MoeCTF2023_Re
文章目录
- MoeCTF2023_Re
-
- 入门指北
- base_64
- UPX!
- Xor
- ANDROID
- EQUATION
- RRRRRc4
MoeCTF2023_Re
入门指北
把
INTRO_RE.exe拖入IDA,F5反编译得到源代码
__int64 __fastcall main()
{
int a; // [rsp+2Ch] [rbp-4h] BYREF
_main();
printf(&_format);
printf("Input the times of appearance of the word \"Reverse\" in the document to continue:\n");
scanf("%d", &a);
if ( a == 13 )
printf("moectf{F1rst_St3p_1s_D0ne}\n");
else
printf("Read carefully!\n");
system("pause");
return 0i64;
}
base_64
pyc反编译把
base_64.pyc反编译得到python代码
#!/usr/bin/env python
# visit https://tool.lu/pyc/ for more information
# Version: Python 3.7
import base64
from string import *
str1 = 'yD9oB3Inv3YAB19YynIuJnUaAGB0um0='
string1 = 'ZYXWVUTSRQPONMLKJIHGFEDCBAzyxwvutsrqponmlkjihgfedcba0123456789+/'
string2 = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
flag = input('welcome to moectf\ninput your flag and I wiil check it:')
enc_flag = base64.b64encode(flag.encode()).decode()
enc_flag = enc_flag.translate(str.maketrans(string2, string1))
if enc_flag == str1:
print('good job!!!!')
else:
print('something wrong???')
exit(0)
import base64
str1 = 'yD9oB3Inv3YAB19YynIuJnUaAGB0um0='
string1 = 'ZYXWVUTSRQPONMLKJIHGFEDCBAzyxwvutsrqponmlkjihgfedcba0123456789+/'
string2 = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
enc_flag=str1.translate(str.maketrans(string1, string2))
flag=base64.b64decode(enc_flag).decode()
print(flag)
UPX!
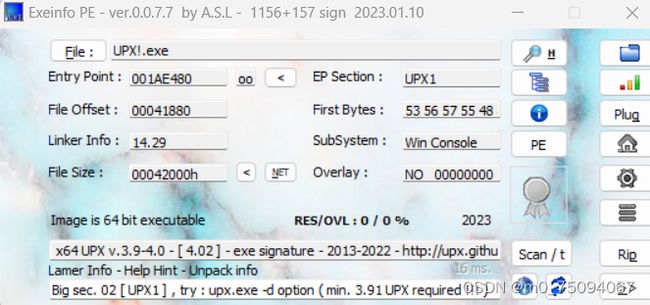
1.UPX!.exe拖入PE发现UPX
UPX 的全称是 “Ultimate Packer for Executables”,它可以将可执行文件中的代码和数据压缩到更小的体积,并在运行时自动解压缩,使程序能够正常执行。
2.利用工具,upx脱壳
D:\Upx\upx-4.1.0-win64>upx -d ../UPX!.exe
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2023
UPX 4.1.0 Markus Oberhumer, Laszlo Molnar & John Reiser Aug 8th 2023
File size Ratio Format Name
-------------------- ------ ----------- -----------
1263104 <- 270336 21.40% win64/pe UPX!.exe
Unpacked 1 file.
enc = [0x0A, 8, 2, 4, 0x13, 1, 0x1C, 'W', 0x0F, '8', 0x1E, 'W', 0x12, '8', ',', 9, 'W', 0x10,'8', '/', 'W', 0x10,'8', 0x13, 8, '8', '5', 2, 0x11, 'T', 0x15,0x14, 2, '8', '2', '7', '?', 'F','F','F', 0x1A]
flag=''
for i in enc:
if isinstance(i, str):
i=ord(i)
flag += chr(i ^ 0x67)
print(flag)
Xor
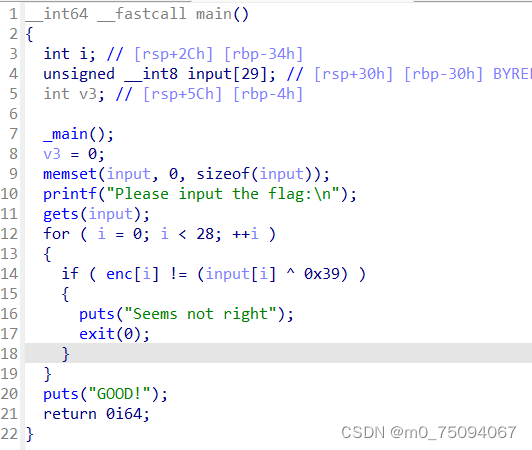
1.拖入IDA,F5得到主函数代码
2.双击数组enc,选取数据shift+e导出,根据a ^ b = c ->c ^ a =b编写脚本
enc = [0x54, 0x56, 0x5C, 0x5A, 0x4D, 0x5F, 0x42, 0x60, 0x56, 0x4C, 0x66, 0x52, 0x57, 0x09, 0x4E, 0x66, 0x51, 0x09, 0x4E, 0x66, 0x4D, 0x09, 0x66, 0x61, 0x09, 0x6B, 0x18, 0x44]
flag=''
for i in enc:
flag += chr(i ^ 0x39)
print(flag)
ANDROID
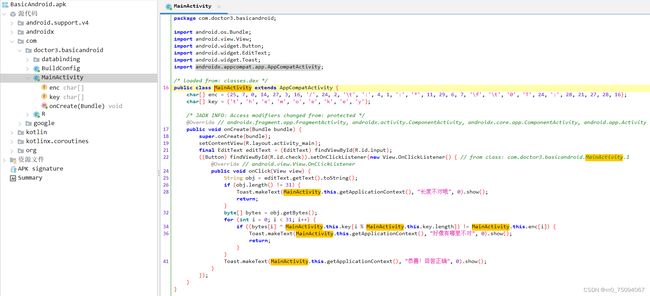
1.把BasicAndroid.apk拖入jadx得到主函数
2.根据xor编写脚本
public class Test {
public static void main(String[] args) {
char[] enc = {
25, 7, 0, 14, 27, 3, 16, '/', 24, 2, '\t', ':', 4, 1, ':', '*', 11, 29, 6, 7, '\f', '\t', '0', 'T', 24, ':', 28, 21, 27, 28, 16};
char[] key = {
't', 'h', 'e', 'm', 'o', 'e', 'k', 'e', 'y'};
for (int i = 0; i < 31; i++) {
int a=(key[i % key.length]) ^ enc[i];
System.out.print((char) a);
}
}
}
//moectf{Java_in_Android_1s_easy}
EQUATION
1.拖入IDA,F5反编译得到主函数代码
发现为31元一次方程组
ctrl+F2选取(char)v5、SBYTE1(v5)、SBYTE2(v5)、SHIBYTE(v5)、(char)v6、SHIBYTE(v6)、v7、!<< 6、
<< 7、<< 8改为v4[24]-v4[30]和=、*64、*128、*256
2.利用z3编写脚本
from z3 import *
v4 = [Int("input[%d]"%i) for i in range(31)]
s = Solver()
s.add(334 * v4[28]
+ 100 * v4[27]
+ 369 * v4[26]
+ 124 * v4[25]
+ 278 * v4[24]
+ 158 * v4[23]
+ 162 * v4[22]
+ 145 * v4[19]
+ 27 * v4[17]
+ 91 * v4[15]
+ 195 * v4[14]
+ 342 * v4[13]
+ 391 * v4[10]
+ 204 * v4[9]
+ 302 * v4[8]
+ 153 * v4[7]
+ 292 * v4[6]
+ 382 * v4[5]
+ 221 * v4[4]
+ 316 * v4[3]
+ 118 * v4[2]
+ 295 * v4[1]
+ 247 * v4[0]
+ 236 * v4[11]
+ 27 * v4[12]
+ 361 * v4[16]
+ 81 * v4[18]
+ 105 * v4[20]
+ 65 * v4[21]
+ 67 * v4[29]
+ 41 * v4[30] == 596119)
s.add(371 * v4[29]
+ 338 * v4[28]
+ 269 * v4[27]
+ 312 * v4[26]
+ 67 * v4[25]
+ 299 * v4[24]
+ 235 * v4[23]
+ 294 * v4[22]
+ 303 * v4[21]
+ 211 * v4[20]
+ 122 * v4[19]
+ 333 * v4[18]
+ 341 * v4[15]
+ 111 * v4[14]
+ 253 * v4[13]
+ 68 * v4[12]
+ 347 * v4[11]
+ 44 * v4[10]
+ 262 * v4[9]
+ 357 * v4[8]
+ 323 * v4[5]
+ 141 * v4[4]
+ 329 * v4[3]
+ 378 * v4[2]
+ 316 * v4[1]
+ 235 * v4[0]
+ 59 * v4[6]
+ 37 * v4[7]
+ 264 * v4[16]
+ 73 * v4[17]
+ 126 * v4[30] == 634009)
s.add(337 * v4[29]
+ 338 * v4[28]
+ 118 * v4[27]
+ 82 * v4[26]
+ 239 * v4[21]
+ 58 * v4[20]
+ 304 * v4[19]
+ 330 * v4[18]
+ 377 * v4[17]
+ 306 * v4[16]
+ 221 * v4[13]
+ 345 * v4[12]
+ 124 * v4[11]
+ 272 * v4[10]
+ 270 * v4[9]
+ 229 * v4[8]
+ 377 * v4[7]
+ 373 * v4[6]
+ 297 * v4[5]
+ 112 * v4[4]
+ 386 * v4[3]
+ 90 * v4[2]
+ 361 * v4[1]
+ 236 * v4[0]
+ 386 * v4[14]
+ 73 * v4[15]
+ 315 * v4[22]
+ 33 * v4[23]
+ 141 * v4[24]
+ 129 * v4[25]
+ 123 * v4[30] == 685705)
s.add(367 * v4[29]
+ 55 * v4[28]
+ 374 * v4[27]
+ 150 * v4[24]
+ 350 * v4[23]
+ 141 * v4[22]
+ 124 * v4[21]
+ 366 * v4[20]
+ 230 * v4[19]
+ 307 * v4[18]
+ 191 * v4[17]
+ 153 * v4[12]
+ 383 * v4[11]
+ 145 * v4[10]
+ 109 * v4[9]
+ 209 * v4[8]
+ 158 * v4[7]
+ 221 * v4[6]
+ 188 * v4[5]
+ 22 * v4[4]
+ 146 * v4[3]
+ 306 * v4[2]
+ 230 * v4[1]
+