【软考网络工程师】华为路由器&交换机配置
文章目录
-
- 写在前面
- DHCP
-
- 案例
- 拓扑
- 具体配置过程
- 检验
- ACL
-
- 案例
- 拓扑
- 具体配置过程
- 验证
- 静态NAT & 动态NAT & Easy IP & NAT Server
-
- 案例
- 拓扑
- 具体配置过程
- 验证
- NAPT
-
- 案例
- 拓扑
- 具体配置过程
- 验证
- VRRP
-
- 案例
- 拓扑
- 具体配置过程
- 验证
- BFD
-
- 案例
- 拓扑
- 具体配置过程
- 验证:
- POE
-
- 简单配置
- Firewall
-
- 拓扑
- 简单配置
- IPSec VPN
-
- 拓扑
- 基本配置
- 结语
- 参考资料
写在前面
还有几天就软考了,考个证混混分。
ENSP工具版本: v1.2.00.510
DHCP
案例
目的: 对交换机配置DHCP,实现PC自动获取IP地址。
设备概述: 设置两个vlan,分别为vlan10 和 vlan 20。然后将两个PC分别划分到两个vlan里。设置两个交换机S5700,分别为辅助交换机(acsw)和核心交换机(coresw)。
拓扑
具体配置过程
acsw:
<Huawei>system-view
[Huawei]undo info-center enable // 关闭日志通知
[Huawei]sysname acsw
[acsw]vlan batch 10 20
[acsw]int g0/0/1 // 有些地方命令直接简写执行了,勿喷
[acsw-GigabitEthernet0/0/1]port link-type access // 配置acsw与PC1连接方式为access
[acsw-GigabitEthernet0/0/1]port default vlan 10 // 默认vlan为vlan 10
[acsw-GigabitEthernet0/0/1]quit
[acsw]int g0/0/2
[acsw-GigabitEthernet0/0/2]port link-type access
[acsw-GigabitEthernet0/0/2]port default vlan 20
[acsw-GigabitEthernet0/0/2]quit
[acsw]int g0/0/3
[acsw-GigabitEthernet0/0/3]port link-type trunk
[acsw-GigabitEthernet0/0/3]port trunk allow-pass vlan 10 20
[acsw-GigabitEthernet0/0/3]q
PC1:
PC2:
coresw:
<Huawei>system-view
[Huawei]undo info-center enable
[Huawei]sysname coresw
[coresw]vlan batch 10 20
[coresw]int g0/0/1
[coresw-GigabitEthernet0/0/1]port link-type trunk
[coresw-GigabitEthernet0/0/1]port trunk allow-pass vlan 10 20
[coresw-GigabitEthernet0/0/1]q
[coresw]dhcp enable
[coresw]ip pool vlan10
[coresw-ip-pool-vlan20]? // 这里看一下都有那些选项可以配置
ip-pool view commands:
configuration Configuration interlock
display Display current system information
dns-list Configure DNS servers
domain-name Configure domain name
excluded-ip-address Mark disable IP addresses
gateway-list Configure the gateway
lease Configure the lease of the IP pool
lock Lock the IP pool
mtrace Trace route to multicast source
nbns-list Configure the windows's netbios name servers
netbios-type Netbios node type
network Add a network
next-server The address of the server to use in the next step of the
client's bootstrap process.
option Configure the DHCP options
option121 DHCP option 121
option184 DHCP option 184
ping Send echo messages
quit Exit from current command view
reset Reset operation
return Exit to user view
screen-width Set screen width
set Set
stack Stack
static-bind Static bind
test-aaa Accounts test
trace Trace route (switch) to host on Data Link Layer
tracert Trace route to host
undo Cancel current configuration
-instance Config VPN instance
[coresw-ip-pool-vlan10]network 192.168.10.0 mask 24
[coresw-ip-pool-vlan10]gateway-list 192.168.10.254 // 设置vlan10的网关
[coresw-ip-pool-vlan10]excluded-ip-address 192.168.10.150 192.168.10.200 // 设置不用于分配的IP范围
[coresw-ip-pool-vlan10]lease day 3 // 也可以同时设置 hour、minute
[coresw-ip-pool-vlan10]dns-list 8.8.8.8 // 由于用不到DNS,就随便配了
[coresw-ip-pool-vlan10]q
[coresw]interface vlanif 10
[coresw-Vlanif10]ip address 192.168.10.254 24
[coresw-Vlanif10]q
[coresw]int Vlanif 20
[coresw-Vlanif20]ip address 192.168.20.254 24
[coresw-Vlanif20]q
[coresw]ip pool vlan20
[coresw-ip-pool-vlan20]network 192.168.20.0 mask 24
[coresw-ip-pool-vlan20]gateway-list 192.168.20.254
[coresw-ip-pool-vlan20]dns-list 8.8.8.8
[coresw-ip-pool-vlan20]excluded-ip-address 192.168.20.150 192.168.20.200
[coresw-ip-pool-vlan20]lease day 3
[coresw-ip-pool-vlan20]q
[coresw]int vlanif 10
[coresw-Vlanif10]dhcp select global // 选择全局地址池
[coresw-Vlanif10]q
[coresw]int vlanif 20
[coresw-Vlanif20]dhcp select global
[coresw-Vlanif20]q
检验
在PC1终端中输入ipconfig,可以看到华为DHCP默认将最大的可分配IP分配给当前主机:192.168.10.253
PC2同理:
ACL
案例
要求:
设备概述:
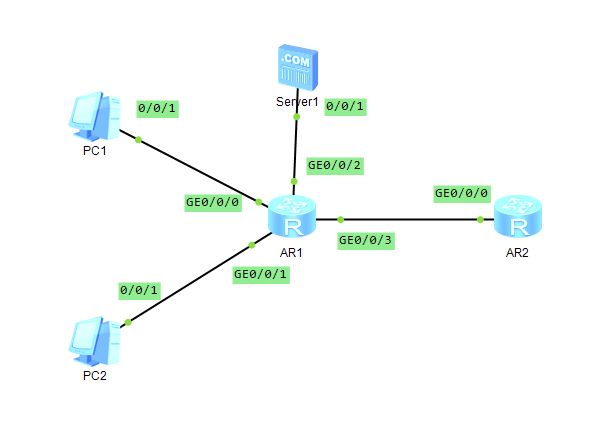
设置两台PC,分别属于不同子网,要求PC1所在子网不得访问服务器,PC2所在子网可以访问服务器。同时外界网络无法访问服务器。设置一台服务器。设置两台路由器AR2220。其中AR2220端口不够的可以自行添加:
拓扑
具体配置过程
PC1:
PC2:
Server1:
AR1:
<Huawei>system-view
[Huawei]sysname AR1
[AR1]undo info-center enable
[AR1]display acl all // 查看所有acl规则
[AR1]int g0/0/0
[AR1-GigabitEthernet0/0/0]ip address 192.168.2.254 24
[AR1-GigabitEthernet0/0/0]q
[AR1]int g0/0/1
[AR1-GigabitEthernet0/0/1]ip address 192.168.3.254 24
[AR1-GigabitEthernet0/0/1]q
[AR1]int g4/0/0
[AR1-GigabitEthernet4/0/0]ip address 10.10.10.1 24
[AR1-GigabitEthernet4/0/0]q
[AR1]acl 3000 // 2000-2999为基础acl配置,3000-3999为高级acl配置
[AR1-acl-adv-3000]rule 10 deny ip source 192.168.2.0 0.0.0.255 destination 192.1
68.4.4 0 // 不允许子网192.168.2.0/24访问金融服务器
[AR1-acl-adv-3000]rule 20 permit ip source 192.168.3.0 0.0.0.255 destination 192
.168.4.4 0 // 允许子网192.168.3.0/24访问金融服务器
[AR1-acl-adv-3000]rule 30 deny ip source any destination 192.168.4.4 0 // 在前面的规则都不匹配时,不允许任何源ip访问服务器
[AR1-acl-adv-3000]q
[AR1]int g0/0/2
[AR1-GigabitEthernet0/0/2]ip address 192.168.4.254 24
[AR1-GigabitEthernet0/0/2]traffic-filter outbound acl 3000
[AR1-GigabitEthernet0/0/2]q
[AR1]display acl all // 可以验证acl规则是否配置成功
Total quantity of nonempty ACL number is 1
Advanced ACL 3000, 3 rules
Acl's step is 5
rule 10 deny ip source 192.168.2.0 0.0.0.255 destination 192.168.4.4 0 (4 match
es)
rule 20 permit ip source 192.168.3.0 0.0.0.255 destination 192.168.4.4 0 (5 mat
ches)
rule 30 deny ip destination 192.168.4.4 0
[AR1]
AR2:
<Huawei>system-view
[Huawei]undo info-center enable
[Huawei]sysname AR2
[AR2]int g0/0/0
[AR2-GigabitEthernet0/0/0]ip address 10.10.10.2 24
[AR2-GigabitEthernet0/0/0]q
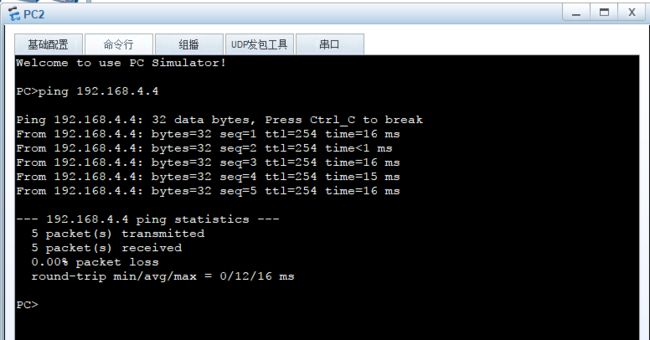
验证
PC1:
PC2:
AR2:
静态NAT & 动态NAT & Easy IP & NAT Server
案例
案例直接用ACL的AR1吧,反正目的是要自己敲一下,执行一遍,来加深一下印象。
原理:
-
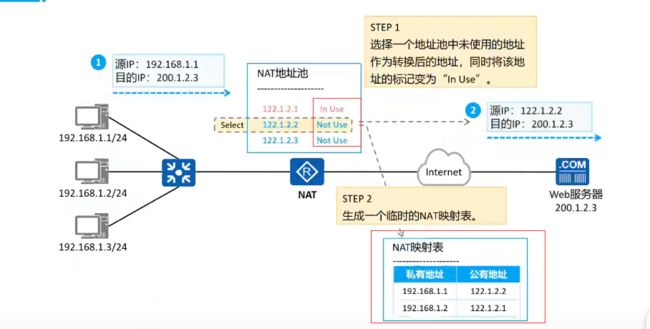
静态NAT:出来一个私网地址分配一个对应的公网地址
-
动态NAT:设置NAT地址池,可以反复使用同一个公网地址:
- Easy IP:直接在路由器出接口上分配不同端口实现NAT转换:
- NAT Server:公私网映射:
拓扑
见ACL
具体配置过程
AR1: (静态NAT)
[AR1]interface GigabitEthernet 4/0/0
[AR1-GigabitEthernet4/0/0]ip address 10.10.10.1 24
[AR1-GigabitEthernet4/0/0]nat static global 10.10.10.2 inside 192.168.2.1
[AR1-GigabitEthernet4/0/0]nat static global 10.10.10.3 inside 192.168.3.1
[AR1-GigabitEthernet4/0/0]quit
AR1: (动态NAT)
[AR1]nat address-group 1 10.10.11.1 10.10.11.3 // 这里不知道能不能将NAT地址池设为10.10.11.0/24,但如果设置成10.10.10.0/24会报错,提示:Error: The address conflicts with interface or ARP IP.
[AR1]acl 2000
[AR1-acl-basic-2000]rule 10 permit source 192.168.2.0 0.0.0.255
[AR1-acl-basic-2000]quit
[AR1]int g4/0/0
[AR1-GigabitEthernet4/0/0]nat outbound 2000 address-group 1 no-pat // 出口转换,“no-pat”,即No-Port Address Translation(非端口地址转换),公有地址与私有地址是1:1映射关系,*** 无法提高公有地址利用率 ***
[AR1-GigabitEthernet4/0/0]quit
AR1: (NAPT)
// 其余与动态ANT相同,只有最后一句去除了no-pat参数
[AR1]nat address-group 1 10.10.11.1 10.10.11.3
[AR1]acl 2000
[AR1-acl-basic-2000]rule 10 permit source 192.168.2.0 0.0.0.255
[AR1-acl-basic-2000]quit
[AR1]int g4/0/0
[AR1-GigabitEthernet4/0/0]nat outbound 2000 address-group 1
[AR1-GigabitEthernet4/0/0]quit
AR1: (Easy IP)
// 其余与NAPT相同,只有最后一句去除了address-group
[AR1]nat address-group 1 10.10.11.1 10.10.11.3
[AR1]acl 2000
[AR1-acl-basic-2000]rule 10 permit source 192.168.2.0 0.0.0.255
[AR1-acl-basic-2000]quit
[AR1]int g4/0/0
[AR1-GigabitEthernet4/0/0]nat outbound 2000
[AR1-GigabitEthernet4/0/0]quit
AR1: (NAT Server)
[AR1]int g4/0/0
[AR1-GigabitEthernet4/0/0] server protocol tcp global 20.20.20.1 www inside 1
92.168.2.1 8081 // 当外网主机访问ip为20.20.20.1的服务器的8081端口的www服务时,路由器会将20.20.20.1映射到内网的192.168.2.1的服务器
验证
无
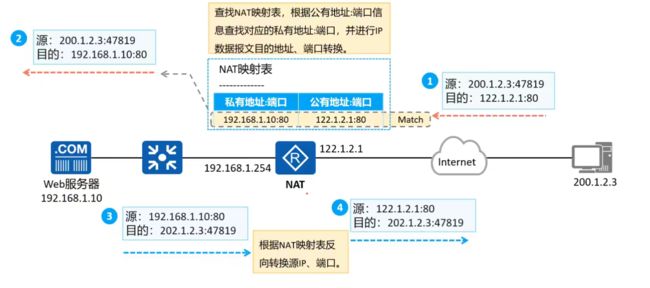
NAPT
案例
目的: 实现公私地址以分配端口的方式转换
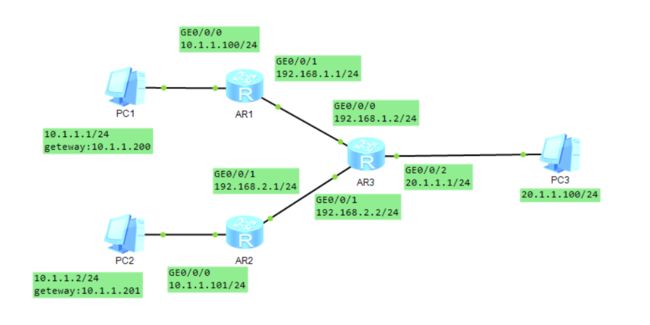
设备概述: 两台PC,在同一子网。一台S5700交换机,三台AR2220路由器。
NAPT原理: 相较于动态NAT,NAPT实现了对私有地址使用相同地址,但是使用不同端口来进行转换,大大提高了公有地址利用率:
拓扑
具体配置过程
PC1:
PC2:
AR1:
<Huawei>system-view
[Huawei]sysname AR1
[AR1]undo info-center enable
[AR1]int g0/0/0
[AR1-GigabitEthernet0/0/0]ip address 192.168.1.254 24
[AR1-GigabitEthernet0/0/0]q
[AR1]int g0/0/1
[AR1-GigabitEthernet0/0/1]ip address 10.10.10.1 24
[AR1-GigabitEthernet0/0/1]q
[AR1]ping 192.168.1.1 // 验证连通性
[AR1]ping 192.168.1.2
[AR1]display ip interface brief // 查看接口配置
[AR1]ip route-static 0.0.0.0 0 10.10.10.2 // 设置静态路由,确保连通
[AR1]acl 2000
[AR1-acl-basic-2000]rule 10 permit source 192.168.1.0 0.0.0.255
[AR1-acl-basic-2000]q
[AR1]nat address-group 1 10.10.10.3 10.10.10.6 // 注意NAT地址池不能以10.10.10.2开始,否则会与AR2的GE0/0/0接口冲突
[AR1]int g0/0/1
[AR1-GigabitEthernet0/0/1]nat outbound 2000 address-group 1
#[AR1-GigabitEthernet0/0/1]undo nat outbound 2000 address-group 1 // 删除nat规则的命令
AR2:
[AR2]int g0/0/0 // 前面基础配置就不放了
[AR2-GigabitEthernet0/0/0]ip address 10.10.10.2 24
[AR2-GigabitEthernet0/0/0]q
[AR2]int g0/0/1
[AR2-GigabitEthernet0/0/1]ip address 10.10.11.1 24
[AR2-GigabitEthernet0/0/1]q
[AR2]ospf 1
[AR2-ospf-1]area 0
[AR2-ospf-1-area-0.0.0.0]network 10.10.10.0 0.0.0.255
[AR2-ospf-1-area-0.0.0.0]network 10.10.11.0 0.0.0.255
[AR2-ospf-1-area-0.0.0.0]q
[AR2-ospf-1]display ip routing-table // 查看ospf状态
[AR2]ip route-static 0.0.0.0 0 10.10.11.2
AR3:
[AR3]int g0/0/0
[AR3-GigabitEthernet0/0/0]ip address 10.10.11.2 24
[AR3-GigabitEthernet0/0/0]q
[AR3]ospf 1
[AR3-ospf-1]area 0
[AR3-ospf-1-area-0.0.0.0]network 10.10.11.0 0.0.0.255
[AR3-ospf-1-area-0.0.0.0]q
[AR3]ip route-static 0.0.0.0 0 10.10.10.1
验证
PC1:
AR1:
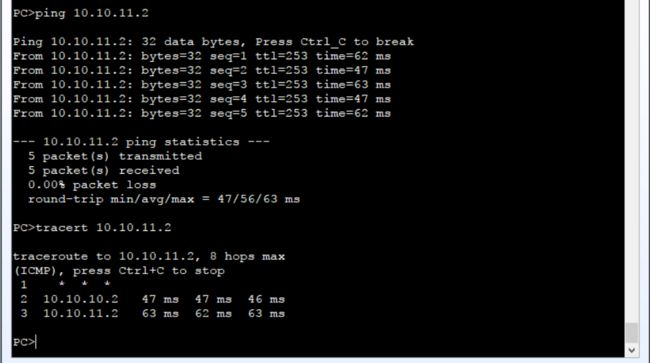
我们让PC1一直ping 10.10.11.2:
PC>ping 10.10.11.2 -t
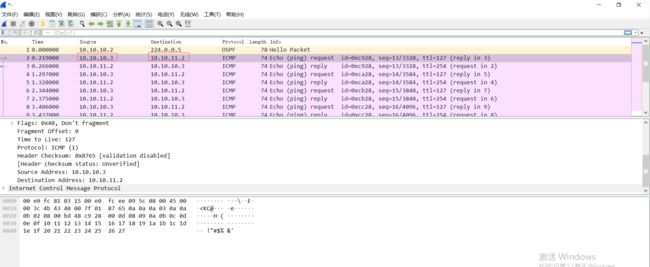
然后在AR1的GE0/0/1接口处抓包:
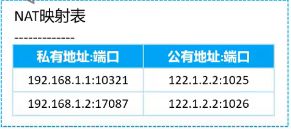
可以看到192.168.1.1的地址在向外发送请求时被NAT转换成了10.10.10.3。
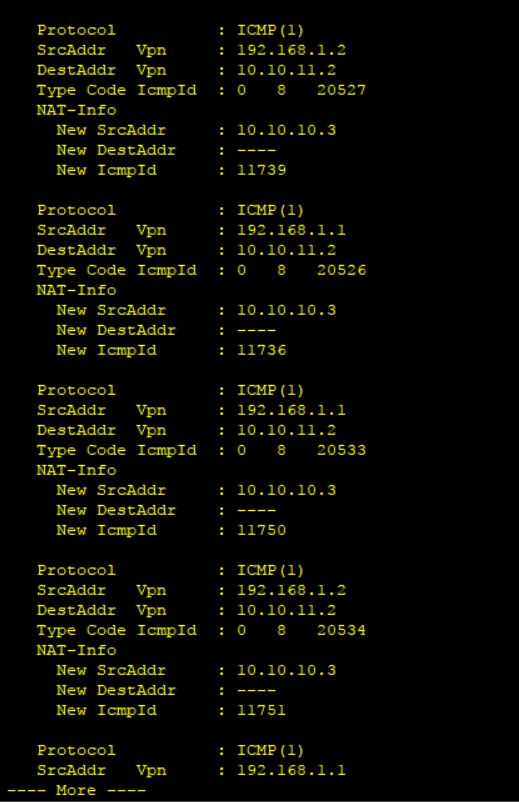
我们再让192.168.1.2同时一起ping 10.10.11.2,在AR1上查看NAT转换情况:
[AR1]display nat session all
VRRP
Virtual Router Redundancy Protocol,虚拟路由冗余协议
案例
目的: 实现PC1和PC2访问虚拟网关,这样网关可以互相备份,实现业务分担。
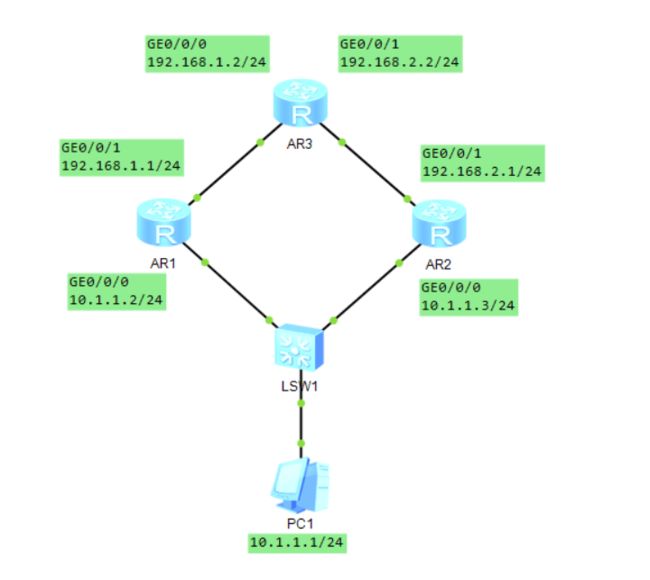
设备概述: 三台PC,三台AR2220。
拓扑
具体配置过程
PC1:
PC2:
PC3:
AR1:
<Huawei>sys
[Huawei]un in en
[Huawei]sysname AR1
[AR1]int g0/0/1
[AR1-GigabitEthernet0/0/1]ip address 192.168.1.1 255.255.255.0
[AR1-GigabitEthernet0/0/1]q
[AR1]int g0/0/0
[AR1-GigabitEthernet0/0/0]ip address 10.1.1.100 255.255.255.0
[AR1-GigabitEthernet0/0/0]vrrp vrid 1 virtual-ip 10.1.1.201
[AR1-GigabitEthernet0/0/0]vrrp vrid 2 virtual-ip 10.1.1.200
[AR1-GigabitEthernet0/0/0]vrrp vrid 1 priority 120 // 配置优先级
[AR1-GigabitEthernet0/0/0]q
[AR1]ospf 1
[AR1-ospf-1]area 0.0.0.0
[AR1-ospf-1-area-0.0.0.0]network 192.168.1.0 0.0.0.255
[AR1-ospf-1-area-0.0.0.0]network 10.1.1.0 0.0.0.255
[AR1-ospf-1-area-0.0.0.0]q
AR2:
[AR2]int g0/0/1
[AR2-GigabitEthernet0/0/1]ip address 192.168.2.1 24
[AR2-GigabitEthernet0/0/1]q
[AR2]int g0/0/0
[AR2-GigabitEthernet0/0/0]ip address 10.1.1.101 24
[AR2-GigabitEthernet0/0/0]vrrp vrid 1 virtual-ip 10.1.1.201
[AR2-GigabitEthernet0/0/0]vrrp vrid 2 virtual-ip 10.1.1.200
[AR2-GigabitEthernet0/0/0]vrrp vrid 2 priority 120
[AR2-GigabitEthernet0/0/0]q
[AR2]ospf 1
[AR2-ospf-1]area 0.0.0.0
[AR2-ospf-1-area-0.0.0.0]network 192.168.2.0 0.0.0.255
[AR2-ospf-1-area-0.0.0.0]network 10.1.1.0 0.0.0.255
[AR2-ospf-1-area-0.0.0.0]q
AR3:
[AR3]int g0/0/0
[AR3-GigabitEthernet0/0/0]ip address 192.168.1.2 24
[AR3-GigabitEthernet0/0/0]q
[AR3]int g0/0/1
[AR3-GigabitEthernet0/0/1]ip address 192.168.2.2 24
[AR3-GigabitEthernet0/0/1]q
[AR3]int g0/0/2
[AR3-GigabitEthernet0/0/2]ip address 20.1.1.1 24
[AR3-GigabitEthernet0/0/2]q
[AR3]ospf 1
[AR3-ospf-1]area 0.0.0.0
[AR3-ospf-1-area-0.0.0.0]network 192.168.1.0 0.0.0.255
[AR3-ospf-1-area-0.0.0.0]network 192.168.2.0 0.0.0.255
[AR3-ospf-1-area-0.0.0.0]network 20.1.1.0 0.0.0.255
[AR3-ospf-1-area-0.0.0.0]q
验证
AR1:
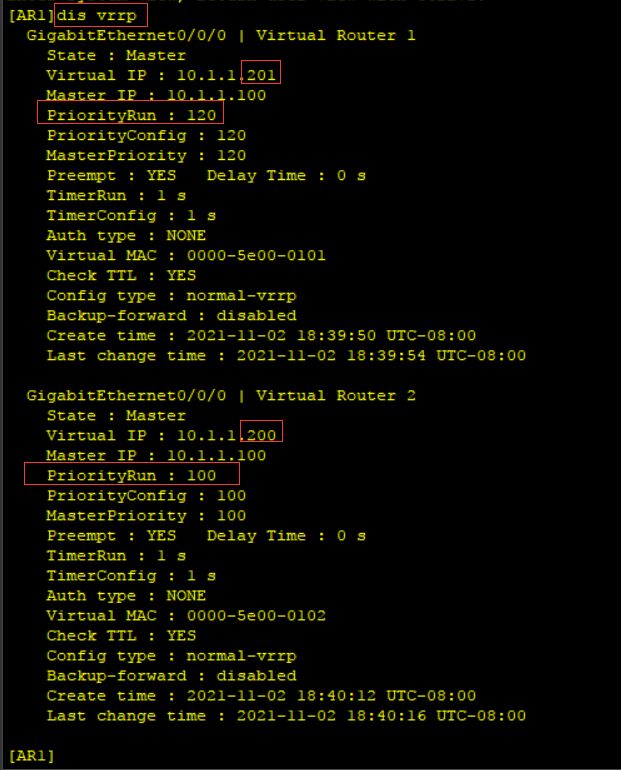
使用display vrrp命令查看:
但不知道为什么我设置了优先级,两个虚拟路由的状态都是Master,而不是一个Master,一个Backup。
PC2:
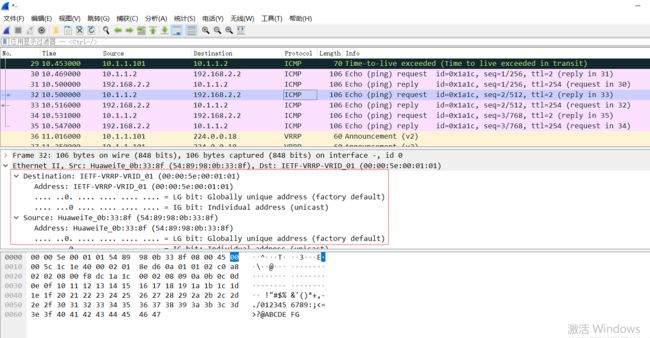
先不停ping 192.168.1.2,然后wireshark抓包
可以发现vrrp不停地向外广播vr声明
我们继续在PC2上
tracert 192.168.2.2
并抓包:
可以看到PC2请求的下一跳mac地址为虚拟路由的虚拟mac地址。
BFD
Bidirectional Forwarding Detection,双向转发检测
案例
先说一下,这个实验参照那本5天软考愣是没弄成功,就权当熟悉命令了(也不影响命令的学习)。该案例是想让BFD与VRRP联动,顺带让OSPF也监听一下BFD。
目的: 在两个路由器间创建 VRRP备份组1,实现链路备份,然后创建BFD会话,快速检测链路故障,实现VRRP快速切换。
设备概述: 一台PC,一台SW5700交换机,三台AR2220路由器。
拓扑
具体配置过程
PC:
AR1:
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]un in en
Info: Information center is disabled.
[Huawei]sysname AR1
[AR1]int g0/0/0
[AR1-GigabitEthernet0/0/0]ip address 10.1.1.2 24
[AR1-GigabitEthernet0/0/0]ospf 1
[AR1-ospf-1]area 0
[AR1-ospf-1-area-0.0.0.0]network 10.1.1.0 0.0.0.255
[AR1-ospf-1-area-0.0.0.0]network 192.168.1.0 0.0.0.255
[AR1-ospf-1-area-0.0.0.0]q
[AR1-ospf-1]int g0/0/1
[AR1-GigabitEthernet0/0/1]ip address 192.168.1.1 24
[AR1-GigabitEthernet0/0/1]q
[AR1]int g0/0/0.1
[AR1-GigabitEthernet0/0/0.1]ip address 10.1.2.1 24 // 这里无法将ip设置到10.1.1.0子网内
[AR1]bfd
[AR1-bfd]q
[AR1]bfd llama bind peer-ip 10.1.1.3 interface GigabitEthernet 0/0/0.1 // 创建BFD会话的绑定信息
[AR1-bfd-session-llama]discriminator local 1 // 配置BFD会话的本地标识符
[AR1-bfd-session-llama]discriminator remote 2 // 配置BFD会话的远端标识符
[AR1-bfd-session-llama]commit
[AR1-bfd-session-llama]q
[AR1]int g0/0/0.1
#[AR1-GigabitEthernet0/0/0.1]dot1q vrrp vid 10 // 发现路由器没有该命令,就用了下面一条,不知道有没有同等效果
[AR1-GigabitEthernet0/0/0.1]dot1q termination vid 10
[AR1-GigabitEthernet0/0/0.1]undo ip address // undo了ip address,不然下一条命令报错提示虚拟ip不在同一子网内,但不知道能不能有效,很慌。。
[AR1-GigabitEthernet0/0/0.1]vrrp vrid 1 virtual 10.1.1.100
[AR1-GigabitEthernet0/0/0.1]vrrp vrid 1 priority 160
[AR1-GigabitEthernet0/0/0.1]vrrp vrid 1 track bfd-session 1 //设置VRRP备份组1监听BFD会话
[AR1-GigabitEthernet0/0/0.1]quit
[AR1]ospf 1
[AR1-ospf-1]bfd all-interfaces enable // OSPF的BFD监听倒是可以实现
[AR1-ospf-1]q
AR2:
[AR2]int g0/0/0
[AR2-GigabitEthernet0/0/0]ip address 10.1.1.3 24
[AR2-GigabitEthernet0/0/0]int g0/0/1
[AR2-GigabitEthernet0/0/1]ip address 192.168.2.1 24
[AR2-GigabitEthernet0/0/1]ospf 1
[AR2-ospf-1]area 0
[AR2-ospf-1-area-0.0.0.0]network 10.1.1.0 0.0.0.255
[AR2-ospf-1-area-0.0.0.0]network 192.168.2.0 0.0.0.255
[AR2-ospf-1-area-0.0.0.0]q
[AR2]int g0/0/0.1
[AR2-GigabitEthernet0/0/0.1]ip address 10.1.2.6 24
[AR2-GigabitEthernet0/0/0.1]q
[AR2]bfd llama bind peer-ip 10.1.1.2 interface GigabitEthernet 0/0/0.1
[AR2-bfd-session-llama]discriminator local 2
[AR2-bfd-session-llama]discriminator remote 1
[AR2-bfd-session-llama]commit
[AR2-bfd-session-llama]q
[AR2]int g0/0/0.1
[AR2-GigabitEthernet0/0/0.1]dot1q termination vid 10
[AR2-GigabitEthernet0/0/0.1]undo ip address
[AR2-GigabitEthernet0/0/0.1]vrrp vrid 1 virtual 10.1.1.100
[AR2-GigabitEthernet0/0/0.1]vrrp vrid 1 track bfd-session 2
[AR2-GigabitEthernet0/0/0.1]q
[AR2]ospf
[AR2-ospf-1]bfd all-interfaces enable
[AR2-ospf-1]q
AR3:
[AR3]bfd
[AR3-bfd]q
[AR3]int g0/0/0
[AR3-GigabitEthernet0/0/0]ip address 192.168.1.2 24
[AR3-GigabitEthernet0/0/0]int g0/0/1
[AR3-GigabitEthernet0/0/1]ip address 192.168.2.2 24
[AR3-GigabitEthernet0/0/1]ospf 1
[AR3-ospf-1]area 0
[AR3-ospf-1-area-0.0.0.0]network 192.168.1.0 0.0.0.255
[AR3-ospf-1-area-0.0.0.0]network 192.168.2.0 0.0.0.255
[AR3-ospf-1-area-0.0.0.0]q
[AR3]ospf
[AR3-ospf-1]bfd all-interfaces enable
[AR3-ospf-1]q
验证:
AR1:
看到BFD会话的状态是ADMINDOWN,VRRP监听BFD起不来也在意料之中,自己也被之前自己通过undo ip address强行让命令执行成功的操作惊到了。。。还望有大佬在评论区能说明一下我的问题所在(是路由器型号问题还是啥?)
AR1:
使用
[AR1]ospf 1
[AR1-ospf-1]bfd all-interfaces enable
[AR1-ospf-1]q
可以使OSPF成功监听BFD:
POE
是一种通过有限以太网给终端设备进行供电的技术。POE的可靠供电距离高达200m
包含供电端设备(Power Sourcing Equipment,PSE)和受电端设备(Power Device,PD)
简单配置
ensp的交换机没有poe的命令,就直接抄了书上的命令,加深一下印象:
[Switch]poe power-management manual // auto/manual
[Switch]poe max-power 216000 slot 1 // 配置1号槽位单板最大对外输出功率:216000mW
[Switch]int e0/0/2
[Switch-Ethernet0/0/2]poe priority high // critical/high/low
[Switch-Ethernet0/0/2]poe power 2000 // 2000mW即2W
[Switch-Ethernet0/0/2]poe legacy enable // 配置对非标准PD设备兼容
[Switch-Ethernet0/0/2]poe power-off time-range xxx // 设置接口下电时间段,xxx为事先定义好的时间按段范围
[Switch]poe power-on interface gigabitethernet 0/0/1 // 手动给GE0/0/1接口上电
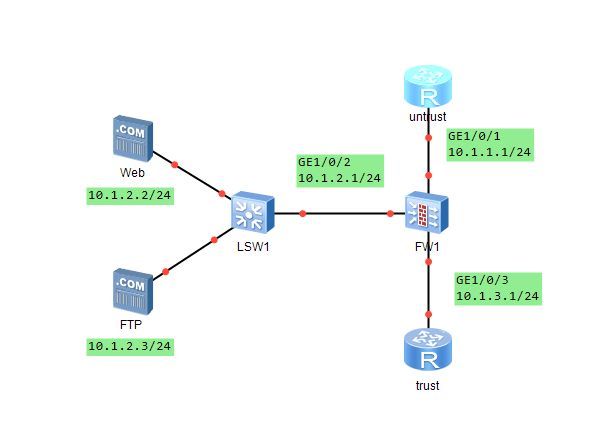
Firewall
资源: USG5500V太老了,没有security-policy命令。 USG6000V 点击链接可以下载:百度网盘链接 提取码:trju ,但我不太清楚这个USG6000V适配哪个版本的ensp,我的ensp上导入后一直无法开启,不停显示“#”。大伙有兴趣的可以试一试。
拓扑
简单配置
// ip 等基础配置略,一个tab符号代表一层(个人习惯)
firewall zone trust // 向区域加入相应接口
add interface GigabitEhternet 1/0/3
quit
firewall zone untrust
add interface GigabitEhternet 1/0/1
q
firewall zone dmz
add interface GigabitEhternet 1/0/2
quit
security-policy // 根据要求创建trust和untrust域间安全策略,允许trust用户访问untrust
rule name policy 1
source zone trust
destination zone untrust
source-address 10.1.3.0 mask 24
destination-address 10.1.1.0 mask 24
action permit
quit
quit
firewall interzone dmz untrust
detect ftp // 配置域间NAT ALG功能,使服务器可以正常对外提供FTP服务
quit
nat server policyweb protocol tcp global 10.1.1.100 80 inside 10.1.1.2 80 no-reverse // 配置内部地址映射到外网地址
nat server policyftp protocol tcp global 10.1.1.100 21 inside 10.1.1.3 21 no-reverse
ip route-static 0.0.0.0 0.0.0.0 10.1.1.2
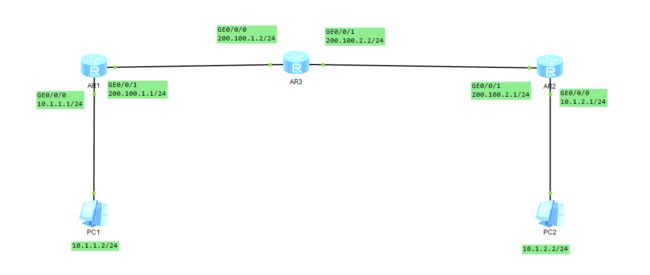
IPSec VPN
PS:一开始配的时候PC1可以连上PC2,再配一次就连不上了,也忘了之前是怎么配的了
拓扑
基本配置
AR1:
[AR1]int g0/0/0
[AR1-GigabitEthernet0/0/0]ip address 10.1.1.1 24
[AR1-GigabitEthernet0/0/0]int g0/0/1
[AR1-GigabitEthernet0/0/1]ip address 200.100.1.1 24
[AR1-GigabitEthernet0/0/1]q
[AR1]acl 3001
[AR1-acl-adv-3001]rule 10 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
[AR1-acl-adv-3001]q
[AR1]acl 3002
[AR1-acl-adv-3002]rule 10 deny ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
[AR1-acl-adv-3002]q
[AR1]ipsec proposal llama1 // 配置IPSec安全协议
[AR1-ipsec-proposal-llama1]esp authentication-algorithm sha2-256
[AR1-ipsec-proposal-llama1]esp encryption-algorithm aes-128
[AR1-ipsec-proposal-llama1]q
[AR1]ike proposal 5 // 配置IKE安全提议
[AR1-ike-proposal-5]encryption-algorithm aes-cbc-128
[AR1-ike-proposal-5]authentication-algorithm sha1
[AR1-ike-proposal-5]dh group14 // 配置DH算法参数
[AR1-ike-proposal-5]q
[AR1]ike peer spuAR2 v2 // 配置IKE对等体
[AR1-ike-peer-spuAR2]ike-proposal 5
[AR1-ike-peer-spuAR2]pre-shared-key cipher Truthahn // 配置预共享密钥为Truthahn
[AR1-ike-peer-spuAR2]remote-address 200.100.2.1
[AR1-ike-peer-spuAR2]q
[AR1]ipsec policy map1 10 isakmp // 配置IKE动态协商方式安全策略
[AR1-ipsec-policy-isakmp-map1-10]ike-peer spuAR2
[AR1-ipsec-policy-isakmp-map1-10]proposal llama1
[AR1-ipsec-policy-isakmp-map1-10]security acl 3001
[AR1-ipsec-policy-isakmp-map1-10]q
[AR1]int g0/0/1
[AR1-GigabitEthernet0/0/1]ipsec policy map1 //引用安全策略组
[AR1-GigabitEthernet0/0/1]nat outbound 3002
[AR1-GigabitEthernet0/0/1]q
[AR1]ip route-s
[AR1]ip route-static 10.1.2.0 255.255.255.0 200.100.2.1
[AR1]ip route-static 200.100.2.0 255.255.255.0 200.100.2.1
AR2:
[AR2]int g0/0/0
[AR2-GigabitEthernet0/0/0]ip address 10.1.2.1 24
[AR2-GigabitEthernet0/0/0]int g0/0/1
[AR2-GigabitEthernet0/0/1]ip address 200.100.2.2 24
[AR2-GigabitEthernet0/0/1]undo ip address
[AR2-GigabitEthernet0/0/1]ip address 200.100.2.1 24
[AR2-GigabitEthernet0/0/1]acl 3001
[AR2-acl-adv-3001]rule 10 permit ip source 10.1.2.0 0.0.0.255 dest
[AR2-acl-adv-3001]rule 10 permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
[AR2-acl-adv-3001]q
[AR2]acl 3002
[AR2-acl-adv-3002]rule 10 deny ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
[AR2-acl-adv-3002]q
[AR2]ipsec proposal llama1
[AR2-ipsec-proposal-llama1]esp authentication-algorithm sha2-256
[AR2-ipsec-proposal-llama1]esp encryption-algorithm aes-128
[AR2-ipsec-proposal-llama1]q
[AR2]ike proposal 5
[AR2-ike-proposal-5]encryption-algorithm aes-cbc-128
[AR2-ike-proposal-5]authentication-algorithm sha1
[AR2-ike-proposal-5]dh group14
[AR2-ike-proposal-5]q
[AR2]ike peer spuAR1 v2
[AR2-ike-peer-spuAR1]ike-proposal 5
[AR2-ike-peer-spuAR1]pre-shared-key cipher Truthahn
[AR2-ike-peer-spuAR1]remote-address 200.100.1.1
[AR2-ike-peer-spuAR1]q
[AR2]ipsec policy use1 10 isakmp
[AR2-ipsec-policy-isakmp-use1-10]ike-peer spuAR1
[AR2-ipsec-policy-isakmp-use1-10]proposal llama1
[AR2-ipsec-policy-isakmp-use1-10]security acl 3001
[AR2-ipsec-policy-isakmp-use1-10]q
[AR2]int g0/0/1
[AR2-GigabitEthernet0/0/1]ipsec policy use1
[AR2-GigabitEthernet0/0/1]nat outbound 3002
[AR2-GigabitEthernet0/0/1]q
[AR2]ip route-static 10.1.1.0 255.255.255.0 200.100.1.1
[AR2]ip route-static 200.100.1.0 255.255.255.0 200.100.1.1
AR3:
[AR3]int g0/0/0
[AR3-GigabitEthernet0/0/0]ip address 200.100.1.2 24
[AR3-GigabitEthernet0/0/0]int g0/0/1
[AR3-GigabitEthernet0/0/1]ip address 200.100.2.2 24
[AR3]ip route-static 10.1.1.0 255.255.255.0 200.100.2.1
[AR3]ip route-static 10.1.2.0 255.255.255.0 200.100.1.1
[AR3]ip route-static 200.100.1.0 255.255.255.0 200.100.2.1
[AR3]ip route-static 200.100.2.0 255.255.255.0 200.100.1.1
结语
网工的配置还挺好玩的
虽然遇到不少ensp的坑,比如win10更新后不兼容virtual box,迫不得已在虚拟机里重装了一遍所有组件2333
参考资料
B站BV号:BV1uK4y1d7JW
《网络工程师5天修炼》第3版