Nginx学习(五)SSL相关知识
Nginx服务器 单项认证
1. CA(证书权威机构)的配置
由于是使用openssl架设私有证书中心,因此要保证以下字段在证书中心的证书、服务端证书、客户端证书中都相同
Country Name State or Province Name Locality Name Organization Name Organizational Unit Name
修改CA配置文件
vim /etc/pki/tls/openssl.cnf database = $dir/index.txt certificate = $dir/cacert.crt serial = $dir/serial crlnumber = $dir/crlnumber private_key = $dir/private/cakey.key ....... [ req_distinguished_name ] countryName = Country Name (2 letter code) countryName_default = CHINA ....... localityName = Locality Name (eg, city) localityName_default = BeiJing ....... 0.organizationName = Organization Name (eg, company) 0.organizationName_default = Co-Mall ........ organizationalUnitName = Organizational Unit Name (eg, section) organizationalUnitName_default = PlatForm
生成证书私钥
[root@kaibin pki]# cd /etc/pki/CA/ [root@kaibin CA]# (umask 077;openssl genrsa -out private/cakey.key 2048) Generating RSA private key, 2048 bit long modulus ...............................+++ ......+++ e is 65537 (0x10001) [root@kaibin CA]# touch index.txt [root@kaibin CA]# echo 01 > serial [root@kaibin CA]# echo 01 > crlnumber
生成自签证书
[root@kaibin CA]# openssl req -new -x509 -key private/cakey.key -out cacert.crt -days 3650 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [CN]: State or Province Name (full name) [BJ]: Locality Name (eg, city) [BeiJing]: Organization Name (eg, company) [Co-Mall]: Organizational Unit Name (eg, section) [PlatForm]: Common Name (eg, your name or your server's hostname) []:www.test01.com Email Address []:
2.在web服务器上生成私钥与证书请求文件,并将证书请求文件传给CA
[root@kaibin conf]# mkdir /usr/local/nginx-1.6.2/ssl [root@kaibin conf]# cd /usr/local/nginx-1.6.2/ssl/ #生成私钥文件 [root@kaibin ssl]# (umask 077; openssl genrsa 1024 > nginx.key) Generating RSA private key, 1024 bit long modulus ..................++++++ .......................................................................................++++++ e is 65537 (0x10001) #生成csr请求文件 [root@kaibin ssl]# openssl req -new -key nginx.key -out nginx.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [CN]: State or Province Name (full name) [BJ]: Locality Name (eg, city) [BeiJing]: Organization Name (eg, company) [Co-Mall]: Organizational Unit Name (eg, section) [PlatForm]: Common Name (eg, your name or your server's hostname) []:www.test02.com Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
CA为web服务器的请求文件颁发证书文件,并传给web服务器
[root@kaibin ssl]# cp nginx.csr /etc/pki/CA/ [root@kaibin ssl]# cd /etc/pki/CA/ [root@kaibin CA]# openssl ca -in nginx.csr -out certs/nginx.crt -days 3650 Using configuration from /etc/pki/tls/openssl.cnf Check that the request matches the signature Signature ok Certificate Details: Serial Number: 1 (0x1) Validity Not Before: Jan 8 22:29:57 2015 GMT Not After : Jan 5 22:29:57 2025 GMT Subject: countryName = CN stateOrProvinceName = BJ organizationName = Co-Mall organizationalUnitName = PlatForm commonName = www.test02.com X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 65:2A:83:82:43:A5:60:E5:A7:1A:56:16:6C:FC:AB:C9:FB:76:B5:DB X509v3 Authority Key Identifier: keyid:32:5F:F3:F7:0E:8C:DD:6E:83:08:97:3D:C2:A0:38:EA:1F:2D:D9:35 Certificate is to be certified until Jan 5 22:29:57 2025 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated [root@kaibin certs]# cp nginx.crt /usr/local/nginx-1.6.2/ssl/
修改nginx配置文件
server {
listen 443 ssl;
server_name www.test02.com;
ssl_certificate /usr/local/nginx-1.6.2/ssl/nginx.crt;
ssl_certificate_key /usr/local/nginx-1.6.2/ssl/nginx.key;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
root html;
index index.html index.htm;
}
}
}
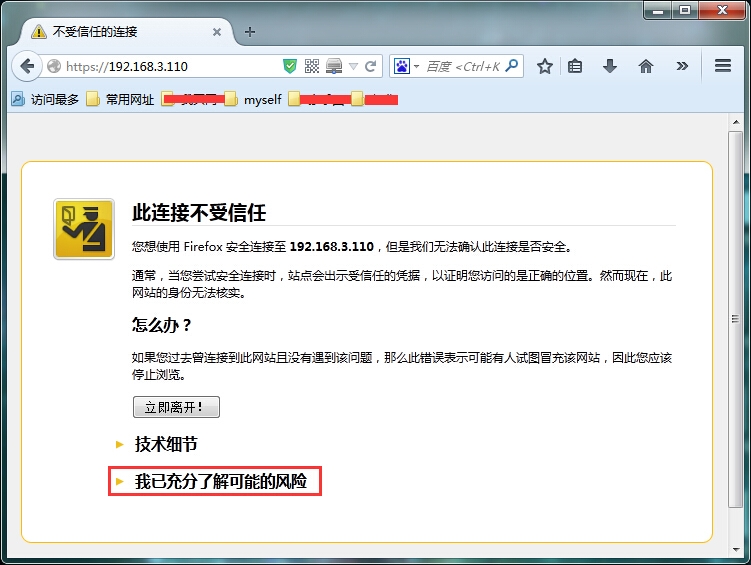
我已充分了解可能的风险-->添加例外-->确认安全例外
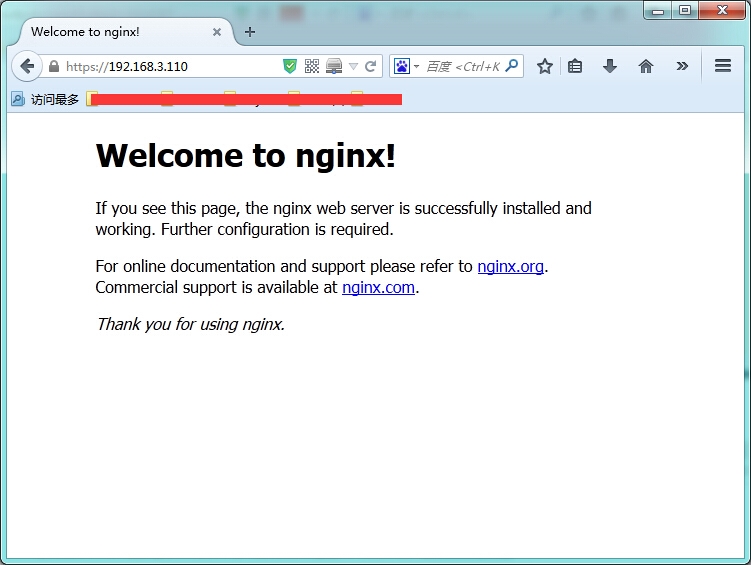
Nginx服务器-客户端 SSL双向认证
在nginx中建立CA目录
[root@kaibin nginx-1.6.2]# mkdir /usr/local/nginx-1.6.2/CA
[root@kaibin nginx-1.6.2]# mkdir /usr/local/nginx-1.6.2/CA/{newcerts,private,conf,server}
newcerts子目录将存放CA签署(颁发)过的数字证书(证书备份目录).
private目录用于存放CA的私钥.
conf目录只是用于存放一些简化参数用的配置文件.
server目录存放服务器证书文件.
[root@kaibin nginx-1.6.2]# tree CA -L 2 CA ├── conf │ └── openssl.conf ├── index.txt ├── index.txt.attr ├── index.txt.old ├── newcerts │ └── FACE.pem ├── private │ ├── ca.crl │ ├── ca.crt │ ├── ca.csr │ └── ca.key ├── serial ├── serial.old └── server ├── server.crt ├── server.csr └── server.key
1. 在conf目录中创建openssl.conf配置文件
[root@kaibin nginx-1.6.2]# vim /usr/local/nginx-1.6.2/CA/conf/openssl.conf [ ca ] default_ca = foo # The default ca section [ foo ] dir = /usr/local/nginx-1.6.2/CA # top dir database = /usr/local/nginx-1.6.2/CA/index.txt # index file. new_certs_dir = /usr/local/nginx-1.6.2/CA/newcerts # new certs dir certificate = /usr/local/nginx-1.6.2/CA/private/ca.crt # The CA cert serial = /usr/local/nginx-1.6.2/CA/serial # serial no file private_key = /usr/local/nginx-1.6.2/CA/private/ca.key # CA private key RANDFILE = /usr/local/nginx-1.6.2/CA/private/.rand # random number file default_days = 365 # how long to certify for default_crl_days= 30 # how long before next CRL default_md = md5 # message digest method to use unique_subject = no # Set to 'no' to allow creation of # several ctificates with same subject. policy = policy_any # default policy [ policy_any ] countryName = match stateOrProvinceName = match organizationName = match organizationalUnitName = match localityName = optional commonName = supplied emailAddress = optional
注:你也可以直接修改openssl的配置文件,这样的话后面制作证书的代码中就不用引用这个配置文件了。
2.创建服务器私有CA
#生成私钥 [root@kaibin CA]# openssl genrsa -out private/ca.key Generating RSA private key, 1024 bit long modulus ...++++++ ........++++++ e is 65537 (0x10001) #根据私钥生成csr请求文件 [root@kaibin CA]# openssl req -new -key private/ca.key -out private/ca.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [CN]: State or Province Name (full name) [BJ]: Locality Name (eg, city) [BeiJing]: Organization Name (eg, company) [Co-Mall]: Organizational Unit Name (eg, section) [PlatForm]: Common Name (eg, your name or your server's hostname) []:www.test02.com Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: #为自己签发证书 [root@kaibin CA]# openssl x509 -req -days 365 -in private/ca.csr -signkey private/ca.key -out private/ca.crt Signature ok subject=/C=CN/ST=BJ/L=BeiJing/O=Co-Mall/OU=PlatForm/CN=www.test02.com Getting Private key [root@kaibin CA]# echo FACE > serial [root@kaibin CA]# touch index.txt [root@kaibin CA]# openssl ca -gencrl -out /usr/local/nginx-1.6.2/CA/private/ca.crl -crldays 7 -config "/usr/local/nginx-1.6.2/CA/openssl.conf" Using configuration from /usr/local/nginx-1.6.2/CA/openssl.conf
3.为私有服务器签发证书
#服务器生成私钥 [root@kaibin CA]# openssl genrsa -out server/server.key Generating RSA private key, 1024 bit long modulus ..........................................................++++++ ...................++++++ e is 65537 (0x10001) #生成csr请求文件 [root@kaibin CA]# openssl req -new -key server/server.key -out server/server.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [CN]: State or Province Name (full name) [BJ]: Locality Name (eg, city) [BeiJing]: Organization Name (eg, company) [Co-Mall]: Organizational Unit Name (eg, section) [PlatForm]: Common Name (eg, your name or your server's hostname) []:www.test02.com Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: #私有CA为服务器签发证书 [root@kaibin CA]# openssl ca -in server/server.csr -cert private/ca.crt -keyfile private/ca.key -out server/server.crt -config "/usr/local/nginx-1.6.2/CA/openssl.conf" Using configuration from /usr/local/nginx-1.6.2/CA/openssl.conf Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows countryName :PRINTABLE:'CN' stateOrProvinceName :ASN.1 12:'BJ' localityName :ASN.1 12:'BeiJing' organizationName :ASN.1 12:'Co-Mall' organizationalUnitName:ASN.1 12:'PlatForm' commonName :ASN.1 12:'www.test02.com' Certificate is to be certified until Jan 9 00:32:31 2016 GMT (365 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated
4.修改nginx配置文件并重启
[root@kaibin sbin]# vim /usr/local/nginx-1.6.2/conf/nginx.conf
server {
listen 443 ssl;
server_name www.test02.com;
ssl_certificate /usr/local/nginx-1.6.2/CA/server/server.crt;
ssl_certificate_key /usr/local/nginx-1.6.2/CA/server/server.key;
ssl_client_certificate /usr/local/nginx-1.6.2/CA/private/ca.crt;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_verify_client on; #开户客户端证书验证
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
root html;
index index.html index.htm;
}
[root@kaibin sbin]# ../sbin/nginx -t
nginx: the configuration file /usr/local/nginx-1.6.2/conf/nginx.conf syntax is ok
nginx: configuration file /usr/local/nginx-1.6.2/conf/nginx.conf test is successful
[root@kaibin sbin]# ../sbin/nginx -s reload
#为这个虚拟机指定PEM格式的证书,这个文件可以包含其他的证书和服务器私钥,秘钥也必须是PEM格式 ssl_certificate /usr/local/nginx-1.6.2/CA/server/server.crt; #为这个虚拟机指定PEM格式的私钥文件. ssl_certificate_key /usr/local/nginx-1.6.2/CA/server/server.key; #指出包含PEM格式的CA(root)证书,用于检查客户端证书. ssl_client_certificate /usr/local/nginx-1.6.2/CA/private/ca.crt; #设置存储SSL会话的存储类型和大小 ssl_session_cache shared:SSL:1m; 语法:ssl_session_cache off|none|builtin:size and/or shared:name:size 缓存类型为: off - 强制关闭:nginx告诉客户端这个会话已经不能被再次使用。 none - 非强制关闭:nginx告诉客户端这个会话可以被再次使用,但是nginx实际上并不使用它们,这是为某些使用ssl_session_cache的邮件客户端提供的一种变通方案,可以使用在邮件代理和HTTP服务器中。 builtin - 内建OpenSSL缓存,仅能用在一个工作进程中,缓存大小在会话总数中指定,注意:如果要使用这个类型可能会引起内存碎片问题,具体请查看下文中参考文档。 shared - 缓存在所有的工作进程中共享,缓存大小指定单位为字节,1MB缓存大概保存4000个会话,每个共享的缓存必须有自己的名称,相同名称的缓存可以使用在不同的虚拟主机中。 #设置客户端能够反复使用缓存中的会话参数时间 ssl_session_timeout 5m; #指出为建立安全连接,服务器所允许的密码格式列表,密码指定为OpenSSL支持的格式, ssl_ciphers HIGH:!aNULL:!MD5; #依赖SSLv3和TLSv1协议的服务器密码将优先于客户端密码。 ssl_prefer_server_ciphers on;
启动nginx ,等待客户连接,如果此时连接服务器,将提示400 Bad request certification的错误,故还需要生成客户端证书。
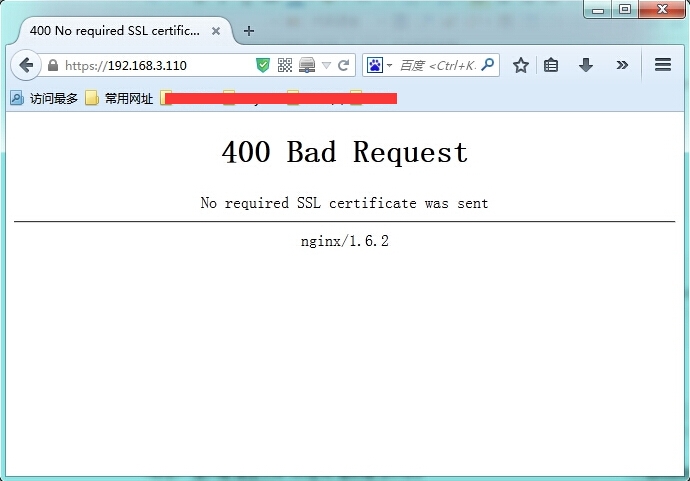
5.生成客户端证书
#生成客户端私钥 [root@kaibin sbin]# openssl genrsa -des3 -out /usr/local/nginx-1.6.2/CA/users/client.key 1024 Generating RSA private key, 1024 bit long modulus .......++++++ ...++++++ e is 65537 (0x10001) Enter pass phrase for /usr/local/nginx-1.6.2/CA/users/client.key: 139912546289480:error:28069065:lib(40):UI_set_result:result too small:ui_lib.c:869:You must type in 4 to 8191 characters Verifying - Enter pass phrase for /usr/local/nginx-1.6.2/CA/users/client.key: #生成客户端csr请求文件 [root@kaibin sbin]# openssl req -new -key /usr/local/nginx-1.6.2/CA/users/client.key -out /usr/local/nginx-1.6.2/CA/users/client.csr Enter pass phrase for /usr/local/nginx-1.6.2/CA/users/client.key: You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [CN]: State or Province Name (full name) [BJ]: Locality Name (eg, city) [BeiJing]: Organization Name (eg, company) [Co-Mall]: Organizational Unit Name (eg, section) [PlatForm]: Common Name (eg, your name or your server's hostname) []:www.test02.com Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: #私有CA为客户端签发证书 [root@kaibin sbin]# openssl ca -in /usr/local/nginx-1.6.2/CA/users/client.csr -cert /usr/local/nginx-1.6.2/CA/private/ca.crt -keyfile /usr/local/nginx-1.6.2/CA/private/ca.key -out /usr/local/nginx-1.6.2/CA/users/client.crt -config "/usr/local/nginx-1.6.2/CA/openssl.conf" Using configuration from /usr/local/nginx-1.6.2/CA/openssl.conf Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows countryName :PRINTABLE:'CN' stateOrProvinceName :ASN.1 12:'BJ' localityName :ASN.1 12:'BeiJing' organizationName :ASN.1 12:'Co-Mall' organizationalUnitName:ASN.1 12:'PlatForm' commonName :ASN.1 12:'www.test02.com' Certificate is to be certified until Jan 9 02:06:05 2016 GMT (365 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated #将文本格式的证书转换成可以导入浏览器的证书 [root@kaibin sbin]# openssl pkcs12 -export -clcerts -in /usr/local/nginx-1.6.2/CA/users/client.crt -inkey /usr/local/nginx-1.6.2/CA/users/client.key -out /usr/local/nginx-1.6.2/CA/users/client.p12 Enter pass phrase for /usr/local/nginx-1.6.2/CA/users/client.key: Enter Export Password: Verifying - Enter Export Password:
6.将证书导入到浏览器

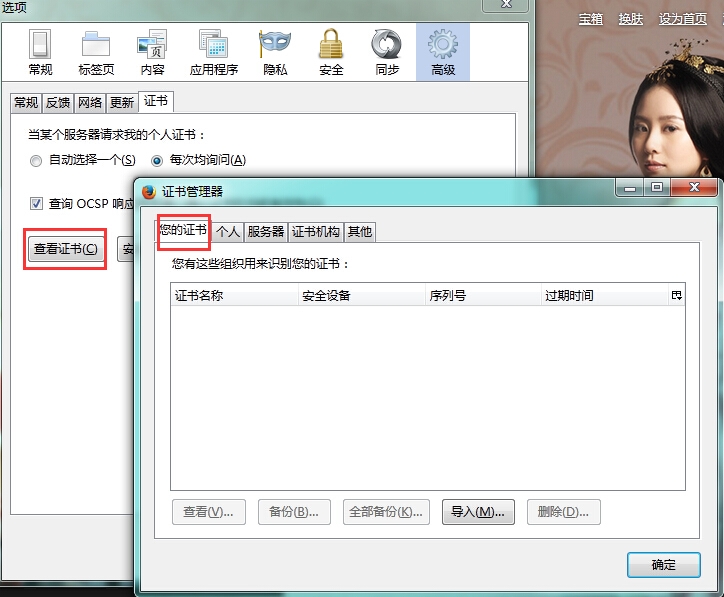
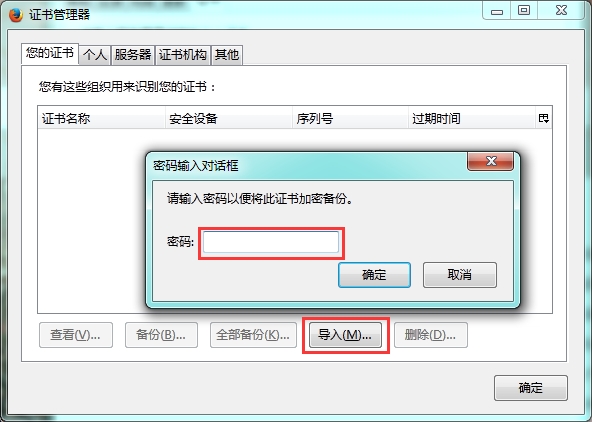
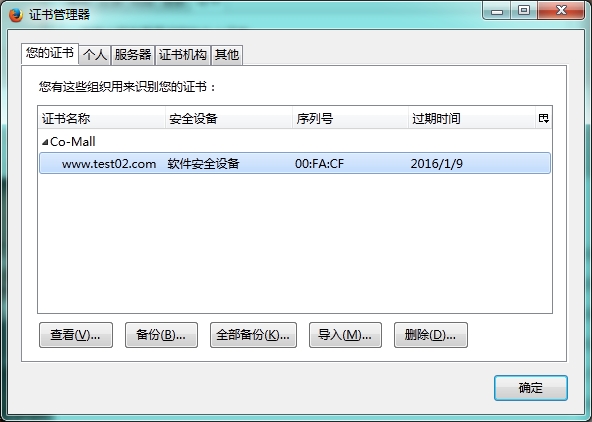
测试登录:
![UWL77WV}585A3R%BV}MT3]E.jpg wKioL1TeP_iw6PVcAAQvnb3Ve88739.jpg](http://s3.51cto.com/wyfs02/M01/59/BD/wKioL1TeP_iw6PVcAAQvnb3Ve88739.jpg)
![H`4$9ATV9PB$EVV04]MN1~5.jpg wKiom1TeP2XTvzT0AALhjIwO8Kw824.jpg](http://s3.51cto.com/wyfs02/M01/59/C0/wKiom1TeP2XTvzT0AALhjIwO8Kw824.jpg)