apache配置SSL
http://blog.chinaunix.net/uid-16979052-id-3549100.html
一:制作根CA
要制作最高层认证中心,可以以一般使用者权限来做,不一定要是 root 。但如果做出来的最高层认证中心,是整个组织签发凭证要用的,建议以 root 的权限来做,比较安全。同理,制作凭证,也可以以一般使用者权限来做。但如果做出来的凭证,是这个伺服器要用的,为安全起见,建议以 root 的权限来做.
1:设定相关目录
[root@redhat ~]# mkdir -pv /etc/ssl
mkdir: created directory `/etc/ssl'
[root@redhat ~]# mkdir -pv /etc/ssl/private
mkdir: created directory `/etc/ssl/private'
[root@redhat ~]# chmod og-rwx /etc/ssl/private/
[root@redhat ~]# mkdir -pv /etc/ssl/certs
mkdir: created directory `/etc/ssl/certs'
[root@redhat ~]# mkdir -pv /etc/ssl/crl
mkdir: created directory `/etc/ssl/crl'
[root@redhat ~]#mkdir -pv /etc/ssl/newcerts
mkdir: created directory `/etc/ssl/newcerts'
2:设定openssl配置文件
[root@redhat ~]# mv /usr/share/ssl/openssl.cnf /etc/ssl/
[root@redhat ~]# ln -sv /etc/ssl/openssl.cnf /usr/share/ssl/openssl.cnf
create symbolic link `/usr/share/ssl/openssl.cnf' to `/etc/ssl/openssl.cnf'
[root@redhat ~]# export OPENSSL_CONF="/etc/ssl/openssl.cnf"
[root@redhat ~]# echo "# OpenSSL Setting Locate" >> ~/.bashrc
[root@redhat ~]# echo "export OPENSSL_CONF=\"/etc/ssl/openssl.cnf\"" >> ~/.bashrc
[root@redhat ~]# openssl rand -out /etc/ssl/private/.rand 1024 ##制作随机数
[root@redhat ~]# chmod og-rwx /etc/ssl/private/.rand
[root@redhat ~]# vi /etc/ssl/openssl.cnf ##编辑配置文件
dir = /etc/ssl
3:制作根CA的私钥
命令中genrsa是表示生成rsa格式的私钥,-des3是指使用的加密算法;-out是指私钥的输出路径;2048是指加密的位数.
[root@redhat ~]# openssl genrsa -des3 -out /etc/ssl/private/redhatroot.key 2048
Generating RSA private key, 2048 bit long modulus
..........+++
.....................................+++
e is 65537 (0x10001)
Enter pass phrase for /etc/ssl/private/redhatroot.key: ##这里提示输入密码
Verifying - Enter pass phrase for /etc/ssl/private/redhatroot.key:
[root@redhat ~]# chmod og-rwx /etc/ssl/private/redhatroot.key
4:填写凭证申请书
凭证申请书,是把你的资料,和这个 Public Key 夹在一起,以便认证中心审核,签上签名用的。所以这个步骤,会问你这个 Key 的相关资料,包括国家、城市、单位名称、部门名称、凭证名称、联络人的信箱,以及申请的效期等等。请一一填写。
[root@redhat ~]# openssl req -new -key /etc/ssl/private/redhatroot.key -out /tmp/redhatroot.req
Enter pass phrase for /etc/ssl/private/redhatroot.key: ##输入上面生成redhatroot.key时设置密码
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [GB]:CN
State or Province Name (full name) [Berkshire]:GD
Locality Name (eg, city) [Newbury]:Dong Guan
Organization Name (eg, company) [My Company Ltd]:none
Organizational Unit Name (eg, section) []:redhat
Common Name (eg, your name or your server's hostname) []:redhat
Email Address []:[email protected]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
5:签发凭证,创建根CA
根CA因为没有上级了,没有人能给它签名,只能自己给自己签名.根CA最好永远不要过期。要是过期重签,所有原来它签发的凭证也都要重签,所有 SSL 程式也都要重新设定。所以我们效期签 7305 天(大约 20年)。若不设效期的话,预设是 30 天(一个月)。redhatroot.crt 是公钥凭证,要尽量散出去,让大家用。最好放到内部网路上,或放到网站上,让大家自己下载,自己加进去。
如:windows添加CA信任
下载ca证书到本地

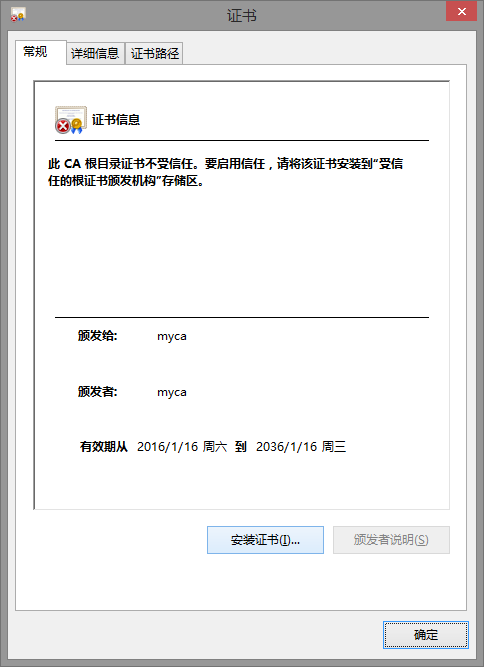
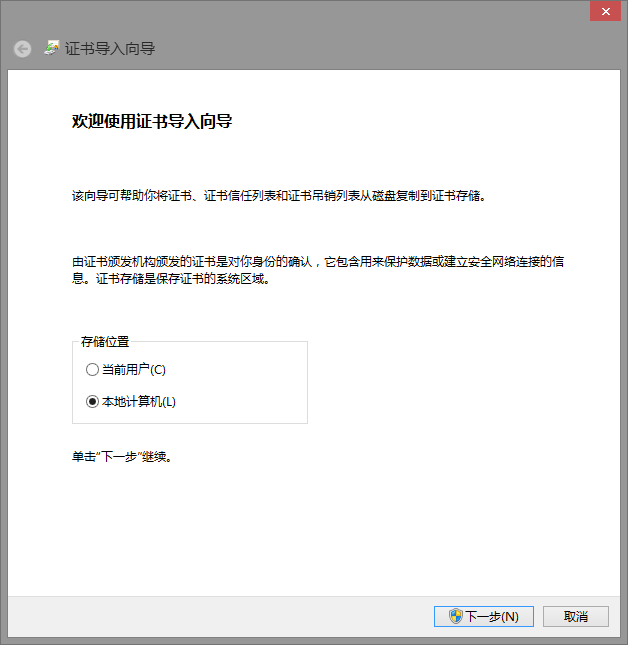
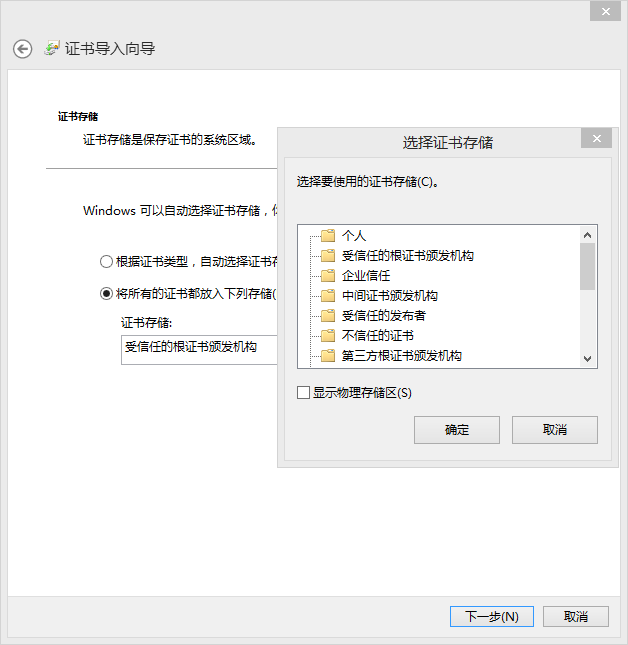
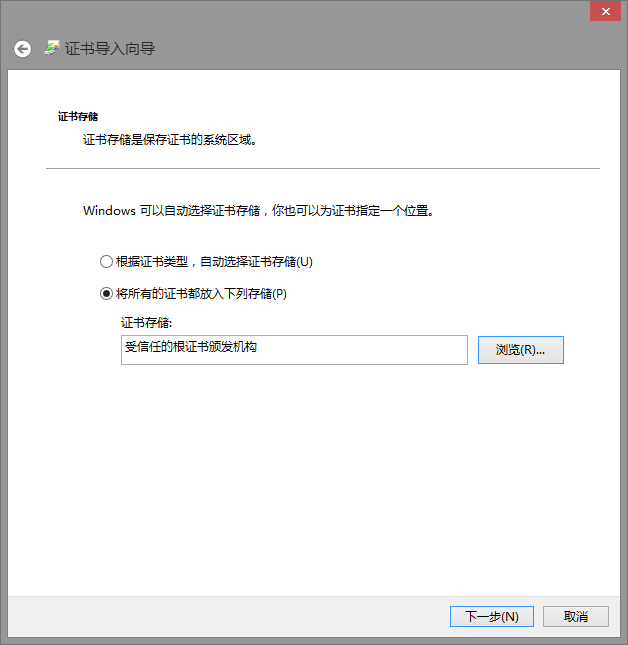
可以 certmgr.msc打开证书管理控制台查看删除等。
[root@redhat ~]# openssl x509 -req -days 7305 -sha256 -extfile /etc/ssl/openssl.cnf \
-extensions v3_ca -signkey /etc/ssl/private/redhatroot.key -in /tmp/redhatroot.req \
-out /etc/ssl/certs/redhatroot.crt
Signature ok
subject=/C=CN/ST=GD/L=Dong Guan/O=none/OU=redhat/CN=redhat/[email protected]
Getting Private key
Enter pass phrase for /etc/ssl/private/redhatroot.key: ##输入上面生成redhatroot.key时设置密码
[root@redhat ~]# rm -f /tmp/redhatroot.req ##签完凭证,凭证申请书就不用了,可以删掉。
二:创建web证书
1:生成证书私钥
[root@redhat ~]# openssl genrsa -out /etc/ssl/private/myhost.key 2048
Generating RSA private key, 2048 bit long modulus
..................+++
.............................................................................................................+++
e is 65537 (0x10001)
[root@redhat ~]# chmod og-rwx /etc/ssl/private/myhost.key
2:填写凭证申请书
被问及Common Name的时候,请输入你的web服务器的完全限定域名(FQDN)例如:redhat.test.com.当被问及A challenge password的时候,直接按回车继续。如果你没有在第二步从key中把passphrase删除,那么每次你运行/usr/local/httpd/apachectl start启动服务器的时候你都要输入密码。这也就意味着如果你的服务器因为某些原因重新启动了,除非你在服务器旁手动敲入了密码,否则你的web服务器就不会启动。
[root@redhat ~]# openssl req -new -key /etc/ssl/private/myhost.key -out /tmp/myhost.req
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [GB]:CN
State or Province Name (full name) [Berkshire]:GD
Locality Name (eg, city) [Newbury]:Dong Guan
Organization Name (eg, company) [My Company Ltd]:none
Organizational Unit Name (eg, section) []:www
Common Name (eg, your name or your server's hostname) []:redhat.test.com ##也可以使用*.test.com 这里很重要
Email Address []:[email protected]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []: ##这里不要输入密码
An optional company name []:
3:生成web证书
[root@redhat ~]# openssl x509 -req -days 3650 -sha256 -extfile \
/etc/ssl/openssl.cnf -extensions v3_req -CA /etc/ssl/certs/redhatroot.crt \
-CAkey /etc/ssl/private/redhatroot.key -CAserial /etc/ssl/redhatroot.srl -CAcreateserial \
-in /tmp/myhost.req -out /etc/ssl/certs/myhost.crt
Signature ok
subject=/C=CN/ST=GD/L=Dong Guan/O=none/OU=www/CN=redhat.test.com/[email protected]
Getting CA Private Key
Enter pass phrase for /etc/ssl/private/redhatroot.key:
[root@redhat ~]# rm -f /tmp/myhost.req
三:配置Apache
1:编辑httpd.conf
编辑httpd.conf的内容以启用ssl支持,如果在安装apache时没有加载ssl模块,那么需要重新安装或编译.需启用LoadModule ssl_module modules/mod_ssl.so(第80行)及 Include /etc/httpd/extra/httpd-ssl.conf(第456行)
[root@redhat ~]# vi /etc/httpd/httpd.conf
LoadModule ssl_module modules/mod_ssl.so ##启用这两行
Include /etc/httpd/extra/httpd-ssl.conf
#<VirtualHost *:80>
#ServerName redhat.test.com ##注释这几行,如果有的话
#DocumentRoot /var/www/extsuite/extmail/html/
#ScriptAlias /extmail/cgi /var/www/extsuite/extmail/cgi
#Alias /extmail /var/www/extsuite/extmail/html
#ScriptAlias /extman/cgi /var/www/extsuite/extman/cgi
#Alias /extman /var/www/extsuite/extman/html
#SuexecUserGroup vmail vmail
#Alias /phpadmin /var/www/phpadmin
#</VirtualHost>
2:添加相关证书文件
[root@redhat ~]# cp /etc/ssl/certs/myhost.crt /etc/httpd/server.crt
[root@redhat ~]# cp /etc/ssl/private/myhost.key /etc/httpd/server.key
3:设置httpd-ssl.conf文件
对照修改以下的地方就可以了,重启后Apache就可以支持SSL了.
[root@redhat ~]# vi /etc/httpd/extra/httpd-ssl.conf
<VirtualHost _default_:443>
# General setup for the virtual host
#DocumentRoot "/usr/local/httpd/htdocs"
#ServerName [url]www.example.com:443[/url]
#ServerAdmin [email protected]
ServerName redhat.test.com:443
DocumentRoot /var/www/extsuite/extmail/html/
ScriptAlias /extmail/cgi /var/www/extsuite/extmail/cgi
Alias /extmail /var/www/extsuite/extmail/html
ScriptAlias /extman/cgi /var/www/extsuite/extman/cgi
Alias /extman /var/www/extsuite/extman/html
SuexecUserGroup vmail vmail
Alias /phpadmin /var/www/phpadmin
ErrorLog /usr/local/httpd/logs/error_log
TransferLog /usr/local/httpd/logs/access_log
# SSL Engine Switch:
4:重启服务
[root@redhat ~]# /usr/local/httpd/bin/apachectl stop
[root@redhat ~]# /usr/local/httpd/bin/apachectl start