Sensitive directory/file Integrity Monitoring and Checking
catalogue
1. OSSEC 2. HashSentry: Host-Based IDS in Python 3. Afick 4. 检测流程
1. OSSEC
OSSEC is an Open Source Host-based Intrusion Detection System. It performs
1. log analysis 2. integrity checking 3. Windows registry monitoring 4. rootkit detection 5. real-time alerting and active response
It runs on most operating systems, including Linux, OpenBSD, FreeBSD, Mac OS X, Solaris and Windows.
0x1: Improving File Integrity Monitoring with OSSEC
FIM or "File Integrity Monitoring" can be defined as the process of validating the integrity of operating system and applications files with a verification method using a hashing algorythm like MD5 or SHA1 and then comparing the current file state with a baseline. A hash will allow the detection of files content modification but other information can be checked too
1. owner 2. permissions 3. modification time.
Implemeting file integrity monitoring is a very good way to detect compromized servers. Not only operating system files can be monitored (/etc on UNIX, registry on Windows, share libraries, etc) but also applications (monitoring your index.php or index.html can reveal a defaced website).
During its implementation, a file integrity monitoring project may face two common issues:
1. The baseline used to be compared with the current file status must of course be trusted. To achieve this, it must be stored on a safe place where attacker cannot detect it and cannot alter it! 2. The process must be fine tuned to react only on important changes otherwise they are two risks: 1) The real suspicious changes will be hidden in the massive flow of false-positives. 2) People in charge of the control could miss interesting changes.
0x2: false positive
A side effect of file integrity monitoring is the number of false positive alerts generated when patching your systems. Keeping the latest patch level is important but hundreds of files can be replaced only by one new package!
Relevant Link:
http://ossec.github.io/docs/ https://blog.rootshell.be/2013/05/13/improving-file-integrity-monitoring-with-ossec/
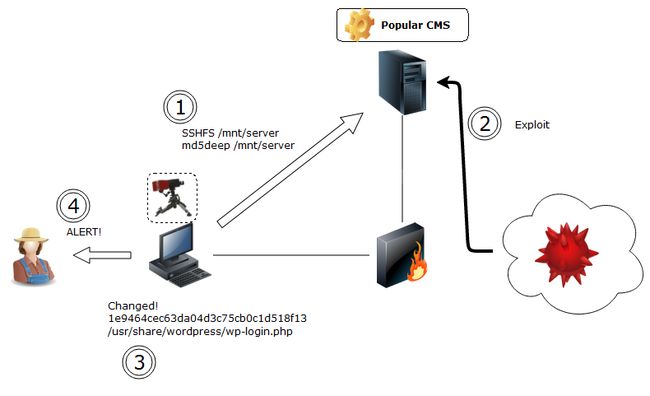
2. HashSentry: Host-Based IDS in Python
HashSentry modus operandi goes like this:
1. The remote File System is mounted using sshfs 2. A hashing algorithm is applied to files and compared with their known original hash. (Hashes are learnt on first run) 3. Alerts are sent to the sysadmin in case a file is modified or a new file appears
Relevant Link:
http://blog.makensi.es/post/5759911160/hashsentry-host-based-ids-in-python-for-the-poor
3. Afick
Afick is a fast and portable intrusion detection and integrity monitoring system, designed to work on all platform (it only needs perl and standard modules), including windows, linux, unix.
The configuration syntax is very close from tripwire/aide
0x1: functionnalities
1. portable without any change to all common operating systems (windows, UNIX ...) 2. easy install : no need to compile or to install many others tools 3. fast 4. display new/deleted/modified files 5. display dangling links 6. may be used by any user 7. any number of base and config 8. config file with exceptions and jokers 9. configuration file syntax close from aide's one 10. command line is perfect on UNIX, but windows users prefer graphical interfaces, so I add a Tk interface
Relevant Link:
https://sourceforge.net/projects/afick/ http://afick.sourceforge.net/
4. 检测流程
1. 遍历目标目录所有文件 2. 获取meta信息 1) filepath 2) hashsum 3) gmt_create 4) gmt_modified 3. 计算filepath的hash值,定位到sqlite里的hash(filepath)记录,如果未找到对应记录,则说明该文件是新增的 1) 需要额外判断一下当前是否是本机第一次运行(基线建立),第一次运行则忽略 2) 如果不是第一次运行,则上报异常文件新增事件 4. 如果成功定位到定位到sqlite里的hash(filepath)记录,获取gmt_create、gmt_modified,比对和当前文件的gmt_create、gmt_modified是否相同,如果相同,则说明当前文件没有修改,则直接跳过 5. 如果gmt_create、gmt_modified不一致,则说明有可能被修改了(因为可能vim打开一次也会导致gmt_create、gmt_modified的改变),计算对应文件内容的HASH值,并和hash(filepath)记录对应记录里的hash进行比对,如果不一致说明文件被修改了,上报该条记录,并更新sqlite缓存记录
敏感目录的文件完整性监控,是对恶意软件犯罪行为的一个普适抽象,即不管这是个什么马,在linux要实现持久存活,都有极大可能会往/etc/init.d/下面写入新文件,或者修改已有文件
Relevant Link:
http://securityxploded.com/pymal.php https://sourceforge.net/directory/os:windows/?q=file%20integrity%20check http://blog.makensi.es/post/5759911160/hashsentry-host-based-ids-in-python-for-the-poor http://www.ethanjoachimeldridge.info/tech-blog/implementing-subresource-integrity-sri http://liw.iki.fi/liw/download/md5sum.py https://github.com/clouserw/scripts/blob/master/md5verify.py https://bbs.archlinux.org/viewtopic.php?id=83839 https://pypi.python.org/pypi/hsh/
Copyright (c) 2016 LittleHann All rights reserved