JRT发布https
网站用Tomcat10作为发布容器,默认是8080端口发布的http协议。这次研究发布成https协议。
首先在Linux上用下面命令得到jks证书文件
openssl genrsa -out ca.key 2048
openssl req -new -x509 -days 3650 -key ca.key -out ca.crt -subj "/C=CN/ST=HuNan/L=ChangSha/O=LiteGrayFish/OU=CA"
openssl genrsa -out server.key 2048
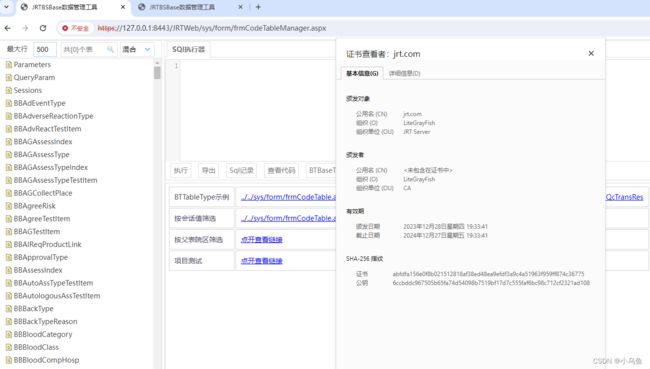
openssl req -new -days 3650 -key server.key -out server.csr -subj "/C=CN/ST=HuNan/L=ChangSha/O=LiteGrayFish/OU=JRT Server/CN=jrt.com"
openssl ca -in server.csr -out server.crt -cert ca.crt -keyfile ca.key
openssl pkcs12 -export -clcerts -in server.crt -inkey server.key -out server.p12
keytool -importkeystore -srckeystore server.p12 -destkeystore server.jks -srcstoretype pkcs12 -deststoretype jks
keytool -list -v -keystore server.jks
shell过程
[BEGIN] 2023/12/28 19:19:55
[root@localhost ~]# openssl genrsa -out ca.key 2048
Generating RSA private key, 2048 bit long modulus
.......................................+++
...........................+++
e is 65537 (0x10001)
[root@localhost ~]# openssl req -new -x509 -days 3650 -key ca.key -out ca.crt -subj "/C=CN/ST=HuNan/L=ChangSha/O=LiteGrayFish/OU=CA"
[root@localhost ~]# openssl genrsa -out server.key 2048
Generating RSA private key, 2048 bit long modulus
.............................................+++
.............+++
e is 65537 (0x10001)
[root@localhost ~]# openssl req -new -days 3650 -key server.key -out server.csr -subj "/C=CN/ST=HuNan/L=ChangSha/O=LiteGrayFish/OU=JRT Server/CN=jrt.com"
[root@localhost ~]# openssl ca -in server.csr -out server.crt -cert ca.crt -keyfile ca.key
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4 (0x4)
Validity
Not Before: Dec 28 11:20:37 2023 GMT
Not After : Dec 27 11:20:37 2024 GMT
Subject:
countryName = CN
stateOrProvinceName = HuNan
organizationName = LiteGrayFish
organizationalUnitName = JRT Server
commonName = jrt.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
A6:BD:BE:91:B1:86:FA:79:AA:A2:12:22:F0:3F:99:8C:9C:6E:4F:13
X509v3 Authority Key Identifier:
keyid:7F:EE:D0:20:0A:F6:74:0C:5C:DB:37:1E:C3:FF:38:AF:E3:89:C8:65
Certificate is to be certified until Dec 27 11:20:37 2024 GMT (365 days)
Sign the certificate? [y/n]:y
failed to update database
TXT_DB error number 2
[root@localhost ~]# openssl pkcs12 -export -clcerts -in server.crt -inkey server.key -out server.p12
unable to load certificates
[root@localhost ~]# cd /jrtbase
[root@localhost jrtbase]# mkdir ca
[root@localhost jrtbase]# cd ca
[root@localhost ca]# ls
[root@localhost ca]# cd /jrtbase/tmp
[root@localhost tmp]# openssl genrsa -out ca.key 2048
Generating RSA private key, 2048 bit long modulus
...............+++
...........+++
e is 65537 (0x10001)
[root@localhost tmp]# openssl req -new -x509 -days 3650 -key ca.key -out ca.crt -subj "/C=CN/ST=HuNan/L=ChangSha/O=LiteGrayFish/OU=CA"
[root@localhost tmp]# openssl genrsa -out server.key 2048
Generating RSA private key, 2048 bit long modulus
...................+++
........................+++
e is 65537 (0x10001)
[root@localhost tmp]# openssl req -new -days 3650 -key server.key -out server.csr -subj "/C=CN/ST=HuNan/L=ChangSha/O=LiteGrayFish/OU=JRT Server/CN=jrt.com"
[root@localhost tmp]# openssl ca -in server.csr -out server.crt -cert ca.crt -keyfile ca.key
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4 (0x4)
Validity
Not Before: Dec 28 11:25:27 2023 GMT
Not After : Dec 27 11:25:27 2024 GMT
Subject:
countryName = CN
stateOrProvinceName = HuNan
organizationName = LiteGrayFish
organizationalUnitName = JRT Server
commonName = jrt.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
5E:EC:DD:BA:F7:04:50:57:C0:55:C4:0D:55:D8:4F:73:77:2D:2E:AD
X509v3 Authority Key Identifier:
keyid:55:7E:11:6E:30:48:87:C3:DE:12:3C:00:0D:5C:5B:5D:B4:76:CC:BD
Certificate is to be certified until Dec 27 11:25:27 2024 GMT (365 days)
Sign the certificate? [y/n]:y
failed to update database
TXT_DB error number 2
[root@localhost tmp]# openssl pkcs12 -export -clcerts -in server.crt -inkey server.key -out server.p12
unable to load certificates
[root@localhost tmp]# keytool -importkeystore -srckeystore server.p12 -destkeystore server.jks -srcstoretype pkcs12 -deststoretype jks
keytool error: java.lang.Exception: Source keystore file exists, but is empty: server.p12
[root@localhost tmp]# openssl ca -in server.csr -out server.crt -cert ca.crt -keyfile ca.key
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4 (0x4)
Validity
Not Before: Dec 28 11:26:50 2023 GMT
Not After : Dec 27 11:26:50 2024 GMT
Subject:
countryName = CN
stateOrProvinceName = HuNan
organizationName = LiteGrayFish
organizationalUnitName = JRT Server
commonName = jrt.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
5E:EC:DD:BA:F7:04:50:57:C0:55:C4:0D:55:D8:4F:73:77:2D:2E:AD
X509v3 Authority Key Identifier:
keyid:55:7E:11:6E:30:48:87:C3:DE:12:3C:00:0D:5C:5B:5D:B4:76:CC:BD
Certificate is to be certified until Dec 27 11:26:50 2024 GMT (365 days)
Sign the certificate? [y/n]:
CERTIFICATE WILL NOT BE CERTIFIED
[root@localhost tmp]# openssl ca -in server.csr -out server.crt -cert ca.crt -keyfile ca.key
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4 (0x4)
Validity
Not Before: Dec 28 11:26:55 2023 GMT
Not After : Dec 27 11:26:55 2024 GMT
Subject:
countryName = CN
stateOrProvinceName = HuNan
organizationName = LiteGrayFish
organizationalUnitName = JRT Server
commonName = jrt.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
5E:EC:DD:BA:F7:04:50:57:C0:55:C4:0D:55:D8:4F:73:77:2D:2E:AD
X509v3 Authority Key Identifier:
keyid:55:7E:11:6E:30:48:87:C3:DE:12:3C:00:0D:5C:5B:5D:B4:76:CC:BD
Certificate is to be certified until Dec 27 11:26:55 2024 GMT (365 days)
Sign the certificate? [y/n]:n
CERTIFICATE WILL NOT BE CERTIFIED
[root@localhost tmp]# openssl pkcs12 -export -clcerts -in server.crt -inkey server.key -out server.p12
unable to load certificates
[root@localhost tmp]#
[root@localhost tmp]#
[root@localhost tmp]#
[root@localhost tmp]# openssl pkcs12 -export -clcerts -in server.crt -inkey server.key -out server.p12
unable to load certificates
[root@localhost tmp]# openssl ca -in server.csr -out server.crt -cert ca.crt -keyfile ca.key
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4 (0x4)
Validity
Not Before: Dec 28 11:27:43 2023 GMT
Not After : Dec 27 11:27:43 2024 GMT
Subject:
countryName = CN
stateOrProvinceName = HuNan
organizationName = LiteGrayFish
organizationalUnitName = JRT Server
commonName = jrt.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
5E:EC:DD:BA:F7:04:50:57:C0:55:C4:0D:55:D8:4F:73:77:2D:2E:AD
X509v3 Authority Key Identifier:
keyid:55:7E:11:6E:30:48:87:C3:DE:12:3C:00:0D:5C:5B:5D:B4:76:CC:BD
Certificate is to be certified until Dec 27 11:27:43 2024 GMT (365 days)
Sign the certificate? [y/n]:y
failed to update database
TXT_DB error number 2
[root@localhost tmp]# openssl ca -in server.csr -out server1.crt -cert ca.crt -keyfile ca.key
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4 (0x4)
Validity
Not Before: Dec 28 11:28:04 2023 GMT
Not After : Dec 27 11:28:04 2024 GMT
Subject:
countryName = CN
stateOrProvinceName = HuNan
organizationName = LiteGrayFish
organizationalUnitName = JRT Server
commonName = jrt.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
5E:EC:DD:BA:F7:04:50:57:C0:55:C4:0D:55:D8:4F:73:77:2D:2E:AD
X509v3 Authority Key Identifier:
keyid:55:7E:11:6E:30:48:87:C3:DE:12:3C:00:0D:5C:5B:5D:B4:76:CC:BD
Certificate is to be certified until Dec 27 11:28:04 2024 GMT (365 days)
Sign the certificate? [y/n]:y
failed to update database
TXT_DB error number 2
[root@localhost tmp]# openssl pkcs12 -export -clcerts -in server.crt -inkey server.key -out server.p12
unable to load certificates
[root@localhost tmp]# openssl ca -in server.csr -out server.crt -cert ca.crt -keyfile ca.key
Using configuration from /etc/pki/tls/openssl.cnf
I am unable to access the /etc/pki/CA/newcerts directory
/etc/pki/CA/newcerts: No such file or directory
[root@localhost tmp]# mkdir /etc/pki/CA/newcerts
[root@localhost tmp]# openssl ca -in server.csr -out server.crt -cert ca.crt -keyfile ca.key
Using configuration from /etc/pki/tls/openssl.cnf
/etc/pki/CA/index.txt: No such file or directory
unable to open '/etc/pki/CA/index.txt'
140532129445776:error:02001002:system library:fopen:No such file or directory:bss_file.c:402:fopen('/etc/pki/CA/index.txt','r')
140532129445776:error:20074002:BIO routines:FILE_CTRL:system lib:bss_file.c:404:
[root@localhost tmp]# touch /etc/pki/CA/index.txt
[root@localhost tmp]# openssl ca -in server.csr -out server.crt -cert ca.crt -keyfile ca.key
Using configuration from /etc/pki/tls/openssl.cnf
/etc/pki/CA/serial: No such file or directory
error while loading serial number
139751165630352:error:02001002:system library:fopen:No such file or directory:bss_file.c:402:fopen('/etc/pki/CA/serial','r')
139751165630352:error:20074002:BIO routines:FILE_CTRL:system lib:bss_file.c:404:
[root@localhost tmp]# touch /etc/pki/CA/serial
[root@localhost tmp]# openssl ca -in server.csr -out server.crt -cert ca.crt -keyfile ca.key
Using configuration from /etc/pki/tls/openssl.cnf
unable to load number from /etc/pki/CA/serial
error while loading serial number
140221599381392:error:0D066096:asn1 encoding routines:a2i_ASN1_INTEGER:short line:f_int.c:210:
[root@localhost tmp]# vi /etc/pki/CA/serial
[root@localhost tmp]#
[root@localhost tmp]# openssl ca -in server.csr -out server.crt -cert ca.crt -keyfile ca.key
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Dec 28 11:33:41 2023 GMT
Not After : Dec 27 11:33:41 2024 GMT
Subject:
countryName = CN
stateOrProvinceName = HuNan
organizationName = LiteGrayFish
organizationalUnitName = JRT Server
commonName = jrt.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
5E:EC:DD:BA:F7:04:50:57:C0:55:C4:0D:55:D8:4F:73:77:2D:2E:AD
X509v3 Authority Key Identifier:
keyid:55:7E:11:6E:30:48:87:C3:DE:12:3C:00:0D:5C:5B:5D:B4:76:CC:BD
Certificate is to be certified until Dec 27 11:33:41 2024 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@localhost tmp]# openssl pkcs12 -export -clcerts -in server.crt -inkey server.key -out server.p12
Enter Export Password:
Verifying - Enter Export Password:
[root@localhost tmp]# keytool -importkeystore -srckeystore server.p12 -destkeystore server.jks -srcstoretype pkcs12 -deststoretype jks
Importing keystore server.p12 to server.jks...
Enter destination keystore password:
Re-enter new password:
Enter source keystore password:
Entry for alias 1 successfully imported.
Import command completed: 1 entries successfully imported, 0 entries failed or cancelled
Warning:
The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using "keytool -importkeystore -srckeystore server.jks -destkeystore server.jks -deststoretype pkcs12".
这样就完成了https的支持