ARM架构kprobe应用及实现分析(11 原理)
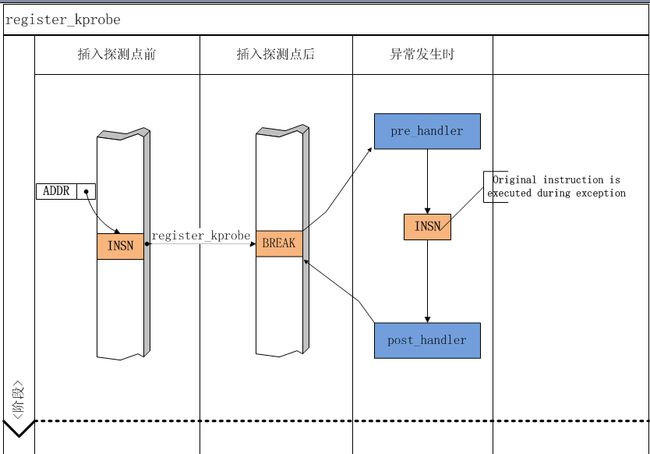
1 拷贝探测的code , 插入特殊指令(ARM是插入未定义指令)
2 CPU运行到未定义指令,会产生trap, 进入ISR,并保存当前寄出去的状态
通过LINUX的通知机制,会执行“pre_handler”(前提是你已经注册过了)
3 进入单步模式,运行你备份出来的代码
(此代码运行的是拷贝出来的,防止别的CPU也恰巧运行到此位置)
4 单步模式后,运行“post_handler”,恢复正常模式,接着运行下面的指令。
参考: kprobes.txt
How Does a Kprobe Work?
When a kprobe is registered, Kprobes makes a copy of the probed
instruction and replaces the first byte(s) of the probed instruction
with a breakpoint instruction (e.g., int3 on i386 and x86_64).
When a CPU hits the breakpoint instruction, a trap occurs, the CPU's
registers are saved, and control passes to Kprobes via the
notifier_call_chain mechanism. Kprobes executes the "pre_handler"
associated with the kprobe, passing the handler the addresses of the
kprobe struct and the saved registers.
Next, Kprobes single-steps its copy of the probed instruction.
(It would be simpler to single-step the actual instruction in place,
but then Kprobes would have to temporarily remove the breakpoint
instruction. This would open a small time window when another CPU
could sail right past the probepoint.)
After the instruction is single-stepped, Kprobes executes the
"post_handler," if any, that is associated with the kprobe.
Execution then continues with the instruction following the probepoint.