第7章 K8s基础篇-服务发布入门
---------杜宽老师宽k8s课程学习笔记---------
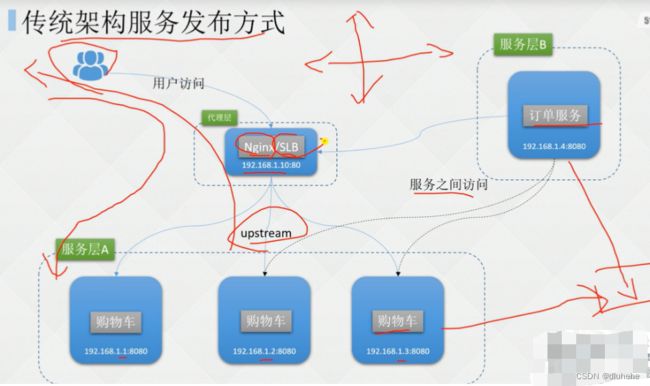
7.1 k8s是如何发布服务的
南北流量:放在公网上供用户访问;
东西流量:系统间内部访问;
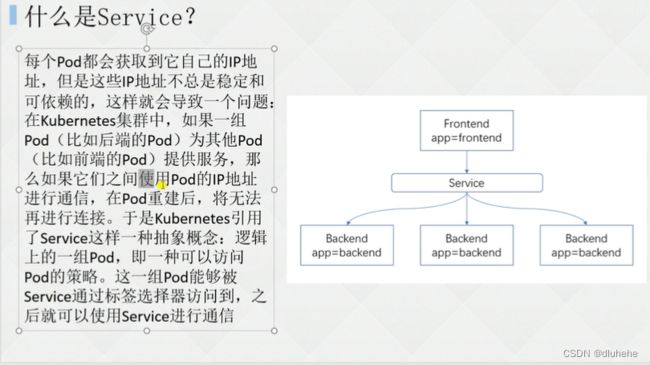
pod删除后重建,ip地址发生变化,故不能采用ip方式访问pod。
k8s对内用service(对应东西流量),对外用ingress(nginx实现,通过域名代理到service,通过service再访问pod)(对应南北流量)。
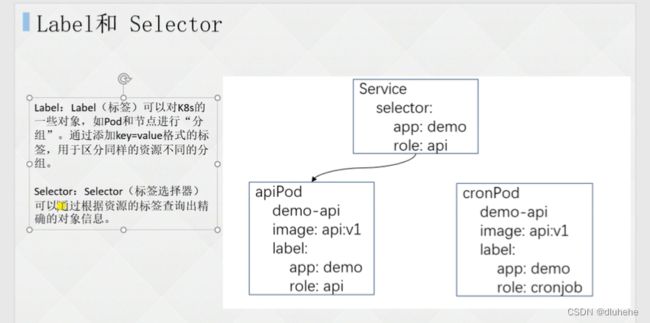
7.2 什么是Label 和 Selector
不同资源控制器打的标签不要一样,比如deployment和deamomset的标签一样都是app=nginx,那就会出现问题。
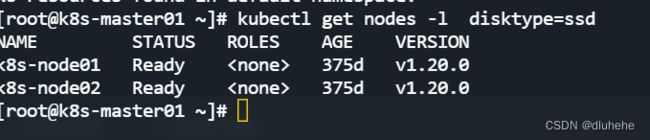
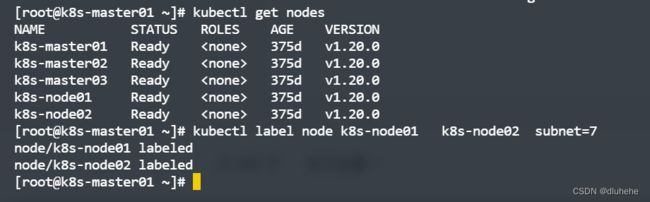
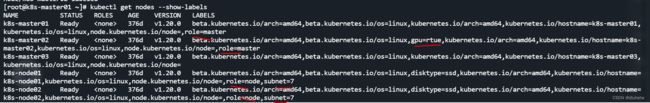
---查看节点的标签
kubectl get nodes --show-labels
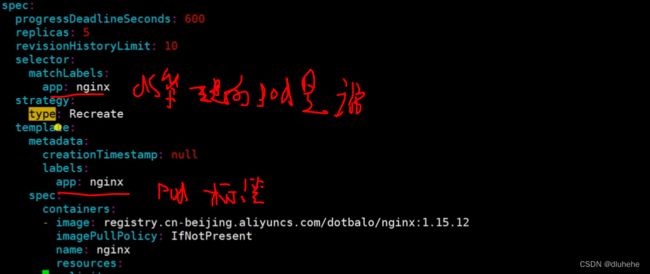
7.3 Label 和 Selector的使用
kubectl label node k8s-node01 k8s-node02 subnet=7新建测试labels的yaml文件:nginx-deploy_labels_1123.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: nginx
name: nginx
spec:
replicas: 5 #副本数
selector:
matchLabels:
app: nginx
#strategy:
#rollingUpdate:
#maxSurge: 25%
#maxUnavailable: 25%
#type: RollingUpdate
template:
metadata:
creationTimestamp: null
labels:
app: nginx
spec:
nodeSelector:
subnet: "7"
containers:
- image: registry.cn-beijing.aliyuncs.com/dotbalo/nginx:1.15.12
imagePullPolicy: IfNotPresent
name: nginx
resources: {}
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
dnsPolicy: ClusterFirst
restartPolicy: Always
schedulerName: default-scheduler
securityContext: {}
terminationGracePeriodSeconds: 30kubectl create -f nginx-deploy_labels_1123.yaml;
kubectl get po -owide;label命令可以给node,pod,service等多种类型资源打上标签;
5个副本都分配在被打标签的(subnet=7)node01和noge02上面;
打标签练习
#Selector 选择器过滤
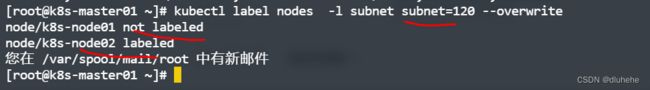
kubectl get nodes -l 'role in (master,node)' 修改标签
kubectl label nodes k8s-node01 subnet=120 --overwritekubectl label nodes -l subnet subnet=120 --overwrite删除标签
kubectl label nodes k8s-node01 subnet-标签批量删除
kubectl label nodes -l subnet subnet-7.4 什么是service
7.5 service的基本使用
去掉nodeselector后的yaml文件如下:
[root@k8s-master01 ~]# cat nginx-deploy_labels_1123.yaml
# cat nginx-deploy.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: nginx
name: nginx
spec:
replicas: 5 #副本数
selector:
matchLabels:
app: nginx
#strategy:
#rollingUpdate:
#maxSurge: 25%
#maxUnavailable: 25%
#type: RollingUpdate
template:
metadata:
creationTimestamp: null
labels:
app: nginx
spec:
#nodeSelector:
# subnet: "7"
containers:
- image: registry.cn-beijing.aliyuncs.com/dotbalo/nginx:1.15.12
imagePullPolicy: IfNotPresent
name: nginx
resources: {}
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
dnsPolicy: ClusterFirst
restartPolicy: Always
schedulerName: default-scheduler
securityContext: {}
terminationGracePeriodSeconds: 30kubectl replace -f nginx-deploy_labels_1123.yaml service必须是pod在同一个namespace下,不然service会找不到pod;
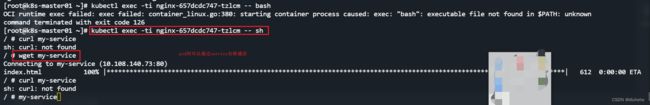
kubectl create -f service_1126.yaml 测试结果
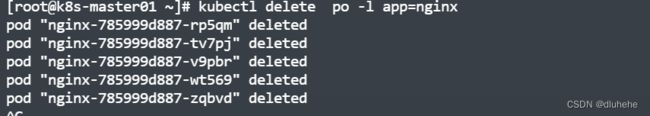
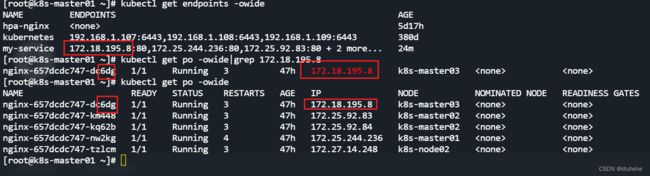
测试:删除app=nginx标签的pod后,新建的pod ip地址发生变化,但仍然可以通过service地址访问。
service采用轮循方式,将请求随机转发后其代理的5个pod中处理;
具体修改位置
修改后的yaml文件如下
[root@k8s-master01 ~]# cat nginx-deploy_labels_1123.yaml
# cat nginx-deploy.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: nginx
name: nginx
spec:
replicas: 5 #副本数
selector:
matchLabels:
app: nginx
#strategy:
#rollingUpdate:
#maxSurge: 25%
#maxUnavailable: 25%
#type: RollingUpdate
template:
metadata:
creationTimestamp: null
labels:
app: nginx
spec:
#nodeSelector:
# subnet: "7"
containers:
- image: registry.cn-beijing.aliyuncs.com/dotbalo/nginx:1.15.12-alpine
imagePullPolicy: IfNotPresent
name: nginx
resources: {}
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
dnsPolicy: ClusterFirst
restartPolicy: Always
schedulerName: default-scheduler
securityContext: {}
terminationGracePeriodSeconds: 30kubectl replace -f nginx-deploy_labels_1123.yaml ![]()
7.6 service的类型
Kubernetes Service Type(服务类型)主要包括以下几种:
➢ ClusterIP :在集群内部使用,默认值,只能从集群中访问。
➢ NodePort :在所有安装了 Kube P roxy 的节点上打开一个端口,此端口可以代理至后端
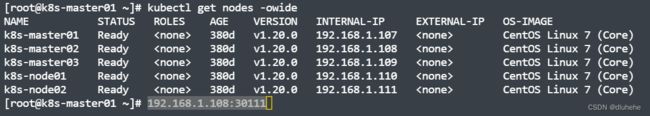
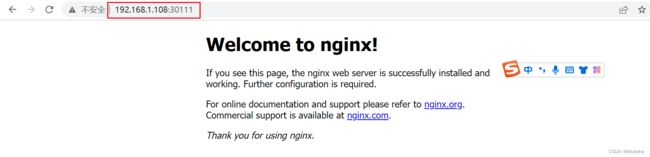
Pod ,可以通过 NodePort 从集群外部访问集群内的服务,格式为 NodeIP:NodePort 。eg:比如笔记本电脑想访问pod服务,显然不能直接在笔记本的浏览器输入pod的地址访问,但我们笔记本和宿主机(master01-03+node01-02,ip:192.168.1.107-192.168.1.111)是通的,可以通过宿主机加映射到pod,这样笔记本就可以直接访问pod里的服务了。
➢ LoadBalancer :使用云提供商的负载均衡器公开服务,成本较高。
➢ ExternalName :通过返回定义的 CNAME 别名,没有设置任何类型的代理,需要 1.7 或
更高版本 kube dns 支持。
7.7 使用NodePort对外发布服务
cat service_1126.yaml
kind: Service
apiVersion: v1
metadata:
name: my-service
spec:
selector:
app: nginx
ports:
- protocol: TCP
port: 80
targetPort: 80
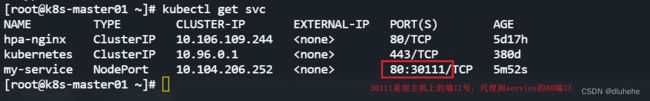
type: NodePort修改service可以通过edit命令
所以我们通过宿主机的30111端口就可以访问到pod的80端口的服务;
7.8 使用 Service 代理 K8s 外部服务
NodePort等方式使用yaml使用selector创建service,系统会创建同名endpoints; 如果是代理外部服务,selector就不用写了,手动创建同名ep即可;
endpoints存储该service所管理的所有pod的ip地址的列表
[root@k8s-master01 ~]# cat service-external-ip.yaml
apiVersion: v1
kind: Service
metadata:
labels:
app: nginx-svc-external
name: nginx-svc-external
spec:
ports:
- name: http
port: 80
protocol: TCP
targetPort: 80
type: ClusterIP
---
# cat nginx ep external.yaml
apiVersion: v1
kind: Endpoints
metadata:
labels:
app: nginx-svc-external
name: nginx-svc-external
subsets:
- addresses:
- ip: 140.205.94.189 #外部公网的ip
ports:
- name: http
port : 80
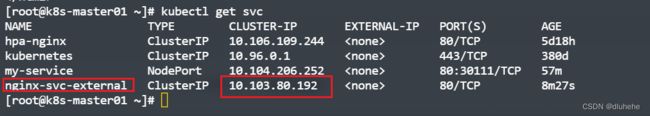
protocol: TCPkubectl create -f service-external-ip.yaml 通过service访问外部(外网)服务测试
外网ip:140.205.94.189 #外部公网的ip
7.9 ExternalName Service代理域名
cat external.yaml
[root@k8s-master01 ~]# cat external.yaml
kind: Service
apiVersion: v1
metadata:
name: external-service
spec:
type: ExternalName
externalName: www.baidu.com7.10 多端口 Service
service代理到后端pod的多个端口;
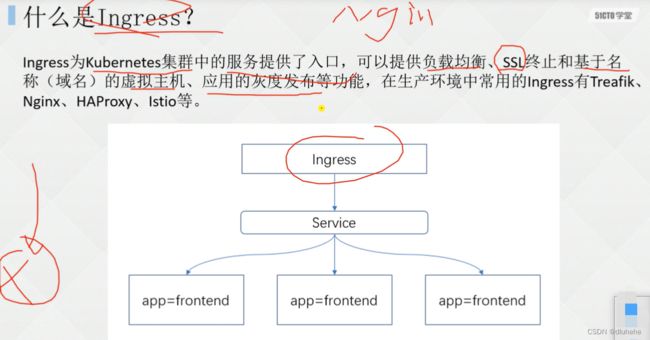
7.11 什么是Ingress
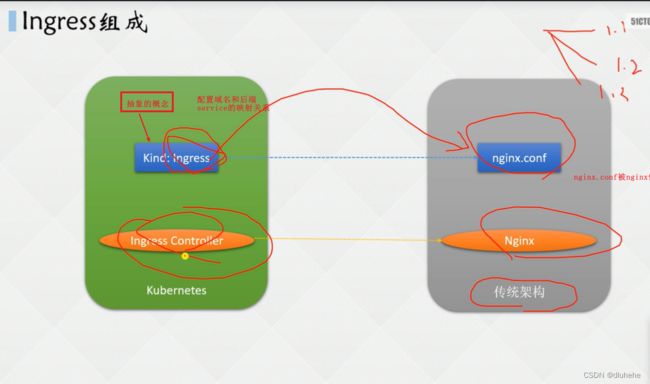
7.12 使用Ingress发布服务的流程
Ingress是配置,Ingress-controller是Ingress配置对应的服务;
nginx.con是配置,nginx是nginx.con配置对应的服务;
7.13 Ingress Controller 安装
cat deploy-ingress.yaml
[root@k8s-master01 ~]# cat deploy-ingress.yaml
apiVersion: v1
kind: Namespace
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
name: ingress-nginx
---
apiVersion: v1
automountServiceAccountToken: true
kind: ServiceAccount
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx
namespace: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- namespaces
verbs:
- get
- apiGroups:
- ""
resources:
- configmaps
- pods
- secrets
- endpoints
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- networking.k8s.io
resources:
- ingressclasses
verbs:
- get
- list
- watch
- apiGroups:
- ""
resourceNames:
- ingress-controller-leader
resources:
- configmaps
verbs:
- get
- update
- apiGroups:
- ""
resources:
- configmaps
verbs:
- create
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx-admission
namespace: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- secrets
verbs:
- get
- create
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- configmaps
- endpoints
- nodes
- pods
- secrets
- namespaces
verbs:
- list
- watch
- apiGroups:
- ""
resources:
- nodes
verbs:
- get
- apiGroups:
- ""
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
- apiGroups:
- networking.k8s.io
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- networking.k8s.io
resources:
- ingressclasses
verbs:
- get
- list
- watch
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx-admission
rules:
- apiGroups:
- admissionregistration.k8s.io
resources:
- validatingwebhookconfigurations
verbs:
- get
- update
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx
namespace: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: ingress-nginx
subjects:
- kind: ServiceAccount
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx-admission
namespace: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: ingress-nginx-admission
subjects:
- kind: ServiceAccount
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: ingress-nginx
subjects:
- kind: ServiceAccount
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx-admission
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: ingress-nginx-admission
subjects:
- kind: ServiceAccount
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: v1
data:
allow-snippet-annotations: "true"
kind: ConfigMap
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx-controller
namespace: ingress-nginx
---
apiVersion: v1
kind: Service
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx-controller
namespace: ingress-nginx
spec:
ports:
- appProtocol: http
name: http
port: 80
protocol: TCP
targetPort: http
- appProtocol: https
name: https
port: 443
protocol: TCP
targetPort: https
selector:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
type: NodePort
---
apiVersion: v1
kind: Service
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx-controller-admission
namespace: ingress-nginx
spec:
ports:
- appProtocol: https
name: https-webhook
port: 443
targetPort: webhook
selector:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
type: ClusterIP
---
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx-controller
namespace: ingress-nginx
spec:
minReadySeconds: 0
revisionHistoryLimit: 10
selector:
matchLabels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
template:
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
spec:
containers:
- args:
- /nginx-ingress-controller
- --election-id=ingress-controller-leader
- --controller-class=k8s.io/ingress-nginx
- --ingress-class=nginx
- --configmap=$(POD_NAMESPACE)/ingress-nginx-controller
- --validating-webhook=:8443
- --validating-webhook-certificate=/usr/local/certificates/cert
- --validating-webhook-key=/usr/local/certificates/key
env:
- name: POD_NAME
valueFrom:
fieldRef:
fieldPath: metadata.name
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
- name: LD_PRELOAD
value: /usr/local/lib/libmimalloc.so
image: registry.cn-beijing.aliyuncs.com/dotbalo/controller:v1.2.0
imagePullPolicy: IfNotPresent
lifecycle:
preStop:
exec:
command:
- /wait-shutdown
livenessProbe:
failureThreshold: 5
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 1
name: controller
ports:
- containerPort: 80
name: http
protocol: TCP
- containerPort: 443
name: https
protocol: TCP
- containerPort: 8443
name: webhook
protocol: TCP
readinessProbe:
failureThreshold: 3
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 1
resources:
requests:
cpu: 100m
memory: 90Mi
securityContext:
allowPrivilegeEscalation: true
capabilities:
add:
- NET_BIND_SERVICE
drop:
- ALL
runAsUser: 101
volumeMounts:
- mountPath: /usr/local/certificates/
name: webhook-cert
readOnly: true
dnsPolicy: ClusterFirst
nodeSelector:
kubernetes.io/os: linux
serviceAccountName: ingress-nginx
terminationGracePeriodSeconds: 300
volumes:
- name: webhook-cert
secret:
secretName: ingress-nginx-admission
---
apiVersion: batch/v1
kind: Job
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx-admission-create
namespace: ingress-nginx
spec:
template:
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx-admission-create
spec:
containers:
- args:
- create
- --host=ingress-nginx-controller-admission,ingress-nginx-controller-admission.$(POD_NAMESPACE).svc
- --namespace=$(POD_NAMESPACE)
- --secret-name=ingress-nginx-admission
env:
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
image: registry.cn-beijing.aliyuncs.com/dotbalo/kube-webhook-certgen:v1.1.1
imagePullPolicy: IfNotPresent
name: create
securityContext:
allowPrivilegeEscalation: false
nodeSelector:
kubernetes.io/os: linux
restartPolicy: OnFailure
securityContext:
fsGroup: 2000
runAsNonRoot: true
runAsUser: 2000
serviceAccountName: ingress-nginx-admission
---
apiVersion: batch/v1
kind: Job
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx-admission-patch
namespace: ingress-nginx
spec:
template:
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx-admission-patch
spec:
containers:
- args:
- patch
- --webhook-name=ingress-nginx-admission
- --namespace=$(POD_NAMESPACE)
- --patch-mutating=false
- --secret-name=ingress-nginx-admission
- --patch-failure-policy=Fail
env:
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
image: registry.cn-beijing.aliyuncs.com/dotbalo/kube-webhook-certgen:v1.1.1
imagePullPolicy: IfNotPresent
name: patch
securityContext:
allowPrivilegeEscalation: false
nodeSelector:
kubernetes.io/os: linux
restartPolicy: OnFailure
securityContext:
fsGroup: 2000
runAsNonRoot: true
runAsUser: 2000
serviceAccountName: ingress-nginx-admission
---
apiVersion: networking.k8s.io/v1
kind: IngressClass
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: nginx
spec:
controller: k8s.io/ingress-nginx
---
apiVersion: admissionregistration.k8s.io/v1
kind: ValidatingWebhookConfiguration
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.2.0
name: ingress-nginx-admission
webhooks:
- admissionReviewVersions:
- v1
clientConfig:
service:
name: ingress-nginx-controller-admission
namespace: ingress-nginx
path: /networking/v1/ingresses
failurePolicy: Fail
matchPolicy: Equivalent
name: validate.nginx.ingress.kubernetes.io
rules:
- apiGroups:
- networking.k8s.io
apiVersions:
- v1
operations:
- CREATE
- UPDATE
resources:
- ingresses
sideEffects: None
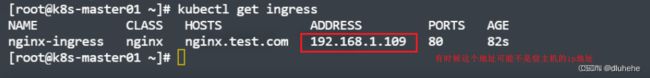
[root@k8s-master01 ~]# kubectl create -f deploy-ingress.yaml 7.14 使用域名去发布K8s内部服务
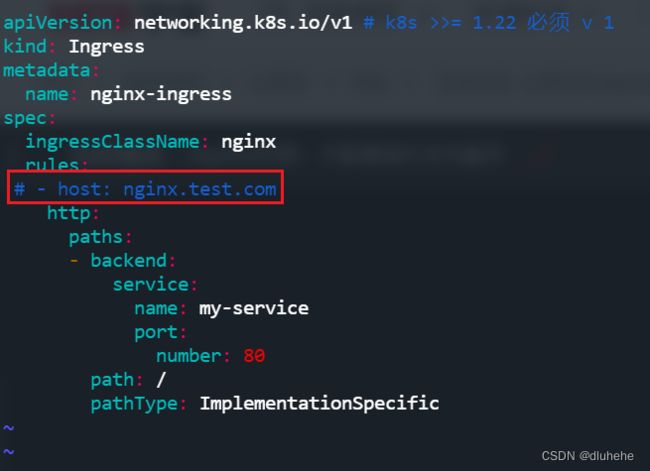
cat web-ingress.yaml
[root@k8s-master01 ~]# cat web-ingress.yaml
apiVersion: networking.k8s.io/v1 # k8s >>= 1.22 必须 v 1
kind: Ingress
metadata:
name: nginx-ingress
spec:
ingressClassName: nginx
rules:
- host: nginx.test.com
http:
paths:
- backend:
service:
name: my-service
port:
number: 80
path: /
pathType: ImplementationSpecific
[root@k8s-master01 ~]# kubectl create -f web-ingress.yaml 多域名多路径配置参考
[root@k8s-master01 ~]# cat web-ingress_more.yaml
apiVersion: networking.k8s.io/v1 # k8s >>= 1.22 必须 v 1
kind: Ingress
metadata:
name: nginx-ingress
spec:
ingressClassName: nginx
rules:
- host: nginx.test.com
http:
paths:
- backend:
service:
name: my-service
port:
number: 80
path: /
pathType: ImplementationSpecific
#more path
- backend:
service:
name: my-service
port:
number: 80
path: /test
pathType: ImplementationSpecific
#more yuming
- host: nginx.test2.com
http:
paths:
- backend:
service:
name: my-service
port:
number: 80
path: /
pathType: ImplementationSpecific
[root@k8s-master01 ~]# 修改hosts文件
具体方法:如何修改hosts文件?几种修改hosts文件的方法_乐吐槽的博客-CSDN博客_修改hosts
 经过任一宿主机节点的ip地址,nginx-controller的service是nodeport的形式,其在每个节点都开了端口映射,任一节点的ip地址+controller的nodeport端口就可以访问controller的pod上,controller pod是nginx,可以对域名做路由。
经过任一宿主机节点的ip地址,nginx-controller的service是nodeport的形式,其在每个节点都开了端口映射,任一节点的ip地址+controller的nodeport端口就可以访问controller的pod上,controller pod是nginx,可以对域名做路由。
ingress路径:客户-->宿主机:端口--->nginx-controller的service(nodeport形式)-->nginx-controller的pod(nginx:完成域名到后端业务service的映射)-->业务的service-->业务的pod
kubectl exec -ti ingress-nginx-controller-7848574b9b-hdfh5 -n ingress-nginx -- shgrep -A 20 'nginx.test.com' nginx.conf/etc/nginx $ grep -A 20 'nginx.test.com' nginx.conf
## start server nginx.test.com
server {
server_name nginx.test.com ;
listen 80 ;
listen 443 ssl http2 ;
set $proxy_upstream_name "-";
ssl_certificate_by_lua_block {
certificate.call()
}
location / {
set $namespace "default";
set $ingress_name "nginx-ingress";
set $service_name "my-service";
set $service_port "80";
set $location_path "/";
set $global_rate_limit_exceeding n;
rewrite_by_lua_block {
--
## end server nginx.test.com
# backend for when default-backend-service is not configured or it does not have endpoints
server {
listen 8181 default_server reuseport backlog=511;
set $proxy_upstream_name "internal";
access_log off;
location / {
return 404;
}
}
# default server, used for NGINX healthcheck and access to nginx stats
server {
listen 127.0.0.1:10246;
set $proxy_upstream_name "internal";
keepalive_timeout 0;
/etc/nginx $ 7.15 Ingress 特例:不配置域名发布服务
cat no-host-web-ingress.yaml
[root@k8s-master01 ~]# cat no-host-web-ingress.yaml
apiVersion: networking.k8s.io/v1 # k8s >>= 1.22 必须 v 1
kind: Ingress
metadata:
name: no-host-nginx-ingress
spec:
ingressClassName: nginx
rules:
- http:
paths:
- backend:
service:
name: my-service
port:
number: 80
path: /no-host
pathType: ImplementationSpecific
[root@k8s-master01 ~]# 笔记本浏览器访问