网络嗅探技术
网络嗅探技术
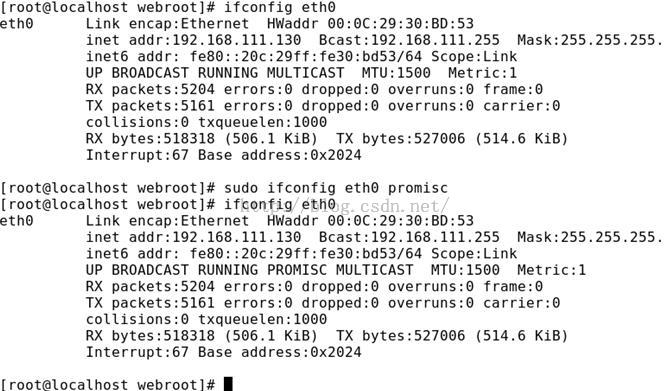
数据链路层上的交换(switched)网络与非交换(unswitched)网络之间也存在区别。在非交换网络中,以太网数据包经过网络上的每个设备,期望每个系统设备只查看以其作为目的地址发送的数据包。然而,将设备设置为混杂模式(promiscuous mode)是相当容易的,该模式允许设备查看所有数据包,而不管其目的地址是什么。大多数的数据包捕获程序,例如tcpdump,默认情况下将它们监听的设备设置为混杂模式。可以使用ifconfig设置混杂模式,如下面地输出所示。
[root@localhost webroot]#ifconfig eth0
eth0 Link encap:Ethernet HWaddr 00:0C:29:30:BD:53
inet addr:192.168.111.130 Bcast:192.168.111.255 Mask:255.255.255.0
inet6 addr:fe80::20c:29ff:fe30:bd53/64 Scope:Link
UP BROADCAST RUNNINGMULTICAST MTU:1500 Metric:1
RX packets:5204 errors:0 dropped:0overruns:0 frame:0
TX packets:5161 errors:0 dropped:0overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:518318 (506.1 KiB) TX bytes:527006 (514.6 KiB)
Interrupt:67 Base address:0x2024
[root@localhost webroot]#ifconfig eth0 promisc
[root@localhost webroot]#ifconfig eth0
eth0 Link encap:Ethernet HWaddr 00:0C:29:30:BD:53
inet addr:192.168.111.130 Bcast:192.168.111.255 Mask:255.255.255.0
inet6 addr:fe80::20c:29ff:fe30:bd53/64 Scope:Link
UP BROADCAST RUNNINGPROMISC MULTICAST MTU:1500 Metric:1
RX packets:5204 errors:0 dropped:0overruns:0 frame:0
TX packets:5161 errors:0 dropped:0overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:518318 (506.1 KiB) TX bytes:527006 (514.6 KiB)
Interrupt:67 Base address:0x2024
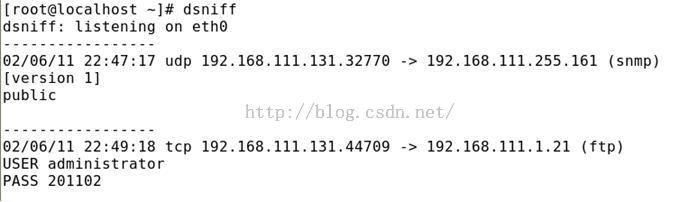
不是出于公共查看的必要而捕获数据包的行为称为嗅探( sniffing),有的也将改词翻译成窃听。以混杂模式在一个非交换网络上窃听数据包可以发现各种有用信息,如下面的输出所示。
[root@localhostwallpapers]# tcpdump -l -X 'ip host 192.168.111.1'
tcpdump:verbose output suppressed, use -v or -vv for full protocol decode
listeningon eth0, link-type EN10MB (Ethernet), capture size 96 bytes
20:15:28.421470IP 192.168.111.130.35928 > 192.168.111.1.ftp: S 1037226089:1037226089(0) win5840 <mss 1460,sackOK,timestamp 20714121 0,nop,wscale 6>
0x0000: 4500 003c c2e0 4000 4006 1807 c0a8 6f82 E..<..@[email protected].
0x0010: c0a8 6f01 8c58 0015 3dd2 d069 0000 0000 ..o..X..=..i....
0x0020: a002 16d0 22ee 0000 0204 05b4 0402 080a ...."...........
0x0030: 013c 1289 0000 0000 0103 0306 .<..........
20:15:28.433049IP 192.168.111.1.ftp > 192.168.111.130.35928: P 28:41(13) ack 1 win 65535<nop,nop,timestamp 161164 20714123>
0x0000: 4500 0041 f8ce 4000 8006 a213 c0a8 6f01 [email protected].
0x0010: c0a8 6f82 0015 8c58 1c79 4b62 3dd2 d06a ..o....X.yKb=..j
0x0020: 8018 ffff 6662 0000 0101 080a 0002 758c ....fb........u.
0x0030: 013c 128b 3232 3020 7765 6c63 6f6d 650d .<..220.welcome.
0x0040: 0a .
0x0000: 4510 0048 c2e7 4000 4006 17e4 c0a8 6f82 E..H..@[email protected].
0x0010: c0a8 6f01 8c58 0015 3dd2 d089 1c79 4bca ..o..X..=....yK.
0x0020: 8018 005c 38ec 0000 0101 080a 013c 1ef4 ...\8........<..
0x0030: 0002 758c 5553 4552 2061 646d 696e 6973 ..u.USER.adminis
0x0040: 7472 6174 6f72 0d0a trator..
20:15:31.602539IP 192.168.111.1.ftp > 192.168.111.130.35928: P 132:174(42) ack 52 win 65484<nop,nop,timestamp 161195 20717300>
0x0000: 4500 005e f8d1 4000 8006 a1f3 c0a8 6f01 E..^[email protected].
0x0010: c0a8 6f82 0015 8c58 1c79 4bca 3dd2 d09d ..o....X.yK.=...
0x0020: 8018 ffcc aad7 0000 0101 080a 0002 75ab ..............u.
0x0030: 013c 1ef4 3333 3120 5061 7373 776f 7264 .<..331.Password
0x0040: 2072 6571 7569 7265 6420 666f 7220 6164 .required.for.ad
0x0050: 6d69 mi
20:15:31.602904IP 192.168.111.130.35928 > 192.168.111.1.ftp: . ack 174 win 92<nop,nop,timestamp 20717304 161195>
0x0000: 4510 0034 c2e8 4000 4006 17f7 c0a8 6f82 E..4..@[email protected].
0x0010: c0a8 6f01 8c58 0015 3dd2 d09d 1c79 4bf4 ..o..X..=....yK.
0x0020: 8010 005c 7d60 0000 0101 080a 013c 1ef8 ...\}`.......<..
0x0030: 0002 75ab ..u.
20:15:35.127890IP 192.168.111.130.35928 > 192.168.111.1.ftp: P 52:65(13) ack 174 win 92<nop,nop,timestamp 20720828 161195>
0x0000: 4510 0041 c2e9 4000 4006 17e9 c0a8 6f82 E..A..@[email protected].
0x0010: c0a8 6f01 8c58 0015 3dd2 d09d 1c79 4bf4 ..o..X..=....yK.
0x0020: 8018 005c 0e52 0000 0101 080a 013c 2cbc ...\.R.......<,.
0x0030: 0002 75ab 5041 5353 2032 3031 3130 320d ..u.PASS.201102.
0x0040: 0a .
20:15:35.130719IP 192.168.111.1.ftp > 192.168.111.130.35928: P 174:209(35) ack 65 win 65471<nop,nop,timestamp 161230 20720828>
0x0000: 4500 0057 f8d2 4000 8006 a1f9 c0a8 6f01 [email protected].
0x0010: c0a8 6f82 0015 8c58 1c79 4bf4 3dd2 d0aa ..o....X.yK.=...
0x0020: 8018 ffbf b8c5 0000 0101 080a 0002 75ce ..............u.
0x0030: 013c 2cbc 3233 3020 5573 6572 2061 646d .<,.230.User.adm
0x0040: 696e 6973 7472 6174 6f72 206c 6f67 6765 inistrator.logge
0x0050: 6420 d.
20:15:35.132029IP 192.168.111.130.35928 > 192.168.111.1.ftp: . ack 209 win 92<nop,nop,timestamp 20720832 161230>
0x0000: 4510 0034 c2ea 4000 4006 17f5 c0a8 6f82 E..4..@[email protected].
0x0010: c0a8 6f01 8c58 0015 3dd2 d0aa 1c79 4c17 ..o..X..=....yL.
0x0020: 8010 005c 6f45 0000 0101 080a 013c 2cc0 ...\oE.......<,.
0x0030: 0002 75ce ..u.
20:15:35.132813IP 192.168.111.130.35928 > 192.168.111.1.ftp: P 65:71(6) ack 209 win 92<nop,nop,timestamp 20720833 161230>
0x0000: 4510 003a c2eb 4000 4006 17ee c0a8 6f82 E..:..@[email protected].
0x0010: c0a8 6f01 8c58 0015 3dd2 d0aa 1c79 4c17 ..o..X..=....yL.
0x0020: 8018 005c bb7e 0000 0101 080a 013c 2cc1 ...\.~.......<,.
0x0030: 0002 75ce 5359 5354 0d0a ..u.SYST..
20:15:35.133745IP 192.168.111.1.ftp > 192.168.111.130.35928: P 209:225(16) ack 71 win 65465<nop,nop,timestamp 161230 20720833>
0x0000: 4500 0044 f8d3 4000 8006 a20b c0a8 6f01 [email protected].
0x0010: c0a8 6f82 0015 8c58 1c79 4c17 3dd2 d0b0 ..o....X.yL.=...
0x0020: 8018 ffb9 0474 0000 0101 080a 0002 75ce .....t........u.
0x0030: 013c 2cc1 3231 3520 5769 6e64 6f77 735f .<,.215.Windows_
0x0040: 4e54 0d0a NT..
通过Telnet、FTP、POP3这些服务在网络上传输的数据是不加密的。在前面的例子中,用户administrator使用密码201102登录到FTP服务器。由于登录期间的认证过程也是不加密的,所以用户名和密码简单地包含在被传输的数据包的数据部分。