加密算法介绍及OpenSSLCA服务
一. 加密算法,协议:
对称加密,公钥加密,单向加密,认证协议
1.)对称加密:使用同一个密钥对数据进行加密,解密。对称加密速度比较快。
常用的对称加密有:DES、IDEA、RC2、RC4、SKIPJACK、RC5、AES等。
2.)公钥加密:生成两个密钥,公开的密钥为公钥,不公开的密钥为私钥。解密数据时需要使用私钥解密。
常用加密算法:RSA, DSA,EIGamal等。
3.)单向加密:加密数据定长输出,不可逆解密。数据变动一点就会导致整个数据损坏。
常见加密算法:MD5,SHA1,SHA256,SHA384,SHA512等。
使用加密计算功能:数据保密性,数据完整性,身份验证。
二. 加密算法通信:
1.)两个主机之间进行通信,发送方首先使用单向加密,获取数据特征码,以保证数据的完整性。使用私钥加密特征码,生成一次性对称密钥,保证数据保密性。使用某种加密算法,对整个数据加密,包含特征码,私钥加密特征码,验证发送者身份。最后用对方主机公钥加密,保证所有数据完整性,保密性。
2.)接收方使用私钥解密公钥,得到对称加密密钥,使用对方公钥解密私钥加密特征码,然后用单向加密获取数据特征码,最后验证数据完整性。
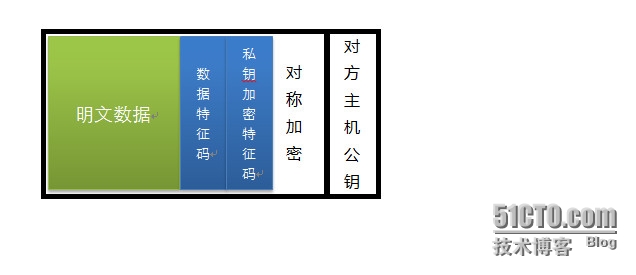
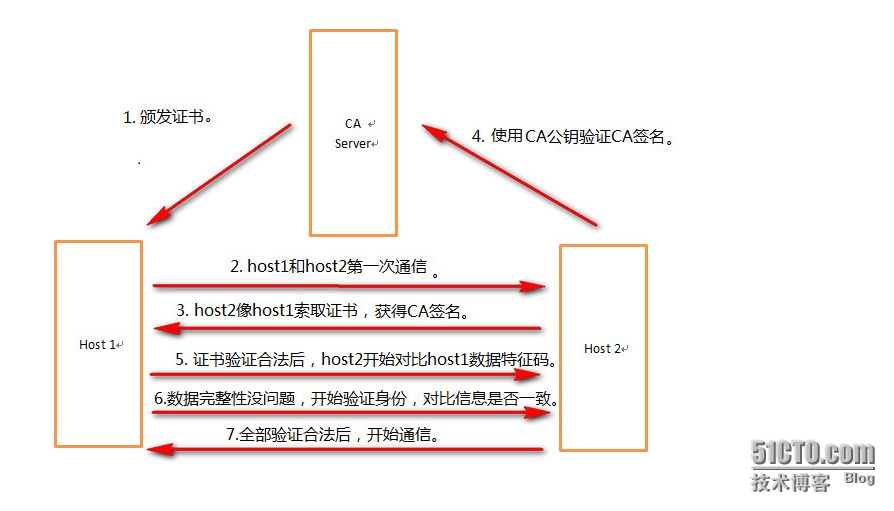
然后通过CA验证。
CA理解:
三.升级OpenSSL
1.)首先升级OpenSSL,由于CentOS6.5上默认安装的版本是openssl-1.0.1e-15.el6。
去官网下载最新版本,openssl-1.0.1h.tar.gz。
2.)解压安装:
# tar -zxf openssl-1.0.1h.tar.gz -C/usr/local/ # cd /usr/local/openssl-1.0.1h/ # ./config shared zlib # make;make install
以上方法安装的会在/usr/local下生成一个ssl目录。
3.)开始替换版本,把老版本的文件和命令修改名字,或者删除。
# mv/usr/bin/openssl /usr/bin/openssl.old.bak # mv/usr/include/openssl/ /usr/include/openssl.old.bak # ln -s/usr/local/ssl/bin/openssl /usr/bin/openssl # ln -s/usr/local/ssl/include/openssl/ /usr/include/openssl/ ln: target`/usr/include/openssl/' is not a directory: No such file or directory #不要加/ # ln -s/usr/local/ssl/include/openssl/ /usr/include/openssl
4.)修改lib搜索路径,绑定。
#echo "/usr/local/ssl/lib" >>/etc/ld.so.conf #ldconfig
5.)查看版本是否更新:
#openssl version -a OpenSSL1.0.1h 5 Jun 2014 builton: Fri Aug 1 15:40:43 CST 2014 platform:linux-x86_64 …… OPENSSLDIR:"/usr/local/ssl"
四.OpenSSL建立CA:
CA路径可以随便建立,但是要修改配置文件中的dir和路径一致,然后还要创建certs crl index.txt newcerts private serial
1.)修改openssl.cnf配置文件
# vimopenssl.cnf dir = /usr/local/ssl/demoCA # Where everything is kept #ls bin CA certs demoCA include lib man misc openssl.cnf private
2.)生成密钥
#cd demoCA/ #(umask 077;openssl genrsa -out private/cakey.pem 2048) GeneratingRSA private key, 2048 bit long modulus ................................................................+++ ..................................+++ eis 65537 (0x10001)
3.)自签证书
命令选项: req: 生成证书签署请求 -news: 新请求 -key/path/to/keyfile: 指定私钥文件 -out/path/to/somefile: -x509: 生成自签署证书 -days n: 有效天数 #openssl req -new -x509 -key private/cakey.pem -out/usr/local/ssl/demoCA/cacert.pem -days 365 Youare about to be asked to enter information that will be incorporated intoyour certificate request. Whatyou are about to enter is what is called a Distinguished Name or a DN. Thereare quite a few fields but you can leave some blank Forsome fields there will be a default value, Ifyou enter '.', the field will be left blank. ----- CountryName (2 letter code) [AU]:CN #国家 Stateor Province Name (full name) [Some-State]:Henan #地区 LocalityName (eg, city) []:ZZ # OrganizationName (eg, company) [Internet Widgits Pty Ltd]:text #公司 OrganizationalUnit Name (eg, section) []:mon #部门 CommonName (e.g. server FQDN or YOUR name) []:Mac #主机名 EmailAddress []: #邮箱 #ls cacert.pem certs crl index.txt newcerts private serial #cat serial 01
4.)节点申请证书:
生成密钥对
# mkdir /usr/local/ssl # cd /usr.local/ssl #(umask 077; openssl genrsa -out /usr/local/ssl/test.key 2048) GeneratingRSA private key, 2048 bit long modulus ....+++ ....+++ eis 65537 (0x10001) #ls test.key
生成证书签署请求
#openssl req -new -key /usr/local/ssl/test.key -out /usr/local/ssl/test.csr Youare about to be asked to enter information that will be incorporated intoyour certificate request. Whatyou are about to enter is what is called a Distinguished Name or a DN. Thereare quite a few fields but you can leave some blank Forsome fields there will be a default value, Ifyou enter '.', the field will be left blank. ----- 此部分要与CA服务器填写一致 CountryName (2 letter code) [XX]:CN Stateor Province Name (full name) []:Henan LocalityName (eg, city) [Default City]:ZZ OrganizationName (eg, company) [Default Company Ltd]:text OrganizationalUnit Name (eg, section) []:mon CommonName (eg, your name or your server's hostname) []:Mac EmailAddress []: Pleaseenter the following 'extra' attributes tobe sent with your certificate request Achallenge password []: #密码部分可以直接回车 Anoptional company name []: #ls test.csr test.key
5.)CA签署证书;
将签署请求发送给CA服务器,我这边是在CA服务器远程复制到本地
#scp 172.16.26.27:/usr/local/ssl/test.csr ./
由于在本地实验过一次签署证书,再次签署的时候报错。
Openssl无法同时建立两个crt。
数据库更新错误
#openssl ca -in /usr/local/ssl/demoCA/client-crt/test.csr -out/usr/local/ssl/demoCA/client-crt/test.crt -days 356 Usingconfiguration from /usr/local/ssl/openssl.cnf Checkthat the request matches the signature Signatureok CertificateDetails: Serial Number: 2 (0x2) Validity Not Before: Aug 2 10:12:44 2014 GMT Not After : Jul 24 10:12:44 2015GMT Subject: countryName = CN stateOrProvinceName = Henan organizationName = text organizationalUnitName = mon commonName = Mac X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 38:54:F5:0E:8A:11:FF:83:52:51:5F:8C:54:2E:29:B3:5D:ED:EB:28 X509v3 Authority Key Identifier: keyid:C6:33:EA:CF:E5:29:D3:AA:56:7F:79:21:D1:3D:99:C4:B1:F4:D9:81 Certificateis to be certified until Jul 24 10:12:44 2015 GMT (356 days) Signthe certificate? [y/n]:y failedto update database TXT_DBerror number 2
删除index.txt索引,然后新touch一个。
#cd ../ #ls cacert.pem certs client-crt crl index.txt index.txt.attr index.txt.old newcerts private serial serial.old #rm -rf index.txt #touch index.txt
重新签署:
#openssl ca -in /usr/local/ssl/demoCA/client-crt/test.csr -out/usr/local/ssl/demoCA/client-crt/test.crt -days 356 Usingconfiguration from /usr/local/ssl/openssl.cnf Checkthat the request matches the signature Signatureok CertificateDetails: Serial Number: 2 (0x2) Validity Not Before: Aug 2 10:13:54 2014 GMT Not After : Jul 24 10:13:54 2015GMT Subject: countryName = CN stateOrProvinceName = Henan organizationName = text organizationalUnitName = mon commonName = Mac X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 38:54:F5:0E:8A:11:FF:83:52:51:5F:8C:54:2E:29:B3:5D:ED:EB:28 X509v3 Authority Key Identifier: keyid:C6:33:EA:CF:E5:29:D3:AA:56:7F:79:21:D1:3D:99:C4:B1:F4:D9:81 Certificateis to be certified until Jul 24 10:13:54 2015 GMT (356 days) Signthe certificate? [y/n]:y 1out of 1 certificate requests certified, commit? [y/n]y Writeout database with 1 new entries DataBase Updated
这回成功了,将证书发送给请求者。
6.)吊销证书:
/usr/local/ssl/demoCA/newcerts # openssl ca -revoke 00.pem Using configuration from /usr/local/ssl/openssl.cnf Revoking Certificate 00. Data Base Updated
更新证书吊销列表
/usr/local/ssl/demoCA/crl #openssl ca -gencrl -out thisca.crl
查看crl文件的内容
# openssl crl -in thisca.crl -noout -text
7.)期间出现了以下问题:Erroropening CA private key ./demoCA/private/cakey.pem
# openssl ca -in /usr/local/client.csr -out /usr/local/client.crt-days 356
Using configuration from /usr/local/ssl/openssl.cnf
Error opening CA private key./demoCA/private/cakey.pem
140486259500712:error:02001002:systemlibrary:fopen:No such file ordirectory:bss_file.c:398:fopen('./demoCA/private/cakey.pem','r')
140486259500712:error:20074002:BIOroutines:FILE_CTRL:system lib:bss_file.c:400:
unable to load CA private key
修改openssl.cnf
[CA_default ] dir = ./ demoCA #修改成要存放密钥的路径,而不是升级后默认的路径。 此路径是/usr/local/ssl/misc #updatedb locateCA.sh /usr/local/openssl-1.0.1h/apps/CA.sh /usr/local/ssl/misc/CA.sh #locate CA.pl /usr/local/openssl-1.0.1h/apps/CA.pl /usr/local/openssl-1.0.1h/apps/CA.pl.bak /usr/local/openssl-1.0.1h/apps/CA.pl.in /usr/local/openssl-1.0.1h/doc/apps/CA.pl.pod /usr/local/ssl/man/man1/CA.pl.1 /usr/local/ssl/misc/CA.pl #./CA.sh �Cnewca #新建立证书
总结:源码包升级openssl时,注意修改配置dir路径,否则会出错。
生成密钥时注意权限问题。
申请证书时,所填写的内容要和CA主机保持一致,不然也会出错。
开始的时候想要卸载自带openssl的rpm包,但是发现依赖关系比较复杂。