MITRE ATT&CK框架
前言:
ATT&CK是一个强大的、庞大的框架,本人目前还在初学阶段,本文仅用于记录在学习ATT&CK中的一些心得体会。
0X00 什么是ATT&CK
Adversarial Tactics, Techniques, and Common Knowledge(敌对的 战术 技术 和常识)
简单来说就是站在攻击方的视角,描述黑客在入侵时可能用到的入侵战术,入侵技术,并建立一个知识库,帮助防守方更好的理解、分析攻击方的意图、下一步攻击行为等,以此来帮助防守方做决策,所谓知己知彼,百战不殆。
ATT&CK将攻击方的战术划分成了12部分(需要注意的是,虽然采用有序列表显示了下面内容,但下面的内容并没有任何线性关系,只是由于ATT&CK矩阵习惯按照下面的顺序来排列入侵战术而已):
- Initial Access(初始访问):通过各种手段尝试访问目标的系统
- Execution(执行):命令执行、软件执行
- Persistence(持久化):使目标长时间处于攻击者受控状态,就算目标进行重启、修改密码等操作也无法摆脱控制
- Privilege Escalation(权限提升):提升到高权限用户,例如root
- Defense Evasion(防御绕过):绕过安全设备的检查
- Credential Access(凭据访问):通过各种方式尝试拿到目标的凭据,通过凭据直接访问系统,例如暴力破解账号密码、用户输入捕获等
- Discovery(发现):发现各种信息,例如系统版本、用户账号、服务探测、进程扫描、注册表扫描等。其实感觉用探测来描述更为贴切?
- Lateral Movement(横向移动):入侵者单点突破系统后尝试通过网络横向移动,来达到控制更多主机,获取更多信息的目的
- Collection(收集):收集各种数据,例如用户数据、邮件数据、图片数据、数据库、视频等。
- Command and Control(命令和控制):入侵者使用各种手段对目标进行远程控制
- Exflitration(外泄):数据转移,数据泄露
- Impact(影响):对目标进行一些破坏性操作,例如清空磁盘、停止服务、关闭/重启系统、去除正常用户权限、数据加密等等
目前ATT&CK的一个很常见的用法就是分析各个APT家族的行为特征。不同的黑客团伙肯定是擅长不同的技术栈,有不同的入侵理解,那么他们的行为也会有一定的特征,使用ATT&CK总结出各个APT组织的战术、技术、入侵策略,可以很好的帮助防守方进行决策,更好抵御入侵。
举一个我在Mitre官网看到的例子(https://medium.com/mitre-attack/getting-started-with-attack-cti-4eb205be4b2f):
例如咱们企业是制药的,我们现在要建立自己的威胁情报系统,那咱们应该关注哪些?那肯定是关注那些天天盯着制药企业进行入侵的APT组织吧?例如APT19:
咱们可以在Mitre官网上查询到关于该组织的一些开源报告,看看他们常用的技术,入侵手段。比如说他们喜欢爬下水道进入我家宅子,那我是不是就可以在下水道安监控。如果他们喜欢爬墙进来,我也可以在围墙上安监控。总而言之就是我知道他喜欢用什么方式入侵我,我就可以更好的制定防守甚至反制策略。
0X01 ATT&CK Matrix
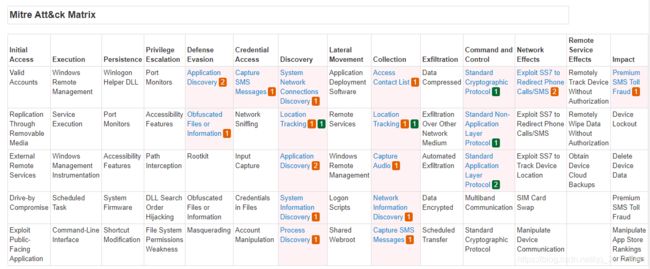
ATT&CK矩阵,使用矩阵的方式来对攻击方的战术、技术进行展现。
1.ATT&CK Matrix 类别
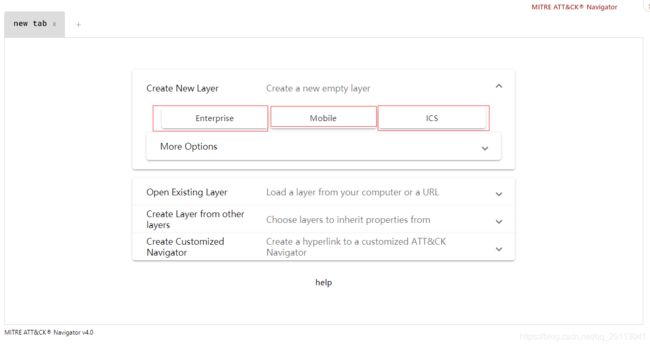
目前共有三类模型:ATT&CK for Enterprise、ATT&CK for Mobile和ATT&CK for ICS。ATT&CK for Enterprise包含适用于Windows、Linux、MacOS、云平台等技术和战术部分。ATT&CK for Mobile包含适用于移动设备的战术和技术。ATT&CK for ICS包含适用于工控设备的战术和技术。(下图为ATT&CK Navigator生成图层时的选项,可以看到默认有三个选项Enterprise,Mobile和ICS)
2.ATT&CK for Enterprise矩阵:
Enterprise矩阵包含了各大操作系统,例如Linux Windows和Mac,还有各大云平台:AWS,Azure AD,GCP等等,涵盖了企业的绝大多数环境。
3.生成自己的矩阵
使用ATT&CK Navigator工具可以轻松生成自己的矩阵,并进行修改。支持导出矩阵数据到SVG、Excel、JSON中,对数据修改后可以再导入到Navigator中进行展现。
Github链接:GitHub - mitre-attack/attack-navigator: Web app that provides basic navigation and annotation of ATT&CK matrices
4.ATT&CK Matrix有什么用?
目前个人体会是可以用于展现沙箱行为数据。是否因为沙箱跑出的大量数据而苦恼?是否苦于不知如何展现沙箱行为数据?是否不知如何优化沙箱行为规则?没有关系,ATT&CK可以帮助你,列表中的每一行技术都有一个具体的ID,只要将沙箱跑出的行为数据与矩阵中的ID进行映射,就可以按照ATT&CK Matrix的形式来展现沙箱数据了,目前很多厂商都在这样做。
DEMO:JoeSandbox(Deep Malware Analysis - Joe Sandbox)
ATT&CK 还有非常多妙用,可以看下官网的一些文章,或者结合公司业务进行使用
5.获取Matrix中的Tactics和Techniques的JSON数据
如果咱们需要用ATT&CK来干些事,那肯定把ATT&CK涉及到的数据保存到本地,或者进一步做一些处理,那么JSON数据从哪来?
(1)数据源
GitHub - mitre/cti: Cyber Threat Intelligence Repository expressed in STIX 2.0
比如说我需要ATT&CK For Mobile的数据,那么就进入mobile-attack目录,然后会看到一个文件mobile-attack.json,这就是我们需要的数据了。
(2)关于数据解析
JSON文件包含了很多类型的数据,根据type字段进行区分,如果只对Tactics和Techniques感兴趣,那么根据type=attack-pattern去解析即可,需要注意的是里面会包含历史被废弃的记录,description字段会有说明。
再就是如果一个Technique对应了多个Tactic,那么在kill_chain_phases字段中会有多条记录,看下DEMO:
{
"external_references": [
{
"url": "https://attack.mitre.org/techniques/T1517",
"source_name": "mitre-mobile-attack",
"external_id": "T1517" # technique的TID
},
{
"description": "Luk\u00e1\u0161 \u0160tefanko. (2019, June 17). Malware sidesteps Google permissions policy with new 2FA bypass technique. Retrieved September 15, 2019.",
"url": "https://www.welivesecurity.com/2019/06/17/malware-google-permissions-2fa-bypass/",
"source_name": "ESET 2FA Bypass"
}
],
"object_marking_refs": [
"marking-definition--fa42a846-8d90-4e51-bc29-71d5b4802168"
],
"created_by_ref": "identity--c78cb6e5-0c4b-4611-8297-d1b8b55e40b5",
"name": "Access Notifications", # technique的名字
"description": "A malicious application can read notifications sent by the operating system or other applications, which may contain sensitive data such as one-time authentication codes sent over SMS, email, or other mediums. A malicious application can also dismiss notifications to prevent the user from noticing that the notifications arrived and can trigger action buttons contained within notifications.(Citation: ESET 2FA Bypass)",
"id": "attack-pattern--39dd7871-f59b-495f-a9a5-3cb8cc50c9b2",
"type": "attack-pattern",
"kill_chain_phases": [ # 该technique在两个tactic中出现,collection和credential-access
{
"kill_chain_name": "mitre-mobile-attack",
"phase_name": "collection"
},
{
"kill_chain_name": "mitre-mobile-attack",
"phase_name": "credential-access"
}
],
"modified": "2020-07-09T14:07:02.217Z",
"created": "2019-09-15T15:26:08.183Z",
"x_mitre_is_subtechnique": false,
"x_mitre_contributors": [
"Luk\u00e1\u0161 \u0160tefanko, ESET"
],
"x_mitre_version": "1.0",
"x_mitre_tactic_type": [
"Post-Adversary Device Access"
],
"x_mitre_detection": "The user can inspect (and modify) the list of applications that have notification access through the device settings (e.g. Apps & notification -> Special app access -> Notification access).",
"x_mitre_platforms": [ # 适用于哪个平台
"Android"
]
},0X02 STIX(Structed Threat Information Expression)
结构化威胁信息表达(STIX™)是一种用于交换网络威胁情报(CTI)的语言和序列化格式。简单来说就是现在威胁那么多,安全厂商那么多,每个厂商都闭门造车,自己建立自己的威胁情报系统,那这些数据不就浪费了吗?何不建立一种公共的威胁情报规范,让大家的威胁情报共享呢?STIX就是来干这个事的
Introduction to STIX:Introduction to STIX
| Name | Description | 备注 |
|---|---|---|
| Attack Pattern | A type of TTP that describe ways that adversaries attempt to compromise targets. | 一种TTP类型,描述入侵者试图破坏目标的方式。 |
| Campaign | A grouping of adversarial behaviors that describes a set of malicious activities or attacks (sometimes called waves) that occur over a period of time against a specific set of targets. | 一组敌对行为,描述一组针对特定目标在一段时间内发生的恶意活动或攻击。 |
| Course of Action | A recommendation from a producer of intelligence to a consumer on the actions that they might take in response to that intelligence | 情报制作者向用户提出的针对情报可以采取的行动的建议 |
| Grouping | Explicitly asserts that the referenced STIX Objects have a shared context, unlike a STIX Bundle (which explicitly conveys no context) | |
| Identity | Actual individuals, organizations, or groups (e.g., ACME, Inc.) as well as classes of individuals, organizations, systems or groups (e.g., the finance sector). | |
| Indicator | Contains a pattern that can be used to detect suspicious or malicious cyber activity. | |
| Infrastructure | Represents a type of TTP and describes any systems, software services and any associated physical or virtual resources intended to support some purpose (e.g., C2 servers used as part of an attack, device or server that are part of defence, database servers targeted by an attack, etc.). | |
| Intrusion Set | A grouped set of adversarial behaviors and resources with common properties that is believed to be orchestrated by a single organization. | |
| Location | Represents a geographic location. | |
| Malware | A type of TTP that represents malicious code. | |
| Malware Analysis | The metadata and results of a particular static or dynamic analysis performed on a malware instance or family. | |
| Note | Conveys informative text to provide further context and/or to provide additional analysis not contained in the STIX Objects, Marking Definition objects, or Language Content objects which the Note relates to. | |
| Observed Data | Conveys information about cyber security related entities such as files, systems, and networks using the STIX Cyber-observable Objects (SCOs). | |
| Opinion | An assessment of the correctness of the information in a STIX Object produced by a different entity. | |
| Report | Collections of threat intelligence focused on one or more topics, such as a description of a threat actor, malware, or attack technique, including context and related details. | |
| Threat Actor | Actual individuals, groups, or organizations believed to be operating with malicious intent. | |
| Tool | Legitimate software that can be used by threat actors to perform attacks. | 可被威胁参与者用于执行攻击的合法软件。 |
| Vulnerability | A mistake in software that can be directly used by a hacker to gain access to a system or network. | 一个直接导致黑客获取系统或网络权限的漏洞 |
STIX对象详解:STIX Version 2.1
0X03 TAXII(Trusted Automated Exchange of Intelligence Information)
可信情报自动交换协议,是一种应用层协议,用于以简单且可扩展的方式传达网络威胁信息。TAXII是用于通过HTTPS交换网络威胁情报(CTI)的协议。TAXII通过定义与通用共享模型一致的API,使组织可以共享CTI。TAXII是专门为支持STIX中的CTI交换而设计的。
To be continued...
相关名词注解:
- TTP(Tactics, Techniques and Procedures)战术、技术和过程
- ICS(Industrial Control System)工业控制系统
- CTI(Cyber Threat Intelligence)网络威胁情报
- IOC(Indicator of compromise)失陷指标,包括在系统日志条目或文件中找到的数据,用于识别系统或网络上的潜在恶意活动。通过监控IOC,组织可以检测攻击并迅速采取行动,防止此类攻击发生,或通过阻止早期攻击来限制损害。
收集的资料汇总:
- ATT&CK设计和哲学论文:https://attack.mitre.org/docs/ATTACK_Design_and_Philosophy_March_2020.pdf
- STIX Usage doc:cti/USAGE.md at master · mitre/cti · GitHub
- Enterprise Tactics:Tactics - Enterprise | MITRE ATT&CK®
- STIX Python API:Creating STIX Content — stix2 3.0.1 documentation
- STIX & TAXII:Cyber Threat Intelligence Technical Committee
- Mitre ATT&CK getting-started:Getting Started | MITRE ATT&CK®
- 一文看懂ATT&CK框架以及使用场景实例:[原创] 一文看懂ATT&CK框架以及使用场景实例-茶余饭后-看雪论坛-安全社区|安全招聘|bbs.pediy.com
- ATT&CK一般性学习笔记 :[原创]ATT&CK一般性学习笔记-企业安全-看雪论坛-安全社区|安全招聘|bbs.pediy.com
- ATT&CK 攻击知识库中文版:Hansight
- ATT&CK 攻击实操:GitHub - lengjibo/ATT-CK-CN: ATT&CK实操
- MITRE STIX数据集:GitHub - mitre/cti: Cyber Threat Intelligence Repository expressed in STIX 2.0