CSC8021_Computer network review
Week 1 OS Tutorial
Scenario: Assuming you are the IT manager of University. Please choose the proper operating systems for computers and servers.
Please consider the following situations:
- Lecturers/PhD students/Research associates/Researchers: researchers with various backgrounds, such as computer networks, business, design, embedded systems, etc.
- Staff professional service
- High performance computers (servers)
- Self-maintained servers, such as email servers, authentication servers, etc.
- Any other situations
Common operating systems: Windows, Mac OS, Linux including server version and desktop version.
There are no wrong answers. Please support your points with reasons why that OS is the most suitable choice for that situation.
场景:假设您是大学的IT经理。请为计算机和服务器选择适当的操作系统。
请考虑以下情况: - 讲师/博士生/研究员/研究员:具有各种背景的研究人员,如计算机网络,商业,设计,嵌入式系统等。
- 工作人员专业服务
- 高性能计算机(服务器)
- 自我维护的服务器,如电子邮件服务器、身份验证服务器等。
- 任何其他情况
常用操作系统:Windows、Mac OS、Linux(包括服务器版和桌面版)。
没有错误的答案。请支持你的观点,并说明为什么该操作系统是最适合这种情况的选择。
Answer:
Lecturers/PhD students/Research associates/Researchers: most of them will choose either
Windows or Mac OS based on their preference. Some people may choose Linux because of the areas that they work on, such as computer networks, operating systems, embedded systems, etc. , which is easier for the relevant development. They may also choose Mac OS for design purpose, which contains more software.
Staff professional service: usually Windows, as it is the most popular OS and contains more common software for normal working
High performance computers (servers): usually headless Linux server version, the command line is useful for maintenance and deployment.
Self-maintained servers: usually headless Linux server version as well, the same reason as above.
讲师/博士生/研究助理/研究人员:他们中的大多数人会选择
Windows或Mac OS根据您的偏好。有些人可能会选择Linux,因为他们工作的领域,如计算机网络,操作系统,嵌入式系统等,这是更容易为相关的开发。他们也可以选择Mac OS作为设计目的,因为它包含更多的软件。
员工专业服务:通常是Windows,因为它是最流行的操作系统,包含更多用于正常工作的常用软件
高性能计算机(服务器):通常是无头Linux服务器版本,命令行对维护和部署很有用。
自维护服务器:通常也是无头Linux服务器版本,原因同上。
second Tutorial exercise
Exercise 1
The performance of a client-server system is strongly influenced by two
major network characteristics:
• the bandwidth of the network (how many bits/sec it can transport)
• and the latency (how many seconds it takes the first bit to travel from
the client to the server).
Give an example of a network that exhibits:
a) high bandwidth and high latency
b) low bandwidth and low latency
客户机-服务器系统的性能受到两个方面的强烈影响主要网络特征:
·网络的带宽(每秒可以传输多少比特)
·和延迟(第一比特从传输到第二比特需要多少从客户端到服务器)。
给予一个网络的例子,它显示:
a)高带宽和高延迟
B)低带宽和低延迟
answer:
a)
Satellite / transcontinental fiber (High latency = large distance)
b)
- 56 kbps modem calling a computer in the same building
- Bluetooth network
- RFID network
a)
卫星/洲际光纤(高延迟=长距离)
B) - 56 kbps调制解调器呼叫同一建筑物中的计算机
- 蓝牙网络
- RFID网络
Exercise 2
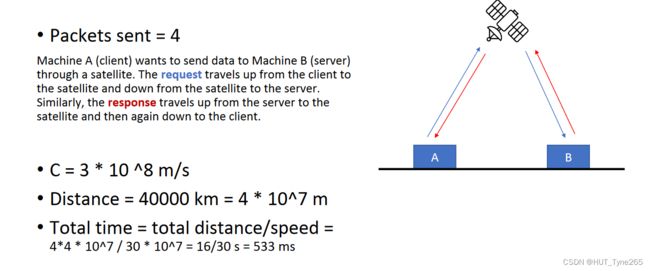
client-server uses a satellite network, with the satellite at a height of 40,000 km. What is the best-case delay in response to a request?
Hit: consider two clients and a satelite.
Exercise 3
a) What are two reasons for using layered protocols?
- Separation of concerns (reduces the complexity of implementation)
- Allows a clear distinction between services and protocols (clear interfaces between layers, each layer )
-
- 关注点分离(降低实现的复杂性)
- 允许明确区分服务和协议(层与层之间的明确接口,每层)
b) What is a disadvantage of using layered protocols? - Redundancy/Repetition of functionality (addressing shows up in the Data Link Layer and Network Layer, Flow control and error detection/correction show up in Data Lin Layer and Transport Layer)
冗余/功能重复(寻址显示在数据链路层和网络层,流量控制和错误检测/纠正显示在数据线路层和传输层)
Exercise 4
What are the advantages of fiber optics over copper as a transmission
medium? Is there any downside of using optics over copper?
Advantages:
- Speed: (fiber can achieve larger bandwidths and therefore larger data transmission rates)
- More suitable for larger distances compared to copper
- Thinner and lightweight (1000 twisted pairs 1km long = 8000 kg, 2 fibers weight only 100 kg and more capacity)
- Lower attenuation therefore lower number of repeaters (once every 50 km compared to once every 5km for copper)
- Not affected by power surges and failures (i.e. EM interference)
- Better security
Disadvantages:
- Installation cost
- Fragility (core is made of glass – short to long range – or plastic – very short ranges)
- Only supports 1-way communication (need 2 fibers for 2-way comm)
(1 fiber optic cable will typically house may ‘individual’ fibers)
优点:
- 速度:(光纤可以实现更大的带宽,因此更大的数据传输速率)
- 与铜相比,更适合更长的距离
- 更薄、更轻(1000对1 km长的双绞线= 8000 kg,2根光纤仅重100 kg,容量更大)
- 衰减更低,因此中继器数量更少(每50公里一次,而铜线每5公里一次)
- 不受电源浪涌和故障(即电磁干扰)的影响
- 更好的安全性
缺点:
- 安装成本
- 易碎性(核心由玻璃制成-短到长距离-或塑料-非常短的距离)
- 仅支持单路通信(需要2根光纤才能实现双路通信)
(1根光纤电缆通常可容纳5根“单独”光纤)
Exercise 5
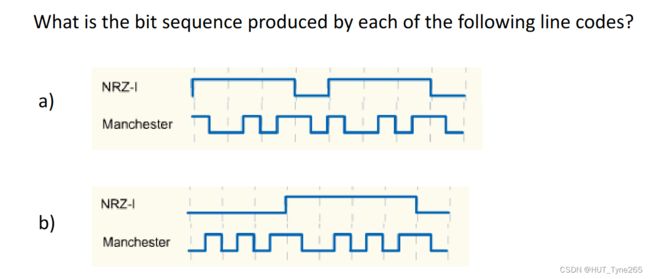
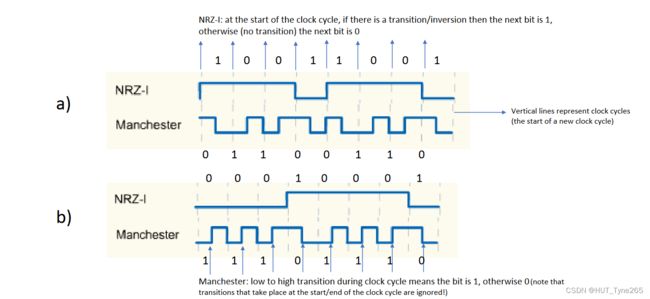 NRZ-I: at the start of the clock cycle, if there is a transition/inversion then the next bit is 1,otherwise (no transition) the next bit is 0
NRZ-I: at the start of the clock cycle, if there is a transition/inversion then the next bit is 1,otherwise (no transition) the next bit is 0
NRZ-I:在时钟周期开始时,如果有转换/反转,则下一位为1,否则(无转换)下一位为0
Vertical lines represent clock cycles(the start of a new clock cycle)
垂直线表示时钟周期(新时钟周期的开始)
Manchester: low to high transition during clock cycle means the bit is 1, otherwise 0(note that transitions that take place at the start/end of the clock cycle are ignored!)
曼彻斯特:在时钟周期期间从低到高的转换意味着该位为1,否则为0(注意,忽略在时钟周期开始/结束时发生的转换!)
week2
Role of the Data Link Layer(understand)
Communication through the physical layer is inherently unreliable
通过物理层的通信本质上是不可靠的
Service: reliable data transmission between adjacent nodes(single communication link)
• Framing – partitions a bit stream into discrete units, called frames
• Error control – detects and corrects errors introduced by the Physical Layer
• Flow control – ensures slow receiver is not out-paced by fast sender
服务:相邻节点之间可靠的数据传输(单一通信链路)
·成帧-将比特流分割成离散单元,称为帧
·错误控制-检测和纠正物理层引入的错误
·流量控制-确保慢速接收器不会被快速发送器超过
Framing methods(apply)
The transmitted element in Data Link layer is called a frame
数据链路层中传输的元素称为帧
A frame is regarded either as a block of characters, or as a sequence of bits
一个帧可以看作是一个字符块,也可以看作是一个比特序列
The sender assembles/breaks an incoming sequence of packets (from network layer) into frames
发送方将(来自网络层的)传入数据包序列组装/分解为帧
The receiver must determine the first and last bit/byte of the frame so that the frames can then be extracted
接收器必须确定帧的第一个和最后一个比特/字节,以便随后可以提取帧
(Bit synchronization is done by physical layer – remember RZ, Manchester, NRZI?)
(Bit同步由物理层完成-记住RZ、曼彻斯特、NRZI?)

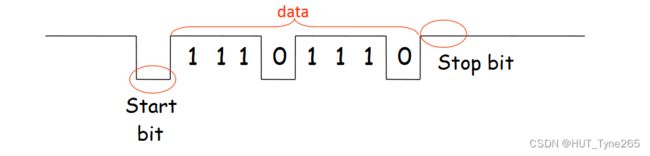
Fixed frame size
Payload is transmitted one character at a time.
有效载荷一次传输一个字符。
5 to 8 bits can be accommodated
可容纳5至8位
Timing only needs maintaining within each character
时间只需要保持在每个字符
There is no common clock at sender and receiver
发送方和接收方没有共同的时钟
Synchronisation takes place with each character through start and stop bits
同步发生在每个字符通过开始和停止位
This is method used on computer serial cables
(eg to RS232/ RJ45 from computer to modem)
这是用于计算机串行电缆的方法
(eg从计算机到调制解调器的RS232/ RJ45)
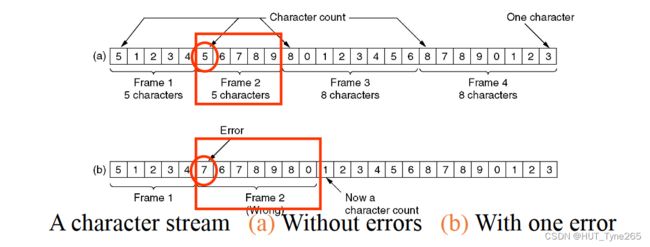
Character count
Payload is transmitted as a variable length block of characters preceded by a character count
有效负载作为前面有字符计数的可变长度字符块进行传输
Count can be corrupted after which it is impossible to determine frame boundaries
计数可能会损坏,在此之后无法确定帧边界
Start and end characters…
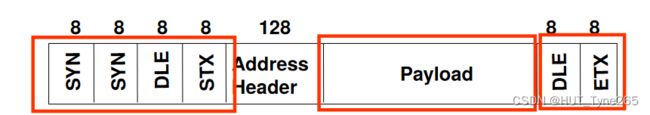 Payload transmitted as a variable length block of characters
Payload transmitted as a variable length block of characters
作为可变长度字符块传输的有效负载
The start of each frame is indicated by a preamble(SYN,SYN,DLE,STX)
每个帧的开始由前同步码指示
The end of each frame is indicated by a postamble(DLE,ETX)
每个帧的结束由后同步码表示
This is more efficient than fixed frame size transmission
这比固定帧大小传输更有效
Problem: the DLE ETX character sequence might appear in the payload of the frame. This would cause the protocol software to assume(incorrectly) that the frame was finished at that point
问题:DLE ETX字符序列可能出现在帧的有效负载中。这将导致协议软件(错误地)假设帧在该点完成
Byte stuffing
Solution: send an extra DLE character before each DLE character in the payload
• You then regard a payload DLE DLE as a single payload DLE
• This is known as byte stuffing
解决方案:在有效载荷中的每个DLE字符之前发送额外的DLE字符
·然后将有效负载DLE DLE视为单个有效负载DLE
·这被称为字节填充。
Example: how is the data sequence DLE DLE ETX sent?

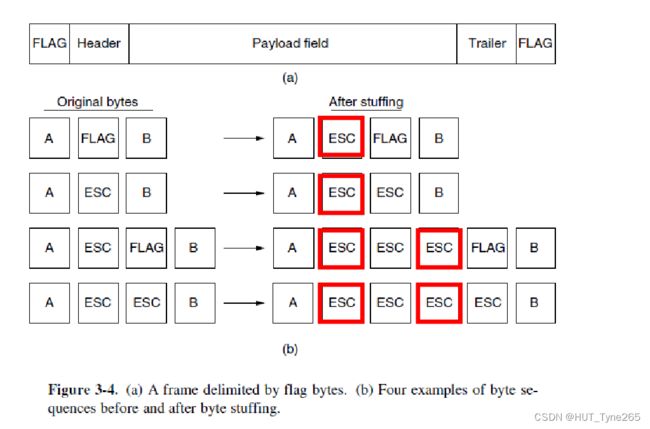 (a)A frame delimited by flag bytes
(a)A frame delimited by flag bytes
(b)Four example of byte sequences before and after byte stuffing
(a)A由标志字节分隔的帧
(B)字节填充之前和之后的字节序列的四个示例
Start and end flags with bit stuffing
 End a frame with a special bit-sequence: 01111110
End a frame with a special bit-sequence: 01111110
• Bit Stuffing is now required for transparency:
• Sender: if five consecutive 1s have been transmitted in the body of the message, insert a 0
• Receiver: should five consecutive 1s arrive, look at the next bit(s):
– if the next bit is a 0: remove it
– if the next bits are 10: found end-of-frame marker
– if the next bits are 11: this is an error
以特殊位序列结束帧:01111110
·透明度现在需要位填充:
·0:如果消息正文中已经发送了五个连续的1,则插入0
·接收器:如果五个连续的1到达,则查看下一个比特:
- 如果下一位是0:则将其删除
- 如果接下来的比特是10:找到帧结束标记
- 如果接下来的位是11:这是错误
 (a)字节填充
(a)字节填充
要发几个+发送内容
00000101=5 发5个字节 内容 A B ESC FLAG
(b)字节填充的标志字节法
1.在发送的内容首尾加上flag
2.在发的内容里面如果有ESC和FLAG则在这前面再加一个ESC
FLAG A B ESC ESC ESC FLAG FLAG
©比特填充的首尾标志字节
1.首尾加上特殊比特模式01111110
2.发送的内容中若有连续的5个1在其后加1个0
01111110 A B
Error handling(understand)
Whenever signals are transmitted over long distances,the signal weakens, and noise is introduced. The receiver cannot resolve the signal levels. This introduces transmission error.
当信号远距离传输时,信号减弱,并引入噪声。接收器无法解析信号电平。这引入了传输误差。

Redundant data
Redundant data is added to the message to allow:
• detection and correction at destination (error correction)
• detection and subsequent retransmission (error detection)
• Error correction requires more redundancy and depends on assumptions made about types of errors.
• A missing message will defeat any level of redundancy!
• Error correction sometimes used for poor links
• Must be supplemented by error detection and retransmission
• Can occur concurrently at more than one OSI layer
将冗余数据添加到消息中,以允许:
·在目的地的检测和校正(错误校正)
·检测和随后的重传(错误检测)
·纠错需要更多的冗余,并取决于对错误类型的假设。
·丢失消息将击败任何级别的冗余!
·错误校正有时用于不良链接
·必须辅以错误检测和重传
·可以在多个OSI层同时发生
Parity bit(apply)
Consider a byte transmitted without redundant data
• 256 possible values 00000000 to 11111111
Now consider the addition of a parity bit
• 512 possible values 00000000x to 11111111x
• X is chosen so that the number of 1’s is even (or odd)
• 256 valid values
• Can detect a single bit error
考虑一个没有冗余数据传输的字节
· 256个可能值0000000到1111111
现在考虑添加奇偶校验位
· 512个可能值0000000x到1111111x
·选择X,使得1的数量为偶数(或奇数)
· 256个有效值
·可以检测单个位错误
Checksum(understand)
A checksum performs a mathematical calculation on a sequence of numbers within the data frame, and records the result in the header.
• The recipient will repeat the calculation and compare the result with the transmitted value.
• Used for error detection.
• Examples of widely-used checksums:
• Internet checksum (part of the IP protocol – Network layer)
• CRC (Cyclic Redundant Check – Data link layer)
校验和对数据帧内的数字序列执行数学计算,并将结果记录在报头中。
·接收方将重复计算并将结果与传输的值进行比较。
·用于错误检测。
·广泛使用的校验和示例:
·互联网校验和(IP协议的一部分-网络层)
· CRC(循环冗余校验-数据链路层)
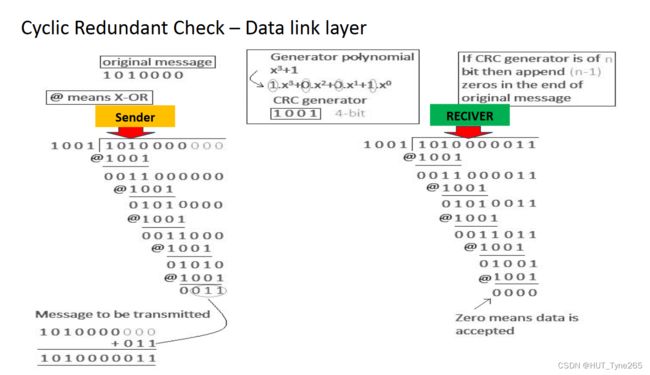 异或:相同得0,相异得1
异或:相同得0,相异得1
在原数据末端加0,多项式的阶数是多少就加几个0
将校验和加在数据项之后,就是带有CRC校验的数据
拼接的校验和长度应与之前加0的个数相等(或者等于除数长度-1)
The Data Link Layer in Broadcast Networks
Medium Access Control (MAC) sublayer
Broadcast channels
A single shared transmission medium is called a broadcast/multiaccess
channel
单个共享传输介质称为广播/多路访问信道
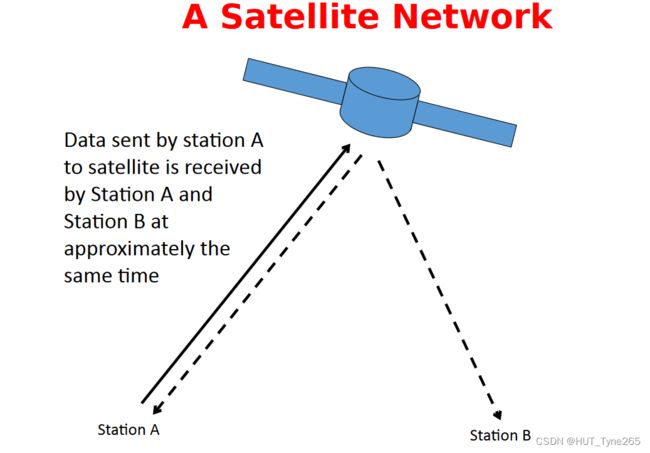
There are two basic types of broadcast networks:
• Satellite networks. These have a very long delay(about 270 msec). The protocols used on satellite channels are called Aloha. There are, of course,several variations.
• Local area networks (LAN). These have a very short delay. Protocols are called CSMA (Carrier Sense Multiple Access), again with several variations.
广播网络有两种基本类型:
·卫星网络。这些具有非常长的延迟(大约270毫秒)。在卫星频道上使用的协议被称为Aloha。当然,有几种变化。
·局域网(LAN)。它们有很短的延迟。协议被称为CSMA(载波侦听多路访问),也有几个变体。
Pure Aloha
This was first developed at the University of Hawaii,using a ground-based radio system.
• Users transmit whenever they want. Colliding frames are destroyed.
• If a frame was destroyed, the sender just waits a random amount of time and sends again (otherwise a collision will occur again and again).
• Question: What is the throughput at low/high load?
• Under low load, there will be almost no collisions.
• The throughput will degrade after the channel reaches about 18% utilisation.
这首先是在夏威夷大学开发的,使用地面无线电系统。
·用户可以随时发送信息。冲突帧将被销毁。
·如果一个帧被破坏,发送方只需要等待一段随机的时间,然后再次发送(否则冲突将一次又一次地发生)。
·问:低/高负载时的吞吐量是多少?
·在低负载下,几乎不会发生碰撞。
·在信道达到约18%的利用率之后,吞吐量将降低。
Why is the channel used so poorly in Pure Aloha?
• Example: T is the time to transmit a frame
• Station A transmits a frame
• Station B transmits a frame just before A is finished transmitting
• After the round-trip time, each station hears both frames
• A collision occurs where the transmissions overlap
• Both frames are discarded
• Therefore the collision wasted almost 2T time
为什么这个频道在纯粹的阿罗哈中使用得如此糟糕?
·示例:T是传输帧的时间
·站A发送帧
·站B刚好在A完成传输之前传输帧
·在往返时间之后,每个站听到两个帧
·在传输重叠的地方发生冲突
·两个帧都被丢弃
·因此,碰撞浪费了近2T的时间
Slotted Aloha
Improvement to the Pure Aloha system:
• Divide the time up into discrete intervals, each interval corresponding to one frame (slotted time).
• Stations can only transmit at the start of each time slot.
• This requires one special station to emit a “pip” at the start of each interval (or a series of intervals) for all others to synchronise (like a clock)
The system peaks with a throughput of 37% channel utilization, double the efficiency of Pure Aloha
Pure Aloha系统的改进:
·将时间划分为离散的间隔,每个间隔对应于一个帧(时隙时间)。
站只能在每个时隙的开始发送。
·这需要一个特殊的站在每个间隔(或一系列间隔)的开始发出“pip”,以便所有其他站同步(如时钟)
该系统的吞吐量峰值为37%的通道利用率,是Pure Aloha效率的两倍
Carrier Sense Multiple Access(CSMA)
With Aloha, satellite stations don’t (can’t) listen
• Performance of Aloha systems could be improved if the stations do not transmit without first paying attention to what other stations are doing.
• Stations listen for (sense) the presence of a carrier signal and act accordingly. Variations are called:
• 1-persistent
• Non-persistent
• P-persistent
• CSMA/CD (Collision Detection)
• CSMA only makes sense on systems with short delays such as LANs.
有了阿罗哈,卫星站不(不能)听
·如果站点在不首先注意其他站点正在做什么的情况下不进行发送,则可以改善Aloha系统的性能。
·站监听(感测)载波信号的存在并相应地采取行动。变体称为:
· 1-持久
·非持久性
·P-持久
· CSMA/CD(碰撞检测)
· CSMA仅在具有短延迟的系统(如局域网)上有意义。
1-persistent
When a station has data to send, it first listens to the channel to see if anyone else is transmitting.
• If the channel is busy, the station waits until it becomes idle.
• When the station detects an idle channel, it immediately transmits a complete frame.
• If the frame is damaged, the station waits a random amount of time and starts all over again.
• This protocol is called 1-persistent because the station transmits with a probability of 1 whenever it finds the channel idle.
Intuitively, this is better than both ALOHA protocols.
• However, if two stations are waiting, both will detect that it has become idle and then transmit simultaneously.
当一个站有数据要发送时,它首先监听信道,看看是否有其他人在发送。
·如果信道忙碌,则站等待直到其变为空闲。
·当站点检测到空闲信道时,它立即发送完整的帧。
·如果帧损坏,站点会随机等待一段时间,然后重新开始。
·该协议被称为1-持久,因为站每当发现信道空闲时以概率1发送。
直觉上,这比两个ALOHA协议都要好。
然而,如果两个站都在等待,则两者都将检测到它已变为空闲,然后同时发送。
non-persistent
This protocol is less greedy than 1-persistent.
• When the sending station detects that the channel is busy, it does not continuously sense it for the purpose of seizing it immediately upon detecting the end of the previous transmission.
• Instead it waits a random period of time and then repeats the algorithm.
• Intuitively, this algorithm should lead to a better channel utilisation (fewer collisions), but longer delays (waiting to sense), than 1-persistent CSMA
这个协议比1-persistent协议更不贪婪。
·当发送站检测到信道忙碌时,它不会为了在检测到先前传输的结束时立即占用它的目的而连续地感测它。
相反,它等待一段随机的时间,然后重复算法。
·直观地,该算法应该导致比1-持久CSMA更好的信道利用率(更少的冲突),但是更长的延迟(等待感测)
P-persistent
This protocol applies to ‘slotted’ channels. One ‘slot’ equals one packet transmission time – there is no ‘pip’.
• When a station becomes ready to send, it senses the channel. If it is idle, it transmits with a probability p(therefore the probability that it defers transmission until the next slot is q = 1 – p).
• If that slot is also idle, it either transmits or defers again, with probabilities p and q respectively.
• If a slot is busy, it waits a random amount of time and starts again.
该协议适用于“时隙”信道。一个“时隙”等于一个数据包传输时间-没有“pip”。
·当一个站准备好发送时,它会感知信道。如果它是空闲的,则它以概率p发送(因此它推迟发送直到下一个时隙的概率是q = 1 - p)。
·如果该时隙也是空闲的,则它再次发送或推迟,概率分别为p和q。
·如果插槽忙碌,它会等待一段随机的时间,然后重新开始。
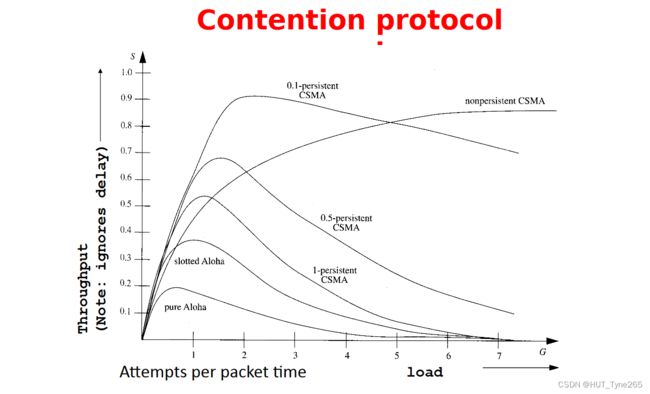
CSMA/CD (Collision Detection)
In the previous protocols, a station sends a complete packet, then decides if it was damaged.
• With CSMA/CD, a station aborts its transmission as soon as it detects a collision.
• This requires some highly special electronics. The stations must sense the channel during transmission,
and compare it with what they have sent (in real-time).
• Quickly terminating damaged frames saves time and bandwidth.
• This protocol, known as CSMA/CD, is widely used on LANs including Ethernet.
在以前的协议中,一个站发送一个完整的分组,然后决定它是否被损坏。
·使用CSMA/CD,一旦检测到冲突,站点就会中止其传输。
这需要一些非常特殊的电子设备。站必须在传输期间感测信道,
然后,将它与他们发送的内容进行比较。
·快速终止损坏的帧可以节省时间和带宽。
该协议称为CSMA/CD,广泛用于包括以太网在内的局域网。
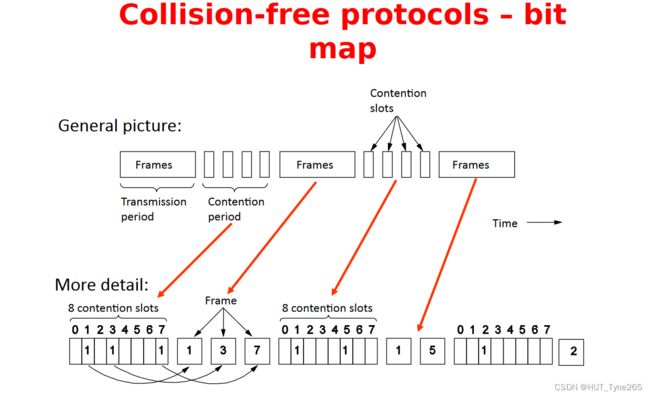
Collision-free protocols
It is possible to arrange protocol features in such a way that collisions simply cannot occur.
• The essential feature of such protocols is that the channel is ‘divided up’ between the hosts, with each host having its own ‘private’ slot.
• Under light loads, this wastes some of the transmission capacity that is idle.
• Under high loads, it works at maximum efficiency.
• A good example is the Bit-map protocol
有可能以这样一种方式安排协议特征,即冲突根本不会发生。
·这种协议的基本特征是信道在主机之间被“划分”,每个主机都有自己的“私有”插槽。
·在轻负载下,这浪费了一些空闲的传输容量。
·在高负载下,它以最高效率工作。
·一个很好的例子是位图协议
Limited contention protocols
Under light load, contention is preferable due to its low delay (collision-free methods have a longer delay)
• As load increases, contention becomes increasingly less attractive. Collision-free methods have a better channel efficiency.
• Obviously, it would be nice if we could combine the best properties of the contention and collision-free protocols, arriving at a new protocol that uses contention at low loads to provide low delay, but uses a collision-free technique at high loads to provide good channel efficiency.
Such protocols are called limited contention protocols.
• The probability of some station acquiring the channel can be increased only by decreasing the amount of competition.
• The limited-contention protocols first divide the stations up into groups.
• Only the members of group j are permitted to compete for slot j. Examples: the Adaptive Tree Walk protocol.
Alternatively, the Binary exponential backoff protocol ,can be used (Ethernet)
在轻负载下,由于其低延迟(无冲突方法具有更长的延迟),
·随着负载的增加,争用变得越来越没有吸引力。无冲突方法具有更好的通道效率。
·显然,如果我们能够联合收割机组合竞争和无冲突协议的最佳特性,从而达到在低负载下使用竞争来提供低延迟,但是在高负载下使用无冲突技术来提供良好的信道效率的新协议,则将是很好的。
这样的协议被称为有限竞争协议。
·只有通过减少竞争量才能增加某些站获取信道的概率。
·有限竞争协议首先将站划分为组。
·仅允许组j的成员竞争槽j。示例:自适应树遍历协议。
或者,可以使用二进制指数退避协议(以太网)
Adaptive Tree Walk protocol
Based on a U.S army algorithm devised for testing soldiers for syphilis during WW2
- Take a blood sample from N soldiers
- Mix a small amount in a single tube and test for antibodies
- If no antibodies are found – all soldiers in the group are healthy
- Else, divide soldiers into two equal groups and repeat process(go to 2)
- 基于美国陆军在二战期间为测试士兵梅毒而设计的算法
1.从N个士兵身上取血样
2.混合少量在一个单一的管和测试抗体
3.如果没有发现抗体-所有的士兵在该组是健康的
4.否则,将士兵分成两个相等的组并重复过程(转到2)
It is convenient to think of the stations as leaves of a binary tree.
• In the first contention slot following a successful frame transmission, slot 0, all stations are permitted to acquire the channel.
• If only one of them does so, fine.
If there is collision, then during the next slot, slot 1, only those stations falling under node 2 in the tree (first sub-tree) may compete.
• If only one of the stations under node 2 acquires the channel, then the following contention slot is reserved for those stations under node 3. Etc…
将站点看作二叉树的叶子是很方便的。
·在成功帧传输之后的第一竞争时隙(时隙0)中,允许所有站获取信道。
·如果只有一个人这么做,那就好。
如果存在冲突,则在下一时隙,时隙1期间,只有落在树(第一子树)中的节点2下的那些站可以竞争。
·如果节点2下的站中只有一个站获取信道,则为节点3下的那些站预留随后的竞争时隙。等等

Binary exponential back-off protocol
After a collision, time is divided up into discrete slots whose length is equal to the worst case round-trip propagation time on the LAN cable.
• After the first collision, each station independently waits either 0 or 1 slot times before trying again. If two stations collide and each one picks the same random number (0 or 1), they will collide again.
• After the second collision, each one picks either 0, 1, 2 or 3 at random and waits that number of slot times.
• If a third collision occurs, then the number of slots to wait is chosen from the interval 0 to 23 – 1.
• After 10 collisions, the number is frozen at 210 -1(1023) slots.
• After 16 collisions, report failure to the computer. Further recovery handled by higher layers.
在冲突之后,时间被划分为离散的时隙,其长度等于LAN电缆上最坏情况下的往返传播时间。
·在第一次冲突之后,每个站在再次尝试之前独立地等待0或1个时隙时间。如果两个站碰撞,并且每个站都选择相同的随机数(0或1),则它们将再次碰撞。
·在第二次冲突之后,每个随机选择0、1、2或3,并等待该时隙次数。
·如果发生第三次冲突,则从0到23 - 1的区间中选择等待的时隙数。
·在10次冲突之后,数量被冻结在210 - 1(1023)个时隙。
·16次碰撞后,向计算机报告故障。进一步恢复由更高层处理。
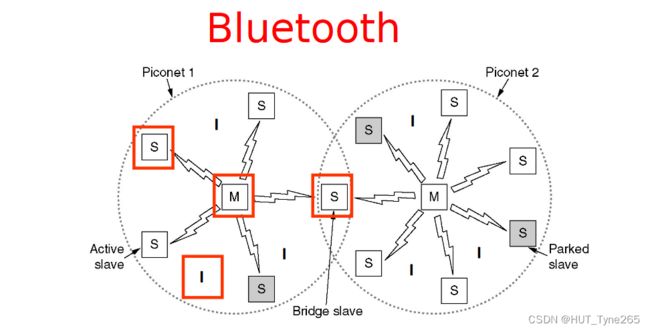 • A piconet contains a master node
• A piconet contains a master node
• …and up to seven active slave nodes within a radius of 10 metres
• A piconet can also contain up to 255 parked (inactive) nodes which have been placed in standby by master
• Multiple piconets can be connected into a scatternet by a bridge slave node
·微微网包含主节点
· …半径10米范围内最多7个活动从节点
·一个微微网还可以包含多达255个已被主节点置于备用状态的停放(非活动)节点
·多个微微网可以通过桥从节点连接成散射网
Exercise C1 - Framing
The following character encoding is used on a data link protocol:
A: 10001111
B: 11001110
FLAG: 01111110
ESC: 11100001
Show the bit sequence transmitted (in binary) for the four-character frame
A B ESC FLAG
when each of the following framing methods are used
a) Byte count
00000101 10001111 11001110 11100001 01111110
b) Flag bytes with byte stuffing
FLAG A B ESC ESC ESC FLAG FLAG
c) Starting and ending flag bytes with bit stuffing
01111110 10001111 101001110 11100001 011111010 01111110
Exercise C2 - Framing
A bit string, 011110111110111110, needs to be transmitted at the data link layer.
What is the string actually transmitted after bit stuffing?
01111011111001111100
Exercise C3 - Framing
One of your classmates, Scrooge, has pointed out that it is wasteful to end each frame with a flag byte and then begin the next one with a second flag byte. One flag byte could do the job as well, and a byte saved is a byte earned. Do you agree?
Tip: what happens if the sender is idle for some time?
(e.g. stops sending data for 15 min after sending a frame that ends with a flag byte)
If endless stream of bytes then one flag byte would be enough to separate frames.
However, if sender stops sending for 15 min (i.e. is idle) and last message ends in a flag byte, then the receiver has no way of knowing if the next byte is the start of a new frame and not just noise on the line.
Framing protocol is much easier if start and end flag bytes are used to delimit a frame.
如果字节流无穷无尽,那么一个标志字节就足以分隔帧。
然而,如果发送方停止发送15分钟(即空闲),并且最后一条消息以标志字节结束,则接收方无法知道下一个字节是否是新帧的开始,而不仅仅是线路上的噪声。
如果使用开始和结束标志字节来定界帧,则成帧协议要简单得多。
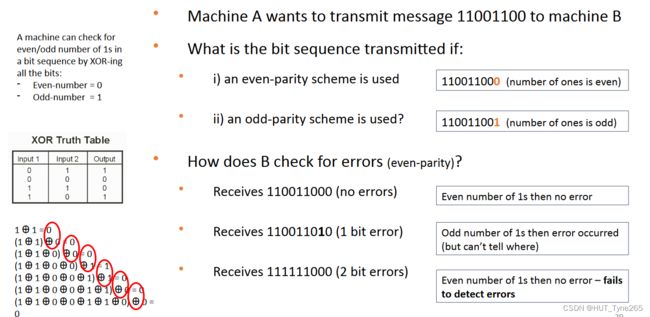
Exercise C4 – Error detection
Machine A wants to transmit message 101101 to machine B using a parity bit for error detection.
-
What is the bit sequence transmitted if:
a) An odd-parity scheme is used?1011011
b) An even-parity scheme is used?1011010 -
Suppose B receives the following message. Assuming an even-parity scheme, can B detect if the message is corrupted? If so, how? If not,why not? Can B detect which bits have been corrupted?
a) 1111010
B detects an error (odd number of 1s), but not which bit has been flipped,retransmission
b) 1010000
B cannot detect error (even number of 1s)
Exercise C5 – Flow control
A channel has a bit rate of 4kbps and a propagation delay of 20 msec.
For what range of frame sizes does stop-and-wait give an efficiency of at least 50%?

Exercise C6 – Multiple Access Protocols
a) What are the three main classes of MAC (medium access protocol)
protocols?
Contention protocols, collision-free, limited contention protocols
b) Give examples of well-known protocols for each of the protocol
classes identified above.
Contention protocols:Pure Aloha, Slotted Aloha, Carrier Sensing Multiple Access (CSMA), 1-persistent, no persistent, p-persistent, CSMA/CD, CSMA/CA
collision-free:bitmap
limited contention protocols:Adaptive Tree Walk Protocol, Binary Exponential Backoff Protocol
c) Classify each of the protocols identified in b) according to:
• It’s use of continuous or slotted time
Pure Aloha, CSMA – (all other Slotted time)
• It’s ability to sense the medium
CSMA
• It’s collision detection capabilities
CSMA/CD (Adaptive tree walk protocol?)
Exercise C7 – Multiple Access Protocols
Identify one multiple access protocol that:
a) Has no carrier sensing capabilities and uses continuous time.
Pure Aloha
b) Has carrier sensing capabilities and uses time slots.
CSMA/CD with Binary Exponential Backoff(Ethernet)
c) Avoids any collisions.
CSMA/CA, bitmap
d) Was used in classic Ethernet.b)
e) Is used by Wi-Fi standard (IEEE 802.11).
MACA or CSMA/CA
f) Provides high throughput under high loads (large N).
P-persistent CSMA (compared to other contention protocols), bitmap avoids collisions altogether (collision-free)
g) Provides low delay under low loads (low N)
Pure aloha or any contention protocol (in general)
Exercise C8 – Multiple Access Protocols
What are the key differences between:
a) Contention and collision free protocols?
Contention protocols will incur lower delay under low load
whereas collision free protocols achieve high throughput under high loads. Describe principles of operation of each class of protocol…
b) CSMA and limited contention protocols?
c) Collision-detection and collision-avoidance CSMA protocols?
CSMA-CA cannot detect collision as it is happening (checks if the packet is damaged once its broadcasted back)
Exercise C9 – Adaptive Tree Walk
Consider a network of eight hosts (A to H) where hosts B, C, and H
try to transmit at the same time.
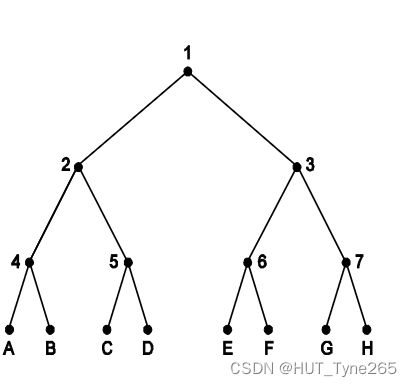
a) For rounds 1 to 5, specify which nodes are allowed to transmit,and whether transmission is successful or whether any of the nodes collide?
1 – Node 1 - all hosts try to transmit, B,C,H collide
2 – Node 2 - B and C try to transmit, B and C collide
3 – Node 4 - B tries to transmit and is successful
4 – Node 5 - C tries to transmit and is successful
5 – Node 3 - H tries to transmit and is successful
b) How would your answer change if B tries to transmit instead of C?
Would require an extra round where leaf nodes A and B are considered individually
1 – Node 1 - all hosts try to transmit, A,B,H collide
2 – Node 2 - A and B try to transmit, A and B collide
3 – Node 4 - A and B try to transmit, A and B collide
4 – Node A - A tries to transmit and is successful
5 – Node B - B tries to transmit and is successful
6 – Node 3 - H tries to transmit and is successful
Exercise C10 – Bluetooth
a) What name is given to a Bluetooth network?piconet
b) What types of nodes exist in a Bluetooth network?Master, slave
- How many nodes of each type can you have in a single network?
1 master, 7 slaves - What is the role of each type of node?
Master – manages connections (all data transmissions go through master node), slave (send/receive data) - What types of connections are allowed?
Master-slave
c) What is (roughly) the maximum distance allowed by Bluetooth connections?10m
d) Is it possible to connect two or more Bluetooth networks?
What name is given to an interconnected collection of Bluetooth systems?scatternet
What name is given to nodes that can form two distinct networks?
Bridge slave
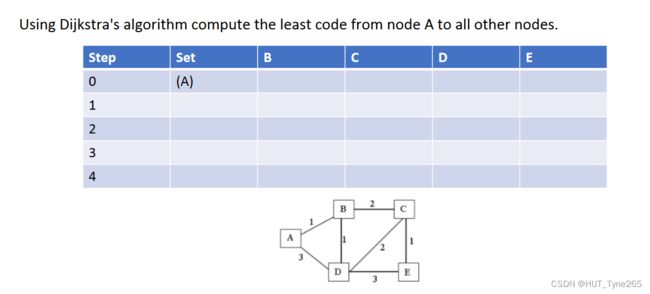
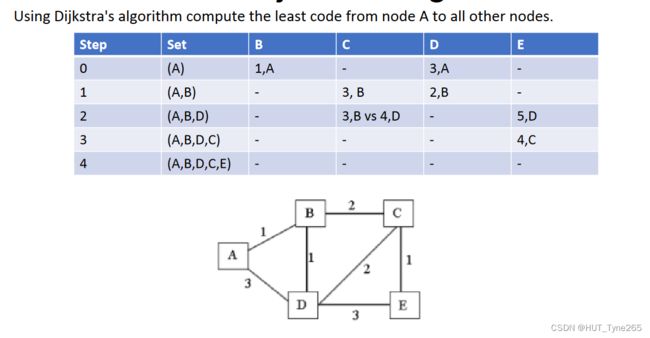
Exercise D1 – Dijkstra’s algorithm
Exercise D2 – Distance Vector Algorithm
Exercise D3
The figure shows routers A, B, C and D connected by links with their associated costs.
• Describe how the routing table (in terms of destination, cost, next hop) for A could get constructed if the routers are using the distance vector technique. Draw the table after each of 2 rounds.
• How does A manage to modify its routing table if the link between A and C breaks, and the distance vector algorithm is re-started? Draw the new table after each of 3 rounds.
图中显示了通过链路连接的路由器A、B、C和D及其相关开销。
·描述如果路由器使用距离向量技术,A的路由表(根据目的地、成本、下一跳)如何构造。每两轮后画一张表。
·如果A和C之间的链路中断,并且重新启动距离向量算法,A如何设法修改其路由表?在3轮中的每一轮之后绘制新的表。
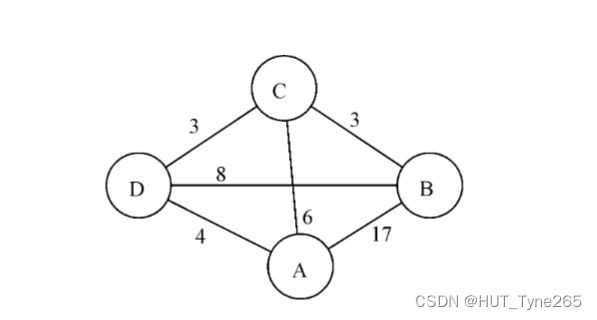 A) Sample Answer:
A) Sample Answer:
i) Routing table for A will initially look like this (after echo packets)
dest cost next hop
A 0 -
B 17 B
C 6 C
D 4 D
A sends this table to its neighbours (in this case B, C, D). A will also receive tables from B, C and D.
Tables from B and D do not provide any improvement (in theory D does show a better route to B but this is overridden by the table from C).
Table from C shows a route to B at cost 3 so the route from A to B via C is 9 and the table is updated.
Like this:
dest cost next hop
A 0 -
B 9 C
C 6 C
D 4 D
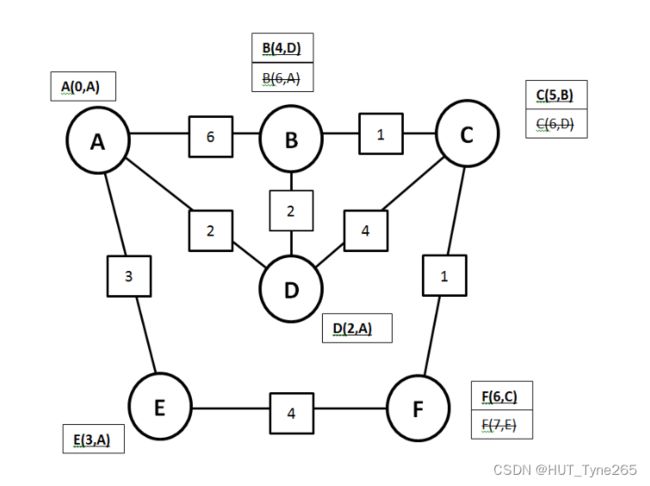
Exercise D4
• The figure shows a network of routers (circles) connected via links with their associated costs
(squares).
• Follow the steps of the Shortest Path routing algorithm until the network is fully labelled and the shortest path from A to F has been found.
·该图显示了通过链路连接的路由器网络(圆圈)及其相关成本(正方形)。
·遵循最短路径路由算法的步骤,直到网络被完全标记并且已经找到从A到F的最短路径。

Packet switching
• In a packet switched network data is transmitted in blocks, known as packets, typically less than 1KB in length.
• Each packet contains a chunk of data and sufficient information for the packet to navigate to its destination and the original data reconstituted.
• A packet arriving at a switch is queued until it is possible to send it on to the next switch by the appropriate route.
• There are 2 basic mechanisms employed for packet switching:datagrams and virtual circuits.
·在分组交换网络中,数据以块的形式传输,称为分组,通常长度小于1KB。
·每个数据包都包含一个数据块和足够的信息,以便数据包导航到其目的地和重建的原始数据。
·到达交换机的数据包将排队,直到可以通过适当的路由将其发送到下一个交换机。
·分组交换有两种基本机制:数据报和虚电路。
Datagrams
• Each datagram is a packet which is treated independently as it traverses the network, each switch
in the network must decide where to send that datagram next.
• It is possible therefore that two datagrams from the same message may take entirely different routes to reach a destination, with the possibility that the order of packets may be changed or than packets may become lost (or terminally delayed) en route.
• Datagram protocols (such as IP) must therefore include sufficient information so that order can be re-instated, missing packets detected and that lost packets are eventually terminated.
·每个数据报都是一个数据包,当它穿过网络时,每个交换机都被独立处理。
必须决定下一个将数据报发送到哪里。
·因此,来自同一消息的两个数据报可能会采取完全不同的路由到达目的地,可能会改变分组的顺序,或者分组可能会在途中丢失(或最终延迟)。
因此,数据报协议(如IP)必须包含足够的信息,以便恢复订单,检测丢失的数据包,并最终终止丢失的数据包。
Virtual Circuits
• In a virtual circuit a preplanned route is set for all packets constituting a message.
• This is achieved by a control packet preceding all the data: each switch makes a decision as the where to send the control, but all subsequent packets follow the control.
• This does not constitute a dedicated route (as in a circuit switched network) as the packets will still be queued at each switch and other virtual circuits may use the same equipment.
·在虚拟电路中,为构成消息的所有分组设置预先规划的路由。
·这是通过在所有数据之前的控制分组来实现的:每个交换机决定将控制发送到哪里,但所有后续分组都遵循控制。
·这不构成专用路由(如在电路交换网络中),因为分组仍将在每个交换机处排队,并且其他虚拟电路可以使用相同的设备。
• The main advantage of the virtual circuit is that each of the switches makes only one route choice per message,
• there is an additional delay in setting up the virtual circuit and the switches must remember the next step of the route for every virtual circuit
• the datagram approach can adapt a route to cope with problems that arise during the transmission of a message
• if messages are generally short or the network unstable, then the datagram approach is better,
• most networks employ some sort of virtual circuit.
·虚电路的主要优点是每个交换机对每个消息仅进行一个路由选择,
·在建立虚拟电路时存在额外的延迟,并且交换机必须记住每个虚拟电路的路由的下一步
·数据报方法可以调整路由以科普消息传输过程中出现的问题
·如果消息通常很短或网络不稳定,那么数据报方法更好,
·大多数网络采用某种虚拟电路。
Comparison between circuit switched and packet switched
• The main reason for employing a packet switched network is to :
• increase carrying capacity.
• Although a packet switched network requires more information to be sent to manage the packets this is generally small enough that a packet switch mechanism will always carry more data than a circuit switch on the same cables.
·采用分组交换网络的主要原因是:
·提高承载能力。
·虽然分组交换网络需要发送更多的信息来管理分组,但是这通常足够小,使得分组交换机制将总是比相同电缆上的电路交换机携带更多的数据。
Transmition Overhead
• For an individual message on an unloaded network the fastest mechanism will be determined by the amount of overhead in routing the data.
• For a circuit switched network this means the time taken to set up the circuit.
• For a datagram this means the cumulative time for routing each packet.
• for a virtual circuit it will be the sum of the time taken to set up the virtual circuit plus the time taken to identify each packet at each switch
·对于未加载网络上的单个消息,最快的机制将由路由数据时的开销量确定。
·对于电路交换网络,这意味着建立电路所需的时间。
·对于数据报,这意味着路由每个数据包的累积时间。
·对于虚拟电路,它将是建立虚拟电路所花费的时间加上在每个交换机处识别每个分组所花费的时间的总和。
Packet Size:
• There is an additional delay in a packet switch network caused by the fact that each switch will not start to send on a packet until it has finished receiving it, whereas in a circuit switch there is no such delay.
• Therefore, small packets travel faster than larger packets,although the more packets there are the more work is needed to route them individually (in a datagram approach).
·在分组交换网络中存在额外的延迟,这是由于每个交换机在完成接收分组之前不会开始发送分组,而在电路交换中没有这种延迟。
·因此,小数据包比大数据包传输得更快,尽管数据包越多,单独路由它们所需的工作就越多(在数据报方法中)。
Circuit setup time:
• Generally the time to initiate a circuit is very similar whether that circuit is physical (circuit switched) or not (packet switched with virtual circuit).
• Thus a packet switched network with virtual circuit will generally be slower than a circuit switched network (although is has a larger capacity).
·通常,无论电路是物理的(电路交换)还是非物理的(具有虚拟电路的分组交换),发起电路的时间都非常相似。
·因此,具有虚拟电路的分组交换网络通常比电路交换网络慢(尽管它具有更大的容量)。
Network Load
• In a lightly loaded network a datagram approach may be faster than a circuit switch as each datagram can potentially take a separate route to the destination.
• However, if the number of short alternative routes is small (relative to the number of packets) then the cumulative delay of routing every packet will be greater than the set up of the circuit, so the circuit switched will be faster.
• If there are a large number of packets on each possible route then the datagram approach may be
slower than the virtual circuit.
·在轻负载网络中,数据报方法可能比电路交换更快,因为每个数据报可能采取单独的路由到达目的地。
·然而,如果短替代路由的数量很小(相对于数据包的数量),则路由每个数据包的累积延迟将大于电路的建立,因此电路交换将更快。
·如果在每个可能的路由上存在大量分组,则数据报方法可以是比虚电路慢。