加密、解密以及openssl
一、计算机之间安全通信的标准
保密性:
数据保密性
隐私性
完整性:
数据完整性
系统完整性
可用性
二、常见的安全攻击方式以及安全体系结构建议
安全攻击:
被动攻击:窃听
主动攻击:伪装、重播、消息修改、拒绝服务
安全机制:加密、数字签名、访问控制、数据完整性、认证交换、流量填充、路由控制、公证
安全服务:
认证:验证数据来源的合法性
访问控制:阻止对资源的非授权访问
数据保密性:保护数据免于非授权泄露
连接保密性
无连接保密性
选择域保密性:只保密那些期望保护的数据
流量保密性
数据完整性:防止数据被恶意修改
不可否认性
三、加密类型和基于证书的认证
1、对称加密
①对称加密算法
DES (56)、3DES、AES (128,192,256,384,512)、Blowfish、Twofish、IDEA、RC6、CAST5
②特性:
1)加密、解密使用同一口令;
2)将明文分隔成固定大小的块,逐个进行加密
③常用工具:gpg, openssl enc
④缺陷:
1)密钥过多:需要为每个通信对象维护一个密钥
2)密钥传输不好实现
3)无法验证身份和数据完整性
2、公钥加密(非对称加密)
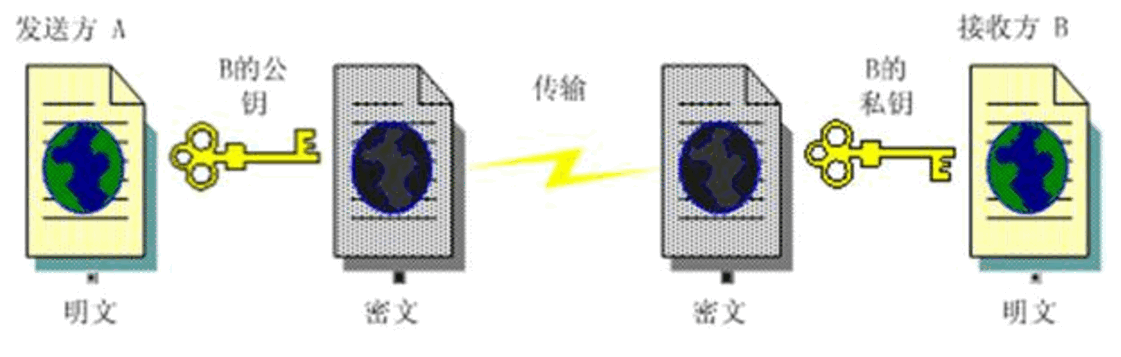
密钥:public key, secret key;公钥和私钥总是成对的,使用A的公钥加密的信息,必须使用A的私钥解密,反之亦然。公钥当然是可公开的,而私钥只能是通信者私有的
原理:通信双方各自拥有一对公钥和私钥,若A想和B通信,则A先向B申请获得其公钥,然后结合算法将明文数据加密成密文发给B,B再用其私钥解密即可
加密算法:RSA, DSA(Digital Signature Algorithm,只能用于签名), EIGamal
常用工具:gpg, openssl rsautl
公钥加密密钥长度很长,加密速度慢,通常不会用其直接加密数据,而用来作身份认证和密钥交换
3、单向加密:提取数据特征码(消息摘要),验证数据完整性的机制
特性:
定长输出:无论原数据多长,加密后的长度是恒定的
雪崩效应:数据的微小改变会引起结果的巨大变化
加密算法:MD5(定长输出128位)、SHA1(160位)、SHA256、SHA384、SHA512
常用工具:md5sum, sha1sum, openssl dgst, chsum
4、安全通信方式:结合对称加密、公钥加密和非对称加密
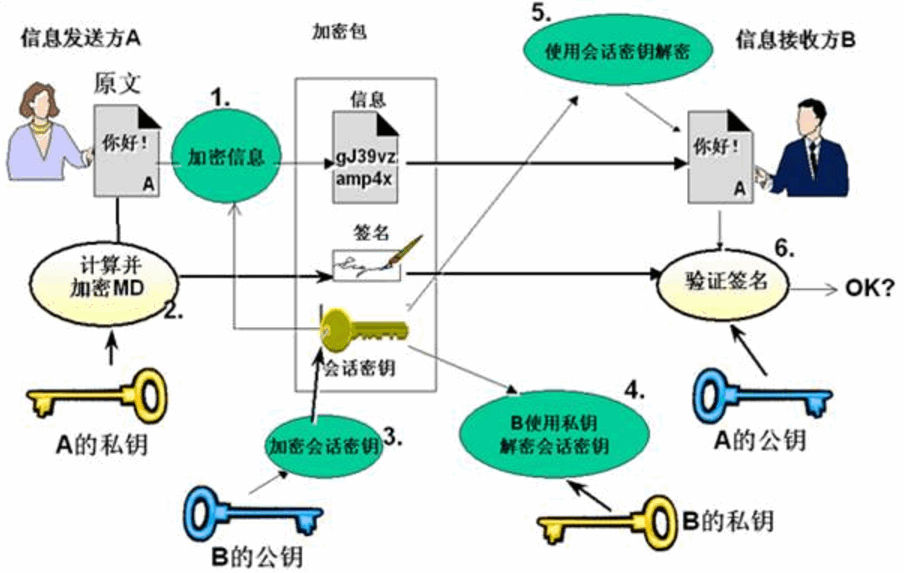
A和B通信:
发送方A:
①使用单向加密算法提取原数据的特征码,再用自己的私钥加密这段特征码后得到数字签名并将其附于原数据之后
②用对称加密算法加密原数据和数字签名,接着使用事先获取到的B的公钥加密会话密钥(对称密钥)
③将各种加密后的信息一并发给B
接收方B:
①B收到信息后,先用私钥解密出会话密钥,再用会话密钥解密出原数据和数字签名
②用A的公钥解密签名,能解密则确认了A的发送方身份
③用单向加密算法计算原数据得到一个特征码,将其与解密签名得到的特征码作比较,相同得说明数据完整性没有问题。
6、CA证书
可靠地获取到对方公钥是双方安全通信的前提。在网络上直接传输公钥容易被冒名顶替,公钥的合法性无法保证,而基于证书的认证是一个合理的解决方案
通信者在通信之前需要先向第三方权威机构CA(Certification Authority)提交数字证书的申请,CA机构验证通信者的身份,决定是否受理。若受理,它会将通信者的公钥和通信者其它的信息(主体名称、主体ID、有效期等)捆绑,并用单向加密算法计算出其特征码,再用CA自己的私钥加密这段特征码得到数字签名。通信者接收到附有数字签名和其它信息的CA证书之后就可开始通信了
验证证书的时候,需要得到CA的公钥。CA会通过一些权威媒介公布其公钥
CA还具有以下几个功能:
证书的更新:CA可以定期更新所有用户的证书,或者根据用户的请求来更新用户的证书
证书的作废:由于用户私钥泄露等原因,向CA提出证书作废的请求;证书已经过了有效期,CA自动将该证书作废。CA通过CRL(证书吊销列表)来完成上述功能
CA证书的信息组成:
版本号-证书序列号-算法参数-发行者的名称-有效期限-主体名称-公钥(由主体自己生成)-发行者的ID-主体的ID-CA的签名
7、两个概念
PKI(public key infrastructure,公钥基础设施)是支持公开密钥管理并能支持认证、加密、完整性和可追究性服务的一套技术和规范,是目前网络安全建设的基础
x.509:国际电信联盟所制定的证书结构和认证协议标准

四、SSL
SSL(secure sockets layer,安全套接字层协议)位于传输层协议和应用层协议之间,可以在Internet上提供秘密性传输。SSL采用公钥技术,其目标是保证两个应用间通信的保密性和可靠性,可在服务器端和用户端同时实现支持。SSL协议要求建立在可靠的TCP协议之上,基优势在于它是与应用层协议独立无关的,高层的应用层协议(例如:HTTP,FTP,TELNET等)能透明地建立于SSL协议之上。SSL协议在应用层协议通信之前就已经完成加密算法、通信密钥的协商及服务器认证工作,在此之后应用层协议所传送的数据都会被加密,从而保证通信的私密性
SSL协议提供的安全信道的特性:数据的保密性、数据的完整性、安全验证
版本:sslv1, sslv2, sslv3
TLS(transport layer secure,传输层安全协议)是SSL的继任者,二者差别不大
以https为例说明秘密通信的过程:
http(80/tcp) --> ssl --> https(443/tcp)
客户端和服务器端在经过tcp三次握手建立连接后,向服务器端索要其CA证书,收到证书后用CA的公钥解密签名,能解密说明证书确为CA所颁发,用单向加密算法计算证书上的数据得到特征码,将这个特征码与解密签名得到的特征码作比较,相同则说明数据完整性没问题。再者,要对比网站名与证书上的主体名称是否一致。认证通过后,客户端生成一个对称加密密钥,用服务器端的公钥加密后传给服务器端,服务器端用自己的私钥解密得到会话密钥,开始后续的数据通信。
密钥交换:IKE
算法:公钥加密、DH(Diffie-Hellman)
五、openssl
openssl是SSL的开源实现,openssl整个软件包主要分成三个部分:应用程序、SSL协议库、密码算法库
openssl: 多用途命令行工具,各功能分别使用子命令实现
libcrypto: 公共加密库
libssl: ssl协议的实现
openssl的配置文件:/etc/pki/tls/openssl.cnf
[root@node2 ~]# rpm -ql openssl /etc/pki/CA #与CA服务器相关的文件的默认目录 /etc/pki/CA/certs /etc/pki/CA/crl #吊销列表存放目录 /etc/pki/CA/newcerts /etc/pki/CA/private #CA的私钥存放目录 /etc/pki/tls /etc/pki/tls/certs /etc/pki/tls/certs/Makefile /etc/pki/tls/certs/make-dummy-cert /etc/pki/tls/certs/renew-dummy-cert /etc/pki/tls/misc /etc/pki/tls/misc/CA /etc/pki/tls/misc/c_hash /etc/pki/tls/misc/c_info /etc/pki/tls/misc/c_issuer /etc/pki/tls/misc/c_name /etc/pki/tls/openssl.cnf #配置文件 /etc/pki/tls/private /usr/bin/openssl /usr/lib64/.libcrypto.so.1.0.1e.hmac /usr/lib64/.libcrypto.so.10.hmac /usr/lib64/.libssl.so.1.0.1e.hmac /usr/lib64/.libssl.so.10.hmac /usr/lib64/libcrypto.so.1.0.1e /usr/lib64/libcrypto.so.10 /usr/lib64/libssl.so.1.0.1e /usr/lib64/libssl.so.10 /usr/lib64/openssl ... [root@node2 ~]# cat /etc/pki/tls/openssl.cnf ... #################################################################### [ CA_default ] dir = /etc/pki/CA # Where everything is kept certs = $dir/certs # Where the issued certs are kept crl_dir = $dir/crl # Where the issued crl are kept database = $dir/index.txt # database index file. #unique_subject = no # Set to 'no' to allow creation of # several ctificates with same subject. new_certs_dir = $dir/newcerts # default place for new certs. certificate = $dir/cacert.pem # The CA certificate serial = $dir/serial # The current serial number crlnumber = $dir/crlnumber # the current crl number # must be commented out to leave a V1 CRL crl = $dir/crl.pem # The current CRL private_key = $dir/private/cakey.pem# The private key RANDFILE = $dir/private/.rand # private random number file x509_extensions = usr_cert # The extentions to add to the cert ...
openssl常用命令或工具:
①openssl version:查看openssl版本
②openssl enc:对称加密
-e:加密,默认
-d:解密
-a:对加密结果进行base64编码
-salt:加盐,可提高密码强度;加盐后,相同的明文可以得到不同的密文。默认情况下,盐值是随机生成的
用法:
# openssl enc -des3 -a -salt -in /path/from/somefile -out /path/to/somecipherfile
# openssl enc -d -des3 -a -salt -in /path/from/somecipherfile -out /path/to/somefile
③openssl dgst:主要用作单向加密(消息摘要),也可用于数字签名和验证
用法:openssl dgst [-md5|-sha1] [-out /path/to/filename] /path/from/somefile
MAC: 消息摘要码,单向加密的一种延伸类的应用,能够实现在网络通信中不基于公钥而保证所传输的数据的完整性
机制:
CBC-MAC
HMAC:使用md5或sha1算法
④openssl passwd:计算密码hash (man sslpasswd)
用法:openssl passwd -1 [-salt SALT] {password} #可直接指定密码也可交互式输入密码
⑤openssl rand:生成随机数
用法:openssl rand -base64|-hex num
⑥openssl rsautl:使用RSA算法进行公钥加密、签名、验证身份等
⑦openssl genrsa:生成私钥
用法:(umask 077;openssl genrsa -out /path/to/keyfile [NUMBITS])
私钥毕竟是很重要的信息,不应让其它用户访问,因此应该缩小其访问权限。上面的括号将umask命令的作用范围限定在括号之内
openssl rsa -in /path/from/private_key_file -pubout [-out /path/to/pubkeyfile] #提出公钥
[root@node2 ~]# openssl #直接输入openssl命令将进入交互页面 OpenSSL> help openssl:Error: 'help' is an invalid command. Standard commands asn1parse ca ciphers cms crl crl2pkcs7 dgst dh dhparam dsa dsaparam ec ecparam enc engine errstr gendh gendsa genpkey genrsa nseq ocsp passwd pkcs12 pkcs7 pkcs8 pkey pkeyparam pkeyutl prime rand req rsa rsautl s_client s_server s_time sess_id smime speed spkac ts verify version x509 Message Digest commands (see the `dgst' command for more details) md2 md4 md5 rmd160 sha sha1 Cipher commands (see the `enc' command for more details) aes-128-cbc aes-128-ecb aes-192-cbc aes-192-ecb aes-256-cbc aes-256-ecb base64 bf bf-cbc bf-cfb bf-ecb bf-ofb camellia-128-cbc camellia-128-ecb camellia-192-cbc camellia-192-ecb camellia-256-cbc camellia-256-ecb cast cast-cbc cast5-cbc cast5-cfb cast5-ecb cast5-ofb des des-cbc des-cfb des-ecb des-ede des-ede-cbc des-ede-cfb des-ede-ofb des-ede3 des-ede3-cbc des-ede3-cfb des-ede3-ofb des-ofb des3 desx idea idea-cbc idea-cfb idea-ecb idea-ofb rc2 rc2-40-cbc rc2-64-cbc rc2-cbc rc2-cfb rc2-ecb rc2-ofb rc4 rc4-40 seed seed-cbc seed-cfb seed-ecb seed-ofb zlib OpenSSL> quit [root@node2 ~]# vim messages hello,how is it going? [root@node2 ~]# openssl enc -des3 -a -salt -in messages -out messages.cipher #加密 enter des-ede3-cbc encryption password: Verifying - enter des-ede3-cbc encryption password: [root@node2 ~]# rm -f messages [root@node2 ~]# openssl enc -d -des3 -a -salt -in messages.cipher -out messages #解密 enter des-ede3-cbc decryption password: [root@node2 ~]# cat messages hello,how is it going? [root@node2 ~]# openssl dgst -md5 -out digest messages #消息摘要 [root@node2 ~]# cat digest MD5(messages)= 718c23ac501a2debea364ab3161d7963 [root@node2 ~]# (umask 077;openssl genrsa -out key1 1024) #生成私钥,指定其权限为600,1024位 Generating RSA private key, 1024 bit long modulus ...............++++++ ..++++++ e is 65537 (0x10001) [root@node2 ~]# ll key1 -rw------- 1 root root 887 Nov 27 06:26 key1 [root@node2 ~]# cat key1 -----BEGIN RSA PRIVATE KEY----- MIICXQIBAAKBgQDP+5x73XLailDhP2BQ0hhxuzSE3yKJepVjLJCWMiemia/9wTDZ z+bIFkHu+gu0DP8jLLBkFjRdKLRg+hIk7uq611qrfQzoeT0myCv4Fy2SlT4+YDmk psq685Kh49kjqqbRi1s5wGgI9AxODCSy2dNASgEkmwrfN8vtt+rtGPTJEwIDAQAB AoGAZZTFrDXPp++Qa0Nx/mdu6vV9RDxbePw3RHX6tHEQrqVnILAf9PI3DJjaYScd WjZS0tI74NZ7gtijqQ3amNFcMT1Vp+H+x4MgISF/0ypHC502YZBgDHaQOFsCu0PI uDeyIASyix9rHnFdUVI3WvmWxczfB6ZIjmBrGCGoNuFhG0kCQQD68cDlkwruCcY5 zlku1PVmEBNi4Fb88R9PjJq92NSihbIrw5rjFl106OBLRPDjTSDuMcvlvgJgElNP bemRBWadAkEA1CxIn8GkIvwgbNTcpDQhDqEpT+ODiAvLZLh8zqZfvmU3uly8DHKl T31droF8lTu5bBIbifVzMU3WSg/neFsHbwJBANr9rkCqGZexn/NCSEG+RolS7hgT ftYt9g0Nvtx+JNHPqrTWdoxGMDieIV6OQ0mZPWuguTc8ogYE9/8RBAsyk2ECQQCJ YnNUHsrtbFyCnAKSwL52/pwFgsh0m06EVYFbPhfY7Sl8nveVB9dK9V5n1Kia6SVT eRYj6q9ASapsIog7QpY5AkAWYJNm+4Ki4ZrZJ5fuAn68tIy3ACYqQlgeD3BVNVwh kahOmdvLH5J0ni17On22v5JKaxEzGeu6mCOH44nlXX1s -----END RSA PRIVATE KEY----- [root@node2 ~]# openssl rsa -in key1 -pubout #从私钥中提出公钥 writing RSA key -----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDP+5x73XLailDhP2BQ0hhxuzSE 3yKJepVjLJCWMiemia/9wTDZz+bIFkHu+gu0DP8jLLBkFjRdKLRg+hIk7uq611qr fQzoeT0myCv4Fy2SlT4+YDmkpsq685Kh49kjqqbRi1s5wGgI9AxODCSy2dNASgEk mwrfN8vtt+rtGPTJEwIDAQAB -----END PUBLIC KEY-----
六、使用openssl建立私有CA
1、建立CA服务器:
①生成密钥
# (umask 077;openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048)
②自签证书
# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem -days 3650
req: 生成证书签署请求
-new: 新请求
-key /path/to/keyfile: 指定私钥文件,会自动提出公钥
-out /path/to/somefile:
-x509: 生成自签署证书
-days N: 有效天数
③初始化工作环境
# touch /etc/pki/CA/{index.txt,serial} #创建索引文件和序列号文件
# echo 01 > /etc/pki/CA/serial #指定可分配的起始序列号;每签署一个证书,该值会自动加1
[root@node2 ~]# cd /etc/pki/CA [root@node2 CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048) Generating RSA private key, 2048 bit long modulus ...........................................................................................................+++ .....+++ e is 65537 (0x10001) [root@node2 CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 3650 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN #主体所属国家 State or Province Name (full name) []:Zhejiang #省份 Locality Name (eg, city) [Default City]:Hangzhou #市 Organization Name (eg, company) [Default Company Ltd]:Dongpu #组织或公司名 Organizational Unit Name (eg, section) []:tech #部门 Common Name (eg, your name or your server's hostname) []:ca.dongpu.com #主机名,这个必须惟一,要与该主机能被解析的网站名保持一致 Email Address []:[email protected] [root@node2 CA]# touch index.txt serial #创建索引文件和序列号文件 [root@node2 CA]# echo 01 > serial [root@node2 CA]# ls cacert.pem certs crl index.txt newcerts private serial [root@node2 CA]# mkdir csr #可手动创建一个目录专门存放申请者请求文件,目录名可任取
2、节点申请证书:
(1)节点生成请求
①生成密钥对
# (umask 077;openssl genrsa -out /etc/httpd/ssl/httpd.key 2048)
②生成证书签署请求
# openssl req -new -key /etc/httpd/ssl/httpd.key -out /etc/httpd/ssl/httpd.csr
③把签署请求文件发送给CA服务器
# scp(具体用法见博客http://9124573.blog.51cto.com/9114573/1718021)
#以下假定要将http服务器配置成https,先给其申请一个CA证书 [root@node1 ~]# mkdir /etc/httpd/ssl [root@node1 ~]# (umask 077;openssl genrsa -out /etc/httpd/ssl/httpd.key 2048) Generating RSA private key, 2048 bit long modulus ..............................................+++ ........................................................................................+++ e is 65537 (0x10001) [root@node1 ~]# ll /etc/httpd/ssl/httpd.key -rw------- 1 root root 1675 Nov 24 08:19 /etc/httpd/ssl/httpd.key [root@node1 ~]# openssl req -new -key /etc/httpd/ssl/httpd.key -out /etc/httpd/ssl/httpd.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN #必须与CA一致 State or Province Name (full name) []:Zhejiang #必须与CA一致 Locality Name (eg, city) [Default City]:Hangzhou #必须与CA一致 Organization Name (eg, company) [Default Company Ltd]:Dongpu #必须与CA一致 #因为openssl是建立私有CA的,因此主体所属的国家、省、市、组织(或公司)名称这几条信息必须与CA保持一致 Organizational Unit Name (eg, section) []:web Common Name (eg, your name or your server's hostname) []:www.dongpu.com Email Address []:[email protected] Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: #若要给请求文件设置密码,要将密码告知CA An optional company name []: [root@node1 ~]# scp /etc/httpd/ssl/httpd.csr [email protected]:/etc/pki/CA/csr/ The authenticity of host '192.168.30.20 (192.168.30.20)' can't be established. RSA key fingerprint is a3:d3:a0:9d:f0:3b:3e:53:4e:ee:61:87:b9:3a:1c:8c. Are you sure you want to continue connecting (yes/no)? y Please type 'yes' or 'no': yes Warning: Permanently added '192.168.30.20' (RSA) to the list of known hosts. [email protected]'s password: httpd.csr 100% 1050 1.0KB/s 00:00
(2)CA签署证书
①验证证书中的信息;
②签署证书
# openssl ca -in /path/to/somefile.csr -out /path/to/somefile.crt -days N
③发送给请求者
[root@node2 CA]# ls csr httpd.csr [root@node2 CA]# openssl ca -in csr/httpd.csr -out csr/httpd.crt -days 1000 Using configuration from /etc/pki/tls/openssl.cnf Check that the request matches the signature Signature ok Certificate Details: Serial Number: 1 (0x1) Validity Not Before: Nov 27 03:20:26 2015 GMT Not After : Aug 23 03:20:26 2018 GMT Subject: countryName = CN stateOrProvinceName = Zhejiang organizationName = Dongpu organizationalUnitName = web commonName = www.dongpu.com emailAddress = [email protected] X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 1A:84:82:8B:09:18:3B:9C:D0:06:B5:E5:50:C1:C1:CF:33:9A:1B:A9 X509v3 Authority Key Identifier: keyid:65:B5:B5:F8:5E:2D:A8:16:3E:5C:58:10:A7:74:93:24:1A:91:DC:AE Certificate is to be certified until Aug 23 03:20:26 2018 GMT (1000 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated [root@node2 CA]# scp csr/httpd.crt [email protected]:/root #将签好的证书发给节点 The authenticity of host '192.168.30.10 (192.168.30.10)' can't be established. RSA key fingerprint is a3:d3:a0:9d:f0:3b:3e:53:4e:ee:61:87:b9:3a:1c:8c. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '192.168.30.10' (RSA) to the list of known hosts. [email protected]'s password: httpd.crt 100% 4610 4.5KB/s 00:00 [root@node2 CA]# ls newcerts #每签署一个证书,newcerts目录下会生成一个证书文件 01.pem [root@node2 CA]# cat serial 02
[root@node1 ~]# mv httpd.crt /etc/httpd/ssl/ [root@node1 ~]# ls /etc/httpd/ssl httpd.crt httpd.csr httpd.key
3、吊销证书
(1)节点
①获取证书serial并告知CA端
# openssl x509 -in /path/to/certificate_file.crt -noout -serial -subject
[root@node1 ~]# openssl x509 -in /etc/httpd/ssl/httpd.crt -noout -serial -subject serial=01 subject= /C=CN/ST=Zhejiang/O=Dongpu/OU=web/CN=www.dongpu.com/[email protected]
(2)CA
①根据节点提交的serial和subject信息来验证与index.txt文件中的信息是否一致;
②吊销证书
# openssl ca -revoke /etc/pki/CA/newcerts/SERIAL.pem
③生成可分配的起始吊销编号(该操作只需在第一次吊销时执行,之后每吊销一个证书,其值会自动加1)
# echo 01 > /etc/pki/CA/crlnumber
④生成或更新证书吊销列表
# cd /etc/pki/CA/crl/
# openssl ca -gencrl -out ca.crl
可查看crl文件的内容:
# openssl crl -in /path/to/crlfile.crl -noout -text
crl文件格式为pem,firefox浏览器不支持
[root@node2 CA]# cat index.txt #查看节点提交的信息与索引文件中的信息是否一致 V 180823032026Z 01 unknown /C=CN/ST=Zhejiang/O=Dongpu/OU=web/CN=www.dongpu.com/[email protected] [root@node2 CA]# openssl ca -revoke newcerts/01.pem #吊销证书 Using configuration from /etc/pki/tls/openssl.cnf Revoking Certificate 01. Data Base Updated [root@node2 CA]# cat index.txt R 180823032026Z 151127042637Z 01 unknown /C=CN/ST=Zhejiang/O=Dongpu/OU=web/CN=www.dongpu.com/[email protected] # R表示revoked,即已被吊销 [root@node2 CA]# echo 01 > crlnumber [root@node2 CA]# cat crlnumber 01 [root@node2 CA]# openssl ca -gencrl -out crl/ca.crl #生成或更新吊销证书列表 Using configuration from /etc/pki/tls/openssl.cnf [root@node2 CA]# openssl crl -in crl/ca.crl -noout -text #查看吊销证书列表 Certificate Revocation List (CRL): Version 2 (0x1) Signature Algorithm: sha1WithRSAEncryption Issuer: /C=CN/ST=Zhejiang/L=Hangzhou/O=Dongpu/OU=tech/CN=ca.dongpu.com/[email protected] Last Update: Nov 27 04:38:57 2015 GMT Next Update: Dec 27 04:38:57 2015 GMT CRL extensions: X509v3 CRL Number: #吊销编号 1 Revoked Certificates: Serial Number: 01 #被吊销的证书序列号 Revocation Date: Nov 27 04:26:37 2015 GMT Signature Algorithm: sha1WithRSAEncryption 3f:5d:5b:6a:f0:9f:f5:6d:fe:48:f6:f7:32:09:c8:30:3f:70: 39:3a:28:a0:bf:e7:31:b3:b5:7a:91:07:71:57:d9:a9:16:f5: ad:a6:13:09:22:95:95:2b:41:f1:32:d7:5a:f4:7a:ad:44:20: aa:d7:b1:d3:f8:45:5d:a6:71:a7:45:4e:c0:71:f9:34:16:ed: af:21:05:46:3d:90:92:a7:8b:ca:f8:2c:90:1e:c7:f7:bc:f7: 9e:cf:e4:6b:30:c5:8a:bd:dd:90:9b:a0:ba:03:dc:06:31:d7: 95:4a:b4:a6:cc:22:6b:ce:87:aa:eb:fe:e4:e8:02:3b:7a:f5: cb:a3:70:af:df:60:be:a5:4d:8e:be:b8:69:c0:92:b7:a1:b8: 6b:9e:4c:a1:35:7c:f1:db:09:b6:e1:5c:b7:1d:b4:5a:44:e0: 70:bd:1f:50:2e:1d:4c:c8:05:04:19:7e:a2:59:0a:3d:8d:2b: 2d:05:8f:12:80:96:16:65:d4:7d:44:80:ee:f8:97:ec:5c:b4: 98:8a:f9:f6:aa:f8:25:cd:f7:d5:11:23:1c:d4:b1:b3:08:54: 33:34:87:94:52:59:7d:56:07:36:e1:d3:b4:ea:e3:aa:d9:69: bb:cb:1a:25:e3:73:c8:3f:68:01:9c:8f:4a:d7:2f:ec:33:82: 52:89:b5:03