华为IPsce以及GRE over IPSec配置练习
华为IPsce以及GRE over IPSec配置练习
- 一、拓扑以及需求
- 二、配置思路
-
- (1)打通核心层
- (2)利用GRE将PC1、PC2逻辑上连接起来
- (3)需求加密1:加密PC3与PC4的通信数据。
- (4)需求加密2:加密通过GRE隧道的通信数据。
- (5)验证连通性
- 三、完整配置
-
- (1)R1
- (2)R2
- (3)R3
- (4)R4
一、拓扑以及需求
某公司核心网络拓扑如下。其中PC1、PC2为财务部门;PC3、PC4为技术部门。为使数据更加安全,现需要对数据进行加密。
需求加密1:PC3与PC4的通信数据。
需求加密2:通过GRE隧道的通信数据。

主要地址说明:
接口地址:10.0.x,y
x:路由器编号从小到大;y:路由器编号小为1,大为2
PC1:10.1.1.2 网关:10.1.1.1
PC2:10.1.2.2 网关:10.1.2.1
PC3:10.0.3.2 网关:10.0.3.1
PC4:10.0.4.2 网关:10.0.4.1
二、配置思路
(1)打通核心层
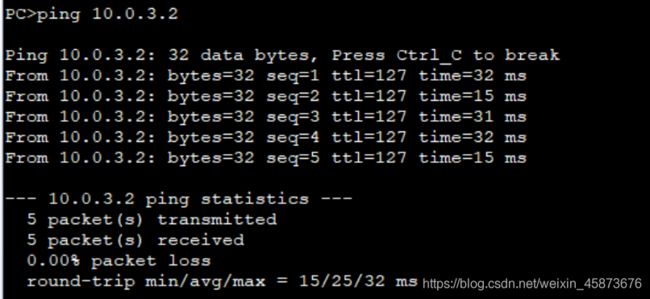
核心层我起了ospf协议,配置这里不多做赘述,有需要可前往华为OSPF配置练习学习。以R2为例,邻居表如下:
(2)利用GRE将PC1、PC2逻辑上连接起来
在R1,R4设备上起GRE三层逻辑通道,简易配置如下:
R1配置:
[r1]interface Tunnel0/0/0
[r1-Tunnel0/0/0]ip address 10.0.14.1 255.255.255.0
[r1-Tunnel0/0/0]tunnel-protocol gre
[r1-Tunnel0/0/0]source 10.0.12.1
[r1-Tunnel0/0/0]destination 10.0.34.2
R4配置:
[r4]interface Tunnel0/0/0
[r4-Tunnel0/0/0]ip address 10.0.14.2 255.255.255.0
[r4-Tunnel0/0/0]tunnel-protocol gre
[r4-Tunnel0/0/0]source 10.0.34.2
[r4-Tunnel0/0/0]destination 10.0.12.1
#
打通以后,我起了rip。
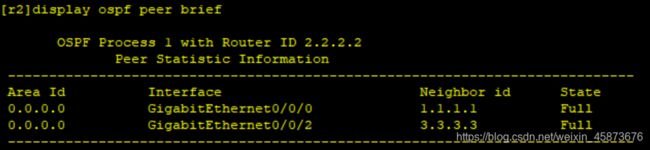
到此,拓扑中PC1-PC2;PC3-PC4均可通信:
PC1-PC2
(3)需求加密1:加密PC3与PC4的通信数据。
此需求我们需要在R2、R3上配置,配置如下:
R2配置:
· 抓取加密流量
[R2]acl 3000
[R2-acl-adv-3000]rule 5 permit ip source 10.0.3.0 0.0.0.255 destination 10.0.4.0 0.0.0.255
· 创建ipsec的安全提议
[R2]ipsec proposal R2
[R2-ipsec-proposal-R2]quit
[R2]display ipsec proposal name R2 //查看proposal一下
· 创建安全策略
[R2]ipsec policy map 10 manual //创建手动安全策略zhpr 10
[R2-ipsec-policy-manual-map-10]security acl 3000 //调用acl
[R2-ipsec-policy-manual-map-10]proposal R2 //调用安全提议
[R2-ipsec-policy-manual-map-10]tunnel local 10.0.23.1 //指定隧道源地址
[R2-ipsec-policy-manual-map-10]tunnel remote 10.0.23.2 //指定隧道目标地址
[R2-ipsec-policy-manual-map-10]sa spi inbound esp 123456 //设置安全联盟的安全索引SPI
[R2-ipsec-policy-manual-map-10]sa string-key inbound esp simple 234567 //设置安全联盟的认证密钥
[R2-ipsec-policy-manual-map-10]sa spi outbound esp 123456
[R2-ipsec-policy-manual-map-10]sa string-key outbound esp simple 234567
· 接口下调用policy策略
[R2]interface GigabitEthernet0/0/2 //公网出口
[R2-GigabitEthernet0/0/2]ipsec policy map
[R2]dis ipsec policy brief //查看ipsec接口信息
注意:
sa spi inbound esp 123456要和对端的outbound保持一致。
sa string-key inbound esp simple 234567要和对端的outbound保持一致。
R3配置与此相似:
R3配置如下:
· 抓取加密流量
[R3]acl 3000
[R3-acl-adv-3000]rule 5 permit ip source 10.0.4.0 0.0.0.255 destination 10.0.3.0 0.0.0.255
· 创建ipsec的安全提议
[R3]ipsec proposal R3
[R3-ipsec-proposal-R3]quit
· 创建安全策略
[R3]ipsec policy map 10 manual
[R3-ipsec-policy-manual-map-10] security acl 3000
[R3-ipsec-policy-manual-map-10] proposal r3
[R3-ipsec-policy-manual-map-10] tunnel local 10.0.23.2
[R3-ipsec-policy-manual-map-10] tunnel remote 10.0.23.1
[R3-ipsec-policy-manual-map-10] sa spi inbound esp 123456
[R3-ipsec-policy-manual-map-10] sa string-key inbound esp simple 234567
[R3-ipsec-policy-manual-map-10] sa spi outbound esp 123456
[R3-ipsec-policy-manual-map-10] sa string-key outbound esp simple 234567
· 接口下调用policy策略
[R3]interface GigabitEthernet0/0/2
[R3-GigabitEthernet0/0/2]ipsec policy map
(4)需求加密2:加密通过GRE隧道的通信数据。
此需求我们需要在R1、R4上配置,配置如下:
R1配置:
· 配置安全提议
[R1]ipsec proposal R1
[R1-ipsec-proposal-tran1]quit
· 配置IKE提议
[R1]ike proposal 5
[R1-ike-proposal-5]encryption-algorithm aes-cbc-128
[R1-ike-proposal-5]authentication-algorithm sha1
[R1-ike-proposal-5]quit
· 配置IKE对等体及其使用协议
[R1]ike peer R1 v2
[R1-ike-peer-R1]pre-shared-key cipher 123456
[R1-ike-peer-R1]ike-proposal 5
[R1-ike-peer-R1]quit
· 配置安全框架
[R1]ipsec profile map
[R1-ipsec-profile-map]ike-peer R1
[R1-ipsec-profile-map]proposal R1
[R1-ipsec-profile-map]quit
· 配置IPSec Tunnel接口
[R1]int tunnel0/0/1
[R1-Tunnel0/0/1]ip address 10.0.0.1 24
[R1-Tunnel0/0/1]tunnel-protocol ipsec
[R1-Tunnel0/0/1]source tunnel0/0/0 //指定Tunnel源接口为GRE Tunnel接口
[R1-Tunnel0/0/1]destination 10.0.14.2 //指定Tunnel的目的地址为GRE Tunnel地址
[R1-Tunnel0/0/1]ipsec profile map
R4配置:
· 配置安全提议
[R4]ipsec proposal R4
[R4-ipsec-proposal-tran1]quit
· 配置IKE提议
[R4]ike proposal 5
[R4-ike-proposal-5]encryption-algorithm aes-cbc-128
[R4-ike-proposal-5]authentication-algorithm sha1
[R4-ike-proposal-5]quit
· 配置IKE对等体及其使用协议
[R4]ike peer R4 v2
[R4-ike-peer-R1]pre-shared-key cipher 123456
[R4-ike-peer-R1]ike-proposal 5
[R4-ike-peer-R1]quit
· 配置安全框架
[R4]ipsec profile map
[R4-ipsec-profile-map]ike-peer R4
[R4-ipsec-profile-map]proposal R4
[R4-ipsec-profile-map]quit
· 配置IPSec Tunnel接口
[R4]int tunnel0/0/1
[R4-Tunnel0/0/1]ip address 10.0.0.1 24
[R4-Tunnel0/0/1]tunnel-protocol ipsec
[R4-Tunnel0/0/1]source tunnel0/0/0 //指定Tunnel源接口为GRE Tunnel接口
[R4-Tunnel0/0/1]destination 10.0.14.1 //指定Tunnel的目的地址为GRE Tunnel地址
[R4-Tunnel0/0/1]ipsec profile map
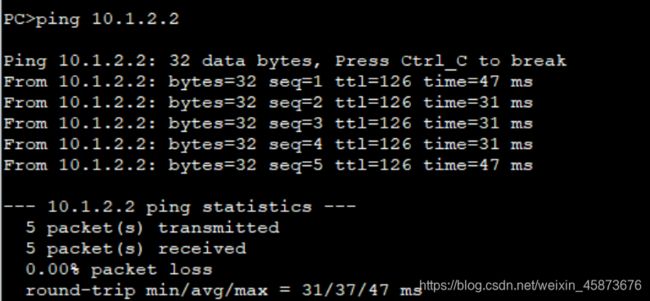
(5)验证连通性
三、完整配置
(1)R1
R1完整配置如下:
[r1]display current-configuration
[V200R003C00]
#
sysname r1
#
ipsec proposal r1
#
ike proposal 5
encryption-algorithm aes-cbc-128
#
ike peer r1 v2
pre-shared-key cipher %$%${"@cGFyLlVmL@4G,4=J.,.2n%$%$
ike-proposal 5
#
ipsec profile map
ike-peer r1
proposal r1
#
interface GigabitEthernet0/0/0
ip address 10.0.12.1 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 10.1.1.1 255.255.255.0
#
interface Tunnel0/0/0
ip address 10.0.14.1 255.255.255.0
tunnel-protocol gre
source 10.0.12.1
destination 10.0.34.2
#
interface Tunnel0/0/1
ip address 10.0.0.1 255.255.255.0
tunnel-protocol ipsec
source Tunnel0/0/0
destination 10.0.14.2
ipsec profile map
#
ospf 1 router-id 1.1.1.1
area 0.0.0.0
network 10.0.12.1 0.0.0.0
#
rip 1
undo summary
version 2
network 10.0.0.0
(2)R2
R2配置如下:
[r2]display current-configuration
[V200R003C00]
#
sysname r2
#
acl number 3000
rule 5 permit ip source 10.0.3.0 0.0.0.255 destination 10.0.4.0 0.0.0.255
#
ipsec proposal r2
#
ipsec policy map 10 manual
security acl 3000
proposal r2
tunnel local 10.0.23.1
tunnel remote 10.0.23.2
sa spi inbound esp 123456
sa string-key inbound esp simple 234567
sa spi outbound esp 123456
sa string-key outbound esp simple 234567
#
interface GigabitEthernet0/0/0
ip address 10.0.12.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 10.0.3.1 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 10.0.23.1 255.255.255.0
ipsec policy map
#
ospf 1 router-id 2.2.2.2
area 0.0.0.0
network 10.0.0.0 0.0.255.255
return
(3)R3
R3配置如下:
[r3]display current-configuration
[V200R003C00]
#
sysname r3
#
acl number 3000
rule 5 permit ip source 10.0.4.0 0.0.0.255 destination 10.0.3.0 0.0.0.255
#
ipsec proposal r3
#
ipsec policy map 10 manual
security acl 3000
proposal r3
tunnel local 10.0.23.2
tunnel remote 10.0.23.1
sa spi inbound esp 123456
sa string-key inbound esp simple 234567
sa spi outbound esp 123456
sa string-key outbound esp simple 234567
#
interface GigabitEthernet0/0/0
ip address 10.0.34.1 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 10.0.4.1 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 10.0.23.2 255.255.255.0
ipsec policy map
#
ospf 1 router-id 3.3.3.3
area 0.0.0.0
network 10.0.0.0 0.0.255.255
(4)R4
R4配置如下:
[r4]display current-configuration
[V200R003C00]
#
sysname r4
#
ipsec proposal r4
#
ike proposal 5
encryption-algorithm aes-cbc-128
#
ike peer r4 v2
pre-shared-key cipher %$%${"@cGFyLlVmL@4G,4=J.,.2n%$%$
ike-proposal 5
#
ipsec profile map
ike-peer r4
proposal r4
#
interface GigabitEthernet0/0/0
ip address 10.0.34.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 10.1.2.1 255.255.255.0
#
interface Tunnel0/0/0
ip address 10.0.14.2 255.255.255.0
tunnel-protocol gre
source 10.0.34.2
destination 10.0.12.1
#
interface Tunnel0/0/1
destination 10.0.14.1
ip address 10.0.0.2 255.255.255.0
tunnel-protocol ipsec
source Tunnel0/0/0
ipsec profile map
#
ospf 1 router-id 4.4.4.4
area 0.0.0.0
network 10.0.34.2 0.0.0.0
#
rip 1
undo summary
version 2
network 10.0.0.0
到此,IPsec与IPsec+GRE配置完成且验证通过。