OpenShift 4 - DevSecOps (4) - 实现一个 CICD Pipeline,并用 RHACS 发现安全隐患(附视频)
《OpenShift 4.x HOL教程汇总》
本文在 OpenShift 4.14 环境中进行验证。
文章目录
- 准备环境
-
- 安装 RHACS 环境
- 安装 Gitea,导入 Git Repository(可选)
- 安装 Codeready Workspace 应用开发环境,导入应用代码(可选)
- 构建并部署测试应用
- 查看 Builder Image 和 App Image 的信息
- 用RHACS发现容器镜像安全漏洞
-
- 用 RHACS 查看可修复的 CVE
- 增加新的 RHACS 安全策略
- 使用低版本 OpenJDK 重新构建应用
- 查看 RHACS 发现镜像的漏洞
- 在 CI/CD Pipeline 中使用 RHACS 扫描镜像
- 阻止不安全的 CI/CD 运行
- 发现并修复应用的 Log4j 漏洞
-
- 在应用中调用 Log4j
- 修复 Log4j 安全漏洞
- 演示视频
- 参考
准备环境
安装 RHACS 环境
- 完成 《OpenShift 4 - DevSecOps (1) - 安装 DevOps 环境》
- 由于名为 Fixable Severity at least Important 的策略比较严格,开启它就无法完成以下操作,所以先在 Platform Configuration 的 Policies 中找到名为 “Fixable Severity at least Important” 的 policy ,然后 Disable Policy。
安装 Gitea,导入 Git Repository(可选)
如果不安装 Gitea,可以在后面的步骤中直接使用 https://github.com/liuxiaoyu-git/quarkus-build-options 作为 Git 源。
- 执行命令向 OpeartorHub注册 Gitea Operator。
$ oc apply -f https://raw.githubusercontent.com/liuxiaoyu-git/gitea-operator/master/catalog_source.yaml
- 在 OpenShift 的 OperatorHub 中找到 Gitea Operator,是有默认配置安装它。
- 执行以下命令,在 git 项目中创建 gitea 实例。
$ oc new-project gitea
$ cat << EOF | oc apply -f -
apiVersion: gpte.opentlc.com/v1
kind: Gitea
metadata:
name: gitea
namespace: gitea
spec:
giteaSsl: true
giteaAdminUser: gitea
giteaAdminPassword: gitea
giteaAdminEmail: opentlc-[email protected]
EOF
- 打开 gitea 项目中名为 gitea 的路由地址,然后用 gitea/gitea 登录。
- 将 https://github.com/liuxiaoyu-git/quarkus-build-options 库导入到 gitea。
安装 Codeready Workspace 应用开发环境,导入应用代码(可选)
- 在 OpenShift 的 OperatorHub 中找到 Codeready Workspaces,然后使用默认配置安装到 openshift-workspaces 项目中。
- 进入 CodeReady Workspaces Operator,然后使用默认配置创建一个“CodeReady Workspaces instance Specification”的实例。创建完可以在开发者视图中的Topology确认部署的资源。
- 打开上图中 CodeReady 的路由,然后提供账户信息。
- 在Create Workspac中进入 Custom Workspace,然后在 devfile URL 中填入以下地址(注意需要使用自己环境的 Gitea 访问地址)。
https:///gitea/quarkus-build-options/raw/branch/master/devfile.yml

构建并部署测试应用
- 创建应用项目。
$ oc new-project workshop-int
-
然后参照下图基于 https://
/gitea/quarkus-build-options 或 https://github.com/liuxiaoyu-git/quarkus-build-options 创建一个 Java 类型的应用。其中 “构建器镜像” 使用 openjdk-11-el7,并选中 “添加管道” 选项。

-
在创建完上述应用资源后会自动启动 Pipeline 运行,并在成功运行后可以访问 workshop-app 对应的路由 URL。

查看 Builder Image 和 App Image 的信息
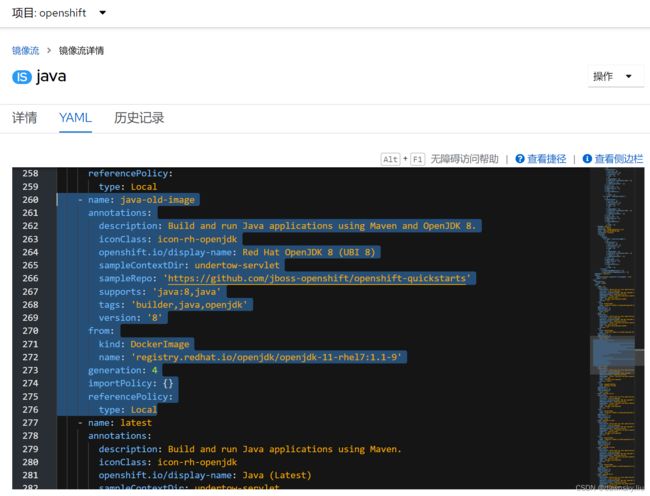
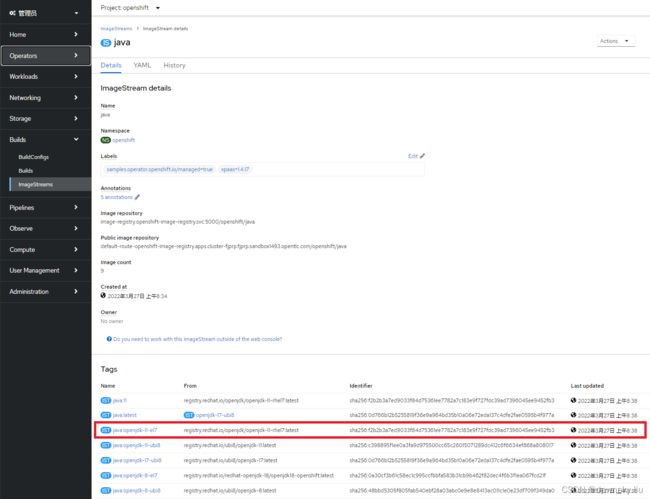
- 在 OpenShift 的管理员视图中进入 Builds 的 ImageStreams 菜单,然后在 openshift 项目中进入名为 Java 的 ImageStream,其中下图名为 “java:openjdk-11-el7” 的 Tag 使用的镜像是“registry.redhat.io/openjdk/openjdk-11-rhel7:latest”。
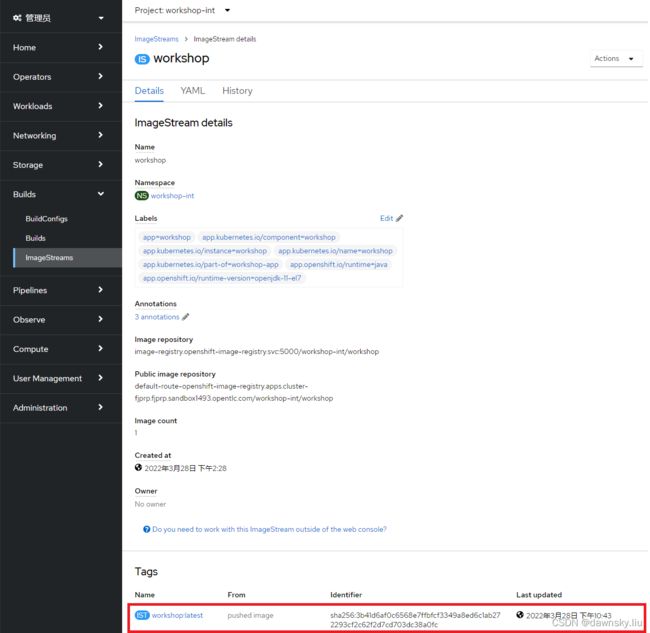
- 然后在 workshop-int 项目中进入名为 workshop 的 ImageStream,该项目是通过 Pipeline 过程把 Builder Image 和 Java 应用包组合构建的应用镜像。
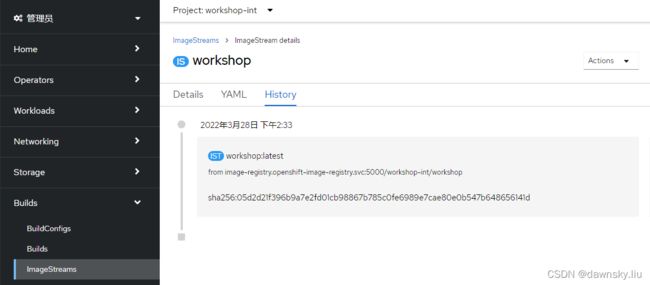
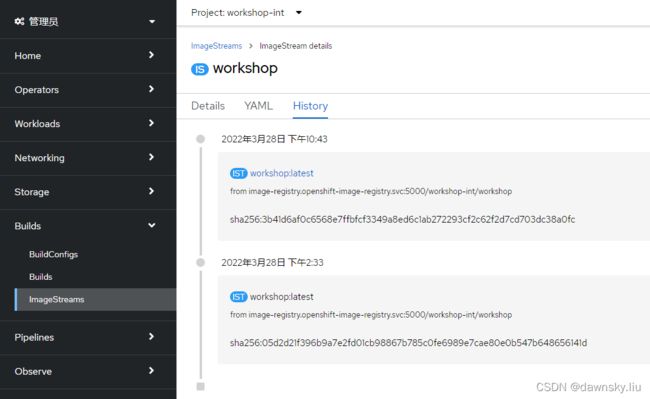
- 查看名为 workshop 的 ImageStream 的 History,可以看到构建 ImageStreamTag 的时间以及对应镜像的 registry 访问地址 “image-registry.openshift-image-registry.svc:5000/workshop-int/workshop”。
注意:sha256:05d2d21f396b9a7e2fd01cb98867b785c0fe6989e7cae80e0b547b648656141d 是该镜像的 Digest。我们在使用一个镜像的时候既可以用 它的 Tag,也可以用它的 Digest。
用RHACS发现容器镜像安全漏洞
用 RHACS 查看可修复的 CVE
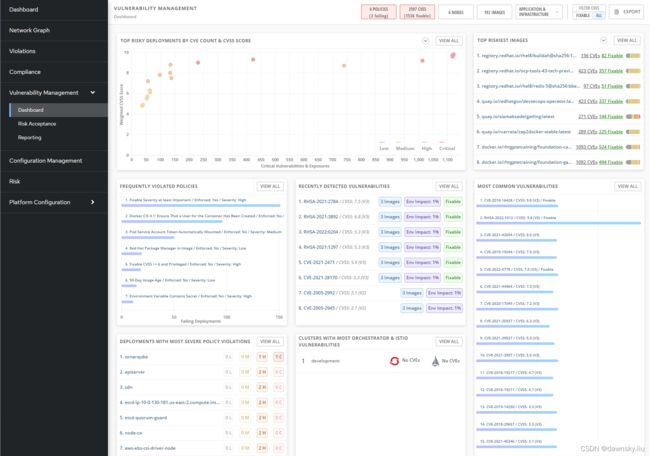
- 在 RHACS 控制台中进入 Vulnerability Management 的 Dashboard,然后在下图的界面中进入 TOP RISK IMAGES 右侧的 VIEW ALL。
- 在 IMAGES 列表中点击下图的 MANAGE WATCHS,会弹出 MANAGE WATCHED IMAGES 窗口。
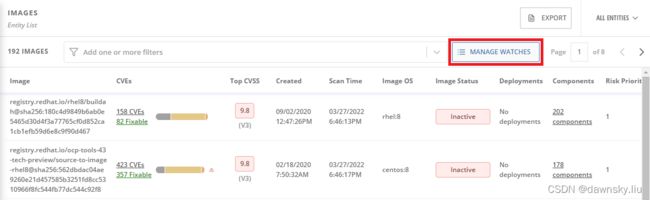
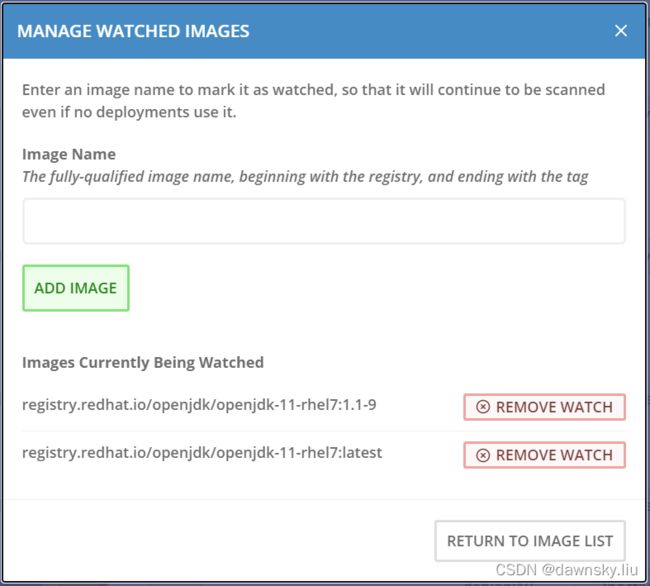
- 将以下两个镜像加入到查看列表中。
registry.redhat.io/openjdk/openjdk-11-rhel7:1.1-9
registry.redhat.io/openjdk/openjdk-11-rhel7:latest
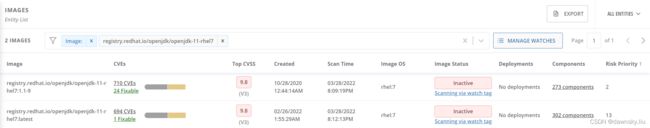
- 返回 IMAGES 页面,按照 Image 查找 “registry.redhat.io/openjdk/openjdk-11-rhel7”,可以看到上面加入的 2 个镜像情况。由于此时这两个镜像都没有直接运行在 OpenShift 中,所以状态都是 “Inactive”。
注意:在写本文的时候 openjdk-11-rhel7:1.1-9 中有 24 个可修复 CVE;而 openjdk-11-rhel7:latest 中只有 1 个可修复的 CVE,不过此时 RedHat 官方还没有提供修复的镜像。
可以查看 openjdk-11-rhel7:latest 镜像的可修复 CVE,当前只是 Moderate级别的。
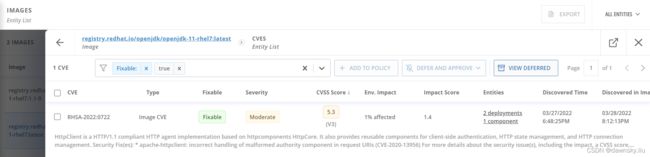
另外还可以查看 openjdk-11-rhel7:1.1-9 的可修复 CVE,其中 “RHSA-2020:4908” 是 Critical 级别的可修复 CVE。
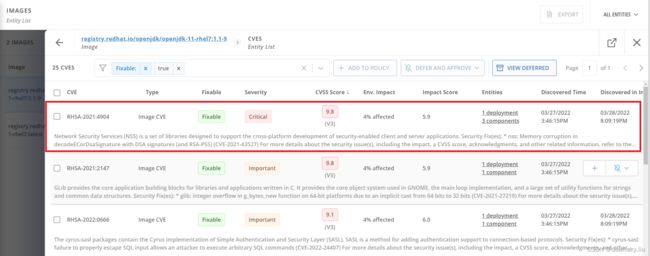
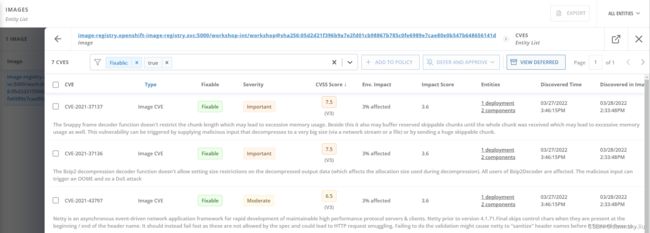
- 在 IMAGES 页面中按照 Image 查找 image-registry.openshift-image-registry.svc:5000/workshop-int/workshop@sha256:05d2d21f396b9a7e2fd01cb98867b785c0fe6989e7cae80e0b547b648656141d,它是前面一节中名为 workshop:latest 的 ImageStream 指向的镜像和 Digest 的组合。因为此时该 App Image 是基于 openjdk-11-rhel7:latest 构建的,所以目前也没有 Critical 级别的 CVE。
增加新的 RHACS 安全策略
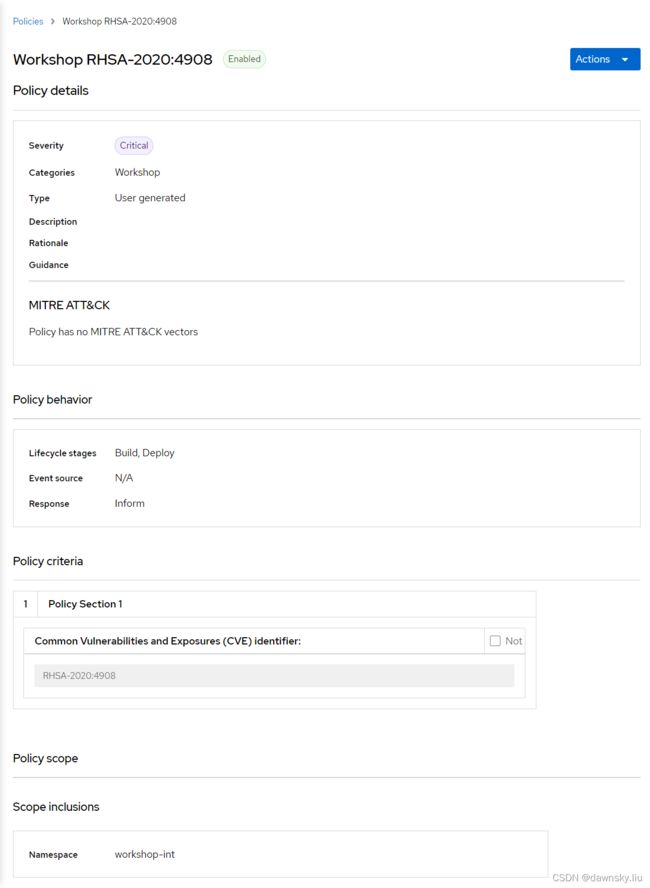
为 RHACS 增加一个新的安全策略,来查找包含漏洞编号为 RHSA-2020:4908 的容器镜像。
- 进入 RHACS 的 Platform Configuration的 Policies 中,然后点击 Create policy 增加一个新的策略,策略基本信息为:
Name:Workshop RHSA-2020:4908
Severity: Critical
Lifecycle Stages: Build, Deploy
Categories: Workshop
其中在 Policy criteria 步骤需要将右侧 Image Contents 的 CVE 拖拽到 Policy Section 1 的 policy field 区域,然后再填入 RHSA-2020:4908
最后保存即可。
使用低版本 OpenJDK 重新构建应用
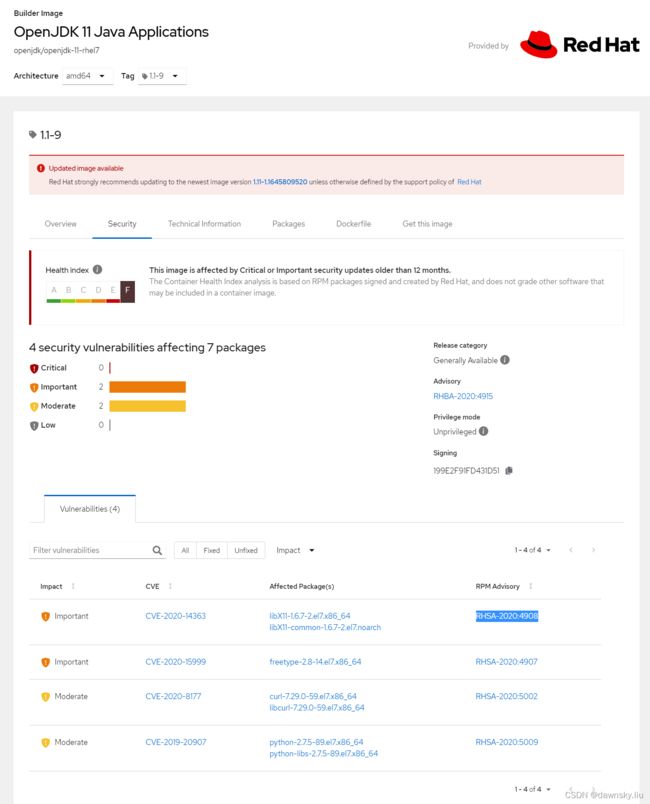
- 访问以下地址,查看 openjdk-11-rhel7:1.1-9 镜像中包含 “RHSA-2020:4908” 的漏洞。
https://catalog.redhat.com/software/containers/openjdk/openjdk-11-rhel7/5bf57185dd19c775cddc4ce5?tag=1.1-9&push_date=1604490183000&container-tabs=security&architecture=amd64
- 将以下内容加到前面 “查看 Builder Image 和 App Image 的信息” 章节第1步的名为 Java 的 ImageStream的 YAML 中。
- name: java-old-image
annotations:
description: Build and run Java applications using Maven and OpenJDK 8.
iconClass: icon-rh-openjdk
openshift.io/display-name: Red Hat OpenJDK 8 (UBI 8)
sampleContextDir: undertow-servlet
sampleRepo: 'https://github.com/jboss-openshift/openshift-quickstarts'
supports: 'java:8,java'
tags: 'builder,java,openjdk'
version: '8'
from:
kind: DockerImage
name: 'registry.redhat.io/openjdk/openjdk-11-rhel7:1.1-9'
generation: 4
importPolicy: {}
referencePolicy:
type: Local
- 使用以下参数再次运行 workshiop-int 项目中名为 workshop 的 Pipeline,其中 VERSION 参数为 “java-old-image”。
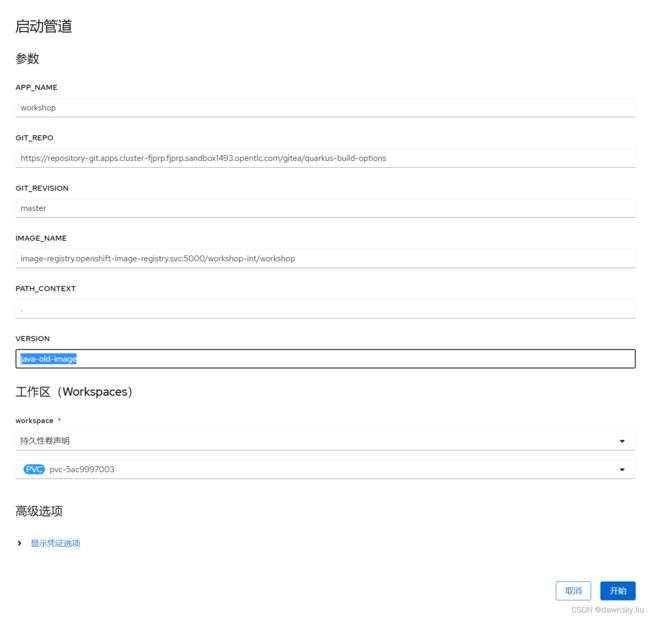
- 在成功运行后可以再次查看名为 workshop 的 ImageStream,在 History 中可以看到已经有新生成的 “workshop:latest” 镜像了。
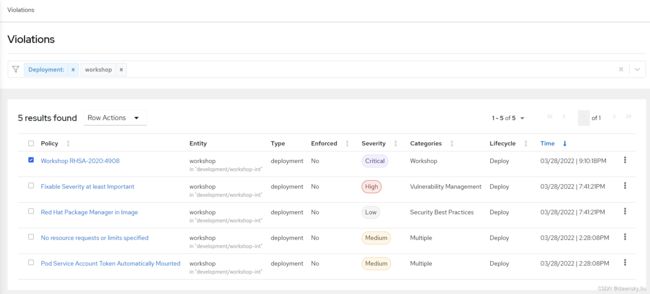
查看 RHACS 发现镜像的漏洞
- 在 RHACS 中的 Violations 中可以看到此时在 workshop 部署中已经违反 “Workshop RHSA-2020:4908” 策略了。
- 进入上面的 “Workshop RHSA-2020:4908” 链接,可以查看违反策略情况。其中在 Deployment 中显示相关镜像,该镜像即为名为 workshop:latest 的 ImageStream 对应的镜像。
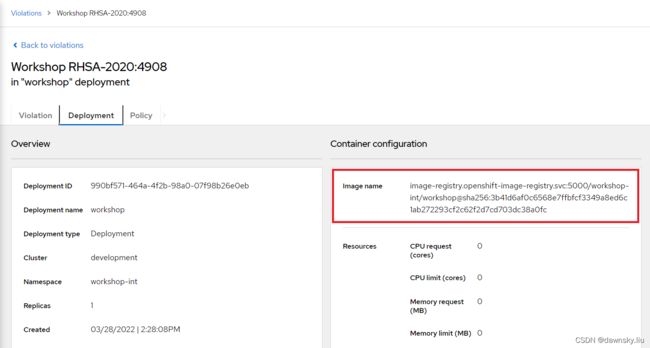
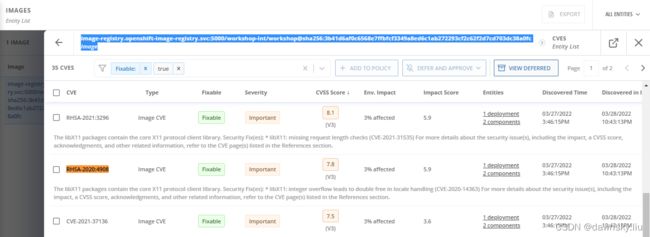
- 还可在 RHACS 中按照以下镜像名称找到该 Image,确认其中包括 RHSA-2020:4908 安全漏洞。
image-registry.openshift-image-registry.svc:5000/workshop-int/workshop@sha256:3b41d6af0c6568e7ffbfcf3349a8ed6c1ab272293cf2c62f2d7cd703dc38a0fc
在 CI/CD Pipeline 中使用 RHACS 扫描镜像
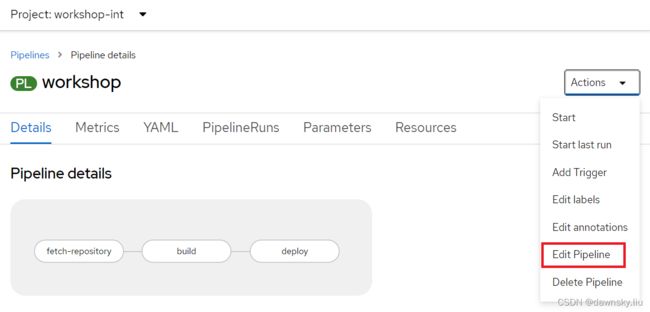
- 在 workshop-int 项目中进入名为 workshop 的 Pipeline。然后点击页面右侧 Actions 的 Edit Pipeline 菜单进入编辑界面。
- 点击 “build” 节点右侧蓝色 “+” 就可以添加一个新的 Task 节点。然后点击新节点的 "Add task”,在弹出窗口中找到名为 rox-imaeg-check、类型为 CT 的任务,最后点击 add 按钮将其加入到 Pipeline。

- 选中新加的 Task 节点,然后按照下图配置输入参数即可,完成后保存。
Display name:rox-image-check
rox_central_endpoint:roxsecrets
rox_api_token:roxsecrets
image:$(params.IMAGE_NAME)
image_digest:$(tasks.build.results.IMAGE_DIGEST)

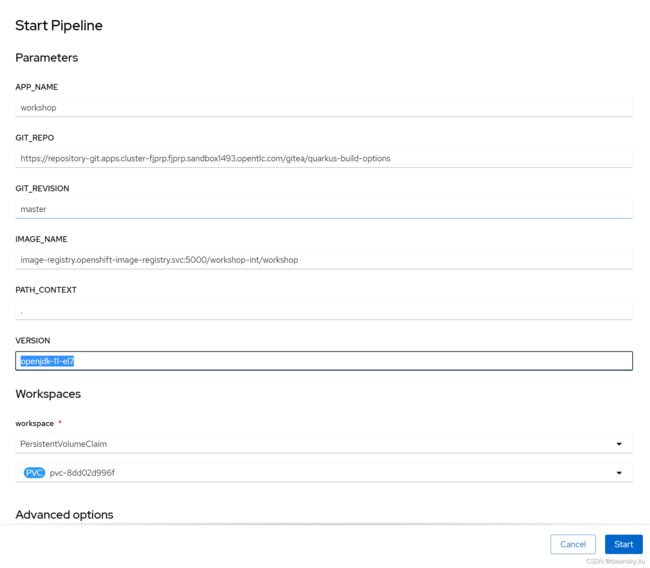
- 点击本节 “步骤1” Action 菜单中的 Start,然后在 Start Pipeline 对话框中确认为 VERSION 参数提供的是 openjdk-11-el7。最后点击 Start 运行名为 workshop 的 Pipeline。
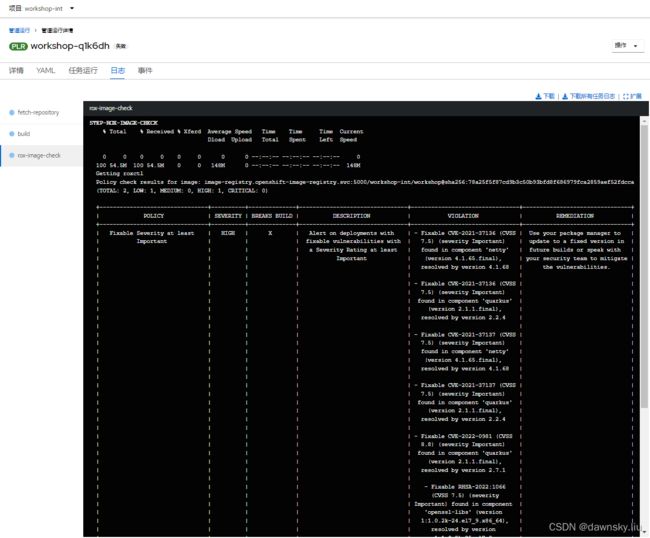
- 运行后可以在 rox-image-check 任务日志中看到以下结果,提示 RHACS 发现构建好的应用镜像有 2 项违规,其中 “Fixable Severity at least Important” 严重程度为 HIGH,所以没有通过镜像检查。另外还检查出构建好的应用镜像中包含 yum、rpm 等程序,认为有安全风险。
STEP-ROX-IMAGE-CHECK
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
31 54.5M 31 17.1M 0 0 117M 0 --:--:-- --:--:-- --:--:-- 116M
100 54.5M 100 54.5M 0 0 142M 0 --:--:-- --:--:-- --:--:-- 142M
Getting roxctl
Policy check results for image: image-registry.openshift-image-registry.svc:5000/workshop-int/workshop@sha256:b4f863396e8d255f996fc1c52b6345c6190984247554dc380ffbaa1cb9ee8d47
(TOTAL: 2, LOW: 1, MEDIUM: 0, HIGH: 1, CRITICAL: 0)
+--------------------------------+----------+--------------+--------------------------------+--------------------------------+--------------------------------+
| POLICY | SEVERITY | BREAKS BUILD | DESCRIPTION | VIOLATION | REMEDIATION |
+--------------------------------+----------+--------------+--------------------------------+--------------------------------+--------------------------------+
| Fixable Severity at least | HIGH | X | Alert on deployments with | - Fixable CVE-2021-37136 (CVSS | Use your package manager to |
| Important | | | fixable vulnerabilities with | 7.5) (severity Important) | update to a fixed version in |
| | | | a Severity Rating at least | found in component 'netty' | future builds or speak with |
| | | | Important | (version 4.1.65.final), | your security team to mitigate |
| | | | | resolved by version 4.1.68 | the vulnerabilities. |
| | | | | | |
| | | | | - Fixable CVE-2021-37136 (CVSS | |
| | | | | 7.5) (severity Important) | |
| | | | | found in component 'quarkus' | |
| | | | | (version 2.1.1.final), | |
| | | | | resolved by version 2.2.4 | |
| | | | | | |
| | | | | - Fixable CVE-2021-37137 (CVSS | |
| | | | | 7.5) (severity Important) | |
| | | | | found in component 'netty' | |
| | | | | (version 4.1.65.final), | |
| | | | | resolved by version 4.1.68 | |
| | | | | | |
| | | | | - Fixable CVE-2021-37137 (CVSS | |
| | | | | 7.5) (severity Important) | |
| | | | | found in component 'quarkus' | |
| | | | | (version 2.1.1.final), | |
| | | | | resolved by version 2.2.4 | |
| | | | | | |
| | | | | - Fixable CVE-2022-0981 (CVSS | |
| | | | | 8.8) (severity Important) | |
| | | | | found in component 'quarkus' | |
| | | | | (version 2.1.1.final), | |
| | | | | resolved by version 2.7.1 | |
| | | | | | |
| | | | | - Fixable RHSA-2022:1066 | |
| | | | | (CVSS 7.5) (severity | |
| | | | | Important) found in component | |
| | | | | 'openssl-libs' (version | |
| | | | | 1:1.0.2k-24.el7_9.x86_64), | |
| | | | | resolved by version | |
| | | | | 1:1.0.2k-25.el7_9 | |
| | | | | | |
| | | | | - Fixable RHSA-2022:1069 (CVSS | |
| | | | | 9.8) (severity Important) | |
| | | | | found in component 'expat' | |
| | | | | (version 2.1.0-12.el7.x86_64), | |
| | | | | resolved by version | |
| | | | | 0:2.1.0-14.el7_9 | |
+--------------------------------+----------+--------------+--------------------------------+--------------------------------+--------------------------------+
| Red Hat Package Manager in | LOW | - | Alert on deployments with | - Image includes | Run `rpm -e --nodeps $(rpm -qa |
| Image | | | components of the Red | component 'rpm' (version | '*rpm*' '*dnf*' '*libsolv*' |
| | | | Hat/Fedora/CentOS package | 4.11.3-48.el7_9.x86_64) | '*hawkey*' 'yum*')` in the |
| | | | management system. | | image build for production |
| | | | | - Image includes | containers. |
| | | | | component 'yum' (version | |
| | | | | 3.4.3-168.el7.noarch) | |
+--------------------------------+----------+--------------+--------------------------------+--------------------------------+--------------------------------+
WARN: A total of 2 policies have been violated
ERROR: failed policies found: 1 policies violated that are failing the check
ERROR: Policy "Fixable Severity at least Important" - Possible remediation: "Use your package manager to update to a fixed version in future builds or speak with your security team to mitigate the vulnerabilities."
ERROR: checking image failed after 3 retries: failed policies found: 1 policies violated that are failing the check
- 下面修复 Red Hat Package Manager in Image 违规。查看名为 workshop 的 Pipeline,进入 s2i-java(build) 任务。
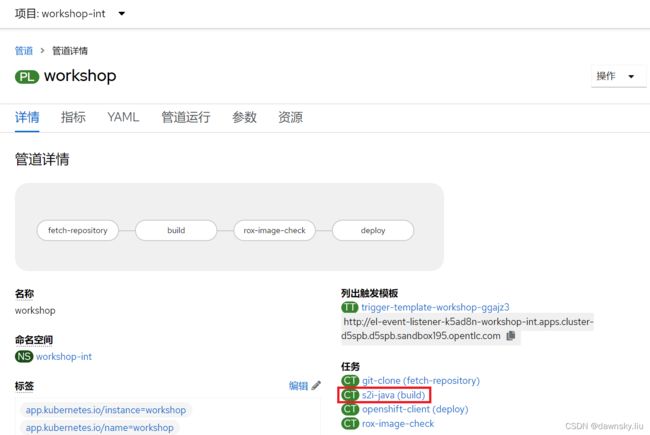
- 可以看到 s2i-java 是 ClusterTask 类型的任务。在 YAML 中编辑 s2i-java 任务,在 spec.steps.name 为 “push” 的区域前添加以下内容。在修复完后可以再次运行 workshop 管道,可以确认已经不再出现 Red Hat Package Manager in Image 违规了。
- args:
- >-
buildah from --storage-driver=vfs --tls-verify=$(params.TLSVERIFY) '$(params.IMAGE):latest' > imgname
buildah run --user=root --storage-driver=vfs `cat imgname` -- sh -c 'rpm -e $(rpm -qa *dnf*) $(rpm -qa *libsolv*) $(rpm -qa *hawkey*) $(rpm -qa yum*) $(rpm -qa *dnf*) $(rpm -qa *subscription-manager*)'
buildah run --user=root --storage-driver=vfs `cat imgname` -- sh -c 'rpm -e $(rpm -qa *rpm*)'
buildah commit --storage-driver=vfs --tls-verify=$(params.TLSVERIFY) `cat imgname` '$(params.IMAGE):latest'
command:
- /bin/sh
- '-c'
image: $(params.BUILDER_IMAGE)
name: remove-package-mgr
resources: {}
volumeMounts:
- mountPath: /var/lib/containers
name: varlibcontainers
- mountPath: /gen-source
name: gen-source
workingDir: /gen-source
- 在 Pipeline 完成运行后,可以查看 rox-image-check 任务的日志。可以看到当使用 openjdk-11-el7 镜像的时候是没有查到安全漏洞。
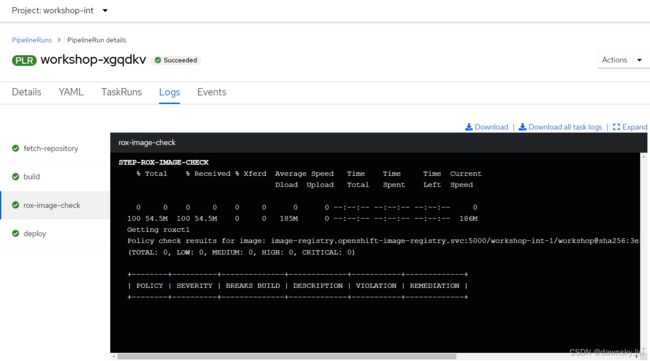
- 再次运行名为 workshop 的 Pipeline,此次为 VERSION 参数提供的是 java-old-image。从运行结果中的 rox-image-check 任务的日志可以看出 RHACS 检查出构建出来的应用镜像包含 RHSA-2020:4908 的安全漏洞。

阻止不安全的 CI/CD 运行
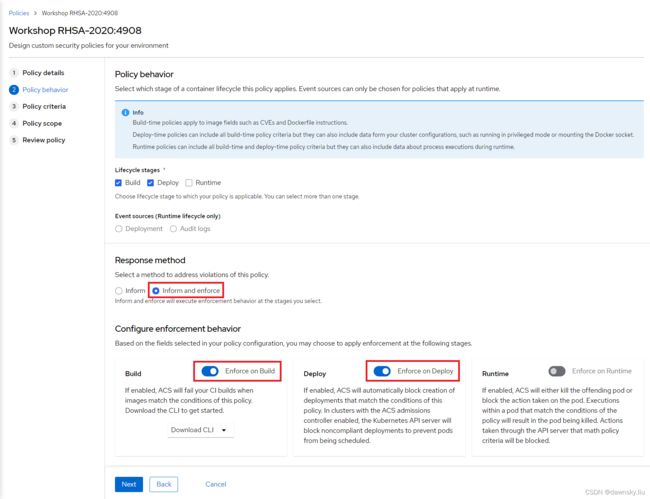
- 在 RHACS 中修改名为 Workshop RHSA-2020:4908 的安全策略。在 Response method 中选择 Inform and enforce,然后打开 Enforce on Build 和 Enforce on Deploy。
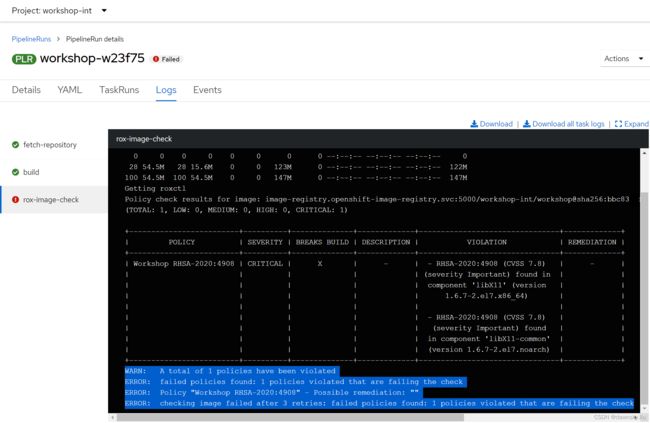
- 再次运行名为 workshop 的 Pipeline,此次为 VERSION 参数提供的是 java-old-image。从运行结果中的 rox-image-check 任务的日志可以看出 RHACS 检查出构建出来的应用镜像包含 RHSA-2020:4908 的安全漏洞,并终止了 CI/CD Pipeline 运行。
发现并修复应用的 Log4j 漏洞
在 RHACS 控制台中进入Platform Configuration中的Policies菜单,确认可以找到名为 Log4Shell 的安全策略。
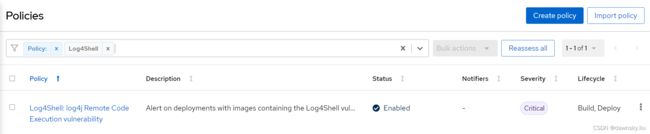
在应用中调用 Log4j
- 修改 quarkus-build-options 仓库中的 pom.xml 文件,在 “” 处增加以下内容。
<dependency>
<groupId>org.apache.logging.log4jgroupId>
<artifactId>log4j-coreartifactId>
<version>2.9.1version>
dependency>
<dependency>
<groupId>org.apache.logging.log4jgroupId>
<artifactId>log4j-apiartifactId>
<version>2.9.1version>
dependency>
- 修改 src/main/java/org/acme/GreetingResource.java 文件为以下内容,其中增加了三行来调用 log4j。
package org.acme;
import javax.ws.rs.GET;
import javax.ws.rs.Path;
import javax.ws.rs.Produces;
import javax.ws.rs.core.MediaType;
// Add import here
import org.apache.logging.log4j.Logger;
import org.apache.logging.log4j.LogManager;
@Path("/hello")
public class GreetingResource {
// Add Logger instantiation here
private Logger logger = LogManager.getLogger(GreetingResource.class.getName());
@GET
@Produces(MediaType.TEXT_PLAIN)
public String hello() {
return "Hello RESTEasy";
}
}
- 重新运行 Pipeline,确认可以看到 Log4Shell 的违规提示。
修复 Log4j 安全漏洞
- 修改 quarkus-build-options 仓库中的 pom.xml 文件,使用更新的 log4j 版本。
<dependency>
<groupId>org.apache.logging.log4jgroupId>
<artifactId>log4j-coreartifactId>
<version>2.17.1version>
dependency>
<dependency>
<groupId>org.apache.logging.log4jgroupId>
<artifactId>log4j-apiartifactId>
<version>2.17.1version>
dependency>
- 再次运行 Pipeline,确认不再有 Log4Shell 的违规提示了。
演示视频
视频
参考
https://devsecops-workshop.github.io/