Ubuntu 申请 SSL证书并搭建邮件服务器
文章目录
-
- Log
- 一、域名连接到泰坦(Titan)电子邮件
- 二、NameSilo Hosting 避坑
- 三、Ubuntu 搭建邮件服务器
-
- 1. 环境准备
- 2. 域名配置
- 3. 配置 Postfix 和 Dovecot
-
- ① 安装 Nginx
- ② 安装 Tomcat
- ③ 申请 SSL 证书(Let's Encrypt)
- ④ 配置 postfix
- ⑤ 配置 Dovecot
- 4. 配置 SpamAssassin 和 OpenDKIM
-
- ① 配置 SpamAssassin
- ② 配置 OpenDKIM
- 参考教程:
- 总结
Log
2024.01.13啊,2024年了啊,稍微记录下吧。查了一圈似乎没有相关的教程,那咱就自己摸索着写一篇吧
2024.01.15有事鸽了一天,今天继续;乐了,不支持SSH,退款了
2024.01.16来了
2024.01.17继续搞;教程有点老了,各种版本更新、服务停止支持,跟扒皮一样一层层去找下一步的解决方案,过程倒是挺有趣,但人也有点麻;Let’s Encrypt的证书申请完了发现网站进不去了,查解决方案的时候发现之前网站配置CDN的时候用的Cloudflare提供自签证书。。。
2024.01.18接着搞;配置完了客户端连接测试 SSL连接错误,还得再测测,从头查查吧
2024.01.25终于有眉目了,服务器厂家没开放465端口,联系下然后加个 TXT 记录防止邮件滥用。问题解决了就发布叭;并没有,被认为是垃圾邮件发出去了收不到;搞定了。
- 前置条件:注册Namesilo账号,并购买一个域名和一个服务器
- 如果要买 NameSilo 的服务器,请先看 章节二
一、域名连接到泰坦(Titan)电子邮件
- 参考教程: Setup Titan MX and TXT records for NameSilo
- 登录 N a m e S i l o \rm NameSilo NameSilo 账户,进入域名管理页面,随后点击管理此域的 DNS 选项。

- 如果是刚入手的域名,需要删除原有的记录,然后根据自己的服务器的IP添加以下两条记录:
| Hostname | Type | TTL |
|---|---|---|
| A | 3600 | |
| www | A | 3600 |
- 随后设置 MX 记录和 TXT 记录(用于验证域名所有权并激活电子邮件服务),添加以下两条记录:
| Hostname | Type | Target Hostname | TTL | Distance |
|---|---|---|---|---|
| @ | MX | mx2.titan.email | 3600 | 20 |
| Hostname | Type | Text | TTL |
|---|---|---|---|
| @ | TXT/SPF | v=spf1 include:spf.titan.email ~all | 3600 |
- MX记录:邮件交换记录 (Mail Exchange Record),域名系统(DNS)中的一种资源记录类型,用于指定负责处理发往收件人域名的邮件服务器。
- SPF记录:发信者策略架构(Sender Policy Framework),为了防范垃圾邮件而提出来的一种DNS记录类型,用于登记某个域名拥有的用来外发邮件的所有IP地址。
- 最终结果如下:
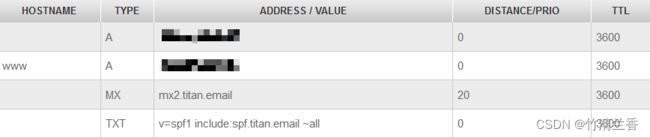
- 进入添加管理邮件页面(需要购买 NameSilo 的 Hosting 服务,第一次进入需要设置备用邮箱,并连接到 T i t a n E m a i l \rm Titan\ \ Email Titan Email):

- 等待域名解析生效后(24小时以内)再次验证:


- 连接成功后就可以添加邮箱了
二、NameSilo Hosting 避坑
-
搞了一下午,最后问客服发现在 NameSilo 上买的服务器不支持 SSH,只能在 cPanel 里点点点,不能用 terminal 敲命令行还玩什么呢。
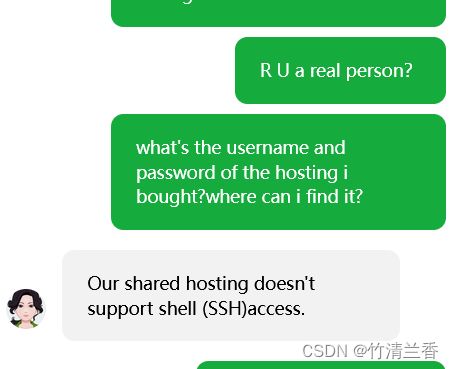
-
单纯写博客用来记录的话倒是可以试下,直接用网站模板拖拽修改排版倒是挺不错的(如果涉及到比较复杂的后台逻辑,想要直接部署一个项目运行的话就不推荐了):
三、Ubuntu 搭建邮件服务器
- 绕回来还是要自己搞,那就找点教程实操一遍,记录下过程和遇到的问题,留以不时之需:
1. 环境准备
- 版本:
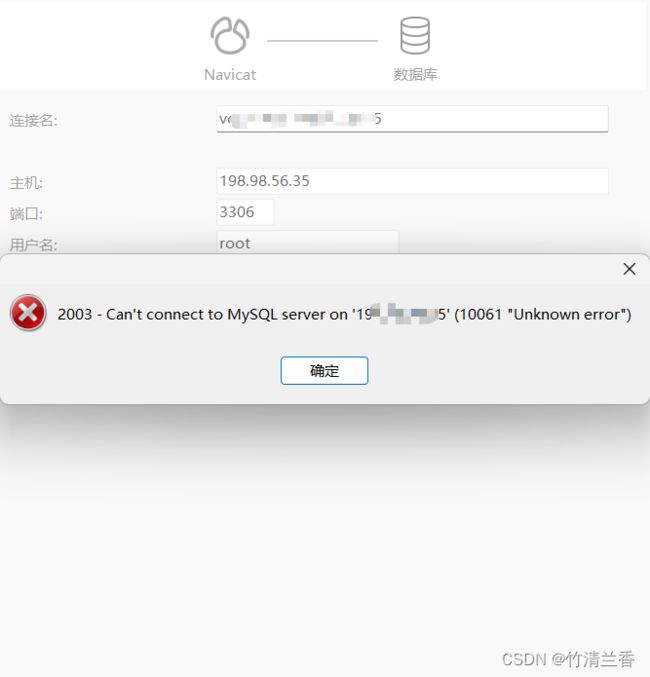
Ubuntu 22.04 LTS - 安装 MySQL:
sudo apt install mysql-server- 命令执行完后
apt已经默认开启服务,因此不需要开启服务以及设置开机自启动
- 命令执行完后
- 相关命令:
- 系统视图:
- 查看状态:
service mysql status - 启动/停止/重启服务:
sudo service mysql start/stop/restart - 查看密码:
sudo cat /etc/mysql/debian.cnf - 进入 MySQL:
sudo mysql
- 查看状态:
- MySQL 视图:
- 系统视图:
2. 域名配置
- 在已有的两条 A 类型解析记录(如下)的基础上进行配置:
| Hostname | Type | TTL |
|---|---|---|
| A | 3600 | |
| www | A | 3600 |
- 添加三个子域名 A 记录:
| Hostname | Type | TTL |
|---|---|---|
| mx | A | 3600 |
| smtp | A | 3600 |
| pop3 | A | 3600 |
- 添加一个 MX 记录:
| Hostname | Type | Target Hostname | TTL | Distance |
|---|---|---|---|---|
| @ | MX | mx.XXX.xxx | 3600 | 20 |
- 添加一个 SPF 记录:
| Hostname | Type | Text | TTL |
|---|---|---|---|
| @ | TXT | v=spf1 mx ~all | 3600 |
- 添加一个 DMARC 记录:
| Hostname | Type | Text | TTL |
|---|---|---|---|
| _dmarc | TXT | v=DMARC1; p=reject; fo=1; rua=mailto:a***@XXX.xxx | 3600 |
3. 配置 Postfix 和 Dovecot
- 安装:
apt updateapt install postfix postfix-mysql dovecot-core dovecot-pop3d dovecot-imapd dovecot-lmtpd dovecot-mysql
- 数据库配置:
- 创建三个数据库表
virtual_domains、virtual_users、virtual_aliases:
- 创建三个数据库表
CREATE TABLE `virtual_domains` (
`id` INT NOT NULL AUTO_INCREMENT,
`name` VARCHAR(50) NOT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB DEFAULT CHARSET=utf8;
CREATE TABLE `virtual_users` (
`id` INT NOT NULL AUTO_INCREMENT,
`domain_id` INT NOT NULL,
`password` VARCHAR(106) NOT NULL,
`email` VARCHAR(120) NOT NULL,
PRIMARY KEY (`id`),
UNIQUE KEY `email` (`email`),
FOREIGN KEY (domain_id) REFERENCES virtual_domains(id) ON DELETE CASCADE
) ENGINE=InnoDB DEFAULT CHARSET=utf8;
CREATE TABLE `virtual_aliases` (
`id` int(11) NOT NULL auto_increment,
`domain_id` int(11) NOT NULL,
`source` varchar(100) NOT NULL,
`destination` varchar(100) NOT NULL,
PRIMARY KEY (`id`),
FOREIGN KEY (domain_id) REFERENCES virtual_domains(id) ON DELETE CASCADE
) ENGINE=InnoDB DEFAULT CHARSET=utf8;
- 插入数据:
- 域名:
insert into virtual_domains values(1,'XXX.xxx') - 用户:
insert into virtual_users values(1,域名序号,md5('密码'),'[email protected]'); - 别名:
insert into virtual_aliases values(1,1,'[email protected]','[email protected]')- (
[email protected]需要先存在于virtual_users中,virtual_aliases中的转发记录才能生效)
- (
- 域名:
① 安装 Nginx
- 安装Nginx 弹出 “Daemons using outdated libraries”,参考解决方案。

- 报错 “./configure: error: the HTTP gzip module requires the zlib library.”,解决:
sudo apt-get install zlib1g-dev - 访问网址显示下图界面为安装成功:

- 备份配置文件:
cp /usr/local/nginx/conf/nginx.conf /usr/local/nginx/conf/nginx.conf.bak
② 安装 Tomcat
- 安装Java环境:
sudo apt install openjdk-17-jre-headless - 安装Tomcat:
sudo wget https://dlcdn.apache.org/tomcat/tomcat-10/v10.1.18/bin/apache-tomcat-10.1.18.tar.gz - 解压Tomcat:
sudo tar -xzvf apache-tomcat-10.1.18.tar.gz -C /usr/local/-C:指定解压⽬录,解决当前⽬录下找不到/usr/local报错
- 启动Tomcat:
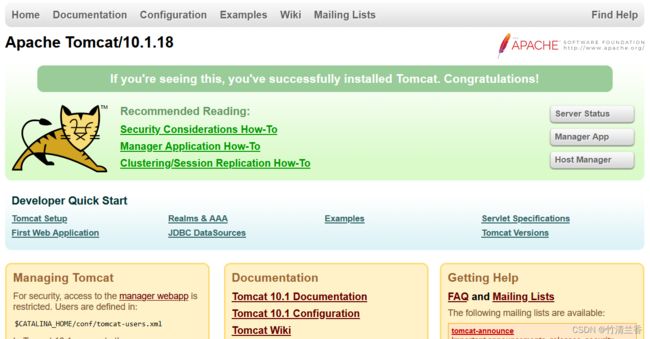
cd /usr/local/apache-tomcat-10.1.18/bin./startup.sh
域名:8080访问进入下图界面为安装成功:
③ 申请 SSL 证书(Let’s Encrypt)
-
安装 snap:
sudo apt updatesudo apt install snapdsnap version
-
通过 snap 安装 certbot:
sudo snap install --classic certbot -
创建的软链接,便于 certbot 命令的使用:
ln -s /snap/bin/certbot /usr/bin/certbot -
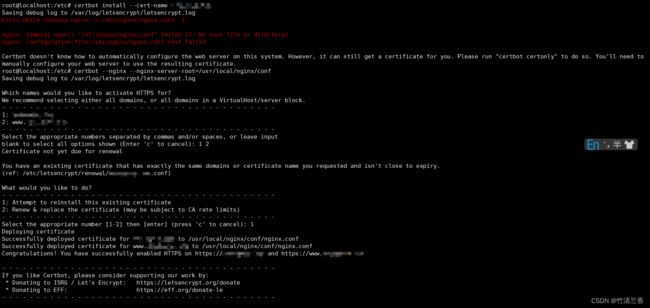
获取证书(Nginx 方式):
certbot certonly --nginx --email 1***@qq.com -d ***.top -d www.***.top -
更新证书:
certbot renew -
续订并重启 Nginx:
certbot renew --renew-hook "service nginx restart"- 如果未到期会提示证书尚未到期更新,也不会重启 Nginx
-
自动续订证书:
30 4 * * 1 certbot renew --renew-hook "service nginx restart" --quiet > /dev/null 2>&1 &- 翻译:每周一的凌晨4点30分,使用Certbot来续订证书,并在完成后重启Nginx服务。所有的输出和错误信息都会被重定向到/dev/null,并且命令会在后台运行。
- 设置系统为北京时间:
sudo timedatectl set-timezone Asia/Shanghai
-
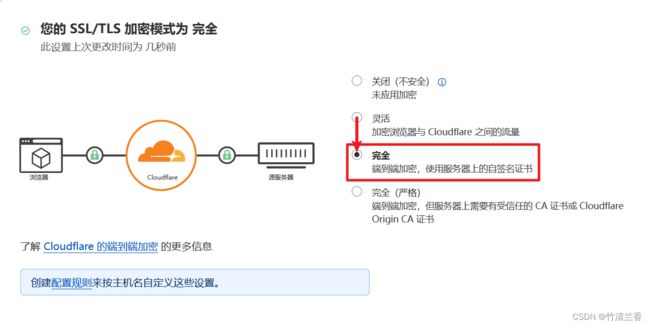
安装完证书访问网站报错,重定向次数过多,解决方法很简单,只需要将 Cloudflare 中的加密模式由灵活(默认模式)修改为完全即可。详细原因可以参考这篇文章的
三:Cloudflare。
④ 配置 postfix
-
官网文档:Postfix文档
-
备份 postfix 的默认配置文件:
cp /etc/postfix/main.cf /etc/postfix/main.cf.bak -
编辑
main.cf:vim /etc/postfix/main.cf- 注释掉下面这部分代码:
- 添加自己的配置(路径里的域名换成自己的):
smtpd_tls_auth_only = yes注释掉表示允许 tls 的 587 端口以及不需要 ssl 验证的 25 端口,用来解决使用 Foxmail 的时候每次登陆都会弹出一个 “安全证书”的问题。
# 使用自己的ssl证书
smtpd_tls_cert_file=/etc/letsencrypt/live/000.top/fullchain.pem
smtpd_tls_key_file=/etc/letsencrypt/live/000.top/privkey.pem
smtpd_use_tls=yes
#smtpd_tls_auth_only = yes
smtp_tls_cert_file=/etc/letsencrypt/live/000.top/fullchain.pem
smtp_tls_key_file=/etc/letsencrypt/live/000.top/privkey.pem
smtp_use_tls=yes
smtpd_tls_CApath=/etc/letsencrypt/live/000.top
smtpd_tls_security_level=may
smtpd_tls_session_cache_database = btree:${data_directory}/smtpd_scache
smtp_tls_CApath=/etc/letsencrypt/live/000.top
smtp_tls_security_level=may
smtp_tls_session_cache_database = btree:${data_directory}/smtp_scache
# 使用dovecot来做身份认证
smtpd_sasl_type = dovecot
smtpd_sasl_path = private/auth
smtpd_sasl_auth_enable = yes
smtpd_recipient_restrictions = permit_sasl_authenticated permit_mynetworks reject_unauth_destination
smtpd_relay_restrictions = permit_mynetworks permit_sasl_authenticated defer_unauth_destination
- 域名相关的基本配置,其他的一般用默认的就行:
myhostname = 000.top
myorigin = $myhostname
mydomain = $myhostname
- 其他配置:
# 确保将邮件投递给 mysql 表中列出的虚拟域
virtual_transport = lmtp:unix:private/dovecot-lmtp
# Postfix 配置虚拟域、用户和别名
virtual_mailbox_domains = mysql:/etc/postfix/mysql-virtual-mailbox-domains.cf
virtual_mailbox_maps = mysql:/etc/postfix/mysql-virtual-mailbox-maps.cf
virtual_alias_maps = mysql:/etc/postfix/mysql-virtual-alias-maps.cf
- 创建上面配置里的三个配置文件并进行配置:
mysql-virtual-mailbox-domains.cfvim /etc/postfix/mysql-virtual-mailbox-domains.cfuser = root password = 123456 hosts = 127.0.0.1:3306 dbname = mailserver query = SELECT 1 FROM virtual_domains WHERE name='%s'
mysql-virtual-mailbox-maps.cfvim /etc/postfix/mysql-virtual-mailbox-maps.cfuser = root password = 123456 hosts = 127.0.0.1:3306 dbname = mailserver query = SELECT 1 FROM virtual_users WHERE email='%s'
mysql-virtual-alias-maps.cfvim /etc/postfix/mysql-virtual-alias-maps.cfuser = root password = 123456 hosts = 127.0.0.1:3306 dbname = mailserver query = SELECT destination FROM virtual_aliases WHERE source='%s'
- 重启服务:
systemctl restart postfix - 测试是否配置成功:
postmap -q 000.top mysql:/etc/postfix/mysql-virtual-mailbox-domains.cf成功则输出1postmap -q [email protected] mysql:/etc/postfix/mysql-virtual-mailbox-maps.cf成功则输出1postmap -q [email protected] mysql:/etc/postfix/mysql-virtual-alias-maps.cf成功则输出[email protected]
- 配置
master.cf:
⑤ 配置 Dovecot
-
配置
dovecot.conf:vim /etc/dovecot/dovecot.conf- 确保启用:
!include conf.d/*.conf - 加入配置,启用协议:
protocols = imap lmtp pop3
-
配置
10-mail.conf:vim /etc/dovecot/conf.d/10-mail.conf- 确保存在配置(该配置确保将邮件存放目录设置在
/var/mail中):mail_location = maildir:/var/mail/vhosts/%d/%nmail_privileged_group = mail
-
创建用户来作为
/var/mail路径的所属人:groupadd -g 5000 vmailuseradd -g vmail -u 5000 vmail -d /var/mailchown -R vmail:vmail /var/mail
-
配置
10-auth.conf: -
配置
auth-sql.conf.ext:vim /etc/dovecot/conf.d/auth-sql.conf.ext- 修改为以下内容:
passdb { driver = sql args = /etc/dovecot/dovecot-sql.conf.ext } userdb { driver = static args = uid=vmail gid=vmail home=/var/mail/vhosts/%d/%n }
-
配置
dovecot-sql.conf.ext:vim /etc/dovecot/dovecot-sql.conf.ext- 确保添加如下配置:
driver = mysqlconnect = host=127.0.0.1 port=3306 dbname=mailserver user=root password=123456default_pass_scheme = MD5password_query = SELECT email as user, password FROM virtual_users WHERE email='%u';
-
将
/etc/dovecot的拥有者改为vmail:dovecot:chown -R vmail:dovecot /etc/dovecotchmod -R o-rwx /etc/dovecot
-
配置
10-master.conf:vim /etc/dovecot/conf.d/10-master.conf- 将
imap-login、pop3-login下第一个的port设置为0,以禁用非 ssl 加密的 imap 和 pop3 协议 - 将
lmtp、auth、auth-worker中的内容修改为以下对应内容:service lmtp { unix_listener /var/spool/postfix/private/dovecot-lmtp { mode = 0600 user = postfix group = postfix } # Create inet listener only if you can't use the above UNIX socket #inet_listener lmtp { # Avoid making LMTP visible for the entire internet #address = #port = #} } service auth { unix_listener /var/spool/postfix/private/auth { mode = 0666 user = postfix group = postfix } unix_listener auth-userdb { mode = 0600 user = vmail #group = } user = dovecot } service auth-worker { # Auth worker process is run as root by default, so that it can access # /etc/shadow. If this isn't necessary, the user should be changed to # $default_internal_user. user = vmail }
-
配置
10-ssl.conf以开启 ssl 认证:vim /etc/dovecot/conf.d/10-ssl.conf- 找到并修改为:
ssl = requiredrequired:必须要有 sslyes:开启 ssl 也允许非 ssl
- 设置 ssl 证书路径:
ssl_cert =ssl_key =
-
查看当前 Dovecot 配置:
dovecot -n -
配置完成,重启后可以使用 Foxmail 连接了:
service postfix restartservice dovecot restart
-
登录失败,到
/var/log查看日志 -
终于找到问题了,记得看看自己的主机厂商有没有开启 465 等端口。
4. 配置 SpamAssassin 和 OpenDKIM
① 配置 SpamAssassin
- 安装:
sudo apt-get install spamassassin spamc - 添加用户:
sudo adduser spamd --disabled-login- 查看用户(详细信息):
cat /etc/passwd - 查看用户(仅用户名):
cat /etc/passwd | cut -d: -f1
- 查看用户(详细信息):
- 配置
spamassassin:vim /etc/default/spamassassin- 确保配置:
ENABLED=1 SAHOME="/var/log/spamassassin/" OPTIONS="--create-prefs --max-children 5 --username spamd --helper-home-dir /home/spamd/ -s /home/spamd/spamd.log" PIDFILE="/var/run/spamd.pid" CRON=1
- 配置
local.cf(用于添加规则):vim /etc/spamassassin/local.cf- 确保开启配置:
rewrite_header Subject ***** SPAM _SCORE_ ***** required_score 5.0 use_bayes 1 bayes_auto_learn 1
- 配置
master.cf: - 重新启动 Postfix 和 SpamAssassin:
sudo service postfix restartsudo service spamassassin restart
② 配置 OpenDKIM
- 安装:
sudo apt install opendkim opendkim-tools - 配置
opendkim.conf:vim /etc/opendkim.conf- 添加以下配置(域名改成自己的):
Domain 000.top KeyFile /etc/dkimkeys/dkim.key Selector dkim SOCKET inet:8891@localhost
- 配置
opendkim:vim /etc/default/opendkim- 添加配置:
SOCKET="inet:8891@localhost"
- 生成 DKIM 密钥对(DKIM :域名密钥识别邮件标准(DomainKeys Identified Mail),电子邮件验证标准)
- 执行命令(域名换成自己的,生成的
dkim.private和dkim.txt在根目录下):sudo opendkim-genkey -t -s dkim -d 000.top
- 移动
dkim.private:sudo mv dkim.private /etc/dkimkeys/
- 切换路径并更改所有者
cd /etc/dkimkeys/sudo chown opendkim:opendkim dkim.private
- 修改文件名(不然重启时会报错):
mv dkim.private dkim.key
- 执行命令(域名换成自己的,生成的
- 配置
main.cf(Postfix):vim /etc/postfix/main.cf- 添加如下配置:
#DKIM smtpd_milters = inet:localhost:8891 non_smtpd_milters = inet:localhost:8891 milter_protocol = 2 milter_default_action = accept
- 重启服务:
sudo service opendkim restartsudo service postfix restart
- 将根目录之前生成的
dkim.txt中括号中的内容去除双引号和换行,作为 TXT 记录添加到域名中
| Hostname | Type | Text |
|---|---|---|
| dkim._domainkey | TXT | v=DKIM1; h=sha256; k=rsa; t=y;p=… |
参考教程:
- ubuntu20 安装和配置mysql8.0.23
- Ubuntu用Postfix+Dovecot搭建优秀的邮件服务器
申请免费ssl证书Ubuntu免费ssl证书(Let’s Encrypt)配置- Ubuntu Nginx 安装与基本配置
- 在ubuntu上使用git克隆github上的项目
- 如何处理ubuntu22.04LTS安装过程中出现“Daemons using outdated libraries”提示
- 【Tomcat】ubuntu系统安装Tomcat
全民https时代,Let’s Encrypt免费SSL证书的申请及使用(Tomcat版)- certbot-auto不再支持所有的操作系统,新的ssl证书方法
- Let’s Encrypt:Your system is not supported by certbot-auto anymore解决方法(证书更新)
- Ubuntu中snap包的安装,删除,更新使用入门教程
- https免费证书(certbot)
- 访问后台出现重定向次数过多该怎么办?-建站需知
- 关于iredmail邮箱系统不使用ssl校验的配置
- Ubuntu下为postfix配置DKIM
- How to Setup SpamAssassin With Postfix On Ubuntu 16.04
官网以及官方文档:
- Postfix主页(德语)
- Postfix文档
- Postfix TLS 支持
- Postfix基本配置
总结
本文记录了如何在一台 Ubuntu 服务器上搭建邮件服务器,主要是安装和配置 Postfix 和 Dovecot,以及 SpamAssassin 和 OpenDKIM 的安装和配置。同时也介绍了如何申请 SSL 证书以及其他服务的相关配置。