- 【万字长文】DeepSeek全栈开发实战:从数据处理到论文写作的全链路深度应用[特殊字符]
富 贵 儿 ¥
人工智能javapython编辑器大数据
引言:AI编程革命的认知升级在Gartner最新技术成熟度曲线中,智能编码助手已进入生产力爆发期。DeepSeek作为国产自研的智能开发引擎,其独特优势在于:垂直领域知识增强:覆盖Python/Java/C++等主流语言技术栈多模态交互能力:支持Markdown、LaTeX等专业格式输出动态上下文感知:最长支持16Ktokens的对话记忆代码安全审查:内置常见漏洞检测机制(CWETop25)本文将
- 输入任意一个数字判断其是不是回文数
西贝爱学习
java算法开发语言
//声明一个包名为com.itheima.fordemo的包packagecom.itheima.fordemo;//导入java.util包下的Scanner类,用于从控制台读取用户输入importjava.util.Scanner;//定义一个名为whiledemo1的公共类publicclasswhiledemo1{//程序的入口方法,Java程序从main方法开始执行publicstati
- Java中的PDF生成
城南|阿洋-计算机从小白到大神
javahtml开发语言
你知道如何轻松生成高质量PDF吗?——Java中的PDF生成大揭秘大家好,我是城南。前言在这个数字化时代,PDF文件已成为传递信息的重要方式。无论是合同、报告,还是技术文档,PDF都因其跨平台兼容性和固定格式而备受青睐。那么,你是否想过如何使用Java生成PDF呢?今天,我们将深入探讨Java中的PDF生成技术,让你轻松掌握这一技能,成为职场中的技术达人。什么是PDF?在深入讨论技术细节之前,我们
- 第一节:React 基础篇-React虚拟DOM原理及Diff算法优化策略
涵信
javascript前端react.js
必考点:虚拟DOM树对比(同级比较、Key的作用、组件类型判断)延伸:React18中并发更新对Diff算法的影响React虚拟DOM原理及Diff算法优化策略虚拟DOM核心原理概念:•虚拟DOM(VirtualDOM)是一个轻量级的JavaScript对象,用于描述真实DOM的结构。React通过虚拟DOM抽象真实DOM,避免直接操作高成本的真实DOM。•当组件状态变化时,React会重新生成新
- 使用Apache POI实现Java操作Office文件:从Excel、Word到PPT模板写入
老哥不老
apachejavaexcel
在企业级开发中,自动化处理Office文件(如Excel报表生成、Word文档模板填充、PPT批量制作)是常见需求。ApachePOI作为Java领域最成熟的Office文件操作库,提供了一套完整的解决方案。本文将通过实战代码,详细讲解如何使用POI写入Excel、Word文件,并深入探讨如何基于PPT模板生成定制化演示文稿。一、ApachePOI:Java操作Office的瑞士军刀ApacheP
- Node.js中的VM模块详解:执行JavaScript代码的虚拟机
大笑编程
node.jsjavascript开发语言js
Node.js是一个基于ChromeV8引擎构建的JavaScript运行时环境,它提供了许多内置模块来扩展其功能。其中一个强大的模块是VM(虚拟机)模块,它允许在Node.js环境中动态执行JavaScript代码。本文将深入探讨Node.js中的VM模块,介绍其用途、功能以及如何使用。1.什么是VM模块?VM模块是Node.js的内置模块之一,用于在运行时执行JavaScript代码。它提供了
- 【Java学习】Spring AI集成指南
meisongqing
基于AI的Java开发人工智能java学习SpringAI
在Java中使用SpringAI可以简化与生成式AI(如OpenAI、HuggingFace等)的集成。以下是详细步骤和示例代码,帮助你快速上手。1.添加依赖首先,在项目的pom.xml中添加SpringAI的依赖(以OpenAI为例):xml复制org.springframework.aispring-ai-openai-spring-boot-starter0.8.1运行HTML如果使用Gra
- JAVA学习日记(二)运算符+流程控制语句
DDDiccc
学习
(三)赋值运算符‘+=’加后赋值,‘-=’减后赋值,‘*=’乘后赋值,‘/=’除后赋值,‘%=’取余后赋值底层隐藏了一个强制类型转换。例:shorts=1;s+=1;等价于s=(short)(s+1)(四)关系运算符‘==’判断两边相等,相等返回true,不相等为false。‘!=’判断是否不相等,不相等返回true,相等返回false。‘>’,‘>=’,‘b?a:b;条件判定:inttemp=t
- JAVA题目笔记(七)
DDDiccc
1024程序员节
//转换罗马数字:键盘录入一个字符串要求1:长度小于等于9要求2:只能是数字将内容变成罗马数字://1-I2-II3-III4-IV5-V6-VI7-VII8-VIII9-IX如果录入数字为0则变成""(长度为0的字符串)Romannumber();publicstaticvoidRomannumber(){Stringroman[]=newString[]{"","I","II","III","
- 如何在Vue 3中使用vue-pdf-embed实现pdf预览、 打印、下载等功能
代码简单说
开发必备2025开发必备(限时特惠)vue.jspdf前端
如何在Vue3中使用vue-pdf-embed嵌入PDF文件在Web开发中,有时需要在网页中嵌入PDF文件以提供丰富的文档展示功能。Vue3作为流行的JavaScript框架,为开发者提供了强大的工具和生态系统。本文将详细介绍如何在Vue3项目中使用vue-pdf-embed组件轻松嵌入PDF文件,让你的网页具备出色的文档展示能力。一、组件特点精确渲染控制在Vue应用中实现对PDF文档渲染的精准掌
- Mybatis源码解析:java语言是编译解释型语言
m0_56710876
程序员java后端面试
前言从3月份开始,打算找工作,一个偶然的机会,拉勾上一个蚂蚁金服的师兄找到我,说要内推,在此感谢姚师兄,然后就开始了蚂蚁金服的面试之旅。把简历发过去之后,就收到了邮件通知,10个工作日联系我,请耐心等待。没过2天就接到一个杭州的座机,说要约我进行电话面试,效率还是挺高,然后当天晚上就进行了一面。下班后,吃了饭,专门找了一条人比较少的小路,到了7点,电话准时打过来了。InnoDB总体结构首先我们来看
- 【并发编程】多线程安全问题,如何避免死锁
阿Q说代码
并发专栏java并发编程线程安全多线程死锁
文章目录概念进程线程对比代码使用进程线程线程创建方式线程的生命周期和状态停止线程方法介绍sleep()/wait()为什么wait()不被定义在Thread中?sleep()定义在Thread中?run()/start()为什么使用多线程?线程安全问题线程死锁如何避免死锁?总结从今天开始阿Q将陆续更新java并发编程专栏,期待您的订阅。在系统学习线程之前,我们先来了解一下它的概念,与经常提到的进程
- Java中的线程安全问题(多线程重点)
bit_zhy
大厂之路java开发语言
JAVA中多线程的线程安全问题1.各个线程在系统中抢占式执行(根本原因)2.多个线程对同一个变量执行修改操作3.针对的变量/对象操作不是原子的针对2,3的一个例子解决办法:加锁(synchronized)修饰变量/对象4.内存可见性所引发的问题(编译器优化导致)例子:解决方法:加锁(synchronized)/volatile5.指令重排序问题(编译器优化导致)总结原因引起线程安全问题的原因大概有
- 第十六届蓝桥杯模拟赛第二期题解—Java
小咖拉眯
蓝桥杯算法java数据结构蓝桥杯图搜索算法
第十六届蓝桥杯模拟赛/校赛第二期个人题解,有错误的地方欢迎各位大佬指正问题一(填空题)【问题描述】如果一个数p是个质数,同时又是整数a的约数,则p称为a的一个质因数。请问,2024的最大的质因数是多少?【答案提交】这是一道结果填空的题,你只需要算出结果后提交即可。本题的结果为一个整数,在提交答案时只填写这个整数,填写多余的内容将无法得分。(1)思路::直接暴力枚举(2)代码publicclassP
- Java异常处理:框架集成实践之微服务场景实践(13)
双囍菜菜
Javajava微服务开发语言
微服务场景实践:异常处理的分布式挑战文章目录微服务场景实践:异常处理的分布式挑战分布式追踪中的异常标记熔断器模式与异常阈值配置GRPC/HTTP2的错误代码映射微服务异常处理的全局视角在微服务架构中处理异常,就像是在一个交响乐团中协调各种乐器——每个服务都是独立的演奏者,但如果没有人指挥,一个小号的走音就可能带偏整个乐团。传统的单体应用异常处理方式在微服务世界中显得力不从心,我们需要全新的策略来应
- 第十六届蓝桥杯模拟赛 Java组
程序员小huang
算法合集蓝桥杯算法
1、填空题【问题描述】如果一个数p是个质数,同时又是整数a的约数,则p称为a的一个质因数。请问2024有多少个质因数。【答案提交】这是一道结果填空的题,你只需要算出结果后提交即可。本题的结果为一个整数,在提交答案时只填写这个整数,填写多余的内容将无法得分。publicclassTM1{publicstaticvoidmain(String[]args){intcount=0;for(inti=2;
- Java 反射机制:概念、用途与示例
码农阿豪@新空间
好“物”分享java开发语言
个人名片作者简介:java领域优质创作者个人主页:码农阿豪工作室:新空间代码工作室(提供各种软件服务)个人邮箱:[2435024119@qq.com]个人微信:15279484656个人导航网站:www.forff.top座右铭:总有人要赢。为什么不能是我呢?专栏导航:码农阿豪系列专栏导航面试专栏:收集了java相关高频面试题,面试实战总结️Spring5系列专栏:整理了Spring5重要知识点与
- 【华为OD技术面试手撕真题】117、最长递增子序列 | 手撕真题+思路参考+代码解析(C & C++ & Java & Python & JS)(0ms)
KJ.JK
华为od华为od机试E卷华为od机试真题最长递增子序列
文章目录一、题目题目描述样例1二、代码参考C语言思路C语言代码C++语言思路C++代码Java语言思路Java代码Python语言思路Python代码JS语言思路JS代码作者:KJ.JK个人博客首页:KJ.JK专栏介绍:本专栏更新每年华为OD机试的高频手撕代码题,每个题目都会使用五种语言进行解答(C&C++&Java&Python&JS),思路分析都非常详细,争取实现最低的时间复杂度和高通过率,每
- 一文搞定 DeepSeek 本地部署,跑起来就这么简单
网罗开发
人工智能AI大模型深度学习人工智能自然语言处理
网罗开发(小红书、快手、视频号同名) 大家好,我是展菲,目前在上市企业从事人工智能项目研发管理工作,平时热衷于分享各种编程领域的软硬技能知识以及前沿技术,包括iOS、前端、HarmonyOS、Java、Python等方向。在移动端开发、鸿蒙开发、物联网、嵌入式、云原生、开源等领域有深厚造诣。图书作者:《ESP32-C3物联网工程开发实战》图书作者:《SwiftUI入门,进阶与实战》超级个体:CO
- 搞定大模型推理瓶颈:DeepSeek 提速全攻略
网罗开发
AI大模型人工智能数据挖掘语音识别机器学习深度学习人工智能
网罗开发(小红书、快手、视频号同名) 大家好,我是展菲,目前在上市企业从事人工智能项目研发管理工作,平时热衷于分享各种编程领域的软硬技能知识以及前沿技术,包括iOS、前端、HarmonyOS、Java、Python等方向。在移动端开发、鸿蒙开发、物联网、嵌入式、云原生、开源等领域有深厚造诣。图书作者:《ESP32-C3物联网工程开发实战》图书作者:《SwiftUI入门,进阶与实战》超级个体:CO
- 优化 Java 数据结构选择与使用,提升程序性能与可维护性
草药味儿の岁月
Java学习java数据结构开发语言
引言在软件开发中,数据结构的选择是影响程序性能、内存使用以及代码可维护性的关键因素之一。Java作为一门广泛使用的编程语言,提供了丰富的内置数据结构,如数组、链表、栈、队列、树、图以及集合框架中的各种接口实现(如List,Set,Map等)。然而,面对不同的应用场景,如何合理地选择和优化数据结构,成为了一个值得深入探讨的话题。本文将介绍几种常见的Java数据结构,并探讨如何根据实际需求进行优化选择
- HTML静态网页成品作业(HTML+CSS)——阜阳剪纸介绍设计制作(1个页面)
爱码网页
学生HTML个人网页作业作品html网页设计与制作静态网页htmlcss前端
不定期分享源码,关注不丢失哦文章目录一、作品介绍二、作品演示三、代码目录四、网站代码HTML部分代码五、源码获取一、作品介绍️本套采用HTML+CSS,未使用Javacsript代码,共有1个页面。二、作品演示三、代码目录四、网站代码HTML部分代码知名作品更多《伏虎》《三岔口》《王祥卧冰》《药王爷骑虎治龙》剪纸传人吴青平阜阳剪纸的巅峰人物朱英和程建礼,分别代表了精细刻法和随意起剪两种风格,两位老
- 【Java面试系列】Spring Boot微服务架构下的分布式事务处理与性能优化详解 - 3-5年Java开发必备知识
菜鸟起航ing
Java场景面试宝典JavaSpringBoot微服务分布式事务性能优化
【Java面试系列】SpringBoot微服务架构下的分布式事务处理与性能优化详解-3-5年Java开发必备知识引言在当今的微服务架构中,分布式事务处理和性能优化是面试中经常被问及的高频话题。随着系统规模的扩大,如何保证数据一致性和系统性能成为了开发者必须面对的挑战。本文将从基础概念到高级特性,结合实际应用场景和面试问题,全面解析这一主题。基础知识1.分布式事务的概念分布式事务是指跨越多个服务或数
- java模拟简单的qq聊天_初学java之模拟QQ聊天软件(简单实现)
伥鬼
java模拟简单的qq聊天
引言:这个程序是自从学习java以来写的第一个比较大的图形界面程序,花费了大约一周的时间,作为期末的课程设计,也算是基本上完成了任务,当然由于作者的编程能力有限,代码中难免存在BUG,不太简练,今天搬到博客上来,也算是对自己学习历程的一段记录吧,当然,如果我的这篇博客有幸被诸君看到,欢迎提出意见和建议,这篇博客仅仅作为我的一个记录吧,如果可能(估计也没时间了),将在后续版本中不断完善。所有源代码移
- linux c语言打印hello,C语言——打印“Hello World!”,这么简单?
彭浩翔
linuxc语言打印hello
iOS开发系列--C语言之数组和字符串概览数组在C语言中有着特殊的地位,它有很多特性,例如它的存储是连续的,数组的名称就是数组的地址等.而在C语言中是没有String类型的,那么如果要表示一个字符串,就必须使用字符数组.今天主要就介绍如...java.lang.NoClassDefFoundError:异常信息:十一月10,20165:20:15下午org.
- 《Vue 实战:小型项目练手与感悟》
计算机毕设定制辅导-无忧学长
#Vuevue.js前端javascript
一、Vue基础与准备在开始Vue项目之前,对JavaScript、CSS、HTML基础知识的掌握至关重要。一、JavaScript基础知识要求数组常用方法filter():创建一个新的数组,新数组中的元素是通过检查指定数组中符合条件的所有元素。map():返回一个新数组,数组中的元素为原始数组元素调用函数处理后的值。forEach():用于调用数组的每个元素,并将元素传递给回调函数。find():
- WebTracing:如何使用一款SDK实现前端全链路监控
我码玄黄
思维的火花教你一招github前端前端开发前端监控
引言在产品的开发和运营过程中我们经常会遇到一些问题,如用户反馈说无法对某某商品下单,而另一位负责运营的同事也提到某某广告在手机上打不开。尽管这些问题被多次报告,但我们却难以复现这些故障,这让团队感到十分棘手。如何有效地记录项目中的错误并能够重现这些问题,正是我们需要通过监控平台来解决的关键痛点之一。WebTracing是一款专为前端项目量身定制的JavaScript埋点SDK,它提供了完善的前端监
- java:编写一个SortedList接口
鱼弦
java开发语言
鱼弦:CSDN内容合伙人、CSDN新星导师、51CTO(Top红人+专家博主)、github开源爱好者(go-zero源码二次开发、游戏后端架构https://github.com/Peakchen)在Java中编写一个SortedList接口,可以用于表示一个有序列表。一个有序列表是一个集合,其中的元素按照特定的排序规则进行排序。以下是一个基本的SortedList接口的示例:publicint
- C语言if语句的坑
埃里克·妙
c语言
嗨!这里是C语言小白。因为考试需要开始学习C语言了,敲惯了JavaScript后,敲C语言实现课后习题,敲出来的结果总是意料之外!每每排错,都是if语句有问题,外层if语句的else子句被当成外层if语句里内嵌if语句的子句了!我真是太不习惯C敲if语句的形式了!今天我就要把它拿下!标准形式的if语句(if语句有两种形式:一种是带else子句的,一种是不带else子句的//带else子句的if语句
- JavaScript性能优化(上)
DirectYang
javascript开发语言ecmascript
1.减少DOM操作减少DOM操作是优化JavaScript性能的重要方法,因为频繁的DOM操作会导致浏览器重绘和重排,从而影响性能。以下是一些具体的策略和技术,可以帮助有效减少DOM操作:1.1.批量更新DOM亲切与母体:将多个DOM更新合并为一个操作。例如,可以创建一个空的容器,先在内存中构建所有需要的子元素,最后一次性将这个容器添加到主DOM树中。constfragment=document.
- 微信开发者验证接口开发
362217990
微信 开发者 token 验证
微信开发者接口验证。
Token,自己随便定义,与微信填写一致就可以了。
根据微信接入指南描述 http://mp.weixin.qq.com/wiki/17/2d4265491f12608cd170a95559800f2d.html
第一步:填写服务器配置
第二步:验证服务器地址的有效性
第三步:依据接口文档实现业务逻辑
这里主要讲第二步验证服务器有效性。
建一个
- 一个小编程题-类似约瑟夫环问题
BrokenDreams
编程
今天群友出了一题:
一个数列,把第一个元素删除,然后把第二个元素放到数列的最后,依次操作下去,直到把数列中所有的数都删除,要求依次打印出这个过程中删除的数。
&
- linux复习笔记之bash shell (5) 关于减号-的作用
eksliang
linux关于减号“-”的含义linux关于减号“-”的用途linux关于“-”的含义linux关于减号的含义
转载请出自出处:
http://eksliang.iteye.com/blog/2105677
管道命令在bash的连续处理程序中是相当重要的,尤其在使用到前一个命令的studout(标准输出)作为这次的stdin(标准输入)时,就显得太重要了,某些命令需要用到文件名,例如上篇文档的的切割命令(split)、还有
- Unix(3)
18289753290
unix ksh
1)若该变量需要在其他子进程执行,则可用"$变量名称"或${变量}累加内容
什么是子进程?在我目前这个shell情况下,去打开一个新的shell,新的那个shell就是子进程。一般状态下,父进程的自定义变量是无法在子进程内使用的,但通过export将变量变成环境变量后就能够在子进程里面应用了。
2)条件判断: &&代表and ||代表or&nbs
- 关于ListView中性能优化中图片加载问题
酷的飞上天空
ListView
ListView的性能优化网上很多信息,但是涉及到异步加载图片问题就会出现问题。
具体参看上篇文章http://314858770.iteye.com/admin/blogs/1217594
如果每次都重新inflate一个新的View出来肯定会造成性能损失严重,可能会出现listview滚动是很卡的情况,还会出现内存溢出。
现在想出一个方法就是每次都添加一个标识,然后设置图
- 德国总理默多克:给国人的一堂“震撼教育”课
永夜-极光
教育
http://bbs.voc.com.cn/topic-2443617-1-1.html德国总理默多克:给国人的一堂“震撼教育”课
安吉拉—默克尔,一位经历过社会主义的东德人,她利用自己的博客,发表一番来华前的谈话,该说的话,都在上面说了,全世界想看想传播——去看看默克尔总理的博客吧!
德国总理默克尔以她的低调、朴素、谦和、平易近人等品格给国人留下了深刻印象。她以实际行动为中国人上了一堂
- 关于Java继承的一个小问题。。。
随便小屋
java
今天看Java 编程思想的时候遇见一个问题,运行的结果和自己想想的完全不一样。先把代码贴出来!
//CanFight接口
interface Canfight {
void fight();
}
//ActionCharacter类
class ActionCharacter {
public void fight() {
System.out.pr
- 23种基本的设计模式
aijuans
设计模式
Abstract Factory:提供一个创建一系列相关或相互依赖对象的接口,而无需指定它们具体的类。 Adapter:将一个类的接口转换成客户希望的另外一个接口。A d a p t e r模式使得原本由于接口不兼容而不能一起工作的那些类可以一起工作。 Bridge:将抽象部分与它的实现部分分离,使它们都可以独立地变化。 Builder:将一个复杂对象的构建与它的表示分离,使得同
- 《周鸿祎自述:我的互联网方法论》读书笔记
aoyouzi
读书笔记
从用户的角度来看,能解决问题的产品才是好产品,能方便/快速地解决问题的产品,就是一流产品.
商业模式不是赚钱模式
一款产品免费获得海量用户后,它的边际成本趋于0,然后再通过广告或者增值服务的方式赚钱,实际上就是创造了新的价值链.
商业模式的基础是用户,木有用户,任何商业模式都是浮云.商业模式的核心是产品,本质是通过产品为用户创造价值.
商业模式还包括寻找需求
- JavaScript动态改变样式访问技术
百合不是茶
JavaScriptstyle属性ClassName属性
一:style属性
格式:
HTML元素.style.样式属性="值";
创建菜单:在html标签中创建 或者 在head标签中用数组创建
<html>
<head>
<title>style改变样式</title>
</head>
&l
- jQuery的deferred对象详解
bijian1013
jquerydeferred对象
jQuery的开发速度很快,几乎每半年一个大版本,每两个月一个小版本。
每个版本都会引入一些新功能,从jQuery 1.5.0版本开始引入的一个新功能----deferred对象。
&nb
- 淘宝开放平台TOP
Bill_chen
C++c物流C#
淘宝网开放平台首页:http://open.taobao.com/
淘宝开放平台是淘宝TOP团队的产品,TOP即TaoBao Open Platform,
是淘宝合作伙伴开发、发布、交易其服务的平台。
支撑TOP的三条主线为:
1.开放数据和业务流程
* 以API数据形式开放商品、交易、物流等业务;
&
- 【大型网站架构一】大型网站架构概述
bit1129
网站架构
大型互联网特点
面对海量用户、海量数据
大型互联网架构的关键指标
高并发
高性能
高可用
高可扩展性
线性伸缩性
安全性
大型互联网技术要点
前端优化
CDN缓存
反向代理
KV缓存
消息系统
分布式存储
NoSQL数据库
搜索
监控
安全
想到的问题:
1.对于订单系统这种事务型系统,如
- eclipse插件hibernate tools安装
白糖_
Hibernate
eclipse helios(3.6)版
1.启动eclipse 2.选择 Help > Install New Software...> 3.添加如下地址:
http://download.jboss.org/jbosstools/updates/stable/helios/ 4.选择性安装:hibernate tools在All Jboss tool
- Jquery easyui Form表单提交注意事项
bozch
jquery easyui
jquery easyui对表单的提交进行了封装,提交的方式采用的是ajax的方式,在开发的时候应该注意的事项如下:
1、在定义form标签的时候,要将method属性设置成post或者get,特别是进行大字段的文本信息提交的时候,要将method设置成post方式提交,否则页面会抛出跨域访问等异常。所以这个要
- Trie tree(字典树)的Java实现及其应用-统计以某字符串为前缀的单词的数量
bylijinnan
java实现
import java.util.LinkedList;
public class CaseInsensitiveTrie {
/**
字典树的Java实现。实现了插入、查询以及深度优先遍历。
Trie tree's java implementation.(Insert,Search,DFS)
Problem Description
Igna
- html css 鼠标形状样式汇总
chenbowen00
htmlcss
css鼠标手型cursor中hand与pointer
Example:CSS鼠标手型效果 <a href="#" style="cursor:hand">CSS鼠标手型效果</a><br/>
Example:CSS鼠标手型效果 <a href="#" style=&qu
- [IT与投资]IT投资的几个原则
comsci
it
无论是想在电商,软件,硬件还是互联网领域投资,都需要大量资金,虽然各个国家政府在媒体上都给予大家承诺,既要让市场的流动性宽松,又要保持经济的高速增长....但是,事实上,整个市场和社会对于真正的资金投入是非常渴望的,也就是说,表面上看起来,市场很活跃,但是投入的资金并不是很充足的......
- oracle with语句详解
daizj
oraclewithwith as
oracle with语句详解 转
在oracle中,select 查询语句,可以使用with,就是一个子查询,oracle 会把子查询的结果放到临时表中,可以反复使用
例子:注意,这是sql语句,不是pl/sql语句, 可以直接放到jdbc执行的
----------------------------------------------------------------
- hbase的简单操作
deng520159
数据库hbase
近期公司用hbase来存储日志,然后再来分析 ,把hbase开发经常要用的命令找了出来.
用ssh登陆安装hbase那台linux后
用hbase shell进行hbase命令控制台!
表的管理
1)查看有哪些表
hbase(main)> list
2)创建表
# 语法:create <table>, {NAME => <family&g
- C语言scanf继续学习、算术运算符学习和逻辑运算符
dcj3sjt126com
c
/*
2013年3月11日20:37:32
地点:北京潘家园
功能:完成用户格式化输入多个值
目的:学习scanf函数的使用
*/
# include <stdio.h>
int main(void)
{
int i, j, k;
printf("please input three number:\n"); //提示用
- 2015越来越好
dcj3sjt126com
歌曲
越来越好
房子大了电话小了 感觉越来越好
假期多了收入高了 工作越来越好
商品精了价格活了 心情越来越好
天更蓝了水更清了 环境越来越好
活得有奔头人会步步高
想做到你要努力去做到
幸福的笑容天天挂眉梢 越来越好
婆媳和了家庭暖了 生活越来越好
孩子高了懂事多了 学习越来越好
朋友多了心相通了 大家越来越好
道路宽了心气顺了 日子越来越好
活的有精神人就不显
- java.sql.SQLException: Value '0000-00-00' can not be represented as java.sql.Tim
feiteyizu
mysql
数据表中有记录的time字段(属性为timestamp)其值为:“0000-00-00 00:00:00”
程序使用select 语句从中取数据时出现以下异常:
java.sql.SQLException:Value '0000-00-00' can not be represented as java.sql.Date
java.sql.SQLException: Valu
- Ehcache(07)——Ehcache对并发的支持
234390216
并发ehcache锁ReadLockWriteLock
Ehcache对并发的支持
在高并发的情况下,使用Ehcache缓存时,由于并发的读与写,我们读的数据有可能是错误的,我们写的数据也有可能意外的被覆盖。所幸的是Ehcache为我们提供了针对于缓存元素Key的Read(读)、Write(写)锁。当一个线程获取了某一Key的Read锁之后,其它线程获取针对于同
- mysql中blob,text字段的合成索引
jackyrong
mysql
在mysql中,原来有一个叫合成索引的,可以提高blob,text字段的效率性能,
但只能用在精确查询,核心是增加一个列,然后可以用md5进行散列,用散列值查找
则速度快
比如:
create table abc(id varchar(10),context blog,hash_value varchar(40));
insert into abc(1,rep
- 逻辑运算与移位运算
latty
位运算逻辑运算
源码:正数的补码与原码相同例+7 源码:00000111 补码 :00000111 (用8位二进制表示一个数)
负数的补码:
符号位为1,其余位为该数绝对值的原码按位取反;然后整个数加1。 -7 源码: 10000111 ,其绝对值为00000111 取反加一:11111001 为-7补码
已知一个数的补码,求原码的操作分两种情况:
- 利用XSD 验证XML文件
newerdragon
javaxmlxsd
XSD文件 (XML Schema 语言也称作 XML Schema 定义(XML Schema Definition,XSD)。 具体使用方法和定义请参看:
http://www.w3school.com.cn/schema/index.asp
java自jdk1.5以上新增了SchemaFactory类 可以实现对XSD验证的支持,使用起来也很方便。
以下代码可用在J
- 搭建 CentOS 6 服务器(12) - Samba
rensanning
centos
(1)安装
# yum -y install samba
Installed:
samba.i686 0:3.6.9-169.el6_5
# pdbedit -a rensn
new password:123456
retype new password:123456
……
(2)Home文件夹
# mkdir /etc
- Learn Nodejs 01
toknowme
nodejs
(1)下载nodejs
https://nodejs.org/download/ 选择相应的版本进行下载 (2)安装nodejs 安装的方式比较多,请baidu下
我这边下载的是“node-v0.12.7-linux-x64.tar.gz”这个版本 (1)上传服务器 (2)解压 tar -zxvf node-v0.12.
- jquery控制自动刷新的代码举例
xp9802
jquery
1、html内容部分 复制代码代码示例: <div id='log_reload'>
<select name="id_s" size="1">
<option value='2'>-2s-</option>
<option value='3'>-3s-</option
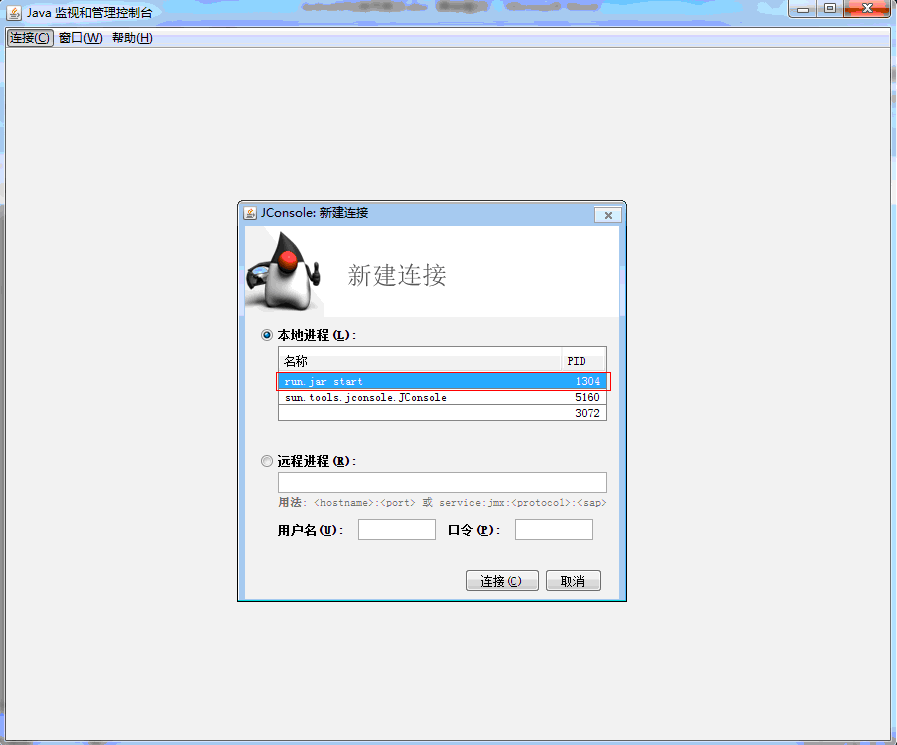 点击连接之后就可以看到ActiveMQ的运行情况。默认情况下是不需要用户名和口令的,修改activemq.bat,找到
点击连接之后就可以看到ActiveMQ的运行情况。默认情况下是不需要用户名和口令的,修改activemq.bat,找到