为/usr/lib64/openldap
# find / -name memberof.la
/usr/lib64/openldap/memberof.la
# ll /etc/openldap/slapd.d/cn\=config
-rw------- 1 ldap ldap 562 Jun 30 16:18 cn=module{0}.ldif
drwxr-x--- 2 ldap ldap 161 Jul 4 2019 cn=schema
-rw------- 1 ldap ldap 378 Jul 4 2019 cn=schema.ldif
-rw------- 1 ldap ldap 513 Jul 4 2019 olcDatabase={0}config.ldif
-rw------- 1 ldap ldap 443 Jul 4 2019 olcDatabase={-1}frontend.ldif
-rw------- 1 ldap ldap 607 Jul 4 2019 olcDatabase={1}monitor.ldif
drwxr-x--- 2 ldap ldap 243 Jul 1 10:57 olcDatabase={2}hdb # 注意这个名字,需要使用可能会有所不同
-rw------- 1 ldap ldap 1249 Jul 4 2019 olcDatabase={2}hdb.ldif
- 编辑一个文件,加载memberof模块使用
touch memberof.ldif; vi memberof.ldif
dn: cn=module,cn=config
cn: module
objectClass: olcModuleList
olcModuleLoad: memberof
olcModulePath: /usr/lib64/openldap
dn: olcOverlay={0}memberof,olcDatabase={2}hdb,cn=config
objectClass: olcConfig
objectClass: olcMemberOf
objectClass: olcOverlayConfig
objectClass: top
olcOverlay: memberof
olcMemberOfDangling: ignore
olcMemberOfRefInt: TRUE
olcMemberOfGroupOC: groupOfUniqueNames
olcMemberOfMemberAD: uniqueMember
olcMemberOfMemberOfAD: memberOf
备注:老的版本是groupOfNames,member. 新版本是groupOfUniqueNames和uniqueMember。
- 执行
ldapadd加载模块
ldapadd -Q -Y EXTERNAL -H ldapi:/// -f memberof.ldif
- 验证
ll /etc/openldap/slapd.d/cn\=config
-rw------- 1 ldap ldap 562 Jun 30 16:18 cn=module{0}.ldif
-rw------- 1 ldap ldap 565 Jul 1 10:39 cn=module{1}.ldif # 这个就是执行后的生成文件,编号记住需要使用
drwxr-x--- 2 ldap ldap 161 Jul 4 2019 cn=schema
-rw------- 1 ldap ldap 378 Jul 4 2019 cn=schema.ldif
-rw------- 1 ldap ldap 513 Jul 4 2019 olcDatabase={0}config.ldif
-rw------- 1 ldap ldap 443 Jul 4 2019 olcDatabase={-1}frontend.ldif
-rw------- 1 ldap ldap 607 Jul 4 2019 olcDatabase={1}monitor.ldif
drwxr-x--- 2 ldap ldap 243 Jul 1 10:57 olcDatabase={2}hdb
-rw------- 1 ldap ldap 1249 Jul 4 2019 olcDatabase={2}hdb.ldif
6.2 memberof模块加载refint
- 编辑一个文件,
修改memberof模块,加载refint
注意 dn: cn=module{1},cn=config 这里的编号是1,每个环境可能不同,被弄错了。
touch refint1.ldif;vi refint1.ldif
dn: cn=module{1},cn=config
add: olcmoduleload
olcmoduleload: refint
- 执行
ldapmodify
ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f refint1.ldif
6.3 refint2.ldif
- 编辑一个文件,添加schema
touch refint2.ldif;vi refint2.ldif
dn: olcOverlay={1}refint,olcDatabase={2}hdb,cn=config
objectClass: olcConfig
objectClass: olcOverlayConfig
objectClass: olcRefintConfig
objectClass: top
olcOverlay: {1}refint
olcRefintAttribute: memberof member manager owner
- 执行 ldapadd
ldapadd -Q -Y EXTERNAL -H ldapi:/// -f refint2.ldif
6.4 验证
- 查看当前dn下包含cn=config配置列表会显示出已生效的memberof和refint配置
# ldapsearch -Q -LLL -Y EXTERNAL -H ldapi:/// -b cn=config dn | grep olcOverlay
dn: olcOverlay={0}memberof,olcDatabase={2}hdb,cn=config
dn: olcOverlay={1}refint,olcDatabase={2}hdb,cn=config
- 添加用户和组并查看
# 用户
cat add_user.ldif
dn: uid=800006,ou=People,dc=example,dc=com
objectClass: top
objectClass: account
objectClass: posixAccount
objectClass: shadowAccount
cn: 800006
uid: 800006
uidNumber: 3006
gidNumber: 100
userPassword: 123456
loginShell: /bin/bash
homeDirectory: /home/demo
shadowLastChange: 17058
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
# 组
cat add_group.ldif
dn: cn=harbor,ou=Group,dc=example,dc=com
objectClass: groupOfUniqueNames
cn: harbor
uniqueMember: uid=800006,ou=People,dc=example,dc=com
# 执行
ldapadd -x -w -D "cn=Manager,dc=example,dc=com" -f add_user.ldif
ldapadd -x -W -D "cn=Manager,dc=example,dc=com" -f add_group.ldif
# 查看验证
# ldapsearch -LL -Y EXTERNAL -H ldapi:/// "(cn=harbor)" -b dc=example,dc=com
dn: cn=harbor,ou=Group,dc=example,dc=com
objectClass: groupOfUniqueNames
cn: harbor
uniqueMember: uid=800006,ou=People,dc=example,dc=com
# ldapsearch -LL -Y EXTERNAL -H ldapi:/// "(uid=800006)" -b dc=example,dc=com memberof
dn: uid=800006,ou=People,dc=example,dc=com
memberOf: cn=harbor,ou=Group,dc=example,dc=com #看到这个说明配置成功了。
7. 配置LDAP sudo权限管理
7.1 服务配置
CentOS7.6下more安装的OpenLDAP是2.4.44 ,schema目录下并没有sudo.ldif以及sudo.schema文件,需要单独处理。 sudo是默认安装的,sudo相关目录下有sudo.schema模板文件schema.OpenLDAP
find / -name schema.OpenLDAP -exec cp {} /etc/openldap/schema/sudo.schema \;
# 生成sudo.ldif
echo 'include /etc/openldap/schema/sudo.schema' > /tmp/sudo.conf
mkdir /tmp/sudo
slaptest -f /tmp/sudo.conf -F /tmp/sudo
vi /tmp/sudo/cn=config/cn=schema/cn={0}sudo.ldif
替换(前3行)
dn: cn={0}sudo
objectClass: olcSchemaConfig
cn: {0}sudo
为
dn: cn=sudo,cn=schema,cn=config
objectClass: olcSchemaConfig
cn: sudo
删除(最后7行)
structuralObjectClass: olcSchemaConfig
entryUUID: ec3b659a-31a9-1039-90ae-87c69280e4a2
creatorsName: cn=config
createTimestamp: 20190703064542Z
entryCSN: 20190703064542.945991Z#000000#000#000000
modifiersName: cn=config
modifyTimestamp: 20190703064542Z
cp /tmp/sudo/cn=config/cn=schema/cn={0}sudo.ldif /etc/openldap/schema/sudo.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/sudo.ldif
rm -f /tmp/sudo.conf /tmp/sudo
7.2 权限配置
vi SUODers.ldif
dn: ou=SUDOers,dc=example,dc=com
ou: SUDOers
objectClass: top
objectClass: organizationalUnit
dn: cn=defaults,ou=SUDOers,dc=example,dc=com
objectClass: sudoRole
cn: defaults
sudoOption: requiretty
sudoOption: !visiblepw
sudoOption: always_set_home
sudoOption: env_reset
sudoOption: env_keep = "COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR LS_COLORS"
sudoOption: env_keep += "MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE"
sudoOption: env_keep += "LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES"
sudoOption: env_keep += "LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE"
sudoOption: env_keep += "LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY"
sudoOption: secure_path = /sbin:/bin:/usr/sbin:/usr/bin
sudoOption: logfile = /var/log/sudo
ldapadd -x -W -D "cn=Manager,dc=example,dc=com" -f SUODers.ldif
7.3 将上面的demo(800001)账户配置为sudo权限
这里配置一个运维sudo role,名称为sudo_ops_role,简单配置为sudo 到root所有权限,并将800001加入该role
vi sudo_ops_role.ldif
dn: cn=sudo_ops_role,ou=SUDOers,dc=example,dc=com
objectClass: sudoRole
cn: sudo_ops_role
sudoOption: !authenticate
sudoRunAsUser: root
sudoCommand: ALL
sudoHost: ALL
sudoUser: 800001
ldapadd -x -W -D "cn=Manager,dc=example,dc=com" -f sudo_ops_role.ldif
7.4 客户端增加如下配置
vi /etc/nsswitch.conf
# 追加内存
sudoers: files ldap
mv /etc/sudo-ldap.conf{,.bak}
vi /etc/sudo-ldap.conf
uri ldap://10.116.72.11/
base dc=example,dc=com
sudoers_base ou=SUDOers,dc=example,dc=com
测试
# ssh [email protected]
[email protected]'s password:
Could not chdir to home directory /home/ldapusers: No such file or directory
-bash-4.2$ sudo su -
Last login: Wed Jul 3 15:09:21 CST 2019 from 10.116.71.200 on pts/0
[root@systerm-shylf-1 ~]#
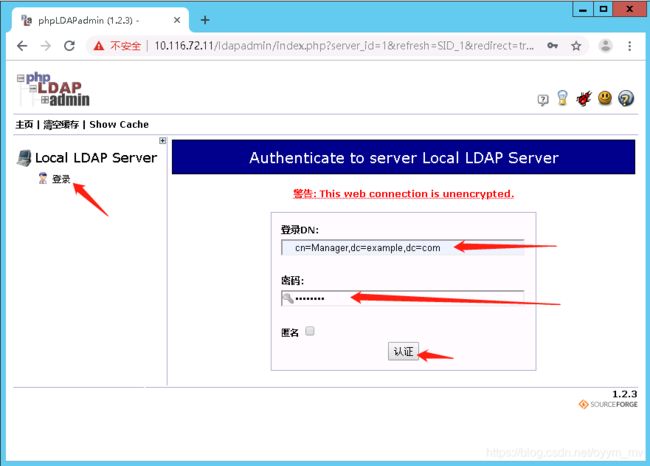
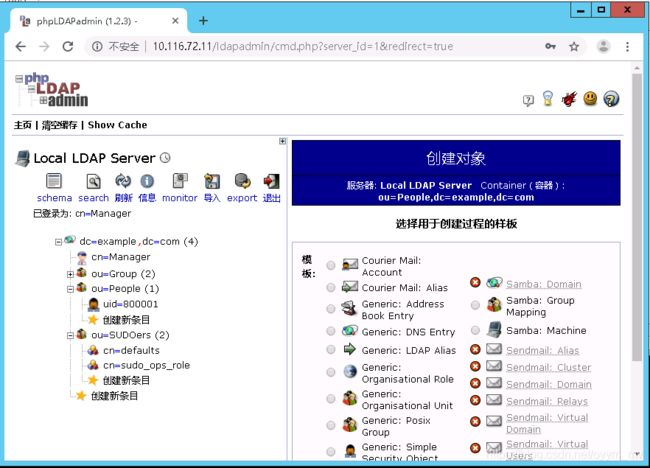
8. 基于web的OpenLDAP管理工具phpldapadmin
实例在openldap安装,实际使用中可以部署在其他服务器上通过网络访问。前端还可以配置一个nginx去代理实现高可用
8.1 安装配置phpldapadmin
# 1. 安装组件
yum -y install epel-release
yum -y install httpd phpldapadmin
# yum安装后的项目文件位置/usr/share/phpldapadmin/htdocs,配置文件位置/etc/phpldapadmin/config.php
# 2. phpldapadmin修改
vi /etc/phpldapadmin/config.php
# 注释掉
//$servers->setValue('login','attr','uid');
# 或者修改为
$servers->setValue('login','attr','dn');
$servers->newServer('ldap_pla');
$servers->setValue('server','name','LDAP Server');
$servers->setValue('server','host','127.0.0.1'); //根据需要修改为实际地址,这个部署到openldap本机直接保留127.0.0.1
$servers->setValue('server','port',389);
$servers->setValue('server','base',array('dc=example,dc=com')); //
$servers->setValue('login','auth_type','cookie');
$servers->setValue('login','bind_id','cn=Manager,dc=example,dc=com');
$servers->setValue('login','bind_pass','');
$servers->setValue('server','tls',false);
# 3. httpd修改
vi /etc/httpd/conf.d/phpldapadmin.conf
Alias /phpldapadmin /usr/share/phpldapadmin/htdocs
Alias /ldapadmin /usr/share/phpldapadmin/htdocs
<Directory /usr/share/phpldapadmin/htdocs>
<IfModule mod_authz_core.c>
# Apache 2.4
# Require local
Require all granted
</IfModule>
<IfModule !mod_authz_core.c>
# Apache 2.2
Order Deny,Allow
Deny from all
Allow from 127.0.0.1
Allow from ::1
# 根据需要配置许可
Allow from 10.116
</IfModule>
</Directory>
# 4. 启动httpd服务
systemctl restart httpd
8.2 使用phpldapadmin
Forbidden
You don't have permission to access /ldapadmin/ on this server.
可以尝试修改httpd.conf
vi /etc/httpd/conf/http.conf
修改
8.3 为phpldapadmin添加suorole配置模版
从这里可以获取到sudoRole模板,http://phpldapadmin.sourceforge.net/wiki/index.php/TemplatesContributed:Sudo 可以在这个基础上进行修改
ll /usr/share/phpldapadmin/templates
# ll /usr/share/phpldapadmin/templates
total 8
drwxr-xr-x 2 root root 4096 Jul 4 15:32 creation
drwxr-xr-x 2 root root 69 Jul 4 15:31 modification
-rw-r--r-- 1 root root 2089 Oct 1 2012 template.dtd
vi /usr/share/phpldapadmin/templates/creation/sudo.xml 注意根据需要进行修改,我的sudo ou名称是SUDOers
<template>
<title>Sudo Policytitle>
<regexp>^ou=SUDOers,dc=.*regexp>
<icon>images/door.pngicon>
<description>New Sudo Policydescription>
<askcontainer>1askcontainer>
<rdn>cnrdn>
<visible>1visible>
<objectClasses>
<objectClass id="sudoRole">objectClass>
objectClasses>
<attributes>
<attribute id="cn">
<display>Policy Namedisplay>
<order>1order>
<page>1page>
attribute>
<attribute id="sudoOption">
<display>Sudo Optiondisplay>
<order>2order>
<page>1page>
<spacer>1spacer>
attribute>
<attribute id="sudoRunAsUser">
<display>Sudo Run As Userdisplay>
<order>3order>
<page>1page>
<spacer>1spacer>
attribute>
<attribute id="sudoCommand">
<display>Sudo Commanddisplay>
<order>4order>
<page>1page>
<spacer>1spacer>
attribute>
<attribute id="sudoUser">
<display>Sudo Usersdisplay>
<option>=php.MultiList(/,(objectClass=posixAccount),uid,%uid%
(%cn%),sudoUser)option>
<order>5order>
<page>1page>
<spacer>1spacer>
attribute>
<attribute id="sudoHost">
<display>Sudo Hostsdisplay>
<array>10array>
<order>6order>
<page>1page>
<spacer>1spacer>
attribute>
<attribute id="description">
<type>textareatype>
<display>Descriptiondisplay>
<order>7order>
<page>1page>
attribute>
attributes>
template>
vi /usr/share/phpldapadmin/templates/modification/sudo.xml
<template>
<title>Sudo Policytitle>
<regexp>^cn=.*,ou=SUDOers,dc=.*regexp>
<icon>images/door.pngicon>
<description>Sudo Policydescription>
<askcontainer>1askcontainer>
<rdn>cnrdn>
<visible>1visible>
<objectClasses>
<objectClass id="sudoRole">objectClass>
objectClasses>
<attributes>
<attribute id="cn">
<display>Policy Namedisplay>
<order>1order>
<page>1page>
attribute>
<attribute id="sudoOption">
<display>Sudo Optiondisplay>
<order>2order>
<page>1page>
<spacer>1spacer>
attribute>
<attribute id="sudoRunAsUser">
<display>Sudo Run As Userdisplay>
<order>3order>
<page>1page>
<spacer>1spacer>
attribute>
<attribute id="sudoCommand">
<display>Sudo Commanddisplay>
<order>4order>
<page>1page>
<spacer>1spacer>
attribute>
<attribute id="sudoUser">
<display>Sudo Usersdisplay>
<order>5order>
<page>1page>
<spacer>1spacer>
attribute>
<attribute id="sudoHost">
<display>Sudo Hostsdisplay>
<order>6order>
<page>1page>
<spacer>1spacer>
attribute>
<attribute id="description">
<type>textareatype>
<display>Descriptiondisplay>
<order>7order>
<page>1page>
<cols>200cols>
<rows>10rows>
attribute>
attributes>
template>
重启httpd服务
systemctl restart httpd
浏览器查看(ou=SUODers,dc=example,dc=com 创建一条子目录 sudoRole)
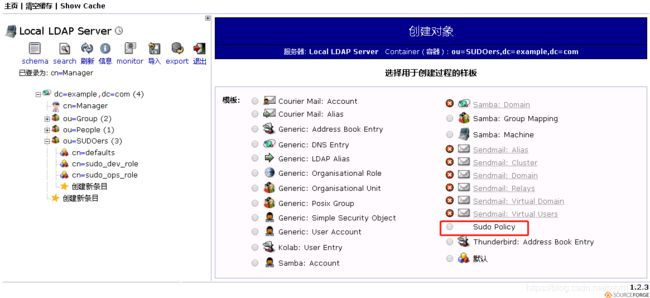
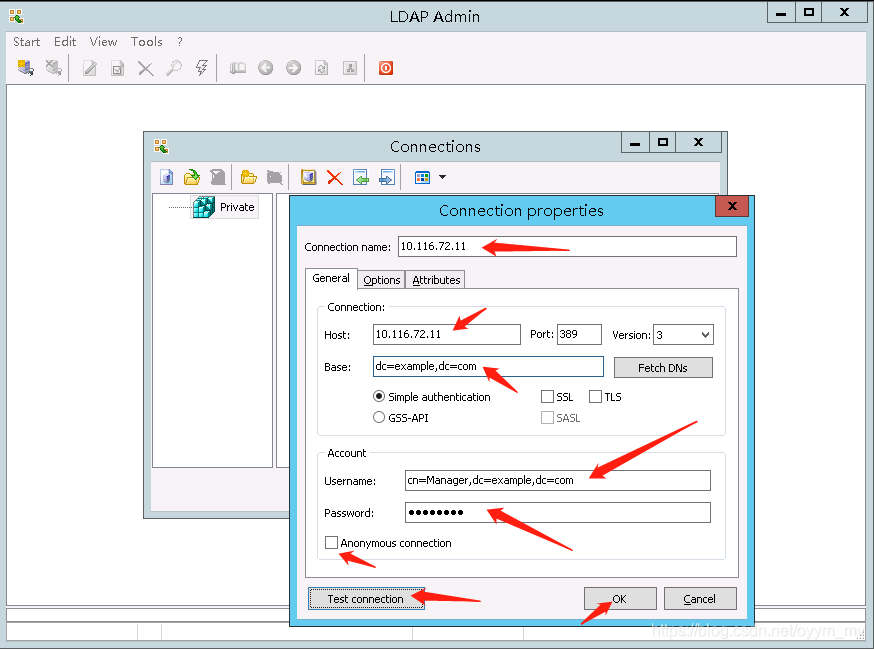
9. windows下的一个OpenLDAP管理工具 LdapAdmin
下载地址 LdapAdmin, 当前最新版本是1.8.3。 下载后直接解压就是一个exe文件。
9.1 创建连接到openldap服务
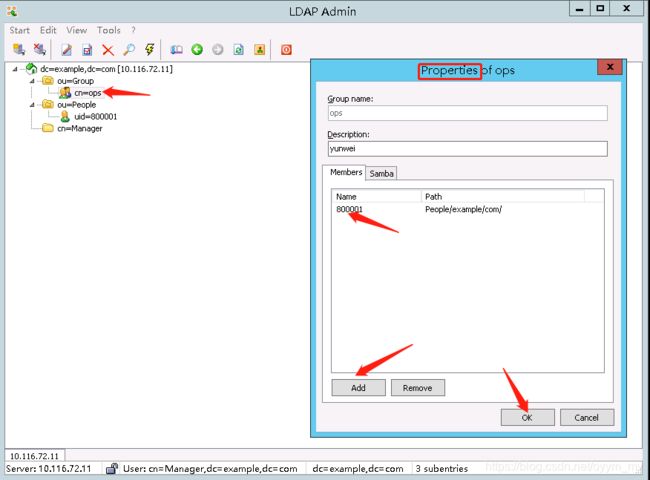
9.2 配置一个运维组ops,然后将用户800001加入到ops组
如上配置完成,还是比较简单的,如果都研究明白还是很多东西的。本文的目的是使用单机配置的方式展示使用openldap作为认证服务需要的功能与配置,之后如果遇到了其他场景再补充。其他文档会涉及到高可用模式(主从,多主,镜像等)的配置
参考文档:
- https://blog.csdn.net/u011607971/article/details/86154096