AWS学习笔记——Chapter5 Identity and Access Management and Security on AWS
前注:
学习书籍
Index
- Identity and Access Management and Security on AWS
-
- 1. Authentication (认证)
- 2. Authorization (授权)
- 3. Auditing (审核)
- 4. Types of security credentials (安全凭证的类型)
- 5. Users
- 6. Groups
- 7. Roles
- 8. IAM Hierarchy of Privileges
- 9. IAM Best Practices
- 10.AWS Compliance Program
- 11.Shared Responsibility Model
-
-
- (1) AWS Responsibility
- (2) Customer’s Responsibility
-
Identity and Access Management and Security on AWS
1. Authentication (认证)
Managing users and their access
Managing federated users and their access
2. Authorization (授权)
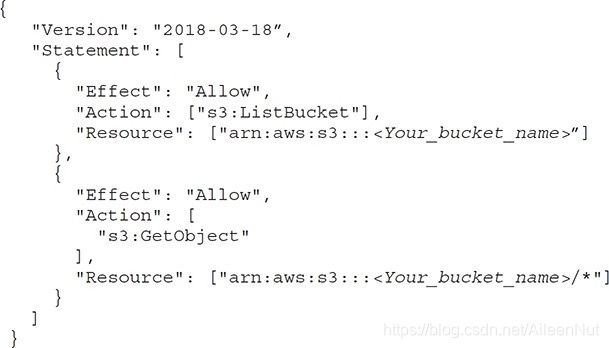
In AWS, authorization is mainly done using IAM policies.
An IAM policy is a piece of code written in JSON where you can define one or more permissions. These permissions define which resources and which actions or operations the IAM entity is allowed.
This policy can be attached to any IAM entity such as a user, group, or role.
You can attach any number of policies to an entity.
A policy can even be attached to multiple entities.
Using a policy, you can either allow or deny access to any resource for any IAM entity, but all permissions are implicitly denied by default.
3. Auditing (审核)
The AWS CloudTrail service records activity made on your account and delivers log files to your Amazon S3 bucket.
CloudTrail can log every API call and related event made.
CloudTrail records important information about each action, including:
· Who made the request?
· When was the request made?
· What was the request about?
· Which resources were acted upon in response to the request?
· Where was the request made from and made to?
4. Types of security credentials (安全凭证的类型)
(1) The security credentials often use:
· IAM username and password
Mainly used for accessing the AWS Management Console.
· E-mail address and password
Associate with your root account.
· Access keys
Often used with the CLI, APIs and SDKs.
· Key pair
Used with Amazon EC2 for logging in to the servers.
· Multifactor authentication (多重身份认证) (MFA)
An additional layer of security that can be used with the root account as well.
(2) Temporary Security Credentials
Temporary Security Credentials are short-term and should never be used for long-term purposes.
Use AWS Security Token Service (AWS STS) to create and pr