WiFidog运行环境及与authpuppy交互数据
0:WiFiDog运行环境
/wlan/portal/buildroot/etc # ps -w
\ PID USER VSZ STAT COMMAND
1 root 868 S init
2 root 0 SW< [kthreadd]
3 root 0 SW< [ksoftirqd/0]
4 root 0 SW< [events/0]
5 root 0 SW< [khelper]
6 root 0 SW< [async/mgr]
7 root 0 SW< [kblockd/0]
8 root 0 SW [pdflush]
9 root 0 SW [pdflush]
10 root 0 SW< [kswapd0]
11 root 0 SW< [crypto/0]
32 root 0 SW< [mtdblockd]
37 root 0 SWN [jffs2_gcd_mtd3]
564 root 864 S /usr/sbin/telnetd
566 root 864 S /usr/sbin/httpd -h /usr/www/
568 root 888 R -sh
881 nobody 1004 S dnsmasq
2191 root 868 R ps -w
2340 root 876 S udhcpd -S /etc/udhcpd.conf
3877 root 884 S udhcpc -i eth0 -p /var/run/udhcpc_wan.pid -s /etc/udhcpc.script
3892 root 1788 S wifidog -c /etc/wifidog.conf
4059 root 1788 S wifidog -c /etc/wifidog.conf
4060 root 1788 S wifidog -c /etc/wifidog.conf
4061 root 1788 S wifidog -c /etc/wifidog.conf
4062 root 1788 S wifidog -c /etc/wifidog.conf
/etc # ifconfig
ath0 Link encap:Ethernet HWaddr 00:0B:6B:B4:01:63
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1036165 errors:0 dropped:0 overruns:0 frame:0
TX packets:902768 errors:0 dropped:181 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:173265983 (165.2 MiB) TX bytes:472405245 (450.5 MiB)
br0 Link encap:Ethernet HWaddr 00:0B:6B:B4:01:63
inet addr:192.168.100.10 Bcast:192.168.100.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1038127 errors:0 dropped:0 overruns:0 frame:0
TX packets:895866 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:136852412 (130.5 MiB) TX bytes:451119780 (430.2 MiB)
eth0 Link encap:Ethernet HWaddr 00:03:7F:FF:FF:FF
inet addr:192.168.0.143 Bcast:192.168.0.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:100545 errors:0 dropped:0 overruns:0 frame:0
TX packets:83617 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:94237206 (89.8 MiB) TX bytes:9617979 (9.1 MiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:50 errors:0 dropped:0 overruns:0 frame:0
TX packets:50 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:5181 (5.0 KiB) TX bytes:5181 (5.0 KiB)
wifi1 Link encap:UNSPEC HWaddr 00-0B-6B-B4-01-63-00-00-00-00-00-00-00-00-00-00
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:2682769 errors:0 dropped:0 overruns:0 frame:0
TX packets:3642860 errors:8464 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:511
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
Interrupt:64 Memory:b0000000-b0020000
/etc # brctl show
bridge name bridge id STP enabled interfaces
br0 8000.000b6bb40163 no ath0
/etc #
/etc # route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.100.0 * 255.255.255.0 U 0 0 0 br0
192.168.0.0 * 255.255.255.0 U 0 0 0 eth0
default 192.168.0.1 0.0.0.0 UG 0 0 0 eth0
/etc # iptables -t nat -L
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
MASQUERADE all -- anywhere anywhere
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
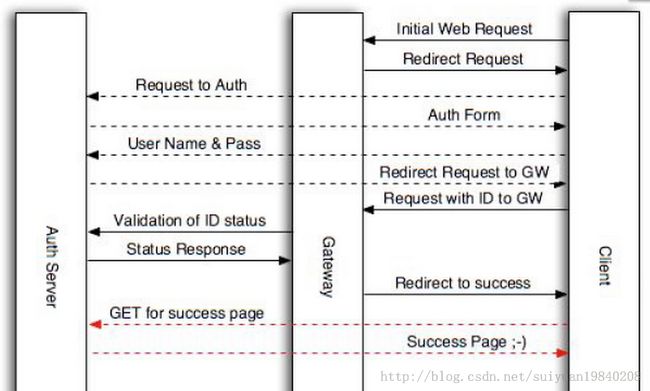
1: 用户,WiFiDog,Authpuppy交互过程
General Flow Description:
- The client does his initial request, as if he was already connected, (e.g.: http://www.google.ca)
- The Gateway's firewall rules mangle the request to redirect it to a local port on the Gateway. When that's the done, the Gateway provides an HTTP Redirect reply that contains the Gateway ID, Gateway FQDN and other informations
- The Client does his request to the Auth Server as specified by the Gateway, see Login Protocol
- The Auth Server replies with a (potentially custom) splash (login) page
- The Client provides his identification informations (username and password)
- Upon succesful authentication, the client gets an HTTP Redirect to the Gateway's own web server with his authentication proof (a one-time token), http://GatewayIP:GatewayPort/wifidog/auth?token=[auth token]
- The Client then connects to the Gateway and thus gives it his token
- The Gateway requests validation of the token from the Auth Server, see Client Protocol
- The Auth Server confirms the token
- The Gateway then sends a redirect to the Client to obtain the Success Page from the Auth Server, redirects to http://auth_server/portal/
- The Auth Server notifies the Client that his request was successful
2:wifidog与authpuppy交互数据包
2.0:wifidog对用户重定向数据包
当用户首次访问一个网址的时候:wifidog会将用户的请求重定义到登陆认证界面。
(http.c:135) Captured 192.168.100.11 requesting [http%3A//apilocate.amap.com/mobile/plaintext] and re-directing them to login page
(http.c:215) Redirecting client browser to http://192.168.0.142:80/authpuppy/web/login/?gw_address=192.168.100.10&gw_port=2060&gw_id=123456789&mac=90:7a:28:01:20:26&url=http%3A//apilocate.amap.com/mobile/plaintext
当用户输入了用户名及密码之后,访问了上面的地址自后,authpuppy就回给运行wifidog的路由器回复一个包:格式如下:http://GatewayIP:GatewayPort/wifidog/auth?token=[auth token]
http%3A//192.168.100.10%3A2060/wifidog/auth%3Ftoken%3D1ea7415482c4af464f1706a92adee9ea824d4242 之后就回出发路由器的login登陆请求。
2.1:wifidog与authpuppy之间的ping数据
(ping_thread.c:167) HTTP Request to Server: [GET /authpuppy/web/ping/?gw_id=123456789&sys_uptime=75432&sys_memfree=38288&sys_load=0.00&wifidog_uptime=6 HTTP/1.0 User-Agent: WiFiDog 20090925 Host: 192.168.0.142 ] (ping_thread.c:171) Reading response (ping_thread.c:199) Read 254 bytes, total now 254 (ping_thread.c:217) Done reading reply, total 254 bytes (ping_thread.c:221) HTTP Response from Server: [HTTP/1.0 200 OK Date: Tue, 10 Jun 2014 09:32:07 GMT Server: Apache/2.2.15 (Fedora) X-Powered-By: PHP/5.3.3 Set-Cookie: authpuppy=s4jijh0k8o7h8dhhp67d1sttb1; path=/ Content-Length: 5 Connection: close Content-Type: text/html; charset=utf-8 Pong ] (ping_thread.c:228) Auth Server Says: Pong2.2:用户与authpuppy之间的登陆认证数据
(centralserver.c:114) Sending HTTP request to auth server: [GET /authpuppy/web/auth/?stage=login&ip=192.168.100.11&mac=90:7a:28:01:20:26&token=9941ed0bc138c12c6edc4b1ed8358bd4516b86f2&incoming=0&outgoing=0&gw_id=123456789 HTTP/1.0 User-Agent: WiFiDog 20090925 Host: 192.168.0.142 ] (centralserver.c:117) Reading response (centralserver.c:144) Read 256 bytes, total now 256 (centralserver.c:164) HTTP Response from Server: [HTTP/1.0 200 OK Date: Tue, 10 Jun 2014 09:32:48 GMT Server: Apache/2.2.15 (Fedora) X-Powered-By: PHP/5.3.3 Set-Cookie: authpuppy=nlq9lq8pjii7hfl80oq5bg0en1; path=/ Content-Length: 7 Connection: close Content-Type: text/html; charset=utf-8 Auth: 1] (centralserver.c:168) Auth server returned authentication code 12.3:运行wifidog的路由器更新traffic counters到authpuppy
(centralserver.c:114) Sending HTTP request to auth server: [GET /authpuppy/web/auth/?stage=counters&ip=192.168.100.11&mac=90:7a:28:01:20:26&token=9941ed0bc138c12c6edc4b1ed8358bd4516b86f2&incoming=1161884&outgoing=81646&gw_id=123456789 HTTP/1.0 User-Agent: WiFiDog 20090925 Host: 192.168.0.142 ] (centralserver.c:117) Reading response (centralserver.c:144) Read 256 bytes, total now 256 (centralserver.c:164) HTTP Response from Server: [HTTP/1.0 200 OK Date: Tue, 10 Jun 2014 09:33:06 GMT Server: Apache/2.2.15 (Fedora) X-Powered-By: PHP/5.3.3 Set-Cookie: authpuppy=6oclp4cvltb8g43c68vuqv7k40; path=/ Content-Length: 7 Connection: close Content-Type: text/html; charset=utf-8 Auth: 1] (centralserver.c:168) Auth server returned authentication code 12.4:用户超时下线
(centralserver.c:114) Sending HTTP request to auth server: [GET /authpuppy/web/auth/?stage=logout&ip=192.168.100.11&mac=90:7a:28:01:20:26&token=9941ed0bc138c12c6edc4b1ed8358bd4516b86f2&incoming=0&outgoing=0&gw_id=123456789 HTTP/1.0 User-Agent: WiFiDog 20090925 Host: 192.168.0.142 ] (centralserver.c:117) Reading response (centralserver.c:144) Read 256 bytes, total now 256 (centralserver.c:164) HTTP Response from Server: [HTTP/1.0 200 OK Date: Tue, 10 Jun 2014 09:57:07 GMT Server: Apache/2.2.15 (Fedora) X-Powered-By: PHP/5.3.3 Set-Cookie: authpuppy=hqo5uln8f2f8254sc2lrkjt3m2; path=/ Content-Length: 7 Connection: close Content-Type: text/html; charset=utf-8 Auth: 0] (centralserver.c:168) Auth server returned authentication code 0
3:wifidog代码主要函数执行顺序
http_send_redirect_to_auth()函数是WiFidog路由器发送数据给用户的接口。
l流程1:httpdGetConnection()-->thread_httpd()-->httpdReadRequest()-->httpdProcessRequest()-->http_callback_404()-->http_send_redirect_to_auth()
流程2:httpdGetConnection()-->thread_httpd()-->httpdReadRequest()-->httpdProcessRequest()-->http_callback_auth-->
authenticate_client()--> auth_server_request(&auth_response, REQUEST_TYPE_LOGIN, r->clientAddr, mac, token, 0, 0)-->fw_allow()-->iptables_fw_access()-->iptables_do_command()--->http_send_redirect_to_auth(r, urlFragment, "Redirect to portal");